Don't Kill my Demon - Havoc for Adversary
Shellcode and Multiple Agents: Combined with Cobalt Strike Malleable C2 Profile
Less popular compared to others, but that’s Havoc. "I respect my Operator" — that’s Havoc.
For instance, such was the approach of the Mysterious Werewolf cluster that leveraged the Mythic framework in one of its campaigns.
However, there’s a reason Havoc feels right when you’re doing modern red team work, and it’s not because of the UI or some checklist of features.
It’s because Havoc is opinionated in the same way Windows internals are opinionated.
It assumes you understand the system you’re inside, and it stays out of your way.

Another thing Havoc gets right is process interaction. Demon doesn’t pretend process injection is some mystical art.
You choose the process. You understand its privileges, its token, its integrity level. You understand what spawning there implies.
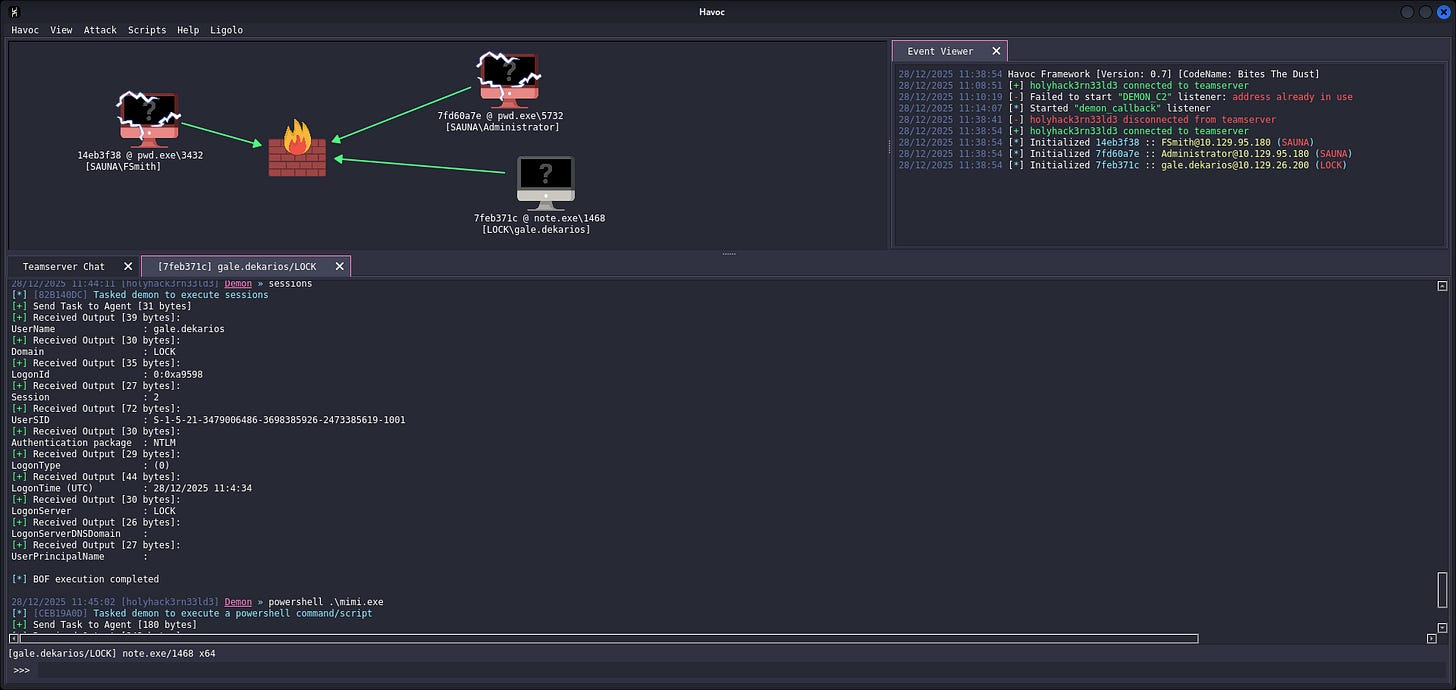
Real-world Campaign Context
Criminals often send out phishing emails on behalf of well-known organizations. To make their messages look plausible and convincing, adversaries eagerly use the names of renowned universities, government regulators, and law enforcement agencies. The names of credible institutions lull the user’s vigilance, prompting them to open malicious emails.
It is important to remember that the organizations whose brands are abused in phishing emails are not liable for the actions of criminals and the associated damage.
Based on the compiler, the Demon also doesn’t scream. Network-wise, execution-wise, behavior-wise.
It stared at EDR telemetry and decided the solution wasn’t more features; it was restraint.

Also, I have in mind for 2026 that we will (STILL) need to do some things to customize our exploit chain to bypass AV/EDR/IDS.
Specifically, we need to make our shellcode less likely to alert signature and dynamic analysis-based detection on the host, as well as make the network traffic look more normal.
Happy Hacking!